Elliot
@ElliotKillick
Followers
3,558
Following
40
Media
6
Statuses
66
Security engineer and researcher | Elliot on Security
Toronto, Canada
Joined February 2021
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
#خلصوا_صفقات_الهلال1
• 295382 Tweets
ラピュタ
• 295053 Tweets
#AlnassrNeedsMidfielder
• 123503 Tweets
#金曜ロードショー
• 96087 Tweets
Gaudreau
• 91088 Tweets
NAMJOON
• 54820 Tweets
YINWAR OVER THE HORIZON
• 53564 Tweets
#พรชีวันEP15
• 48265 Tweets
#Mステ
• 39206 Tweets
#バルス祭り
• 37204 Tweets
CK WEDDING DAY
• 31797 Tweets
#笑うマトリョーシカ
• 26361 Tweets
ムスカ大佐
• 20529 Tweets
#ساعه_استجابه
• 18371 Tweets
CHERISH TWENTY WITH WONYOUNG
• 17624 Tweets
ブラックスワン
• 15154 Tweets
トパーズ
• 11505 Tweets
パズーとシータ
• 11396 Tweets
ロボット兵
• 10437 Tweets
Last Seen Profiles
I found out "C:\Windows\System32\WorkFolders.exe" (signed by MS) can be used to run arbitrary executables in the current working directory with the name control.exe. It's like a new rundll32.exe
#lolbin
but for EXEs!
10
658
2K
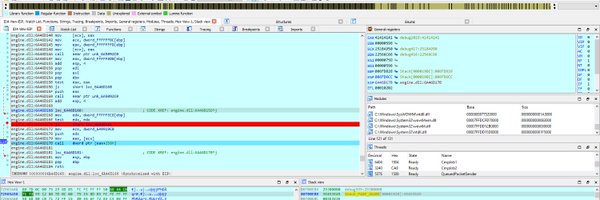
Perfect DLL Hijacking: It's now possible with the latest in security research. Building on previous insights from
@NetSPI
, we reverse engineer the Windows library loader to disable the infamous Loader Lock and achieve ShellExecute straight from DllMain. 🔍 Link in bio 🔗
15
302
836
🚀 Want to level up your Windows reverse engineering skills fast? Check out this newly published
#lolbin
RE methodology post! Uncover undiscovered lolbins in Windows right now! Link in bio 🔗
4
77
381
#lolbin
for hiding the CMD window so it runs in the background (signed by MS): DeviceCredentialDeployment.exe
1
11
32
@BiteFre4k
Will do! I recently found a real game changer of a lolbin that allows for background download, upload (probable, but still researching that one), AES encryption/decryption (!) and more all in a very legitimate context. I've yet to post it to LOLBAS but I'll keep you posted.
4
0
31
@ConsciousHacker
Hmm, well I don't currently have a blog platform. But, that definitely sounds like a good idea so I may just have to get one!
4
0
20
@Hexacorn
Yes, I did see your post for the older cmdln32.exe. You were very close but missing the /lan switch to make it work on the new cmdl32.exe! Also, I was luckily able to make it practically usable by denying delete permissions on the folder (and setting %TMP%)
1
0
20
@ChardeMashall
An unmodified Mimikatz being dropped to the disk will be detected no matter how you get it there. This is really for EDRs/XDRs that detect malicious use of lolbins. E.g. I'm aware that Trend Micro Apex One will instantly kill and flag on any certutil.exe that tries to download
3
0
11
@mariuszbit
My pleasure! Looking at DLL imports (using dumpbin and janky scripts), grepping for interesting UTF-16LE strings, and dynamic analysis with ProcMon were how I got most of my leads. There's definitely still much to discover!
0
0
11
@YoSignals
@NoobieDog
Oh, wow! I usually do a preliminary check to make sure my finding is new but I didn't come across your website. If you want, I could add your name and resource to the LOLBAS PR though.
0
0
7
Hey I'm back but now with a new
#informationsecurity
blog (), never before seen zero day exploits, and lots of new offensive security techniques & tools for you (also more new lolbins)! Expect all this and more in what's to come next...
0
2
10
@ChardeMashall
This is just a fun little example showcasing downloading Mimikatz. IRL, you would probably hook it up to your own malicious shellcode loader (with XOR/RC4 encyption) to bypass AV. (Then "load kiwi" from within Meterpreter for Mimikatz :) ) There are tons of them on GitHub ;)
1
0
10
@YoSignals
@NoobieDog
I went ahead and acknowledged you at the top of the list on the LOLBAS submission:
0
1
4
@SecuritySense
@ZephrFish
Same as the ones WorkFolders was executed with; this isn't a UAC bypass or privilege escalation vulnerability.
1
0
5
@Mitnick40306247
Well, it’s been a while. AVs have probably started putting out signatures to defend against this attack (although it’s still relatively undetected). Try obfuscating the command-line as shown here by
@Wietze
to evade detection:
0
1
3
@theglennbarrett
Yes, execute lolbins such as this one are usually useful for covert persistence mechanisms or to disrupt parent-child process relationships EDRs are known to alert on.
0
0
3
@0gtweet
Yeah, I saw that option too in my RE. Unfortunately it didn't seem to have any effect :/
1
0
2
@cyb3rops
@virustotal
Fair enough. Like I said in the post, JavaScript obfuscation is very common to do legitimately on the web. So, for quick and dirty it's easy to blend in
0
0
1
@olafhartong
@Wietze
@gpunktschmitz
@maarten_goet
Yeah, that tends to be the problem with publishing your tradecraft, it gets burned... :/ But at least for now it can be used freely before it starts getting added to detection rules.
1
0
1
@0gtweet
Yes, it took inspiration from your amazing tweet 😂 I was looking for a direct download to the Mimikatz EXE when I remembered the link you used lol
1
0
1
@AbeSnowman
@Wietze
Yep, I reverse engineered WorkFolders. This is exactly what it does; just a simple wrapper binary that calls ShellExecute() to open control.exe with the arguments "/name Microsoft.Workfolders".
1
0
1
@JacobDjWilson
The ServiceName parameter can be anything you want. I just set it to WindowsUpdate for extra stealthiness ;)
0
0
1