Kévin - Mizu
@kevin_mizu
Followers
3,168
Following
670
Media
35
Statuses
734
Vulnerability researcher 🐛 | CTF with @HexagonCTF , @rhackgondins 🦦 | Team FR 2023 🇫🇷 |
Joined May 2017
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Lewis
• 622136 Tweets
#BritishGP
• 367540 Tweets
Macron
• 222693 Tweets
#ElectionsLegislatives2024
• 193097 Tweets
Jordan
• 156331 Tweets
Amerix
• 154714 Tweets
Le NFP
• 130409 Tweets
Feds
• 130112 Tweets
Melenchon
• 99590 Tweets
EMMANUEL
• 98543 Tweets
Ferrari
• 68155 Tweets
Coco
• 67565 Tweets
Lando
• 67128 Tweets
Norris
• 62952 Tweets
McLaren
• 58359 Tweets
Hanouna
• 55330 Tweets
Vive la France
• 49962 Tweets
ON A GAGNÉ
• 44848 Tweets
Nyakundi
• 39077 Tweets
Pleure
• 35375 Tweets
ON L'A FAIT
• 30805 Tweets
Ombachi
• 29243 Tweets
Margot Robbie
• 27776 Tweets
National Rally
• 27483 Tweets
Gaitho
• 25585 Tweets
Gabriel Attal
• 21249 Tweets
U-Haul
• 20706 Tweets
Hollande
• 18140 Tweets
Le Pen
• 18125 Tweets
EL PARQUE IS COMING
• 17589 Tweets
Nuevo Frente Popular
• 15998 Tweets
New Popular Front
• 13412 Tweets
Poutou
• 12763 Tweets
UK and France
• 12163 Tweets
Vive la République
• 10848 Tweets
Last Seen Profiles
I'm glad to finally present my research about "Abusing Client-Side Desync on Werkzeug" at
@sstic
2023 📜
Research paper is available here:
Slides are available here:
12
145
461
For the
@GrehackConf
2023
#CTF
, I made 2 hard
#web
challenges 🚩
They were about:
[1] Python class pollution to RCE on Flask application
[2] HTTPOnly cookie leak due to Werkzeug improper Cookie parsing
Detailed writeups 👇
[1]
[2]
1
62
218
I've finally finished my writeups for
#FCSC2024
, which covered:
- Nginx X-Accel-Redirect file read
- Werkzeug error-based request smuggling
- HTTP/1.1 and HTTP/0.9 browser confusion
- Connection: close bypass via Expect: 100-continue
- ...
Link 👇
1/2
2
36
182
I think it's time for a solution ⏰
To solve this challenge, you had to abuse the DOMPurify namespace misconfiguration to trigger an XSS this way 👇
Solution link:
1/6
4
38
163
Yesterday, I did a talk on
@rootme_org
about
#electron
security. In this talk I also presented a step-by-step writeup of the research leading to finding the XSS to RCE vulnerability on
@drawio
last summer (CVE-2022-3133) ☀️
You can find the slides here:
2
38
97
Really proud of those bypass/mXSS variations. They involve some cool second-order DOM Clobbering and a new mutation gadget that I would like to call the elevator x)
1/2
DOMPurify 2.5.3 and 3.1.3 were released, covering a range of attack variations relating to nesting-based mXSS.
Thanks again to
@kevin_mizu
&
@ryotkak
for the invaluable help with finding new variations & verifying latest fixes 🙇
1
22
119
5
14
93
I think it's time for a solution ⏰
TL;DR
- Eventlet normalizes - to _ in header keys.
- The Fetch spec blocks Transfer-Encoding but not Transfer_Encoding.
- Bypass tracking policy on Firefox using open().
Detailed writeup 👇
1/2
2
25
92
👀
As expected, two variations of the so far known mXSS attacks have been spotted and new DOMPurify releases are ready to fix those.
Many thanks to
@kevin_mizu
and
@hash_kitten
for spotting and reporting those 🙇
2
30
157
4
3
84
Challenge time is now over ⏰
TL;DR
- HTML injection
- Axios DOM Based CSPP
- Axios CSPP response overwrite gadget
- jQuery DOM Clobbering + CSPP selector overwrite gadgets
- Setting src attr to "javascript:" for each HTML node ➝ XSS
Detailed writeup 👇
0
13
79
Challenge time is now over, I hope you've liked it! 😁
TL;DR
- mXSS via client-side / server-side confusion
- auto download to store the payload on file://
- puppeteer bot without SOP ➝ devtools (CDP)
- open file:// ➝ leak the flag
Detailed writeup 👇
0
23
79
This is why I probably should stop reporting issues to the Werkzeug repository…
I've finally finished my writeups for
#FCSC2024
, which covered:
- Nginx X-Accel-Redirect file read
- Werkzeug error-based request smuggling
- HTTP/1.1 and HTTP/0.9 browser confusion
- Connection: close bypass via Expect: 100-continue
- ...
Link 👇
1/2
2
36
182
5
8
73
👀
[ECSC 2023 🇪🇺]
L'équipe de France s’envole dans une semaine en Norvège pour l’
#ECSC2023
! 🇫🇷 🔜 🇳🇴
Une présentation des hackeurs éthiques de l'
@ECSC_TeamFrance
s'impose🕵️
Envie d’en savoir plus ?➡️
👀
@enisa_eu
#ANSSI
#CTF
#TeamFrance
#CyberMois
1
31
105
5
5
70
My first monthly
@intigriti
challenge is now available 🔥
Will you be able to solve it? 👀
⏰ It's CHALLENGE O'CLOCK!
👉 Find the FLAG before Tuesday November the 7th!
👉 Win €300 in SWAG prizes!
👉 We'll release a tip for every 100 likes on this tweet!
Thanks
@kevin_mizu
for the challenge! 👇
5
17
227
1
6
69
Challenge's time is over ⏰
To solve it, you had to take part of the fact the it is possible to clobber a form using the following notation 👇
1/6
1
9
55
My writeup for the march
@intigriti
#XSS
challenge :
Thanks
@0xGodson_
and
@BrunoModificato
for the quality of the challenge 🙏
1
12
51
I really enjoyed doing the
@MidnightFlag
's qualification with my friends:
@PerceSecu
,
@voydstack
and
@Nishacid
(Maybe even more because we ended first :p)
Thanks to all the challenge makers 🙏
My writeups are available here:
C'est terminé pour les qualifications de cette troisième édition du Midnight Flag CTF !
Merci à tous pour votre participation, nos partenaires et aux personnes ayant participé au live :
-
@AirbusCyber
-
@DGA
- @/DGSE
-
@rootme_org
-
@BZHunt1
-
@ESNABretagne
-
@ESNHACK
-
2
6
40
3
7
50
This week, I solved an interesting challenge made by
@0xItarow
at
@_barbhack_
🌞
It was about RPO abuse on a file upload feature!
You can find the writeup here: 🎉
1
20
48
#YogoshaChristmas
CTF is over and I ended 2nd over 92 users 🎉
You can find my
#writeups
here:
Congratulations to all the other challengers! 👏
3
5
44
GG to all the solvers! However, no one solved it in the intended way :p
Before giving my solution, I'm extending the challenge for another week with a fixed version!
If you find the solution, please send me a DM 📮
The challenge is accessible here 👇
2
7
44
I'm really proud of this one. It's not an easy one, but I find the final chain super interesting!
If you have some time, please take a look 🙏
⏰ It's CHALLENGE O'CLOCK!
👉 Pop an alert before Tuesday January the 15th!
👉 We'll release a tip for every 100 likes on this tweet!
👉 Thanks
@kevin_mizu
for the challenge! 👇
10
26
194
1
5
41
We've made the web challenges with
@BitK_
, if you have some times, come take a look 🚩
Can't wait to see how many times it will take someone to clear the category 👀
#FCSC2024
🐔 la compétition est ouverte !
📢 Jusqu’au 14 avril, résolvez un maximum d’épreuves : crypto, reverse, pwn… pour gagner votre place au sein de l’
@ECSC_TeamFrance
qui représentera la France à l’ECSC.
🚩 RkNTQ3tnbCZoZiF9
➡️ À vous de jouer :
3
32
58
4
7
41
Last week, I organized with friends the
@ctf_esaip
, for this occasion, I made 5 web challenges 🚩
They were about mXSS, subdomain takeover, prototype pollution, OAuth... 🔥
I started to write my writeups, they can be found here: 🕸️
1
10
38
Last week, I created 3 web challenges for the
#10kCTF
organised by
@rootme_org
. 🚩
They were about: URL parsing confusion, SQLi in prepared query and HTML sanitizer bypass!
You can find the writeups here:
2
5
37
I hope that you will like them 😁
Our contributors have struck again!! 5 new Web-Client challenges are now available on the
#RootMe
and Root-Me Pro environments.
Thanks to
@kevin_mizu
for his remarkable work 👏!
Good flag to all! 🚩
1
4
19
1
3
32
Sad de pas avoir pu être sur la photo mais, tout de même content de notre résultat 🎉
Merci aux créateurs de challenges et à la
@_barbhack_
pour le CTF 😁
2
1
27
All done – our live
#BugBounty
at
@nullcon
Berlin has just come to an end! Many thanks to our partner
@otto_de
for your trust, a big round of applause to all the hunters and special shout out to our top 3:
@hanno
Noxious and
@cWaveSoftware
👏
Here is
1
11
59
0
0
27
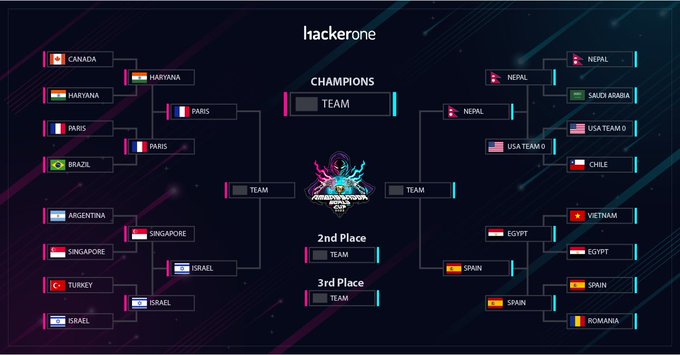
🇫🇷 🔥
The results are in! 📊
The four teams moving on to Round 4 of the
#AmbassadorWorldCup
are
#TeamParis
🇫🇷,
#TeamIsrael
🇮🇱,
#TeamNepal
🇳🇵, and
#TeamSpain
!🇪🇸
Congratulations to all AWC teams for the incredible teamwork and effort put into protecting our AWC partners. 🙌
32
61
308
0
2
26
I'm really proud to announce that 2 of my challenges have been released on
@rootme_org
🔥
They introduce about DOM Clobbering and XS Leaks vulnerabilities🌐
You can find them here:
-
-
0
4
25
It was fun looking for bugs with
@ryotkak
,
@hash_kitten
,
@joaxcar
,
@TheGrandPew
and
@IcesFont
😁
As always, thanks to
@cure53berlin
for the reactivity 🙏
2/2
4
0
25
@Rhynorater
The same tricks have been used by
@wir3less2
back in 2022 to bypass Amp4Email, if you are interested:
0
3
23
Hello👋
Pendant le CTF web de l'
@EuCyberCup
, avec
@Ooggule
et
@FeelProud_sec
, nous avons obtenu le flag du 2ème challenge "Panid" d'une manière non attendue, vous pouvez retrouver le writeup ici :
PS: Merci à l'admin pour le flag :)
1
2
22
@intigriti
As the payload it directly reflected from PHP to a JavaScript string, it is possible to use encoding notation to bypass PHP htmlspecialchars function 😁
For example, the following payload should makes an alert:
\x3cimg src=x onerror=alert(1)\x3e
0
2
21
@intigriti
There is definitely an SSRF vulnerability, but if I'm not mistaken, recent Chromium versions no longer allow the about:blank page to frame the file:// wrapper. So, it shouldn't be possible to leak local files 🤔
2
0
20
@Rhynorater
@MtnBer
Thanks for sharing the extension! If anyone is interested, it can be found here: .
Btw, I'm working on new features that will allow, for example, hooking selectors occurring after an innerHTML. This would be useful for leveraging sanitized HTML inputs :D
1
5
18
If you are doing bug bounty you should definitely check out
@Icare1337
's research on LibreOffice 🔥
0
1
18
@pilvar222
This is a nice trick! If you are interested,
@terjanq
have made a challenge / article about it:
I also found something equivalent on drawio using a restrictive JSONP endpoint to bypass a CSP:
1
2
16
@sudhanshur705
In case cookies are set to SameSite=Lax, you could abuse the fact that iframes load only SameSite=None cookies while loads both SameSite=None and SameSite=Lax 😁
1/2
1
1
15
@yeswehack
The vulnerability describe in the snippet is about RCE via custom python library overwrite. In fact, the upload features does not check if the file exist and didn't sanitize the filename making possible to path traversal.
1
0
15
@sudhanshur705
@gregxsunday
One of the biggest problems with HTML injection during PDF generation is that if it is sanitized, you can't see what happens during the PDF generation process.
By using <plaintext>, you can get the raw HTML printed as text in the output :D
2
1
14
@Sonar_Research
This challenge is about path traversal to template overwrite to RCE.
In fact, it is possible to create a user which is called "../templates/error.html". This will cause the app to user the error.html template file as the current user's note.
2
0
12
@yeswehack
This challenge is about insecure password reset token generation to account takeover.
In fact, the token is generated using md5(random_int(1000, 9999) which make it vulnerable to brute force.
3
0
11
👀
Hi friendz ! 🧙♂️
Prochain Stream : Mardi 17 Octobre à 21h ! 🔥
Topics :
- Open-Sourcing push-my-diffs by
@TheLaluka
🔭
- Kubestroyer, HowTo & WhatNot by
@Rolix_cy
🧊
- Hooking client side sinks using DOMLogger++ by
@kevin_mizu
🕸️
A très vite ! 😎🛠️
1
9
35
0
0
12
@intigriti
This snippet of code is about open redirect to XSS via redirectURL get parameter 💥
1) regexUrl allows any protocol with numbers, chars and tab.
2) antiXSS block URL which start with JavaScript.
Thus, using jAvAScRIPt: or \tjavascript: wrapper should bypass the check.
1
1
11
Hello! Je m'y prends un peu tard mais, je suis à la recherche d'une place étudiante pour la
@_barbhack_
, quelqu'un en aurait une en trop ? 😄
0
7
11
@joaxcar
Nice challenge again! Got it with a 30-char long payload :p
Curious to see if other ppl will manage to solve it differently :D
2
0
11
@MtnBer
@ctbbpodcast
Thanks a lot for sharing 🙏
I'm currently working on new cool updates and templates. I'll share them soon :D
1
0
10
@huntr_ai
Thanks for the highlight! It's been a pleasure to look for issues in AI open source projects 😁
I hope to be able to find more cool bugs in the future!
1
0
10
Last weekend, I did the
@DamCTF
with the
@rhackgondins
, We finished 12th over 550 student teams. 🎉
You can find my writeups here:
1
0
9
Other web challenges (made by
@BitK_
) writeups can be found in the
#writeup
channel of the CTF Discord server:
Btw, all the
#FCSC2024
challenges are available on ! 👀
Thanks
@ECSC_TeamFrance
again for the opportunity 💙
2/2
2
1
9
To conclude, I would like to thank everyone who participated in this challenge 🙏
Furthermore, congrats to all the solvers and especially to the top 3:
🏆
@SecurityMB
🥈
@ixSly
🥉
@maple3142
Stay tuned, as another challenge might be released by the end of the year 👀
6/6
0
0
9
@PinkDraconian
@intigriti
Even if the CSP has a nonce, we can use the base tag to change the domain on which the script src will be loaded :D
Ref:
1
0
8
@joaxcar
@renniepak
If using the Burp's browser is a problem, I've created an extension () which allows you to fully configure what you want to hook/replace and get a notifications from.
It is not yet ready for auto prototype pollution detection, but it might be a solution :D
0
0
7
Dans la perspective de disputer l'Open Tour et de participer à différentes LAN qui auront lieu cette année, nous nous associons à la structure
@HegemoniaFrance
qui nous accompagnera tout au long de cette saison 2019
#CKDO
0
2
7
Only 2 days left and 11 solves so far!
Anyone else to solve the challenge? 😁
@kevin_mizu
Good news! The challenge is back online and we've extended the deadline to Friday night 🥳🎉
We'd like to apologize for the downtime, so please take this free hint 💜
1
0
14
0
0
6
@intigriti
This is a self XSS abuse to leak sensitive content in the DOM. Thanks to the opener link (check ), it is possible to setup 2 windows, 1 with the victim card and another with the XSS (CSRF) which will be able to access opener info (same origin) :p
2
0
7
@intigriti
I've recently gave a small flask / HTML PoC for this vulnerability which can be found here:
0
0
6
@_Worty
@EsnaBretagne
@Atlas453_
@DinerHell
@0xItarow
@Gaburall
@SpawnZii
@iHuggsy
@D1n0x0r
@gcc_ensibs
Les boss rien à dire, juste decu que t'es pas eu ton abonnement rm 😂
0
0
6
Don't hesitate to follow other
@ctf_esaip
challenges makers:
@hiippiiie
@Ooggle_
@Ruulian_
@FeelProud_sec
@Rolix_cy
@PotierTanguy
@0sy_ris
0
1
5
@intigriti
On the above sniper, the vulnerability occurs in JWT token verification. In fact, the key used for the token verification is read from a file defined by the JWT kid value (inside his header). This value can be change by an attacker by whatever he wants.
1
1
5
@_Worty
also made an excellent writeup ( ) feel free to read it! 🔥
If you want to try challenges by yourself, sources are available here: 👀
1
0
5
To conclude this short write-up, I would like to congrats the 3 flaggers of the challenge:
🏆
@Blaklis_
🥈
@pilvar222
🥉
@ankursundara
Solution link: 🎉
6/6
0
1
5