pilvar
@pilvar222
Followers
937
Following
380
Media
82
Statuses
280
Computer Science student @EPFL | CTF player @polygl0ts and @0rganizers | ECSC Swiss National Hacking Team @TeamM0unt41n | Part-time bug hunter 🐞
Joined October 2013
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Mbappé
• 654002 Tweets
Carvajal
• 422074 Tweets
Real Madrid
• 290905 Tweets
#EveryWONWOO_Day
• 182112 Tweets
Amber Rose
• 164492 Tweets
#Jimin_Who
• 163882 Tweets
WHO IS COMING
• 151731 Tweets
Jack Black
• 143187 Tweets
JIMIN IS COMING
• 140990 Tweets
Gibraltar
• 131332 Tweets
Hala Madrid
• 93215 Tweets
WHO MV TEASER
• 84120 Tweets
Prime Day
• 84048 Tweets
#남신_그러나_고양이_전원우생일
• 74596 Tweets
#西園寺さんは家事をしない
• 73568 Tweets
Haddad
• 62395 Tweets
Walker
• 58866 Tweets
Bronny
• 42871 Tweets
Tenacious D
• 41668 Tweets
wonu
• 34504 Tweets
土井先生
• 34307 Tweets
Yoro
• 33615 Tweets
Kyle Gass
• 32701 Tweets
THANK YOU HAECHAN
• 31468 Tweets
アルカディア
• 27373 Tweets
Virgen del Carmen
• 26838 Tweets
WHO IS MY HEART WAITING
• 23556 Tweets
PARK JIMIN
• 18062 Tweets
Joe Bryant
• 16154 Tweets
KP.3
• 15380 Tweets
ピーナッツくん
• 15280 Tweets
インライ
• 13409 Tweets
レイエス
• 11331 Tweets
Matt Walsh
• 10341 Tweets
Last Seen Profiles
Pinned Tweet
My talk for
@1ns0mn1h4ck
is now available on youtube! Hope you'll enjoy it! :D
5
55
208
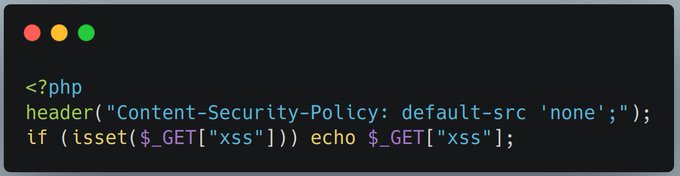
🧵[1/9] Time to publish the solution to this challenge! The goal of this challenge was to find an XSS while avoiding it being blocked by the CSP sent by the PHP header() function. Let's dive into it!
4
46
211
1) This is not a wordpress vulnerability, but a plugin's one
2) This is not a 0day, it's already been reported and fixed since September
3) If it was, you would be disclosing it unresponsibly
Yet, you received tons of likes and RT by straight up lying 🤡
we are happy to share a 0day we have found on wordpress login page allow un-auth cross site scripting (xss)
#bugbountytip
#BugBounty
#ItTakesACrowd
40
284
1K
5
12
79
Yay, I was awarded a $2000 bounty on
@Hacker0x01
!
#TogetherWeHitHarder
Big thanks to all absurd XSS black magic fuckeries I've seen in various CTFs, really helped be getting my exploit to work :D
5
3
70
Imagine creating a web chall using the sanitizer API, then Chrome just fucking removes it with its new release 3 days before the CTF starts 💀
Anyway, come play LakeCTF, it's this weekend and I've prepared 2 challenges for it :) (and go follow
@polygl0ts
!)
0
2
49
blooded two challs + first to full clear web, guess I'm the best web security company out there lol
#BusinessCTF23
3
2
41
Can't believe this just happened 🤯
@msftsecurity
if you need to learn hacc plz hire me ty
#BusinessCTF23
4
1
34
@terjanq
🧵[6/9] This means that if we have, for example, a request containing more than 1000 GET parameters, a warning will be sent, and the CSP header won't! Trying this solution () on remote, we can pop an alert!
1
3
31
I find pentesting Active Directory to be hard because of all of the tools, commands, and techniques you have to keep in mind, but
@orangecyberdef
's mindmap is very nice and it helped me a ton of times!
I can only recommend putting it in your bookmarks :)
2
6
22
Last year I cried over a
@PlaidCTF
web challenge all night while being super sleep-deprived... But this year, well exactly the same thing happened, but at least it's solved now 🫠
1
1
22
OMG this explains so much things!! I wonder how I missed this info all my life!
Thanks
@WebSecAcademy
! :D
0
3
20
Met up with
@vie_pls
and
@_under_hill
today! They were in Switzerland for the week, couldn't miss the occasion to hang out with them :)
0
0
18
@terjanq
@hash_kitten
@haqpl
@SecurityMB
@arkark_
@satoki00
@Satoooon1024
@c3l3si4n
@rootaux
@ankursundara
@Strellic_
@IcesFont
@sushicomabacate
@darinmao_
@blueminimal
@realansgar
@BrunoModificato
@taramtrampam
@SasukeOurad
@0x22sh
@frevadiscor89
@ixSly
@kolokokop
@damned_me_
🧵[9/9] I hope you enjoyed the challenge! If you did, you might want to check out the talk where I presented it along with other techniques, I will post the link on my twitter as soon as the recording is published!
1
1
16
Awesome writeup by
@xanhacks
for my LakeCTF challenge GeoGuessy, including the two unintended as well as the intended solution!
Go check it out it's very nice :)
1
0
15
Hey that's us on the first pic! 😄
🏆 Reliving the highlights of the Cybersecurity Rumble 2023!
Again, congratulations to our winners:
🥇 p0lyflag
🥈 __watermelon_chk_fail
🥉
@C_S_C_G
A big shoutout to all teams, volunteers and our amazing partners, you made this event unforgettable!
Until next year! 🚀
0
1
4
1
0
14
@terjanq
🧵[5/9] At this point, it is necessary to dive into php internals, and look for a way to create warnings before the php page code is executed. Looking at the http parameters processing, we can find that there are multiple cases where warnings are created, here are three examples:
1
2
14
Yay, I was awarded a $500 bounty on
@Hacker0x01
!
#TogetherWeHitHarder
I honestly forgot about this report, what a great surprise :D
4
0
12
Not a first blood, but hey at least I get the $100 swag card :p
Thanks for these cool challs
@hackthebox_eu
! Am enjoying them a lot :)
#OperationTinselTrace
2
0
12
Just completed
@hackthebox_eu
's Blockchain challenges! That was quite fun, looking forward to start solving some in CTFs :)
2
0
12
@intigriti
Easy, unsubscribeUser is not defined. The dev forgot to include the necessary js code for this feature to work, making the company vulnerable to GDPR fines 😎
0
0
10
happy ending
@pilvar222
1. Why do you have a sticker of my face.
2. Are you coming to defcon I can get you another one :P
1
0
1
0
0
10
Awesome writeup, thanks for sharing it
@MaitaiThe
:)
After around 20 days i've successfully completed the writeup for the last web chall of
@LakeCtf
finals. Even though i was not able to solve it, i've learned so much.
I would like to thank
@pilvar222
really much for dealing with me during all the process.
2
9
37
0
0
8
Congratz to the qualified teams! :)
And that's a wrap for LakeCTF Quals 2023!
Congratulations to our 9 qualified teams!
🥇
@dicegangctf
🥈 ISITDTU
🥉
@fibonhack
See you all in Lausanne for the finals! 😄
PS: The 10th spot for the finals can still be won as the first prize of
@1ns0mn1h4ck
's CTF academic bracket!
0
6
29
0
0
8
@CyberTeamItaly
@0rganizers
@CyberSecNatLab
@CyberChallengIT
@openECSC
@enisa_eu
Once more, the maestro of Italian cinema, CyberTeamItaly, gives us a heady mixture of suspense, stormy melodrama, and theatrically dramatic characters. It is safe to say that we've found this year's winners. 9.5/10
0
0
7
@kevin_mizu
Ayy! Thx for the chal :)
Now is time to send you a weaponized solution and pwn your blog😈
1
0
7
🧵[3/9] This issue can be abused by forcing a page to send content before the header() function, thus preventing the presence of a potentially important security header. This has already been used in CTF challenges, notably in baby-csp by
@terjanq
1
1
6
@zeyu2001
The story repeats lol
Have the same feelings sometimes. Especially rwctf style challs where you need to find a 0day in a repo. Just feels like work it's not very enjoyable and it's tiring
1
0
6
@terjanq
🧵[7/9] This solution is only one among many. From the different solutions I've seen, some also used the maximum length of the parameters or files, and I wouldn't be surprised if many others are still unexplored ways to have warnings! In any case, big props to the solvers!
1
1
6
Awesome looking tool for finding well-hidden client-side vulns! Can't to try it out! 😄
0
0
6
Just discovered this version of DOM clobbering while reading
@Strellic_
's very cool write-up of his own challenge "AnalyticalEngine" . Can't wait to see the new challenges he made for corCTF 2022! 😁
1
0
5
@OctagonNetworks
The fumction is only used to prepend backslashes to certain characters such as quotes. However, here, you don't need these to continue the query, you can simply uses spaces, subqueried, etc...
1
0
4
I love programs like these!
Compensate for efforts put into a duplicate is probably the best way a program can show its consideration for its hackers ❤️
(Also helps us keeping sanity 😅)
#BugBounty
0
0
4
@LiveOverflow
@Ox4d5a
Hi, here are the 340,282,366,920,938,000,000,000,000,000,000,000,000 ipv6 adresses I'd like to scan :)))
1
1
3
@Shadowwws7
Heh, it's not *that* ephemeral, when I'll be old I'll hang all of my laptops on the wall and it'll give me great memories :)
1
0
3
```rb
fun fact:
discord's tweet integration supports text formatting!
```
__we can even mention other users!__ <
@229923319829364736
>
1
1
3
@garlic0ne
It's the default port for Burp Suite's proxy, so either the chall or the proxy fails to run until you change and restart it, which is quite annoying 😅
0
0
3
It was a really fun experience, thanks everyone for participating! :)
LakeCTF Qualification has ended ! Congratulations to the top 10 teams (7 Academic teams and 3 Non-Academic) that qualify for the finals
@EPFL
the 5th of November.
1st.
@dicegangctf
2nd.
@flagbot_eth
3rd.
@SuperGuesser
@ICepfl
#EPFLIC20
0
11
52
0
0
3
@terjanq
🧵[4/9] However, this technique has certain limitations. It requires either sending data before header() via functions such as echo, or to have warnings created by the code before header() while display_errors is enabled. This challenge requires us to surpass these limitations.
1
1
3
@albinowax
If you're still looking for some ideas, I recently learned about TLS poisoning, and I think it could have more potential by digging further! :)
@joshmdx
, the researcher that discovered this, had some suggestions here: (timecode). Good luck! :D
1
0
3
@cyan_pencil
I thought of it, but I'm unfortunately unable to do so for reasons beyond my control 😤
0
0
3
@BroodaShah
@RealTryHackMe
@hackthebox_eu
@PentesterLab
Almost there! Honestly impressed by your commitment, you're off to a great start for a prodigious career! :D
1
0
2