Alin Tomescu
@alinush407
Followers
45,188
Following
0
Media
129
Statuses
719
Founding Team & Head of Cryptography at @AptosLabs | crypto(graphic) thoughts, papers, blog posts, (open) questions | oh, and motorcycling! 🏍️
California, USA
Joined July 2009
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
seokjin
• 857765 Tweets
Judge Cannon
• 187741 Tweets
LINGORM TSOU EP4
• 173574 Tweets
#ใจซ่อนรักEP4
• 161962 Tweets
Jack Smith
• 143265 Tweets
#THEFIRSTTAKE_SB19第2弾
• 123140 Tweets
#海のはじまり
• 97227 Tweets
Morning Joe
• 83287 Tweets
Special Counsel
• 72945 Tweets
BLEND AND BREW X NORAWIT
• 51320 Tweets
UVERworld
• 49193 Tweets
Coolock
• 48965 Tweets
あんスタ
• 46155 Tweets
プライムデー
• 42735 Tweets
NCAA
• 37304 Tweets
Ford Foundation
• 36879 Tweets
海ちゃん
• 33701 Tweets
11th Circuit
• 31661 Tweets
CHK CHK BOOM MV TEASER 2
• 26737 Tweets
#StrayKids_ATE_D3
• 26580 Tweets
ジンくん
• 20240 Tweets
Jack Black
• 17965 Tweets
gracie
• 15696 Tweets
田中れい
• 15286 Tweets
TAKUYA
• 15169 Tweets
Mase
• 14291 Tweets
#幸せになってほしかったキャラ挙げろ
• 13309 Tweets
J Prince
• 12139 Tweets
Museum Card
• 11886 Tweets
Larry Fink
• 11475 Tweets
ミュージアムカード
• 10664 Tweets
Romanowskiego
• 10633 Tweets
弥生さん
• 10385 Tweets
Last Seen Profiles
Pinned Tweet
What is an
@aptos
keyless account? 🧵
It's a blockchain account derived from (say) your Google account and an application (wallet, dapp, etc).
It's bound not just to you (e.g., you
@gmail
.com) but also to the application (e.g.,
@PetraWallet
, or
@ThalaLabs
, or
@VibrantXFinance
)
10
31
102
Dear
#crypto
Twitter, what kind of cryptography would you like to use in your Move smart contracts on
@AptosLabs
? Currently...
38
33
168
Want to write or play randomized games on
@Aptos_Network
in Move? 🎮
We are looking for feedback on our on-chain, distributed randomness API in Move 🎲!
See Aptos Improvement Proposal (AIP) 41 here:
A very short (1/4) thread 🧵below...
5
56
177
A question about
@sama
's
@worldcoin
: What happens when I lose my SK after registering with my iris? Or when my SK is stolen.
Currently, nothing, it seems. I'm done. I can't recover my account (see ).
Disturbing, but potentially fixable (1/n) 🧵
6
52
118
If you ride motorcycles and do other fun things like commit to polynomials, Verkleize your trees, aggregate signatures or proofs, make HVZK interactive protocols non-interactive and/or write Rust code, then apply to
@AptosLabs
and we'll take you for a ride! (
@rgelash
@sherry_xzy
)
11
9
103
🧵
@AptosLabs
taught me the challenges of going from _idea_, to academic paper, to production-ready implementation and, finally, to deployment!
🎲 A perfect example is our *instant* on-chain randomness in Move, or
@aptos
Roll:
Let's look at the idea💡!
3
27
107
At
@AptosLabs
, researchers works closely with engineers to solve tomorrow's problems ().
Ask
@PetraWallet
's
@drewhariri
, who just learned what a pairing-friendly group is, how BLS signatures work and how they give threshold OPRFs ()
4
5
90
🥳🎉🍾 Aptos Keyless accounts!
1. No more mnemonics, no more lost keys!
2. Sign your
@Aptos
transactions with your existing Google account!
3. Sign in into a dapp without a wallet!
4. Protect your Aptos Keyless session using Face ID on Apple devices!
5. Privacy
The Aptos ZK ceremony was just the beginning! 🔥🛠️ Developers can keep up the momentum by checking out our Aptos Keyless SDK, now open for early testing and feedback on
@Aptos
Devnet.
Aptos Labs needs world-class builders on Aptos to put our research and tech to the test! 💪
7
60
238
1
30
89
If you're interested in being my intern at
@vmwareresearch
and working on privacy-preserving research, DM me!
1
24
74
Want to build powerful *cryptographic* dApps?
Check out
@Aptos_Network
's cryptographic APIs in Move!
Whether you want to veil your coins, harness off-chain public randomness, or verify a Groth16 ZKP over *any* curve, we've got you covered! 🧵
2
19
60
We've recently updated AIP-41, which proposes an API for on-chain randomness on
@Aptos_Network
!
Take a look at v1.2 here:
Want to write or play randomized games on
@Aptos_Network
in Move? 🎮
We are looking for feedback on our on-chain, distributed randomness API in Move 🎲!
See Aptos Improvement Proposal (AIP) 41 here:
A very short (1/4) thread 🧵below...
5
56
177
2
14
52
Like I said before, mnemonics suck!
So I contributed to the ZK ceremony for
@Aptos_Network
's OpenID-based blockchain accounts
Your blockchain account = your Google account!
Check out the 🌶️ details in AIP-61:
(My contribution )
5
14
55
Today I learned a(nother) cool way to prove an inner-product from
@sourav1547
et al's paper () that leverages the univariate sumcheck protocol from Aurora ().
3
8
54
Sweet thread on how
@Aptos
keyless accounts leverage the OpenID Connect (OIDC) protocol to authorize transactions.
This includes reaching consensus on the PKs of the OIDC providers, which was efficiently implemented and described in AIP-67 by
@zjma2022
!
1/ The team at
@AptosLabs
is actively working on developing Keyless accounts for
@Aptos
, investing significant effort into this revolutionary project🌠
As announced in AIP-61, the Consensus on JSON Web Keys is presented in a separate AIP-67 proposal.
Details in the thread👇
2
9
49
2
11
49
🧵 How do we provide instant on-chain randomness on
@Aptos_Network
?
One key ingredient is a fast Lagrange interpolation algorithm from our 2020 work (& my PhD thesis) with
@bennypinkas
,
@ittaia
et al ()
So, if you're doing threshold BLS, read below...👇
1
11
47
Check out my
#zkSummit11
talk on
@Aptos
keyless accounts:
The slides are available here:
Oh, that's me 🏍️'ing from CA to TX to catch the total solar eclipse 🌞 (and my flight to Athens, Greece for
#zkSummit
)
5
10
51
Here's a short explanation of rogue-key attacks, which I wish I had on hand to show during today's Move Monday at
@AptosLabs
().
4
4
39
A step closer to stateless cryptocurrencies via aggregatable subvector commitments w/
@ittaia
,
@VitalikButerin
,
@drakefjustin
,
@dankrad
and
@Khovr
. Plus a big thanks to
@MadarsV
:
0
11
39
1/ “If you thought before that science is certain, well, that’s just an error on your part.” –
@ProfFeynman
.
A thread 🧵 and blogpost ✍️ below, to remind us that science is a process, not a truth ().
1
5
32
Mnemonics suck.
Thanks to
@drewhariri
's amazing work, auto-backed-up passkeys allow users to create an
@Aptos_Network
account without writing down a mnemonic!
Nor do they expose the underlying secret key, which will make it harder for users to shoot themselves in the foot.
2
6
37
Lots of magic behind
@Aptos
keyless accounts: zero-knowledge proofs (Groth16), verifiable unpredictable functions (BLS), SNARK-friendly hashing (Poseidon) and, of course...
Polynomials galore!!
@mstraka
explains how we use polynomials in our ZK circuit to concatenate strings 👇
0
3
34
Wish I was in Singapore to listen to
@bennypinkas
talk about MPC!
Our in-house expert on MPC (multi-party computation),
@bennypinkas
, is Singapore-bound to share his insights at DeCompute 2023.
Secure your spot:
3
2
39
2
1
32
I can't watch this 🫣, but I hope you do! 😄
In the podcast, I cover
@aptos
on-chain randomness () and keyless accounts ().
Oh, and there's a lot of talk about peppers, for some reason? 🌶️
cc
@perryjrandall
and
@aptoskent
Cutting edge crypto: PROD vs Sci-Fi
0.7x speed w/ frequent rewinds was the only way for this
@zeroknowledgefm
episode with
@alinush407
.
👊 to
@AptosLabs
for leading the charge on bringing the newest crypto research to users rather than just papers!
3
4
21
4
9
31
Indeed,
@Aptos_Network
will soon enable support for *keyless* accounts!
Your
@Aptos_Network
blockchain account = Your OpenID account (e.g., Google, Facebook, Apple, etc.)!
Inexperienced users will no longer lose their secret key because they won't have one to begin with!
👇👇
OpenID Blockchain accounts implementation will be a step forward in enhancing user-friendliness, security, and efficiency.
Excited to share that as a representative of
@everstake_pool
, I joined the
@Aptos_Network
ZK Setup Ceremony.
Check out the 🧵for more explanations.
2
20
76
0
3
31
Join us: we've got cool research problems (Verkle trees, DAG-based consensus, sharding, aggregate signatures)... and many motorcycles! 🏍️🛵
5
1
20
Thank you
@Oleksii_Ever
! We’ve pushed some changes to the AIP since and we’re still looking for more feedback!
@MoveBuilders
@Aptos_Network
@0xsrmist
2/ Do you want to know more about a distributed randomness API in
#Move
?
@alinush407
did us a favor by explaining what it is and invited us to join the AIP-41 - Move APIs for randomness generation discussion:
1
0
8
1
1
18
New work on scaling BLS threshold sigs (and other threshold cryptosystems), including its DKG protocol, by precomputing proofs fast in KZG polynomial commitments w/
@ittaia
and
@bennypinkas
:
0
10
29
Tomorrow (Tuesday), IIRC, I will be talking about our work on UTT: Sensibly-anonymous decentralized payments without zkSNARKs ().
Today is for flying across the Atlantic ocean 😅.
@Aptosassistant
@alinush407
is giving a talk today on something cryptography I don’t understand at SBC!
0
0
2
3
2
28
WHO DID THIS??
@AlyssaPonzo
,
@mstrakastrak
,
@zjma2022
,
@rex1fernando
shame on you for making blockchain accounts so easy to use by everyone!
@AptosLabs
@Aptos
5/ Keyless accounts
Say goodbye to cumbersome secret keys as users will have the option to link their blockchain accounts directly to existing OIDC accounts (such as Google)
Some details were previously highlighted here👇
1
0
11
0
0
25
@chelseakomlo
At
@Aptos_Network
, for our PoS distributed randomness, we are using groups of ~1000 and thresholds of 666, leveraging my PhD thesis work ().
Large thresholds can be a cheap price one pays for doing threshold crypto in the PoS setting!
1
3
25
Really neat paper I skimmed through this morning: "Structure-preserving Threshold Signatures", by
@Mahdi_seda
,
@drl3c7er
,
@cryptulf
and
@bpreneel1
. (tl;dr as screenshots):
7
5
25
@realjcz
This is already happening to some extent: on
@Aptos_Network
, we leverage the OpenID Connect (OIDC) protocol to create "keyless" blockchain accounts backed by a Web 2 account: e.g., your blockchain account = your Google account or your Facebook account
See
1
0
23
Continuing the tweet hurricane 🌀 on the challenges of taking
@aptos
on-chain randomness from idea ✅ , to *academic paper* 📜, to production-ready implementation and, finally, to deployment ().
Let's look at *the paper* part of the journey! 🛣️ 🏍️
🧵
@AptosLabs
taught me the challenges of going from _idea_, to academic paper, to production-ready implementation and, finally, to deployment!
🎲 A perfect example is our *instant* on-chain randomness in Move, or
@aptos
Roll:
Let's look at the idea💡!
3
27
107
1
7
21
RaNd0Mly hack on your
@Aptos_Network
randapps!
See our developer-friendly API here () and how you can use it to build a raffle () or a lottery ().
On-chain, unpredictable, unbiasable, *instant* randomness! 🎲
1
0
23
@SashaSpiegelman
@jacopo851
@dubbel06
@0xMert_
@XiangZhuolun
@jacopo851
, from Algorand's design (), their beacon is *external* and thus much trickier to use securely & swiftly (delivers once every 8 rounds).
Our APIs are as secure as our PoS blockchain & return randomness instantly to the caller (see screenshots).
4
3
22
Join us tomorrow for the first Vector Commitment day, organized by
@13portocale
and
@rgennaro67
(). I'll be speaking about how to go beyond Merkle trees using lattices, polynomial commitments and other fantastic beasts!
1
1
22
@VitalikButerin
How will Verkle trees affect state synchronization between nodes who are too far behind and up-to-date nodes?
The up-to-date nodes will have to spend time computing expensive Verkle proofs for the up-to-date state they send over, no?
1
0
21
Listen to
@ittaia
talk about consensus, from Part-Time Parliament, to PBFT, to HotStuff and beyond, with
@AnnaRRose
and
@fredhrson
on the Zero-Knowledge Podcast (
@zeroknowledgefm
):
0
7
21
Delighted to speak to you about ZK ar
@Aptos
and ZK in general
@edfrost_ur
! 🙏
Time flies so fast when you’re talking about things you love ❤️
Should’ve done 2 hours!
I was delighted to welcome
@alinush407
on the latest episode of Absolutely Zero Knowledge.
Watch as Alin unpacks the ZK use cases at
@AptosLabs
.
I've loved sharing my conversations with the ZK community... and all episodes will soon be on Spotify! 👀
0
1
14
1
6
22
Today I (almost fully) read: "Linear-map Vector Commitments and their Practical Applications" by Matteo Campanelli,
@13portocale
,
@CarlaRafols
, Alexandros Zacharakis and
@arantxazapico
()
1
4
21
Huge shout out to
@AnnaRRose
for creating the ZK podcast
@zeroknowledgefm
and building an amazing community around it! 🙏
Honored to be a part of it again. Previously, I mused about stateless validation:
Also, big thank you to
@nico_mnbl
for co-hosting!
I can't watch this 🫣, but I hope you do! 😄
In the podcast, I cover
@aptos
on-chain randomness () and keyless accounts ().
Oh, and there's a lot of talk about peppers, for some reason? 🌶️
cc
@perryjrandall
and
@aptoskent
4
9
31
1
1
19
Check out our new technique for computing all N proofs fast in the Pointproofs VC by Gorbunov et al. (
@sergey_nog
) () with a quick implementation here ()!
3
6
20
Check out
@bennypinkas
’s thread on our weighted DKG and weighted VRF constructions, the cryptography that powers
@Aptos_Network
’s *instant* on-chain randomness!
🧵Our new eprint report describes some technical details of building the new on-chain randomness service on
@Aptos_Network
.
This is joint work with
@sourav1547
,
@alinush407
and
@XiangZhuolun
.
See
More details ⬇️
1
8
43
0
1
20
Nobody likes complaints… especially in verifiable secret sharing (VSS) protocols!
Exited to share our paper on a new simple and efficient way to design Verifiable Secret Sharing schemes in both synchrony and asynchrony with support for dual-thresholds
Joint work with
@XiangZhuolun
@alinush407
@SashaSpiegelman
@bennypinkas
and Ling!
2
35
91
0
1
11
Every time I see a tweet for an
@aptos
keyless integration I will chug down a beer 🍺 to celebrate!
(No) mercy! 🙏
2
0
18
Our SCN'20 presentation on Aggregatable Subvector Commitments for Stateless Cryptocurrencies is up on YouTube: . This is joint work with
@ittaia
,
@VitalikButerin
,
@drakefjustin
,
@dankrad
and
@khovr
!
0
4
19
6. Because we (
@sourav1547
,
@bennypinkas
,
@XiangZhuolun
) just *love* solving hard cryptography problems!
Will be back with more technical details! :)
The randomness ROLL API tutorial by
@alinush407
is really worth a watch (it's a quick 11 minutes). But also here's a spoiler
0
1
10
1
2
18
If you want to read about the coolest signature scheme and its application, this blog post is for you!
Pointcheval & Sanders (PS) signatures can be computed directly over Pedersen commitments, are re-randomizable (together with the commitment) and are easily thresholdizable.
Decentralized thoughts on pairing-based anonymous credentials and the power of re-randomization - with
@alinush407
1
6
27
1
2
18
Check out
@Aptos
’s ZK circuit that powers Aptos keyless accounts, built by
@mstrakastrak
:
Very excited to share this with our ecosystem and the broader Web3 ecosystem!
We build in the open & we hope you do too! Surprise us with what you build!
0
2
18
Check out our new work with
@superaluex
and Zack Newman (MIT) on authenticated dictionaries with cross-incremental proof (dis)aggregation from hidden-order groups, with application to stateless validation and transparency logging:
1
8
18
Want to securely & efficiently bootstrap a threshold BLS signature scheme? Check out our new work w/
@ittaia
and
@bennypinkas
on scalable distributed key generation protocols + bonus scalable verifiable secret sharing + bonus new vector commitment scheme:
1
4
18
Tomorrow at 9:10am PDT at
@IEEESSP
I'll present a few steps "Towards Scalable Threshold Cryptosystems", with Robert Chen, Yiming Zheng,
@ittaia
,
@bennypinkas
, Guy Golan Gueta and Srinivas Devadas. Check out our blogpost(s) for the nitty gritty details:
1
4
17
If you’re trying to understand what a
#zeroknowledge
proof is, without understanding what an (NP) relation or language is, you won’t get very far.
This short-and-sweet article by
@nico_mnbl
will get you there:
1
4
16
Have you ever wondered what's a "cryptographic hash function"? Here's a few (decentralized) thoughts on it, with the help of
@ittaia
:
0
7
15
tl;dr: Your email account = your blockchain account
If you have ideas on bootstrapping Web3 blockchain accounts from existing Web2 accounts (e.g., Gmail, Twitter, GitHub, etc) *without* relying on extra trusted 3rd parties, take a look at
@_weidai
's thread below 🧵👇.
0
2
11
No PhDs are needed! 😄
These days, the cryptocurrency space *itself* is more than enough proof that cutting-edge cryptography work can be done by anyone: high school students, college dropouts, or undergraduates.
Amazing work all over the place! 🪄
This thread dives us into
@Aptos
Magic 🪄🌐
While challenging for those without a PhD or enough education, each try unveils deeper knowledge.
Investing time to enhance tech knowledge is worth it!
@alinush407
provides a window into deeper understanding!
0
5
22
1
0
16
Indeed, open sourcing ZK circuits is a must for two reasons:
1. It lets the community audit & improve our work
2. It allows for permissionless innovation
0
1
13
A step forward for smart contract security on
@Aptos_Network
!
0
0
13
They must be so happy to hear we use non-malleable Groth16 zkSNARK for keyless accounts, right?
Or because of the constant-sized shares in our weighted verifiable unpredictable function, used in randomness?
Or due the optimized low-degree testing in our PVSS?
I’ll stop… 😂
Tons of fun with
@northwesterncs
students &
@samirkhuller
visiting
@AptosLabs
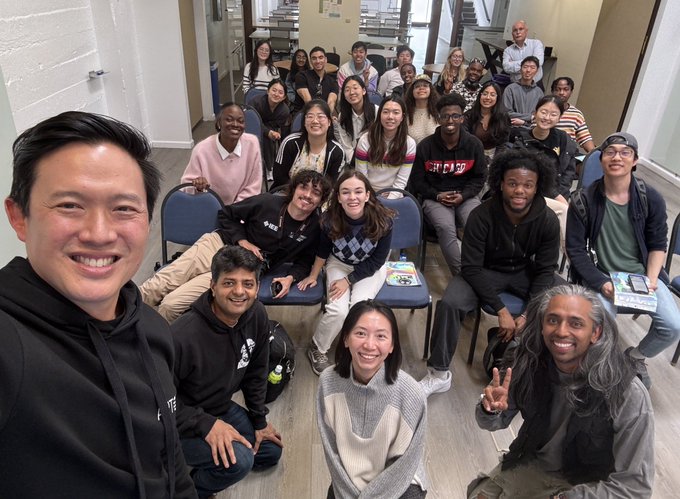
today. Thoughtful discussions. A bright future await!
7
13
124
1
0
10
If you want to learn more about this "test-and-abort" attack on randomized dapps, see our AIP for randomness APIs in Move:
Today's lesson on Move:
Ever wonder why functions are private or public? Let's go over the reasons you'll want to make them one way or another with a little chance game I like to call:
Dice roll
#DailyMove
2
18
75
0
1
12
Check out the *updated* Edrax paper by
@chepurnoy
,
@chbpap
and
@YupengZhang7
on stateless cryptocurrencies from vector commitments (VCs). It uses multivariate polynomial commitments and SNARKs to obtain a VC with constant-sized proofs:
1
4
10
Put simply into one figure: VSS with ACKs instead of complaints!
Systems that uses the complaint based sync Verifiable Secret Sharing for Distributed Key Generation, please check our VSS paper ! We describe a simple VSS that needs only one broadcast in the worst case.
@arpaofficial
@SkaleNetwork
0
0
8
1
2
11
We knew that an adversary who can compute DLs can break CDH.
This paper shows, surprisingly, that the opposite also holds on many SoTA elliptic curves (i.e., DL and CDH are equivalent assumptions).
The last sentence in the abstract lacks context & should probably be ignored.
@matthew_d_green
@StefanoMTessaro
@Leptan
@luca_defeo
@cronokirby
@EllipticKiwi
@mmaker
Why is everyone taking the cryptanalysis angle? This tells us that DDH and DLOG are the same in the curves we use. That's huge!!!! (Or am I an idiot and completely misunderstanding.)
6
0
14
1
0
10
🤓
ICYMI
@AptosLabs
Head of Cryptography
@alinush407
dives into Aptos Keyless and On-Chain Randomness on the
@zeroknowledgefm
podcast—give it a 👂👇
11
11
125
0
0
8
@cusma_b
@ittaia
@VitalikButerin
@drakefjustin
@dankrad
@Khovr
@Algorand
Indeed, Pointproofs are very cool! We relate to them in Sec 1.2. Real quickly though: (1) we precompute *all* proofs in quasilinear time (2) our proof updates have O(1)-sized update keys (3) our verification key is O(1)-sized and (4) our API accounts for (verifiable) update keys
0
1
9
Thank you
@AnnaRRose
and
@fredhrson
for having me and for digging deep with your questions! This was my first very first podcast and I had lots of fun!
🔊 This week,
@AnnaRRose
and
@fredhrson
chat with
@alinush407
a post-doc researcher at
@vmwareresearch
, about the concept of stateless systems. Specifically, they explore his work on stateless validation, why this would be desirable!
0
1
6
0
2
9
Today, I am thankful for Catalano-Fiore (
@dariofiore0
) vector commitments (CF VCs), which we recently used to build authenticated dictionaries (ADs)! So check out our new blogpost on CF VCs () and the ADs we built from them ()!
0
0
9
We suspected that PVSS-based aggregatable DKGs would be the cleanest to implement in the
@aptos
BFT protocol & should be efficient too.
The state-of-the-art was our EUROCRYPT'21 paper with
@kobigurk
,
@Daeinar
, Mary Maller, Sarah Meiklejohn &
@Giladstern_
:
1
0
7
Aptos randomness wouldn’t be possible without the Das PVSS, so hats off to you good sir!
This is built atop solid cryptographic and consensus foundations. It feels great to work on something that is getting deployed in the real world. Thanks
@Aptos_Network
for the amazing opportunity!
Stay tuned for the technical paper...
1
1
28
0
0
8
@bennypinkas
will be speaking about our new aggregatable publicly-verifiable secret sharing (PVSS) and verifiable unweighted functions (VUFs) constructions in the proof-of-stake (weighted) setting.
These schemes make *instant* on-chain randomness possible on
@Aptos
!
0
2
8
cc
@Ludacris
for confirmation
Perhaps Ludacris was misunderstood:
That by singing “Move b****, get out the way”, he was rejoicing about the Move language, and how it gets out of memory key resources via a type safe borrow checker
How else could he do 100 on the (information super)highway?
#WordOfMouf
6
1
25
1
0
8