Gynvael Coldwind (@gynvael.bsky.social)
@gynvael
Followers
38K
Following
11K
Media
471
Statuses
6K
security researcher/programmer/director @ HexArcana Cybersecurity GmbH ⁂ @pagedout_zine ⁂ @DragonSectorCTF ⁂ https://t.co/ShG2c5As1K ⁂ ex-Google ⁂ he/him
Zürich, Switzerland
Joined July 2009
So an AMD engineer and 2 Google engineers walk into a bar. and write an article about how "Hello World" in #Python works. The article turns out to be 26 pages. From Python, through C, WinAPI/Kernel, font rendering, to GPU. Enjoy!.
12
255
880
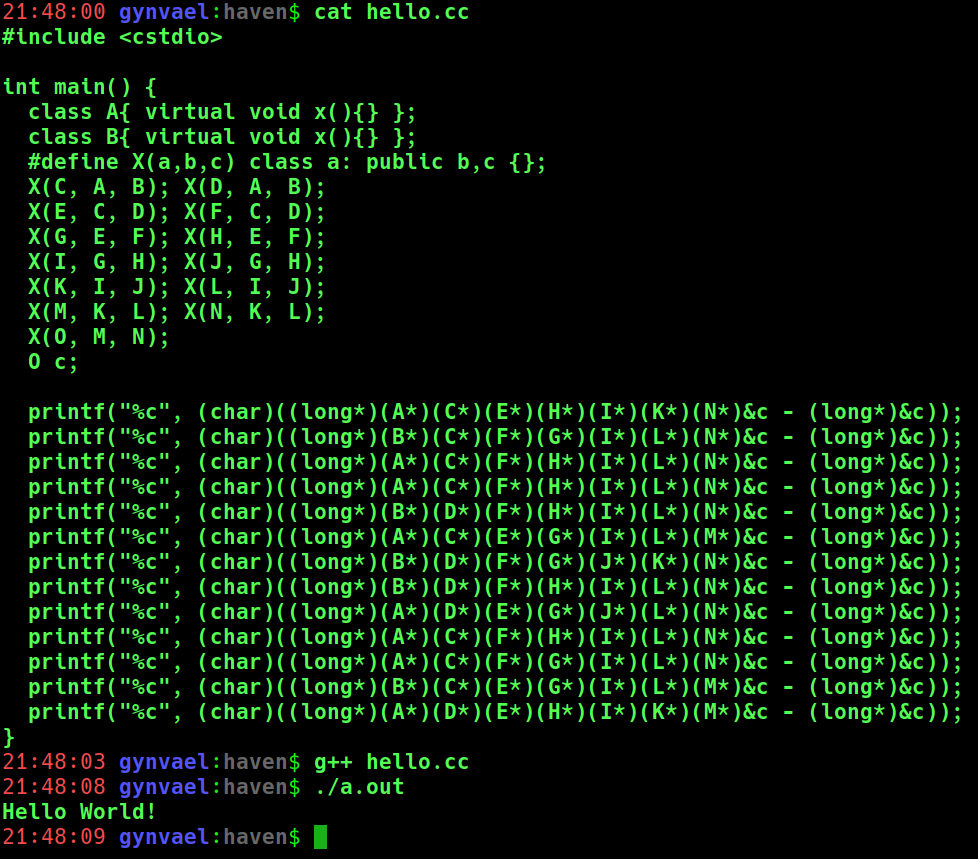
Python was too hard so I've switched to C++. Here's my first "Hello World"!
My first program in Python! I still find this syntax a bit confusing with no { } etc. def main(. line0: print("Hello World!"),. line1: print("What's your name?"),. line2: (x := input("Name plz: ")),. line3: print(f"Your name is: {x}").):. pass
21
47
733
TIL from @q3k and @marcan42: wget saves downloaded file's source URL (and sometimes referrer) in extended attributes. This includes the cases where the URL has a user/password in it 🙃. $ getfattr -d -m - test.user.xdg.origin.url="https://user:[email protected]/".
7
273
617
Yesterday's "Breaking "DRM" in Polish trains" talk by @dsredford / MrTick / q3k was one of the best investigative reverse-engineering case studies I've seen. It's a must watch.
5
120
428
Service announcement:.I've got the so-called long-COVID (3 months in at this point), so currently all my projects (YouTube livestreams, @pagedout_zine, etc) are put on hold until I get better. Sorry!.
118
14
426
Paged Out! #2 (Nov 2019) is out! And it's free to download :).This issue has 55 articles in 11 categories:.Programming.OS Internals.Assembly.Operating Systems.GameDev.Electronics.Security/Hacking.SysAdmin.Reverse Engineering.Algorithms.Writing Articles
4
211
406
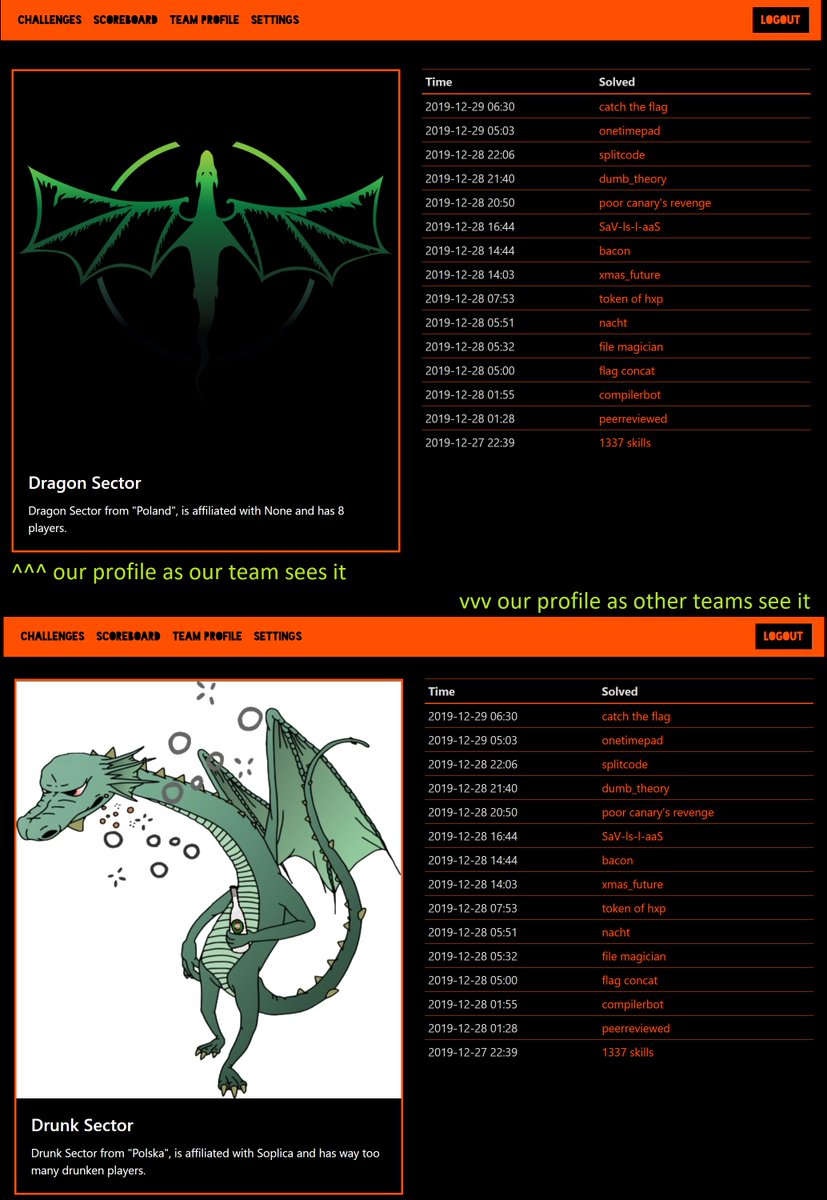
<@yyyyyyy> congrats to Drunk Sector for finding out about their team name only 40 hours into the competition!. I don't even 🤣🤣🤣. #TrolledAtCCCCTF #IDontEven #Potatos
5
35
323
A pretty amazing opportunity to see (and compare RE methods of) 4 security youtubers/streamers as they go against an upgraded Google CTF 2018 BQ RE challenge - Kudos to ReverseiT & @MurmusCTF @Zanidd @_johnhammond @LiveOverflow !.
4
60
247
I'm going to do a longer stream tomorrow (expected 4h) to solve all the challenges from Google's CTF Beginners Quest 2019. There are 13 challenges, some of them having two flags. Should be fun :).#googlectf
4
62
222
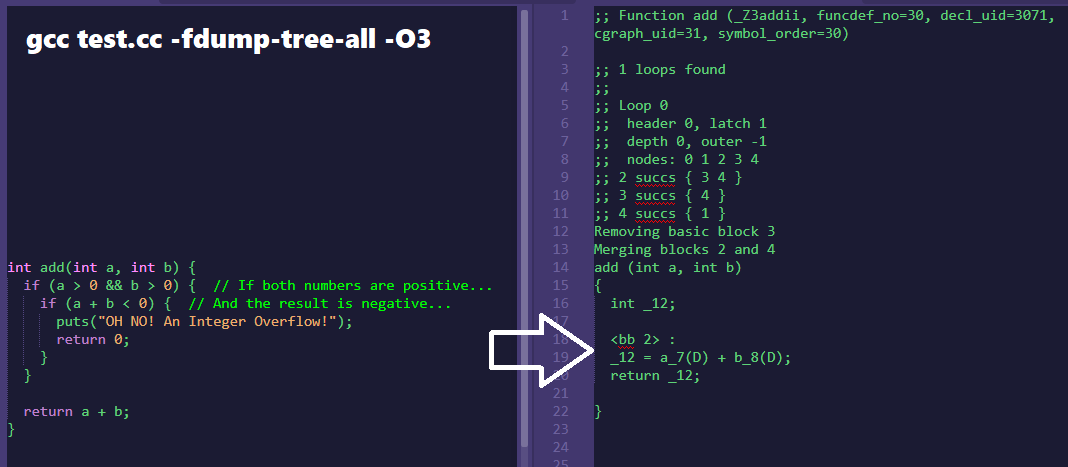
Current collection of cursed operators in various programming languages (from various sources). New submissions welcomed!. Featuring at least #javascript #python #c and #cpp, but most of these "work" in other languages too.
16
50
218
My weird php://filter/convert.iconv solution for Cool Storage System stage 2 of @1ns0mn1h4ck CTF Teaser:.Pretty crazy if you would have asked me ;).
7
104
188
New into CTFs? Full-format ranked CTFs look scary? Or just looking to have fun and learn something? Try the Beginners Quest @ Google CTF Quals :).#GoogleCTF.
2
80
180
In the topic of #GoogleCTF - I will be showing how to solve all of the Beginners Quest challenges on a special livestream tomorrow (Tue), 8pm CEST:.(recording will be available).
4
72
177
The final match of Hackceler8 (GoogleCTF Final Event) is now over!.1st + $3k. PPP (@PlaidCTF) .2nd + $2k. I Use Bing.3rd + $1k. pasten (@pastenctf).4th + $500. TFNS (@FlatNetworkOrg).Congratz!.Our experimental speed-hacking competition is now over. Videos soon! GG :)
3
24
175
This reminded me of when early in my career I reported a vulnerability in Starcraft map format (potential RCE) to Blizzard and in reply got advice to install an anti-virus and a firewall 🙃. Reporting vulnerabilities is an art of its own 😆.
Vulnerability Disclosure:. Me: Hi, do you have a contact to discuss vulnerabilities in your product?.Them: Na fam, chill! We got this!!. 🤨
6
18
171
Paged Out! #4 has some amaazinggg stuff inside. And it's free. Like free free, you don't even have to give out your email address :).
3
49
167
Recording of solving all (19) challenges from #GoogleCTF Beginners Quest is up: (description has timestamps for all challenges + a link to the github repo with scripts/notes).
1
65
162
Service announcement update:.Still having post COVID syndrome (9 months in at this point). All projects (YouTube livestreams, @pagedout_zine, etc) are still on hold. Sorry!.
28
3
158
@LiveOverflow @svblxyz @KodyKinzie @YouTube Nah, our channels will be fine since we only show how to bypass INsecure computer systems ;). On a more serious note I'll take a look when I'm back from vacation.
1
7
140
Congratz to @EatSleepPwnRpt for top1 in Geneva! Good Game, Well Played! :).@DragonSectorCTF finished 2nd this time (yay!), with @p4_team third (well done!). Kudos to @1ns0mn1h4ck for making yet another great CTF :)
3
34
150
Members of my CTF team & the SPS train repair company will meet NEWAG, the train manufacturer, in court on Wednesday (you might remember the 37C3 talk; link in reply). The lawsuit was initiated by NEWAG, but, according to reporting, counterclaims were filed by SPS as well. 1/3.
Just two days left until the first hearing in Newag's lawsuit against us (Dragon Sector members) and SPS. In case you've missed it, we're being accused of infringing upon Newag's intellectual property and unfair competition. More details:
6
30
142
Hey @github, what's the reason that you're allowing an account impersonating me, abusing my copyrights+trademarks to stand active for over 11 days from it being reported to you by multiple parties?. Is this the typical pace you're dealing with abuse?. Ctx:
If you have received an e-mail from gynvael@coldwind.dev (note .dev, not .pl) then it's a social engineering attempt by an unknown party. I was notified that at least several Polish security researchers were targeted. Please let me know if you got an e-mail from that domain too.
5
33
140
If you have received an e-mail from gynvael@coldwind.dev (note .dev, not .pl) then it's a social engineering attempt by an unknown party. I was notified that at least several Polish security researchers were targeted. Please let me know if you got an e-mail from that domain too.
5
42
136
Absolutely amazing article on ZIP files by @hansw2000, with in-depth description of the compression algorithms and a step-by-step example implementation!.
0
45
130
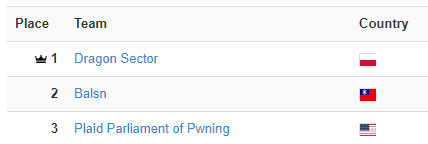
Our CTF team placed top1 @ in 2019!.That's the 3rd top1 in the history of our team, and I'm really proud of our team's accomplishments!.Kudos to our captain valis, our vice-captain @dsredford, all the team members and all guest players that played with us!.
2019 was a great year for Dragon Sector!.🏆1st place at global ranking for the 2nd year in a row & 3rd time in the history of our team.🥇1st place at 2 CTFs.🥈2nd place at 5 CTFs.🥉3rd place at 5 CTFs.💻And also organized a well received Dragon CTF 2019!
3
4
133
This case is hilarious ;).It's an 0-day. When SSD tried to report to @NETGEAR / @Bugcrowd, whoever handled the report seems to have ???misread the newest firmware version for R7000 as 1.3.2.134???, and the bug affects only 1.0.11.116. Problem is, 1.0.11.116 is the newest fw🙃.
New advisory is now out!. The Nighthawk R7000 is a popular Netgear router, with over 50,000 positive reviews on Amazon. Find out how a vulnerability in NETGEAR R7000 allows an attacker to run arbitrary code without requiring authentication.
1
36
122
This! The "Reverse Compilation Techniques" thesis by @criscifuentes was one of two main resources I've used when learning reverse engineering (the other was "Reversing: Secrets of Reverse Engineering" book). Definitely recommended reading :).
A sometimes lost fact, but the entire field of decompilation using compiler and program analysis techniques that we know as standard practice today as seen in IDA Hex Rays and Ghidra was invented by @criscifuentes and her thesis on the DCC decompiler in 1994.
0
23
129
This idea is absolutely barbaric and just gruesome. Folks, I am a vulnerability researcher. I stare at the screen the whole day looking at code. And you want me to do THIS?! The whole idea is bound to just bring pain and suffering to people. I'm fine with the boxing part though.
@hackthebox_eu ok, hear me out. "Hack The Boxing". It's like Chess Boxing, but we alternate between boxing and solving a HTB machine. I just thought up the concept, but can't claim credit for the name.
5
8
131
Finally reached 10k subs on my English YT channel! :).Thank you for your trust! (though seriously, keep verifying what I say).And kudos + big thx to my livestream team for helping me out: @foxtrot_0x4fult @KrzaQ2 @disconnect3d_pl @masakralol and maryush :).
3
16
126