Lukasz Olejnik
@lukOlejnik
Followers
14K
Following
4K
Media
5K
Statuses
18K
Security&Privacy. Data protection. Research. Engineering.Analyst.Policy. W3C. Consultant. Book author. (perhaps happy to work for you?). Ph.D, LL.M. @warstudies
Brussels / London / EU
Joined March 2013
Hi there! European Parliament has just passed end-to-end encryption and no backdoors in #ePrivacy Regulation. And how's your day?
14
725
913
This is a huge world precedent. Not even Stasi or other communist country "security services" had a DIRECT LINE into people's lives, essentially their minds.
Here. I said it in @Telegraph. Any kind of data may be potentially targeted. Apple's system is a world-precedent in the area of remote inspection of private data/files. This is a huge power/capability.
11
204
545
Meta/Facebook was fined a record #GDPR EUR 1.2 BILLION for violating European privacy rules. The company has now been given a DEADLINE to stop the transfer of user data to the United States. This (if nothing changes) means SHUTDOWN OF Facebook in Europe.
16
129
570
@VeraJourova With all due respect, today you mentioned breaking, exactly. As for the infrastructure, it would be an inefficient solution, easy to bypass (& ineffective), but introducing a dangerous precedent. Extending the scanning to other content would then be really simple. #ChatControl.
So here's @EU_Commission's VP @VeraJourova speaking that the #ChatControl regulation is designed to break encryption (captioned. Mass, untargeted surveillance. Oh and by the way, the European Court of Human Rights has a verdict that untargeted encryption breaking is illegal.
10
47
441
Singapore stops its "Smart Nation" (connected and intelligent "everything") project following a data breach of 1.5M patients. #GDPR
8
243
229
Chrome suddenly introduced automatic browser sign-in. Consent, user awareness, dark patterns? I provide a case study through privacy lens. #GDPR
8
154
201
Exfiltrating private data like browsing history using browser ambient light sensors. My work with @arturjanc
2
195
187
Mozilla is completely removing Firefox support for battery level readout by websites, citing privacy concerns.
Web scripts using battery level readouts to track users. Privacy analysis of @w3c Battery Status API
6
175
170
Dangerous Linux kernel privacy vulnerability in TCP/IP implementation. User fingerprinting. Attack could be deployed on a malicious website! Tracking devices across browsers, browser privacy modes, containers, networks. Very serious. Privacy is hard #GDPR
2
74
172
So here's @EU_Commission's VP @VeraJourova speaking that the #ChatControl regulation is designed to break encryption (captioned. Mass, untargeted surveillance. Oh and by the way, the European Court of Human Rights has a verdict that untargeted encryption breaking is illegal.
10
71
159
Smartphones today are prepared to process/collect some very sensitive, if private, information. For example, full support for tracking sexual activity. First, Android. For example: getProtectionUsed. #GDPR )
8
55
159
My analysis of @ICRC report selection. Cyberoperations. What impacts on exploit cost? Why supply chain attacks are a risk? Targeting health care (lethal cyberattacks; can you even detect?), ICS. Armed conflict context. How to move forward? #CyberICRC
3
75
155
iPhone apps are collecting quite some A LOT OF user private data. Extremely verbose, allowing to fingerprint, perhaps even track users. Context from my works. About privacy risks of light data: Risks of battery information:
This screenshot shows the app analytics data sent by two different iOS apps: @duolingo and @Tinder. What's the likelihood that both apps are installed on the same device? 💯? 🤯. Both apps use @unity Ads. The data in the screenshot is collected by the Unity Ads framework included
5
65
150
My article, analysis, op-ed in @WIRED about smartphone apps letting Ukrainians report Russian forces. Such capability blurs the lines between civilians (to be protected by international humanitarian law) and combattants, the core principle of distinction.
17
62
140
My opinion article in @WIRED about an element in India's data protection law proposal that might threaten privacy (and security) research. Outright banning re-identification, without proper considerations, may weaken data protection and systems security.
5
104
146
Here. I said it in @Telegraph. Any kind of data may be potentially targeted. Apple's system is a world-precedent in the area of remote inspection of private data/files. This is a huge power/capability.
My comment in @Telegraph about Apple's new tech to scan images on user's devices for illegal content. Such a 'surprise feature' makes you wonder what may or may not come in the future, and what are really the security and privacy guarantees.
4
49
125
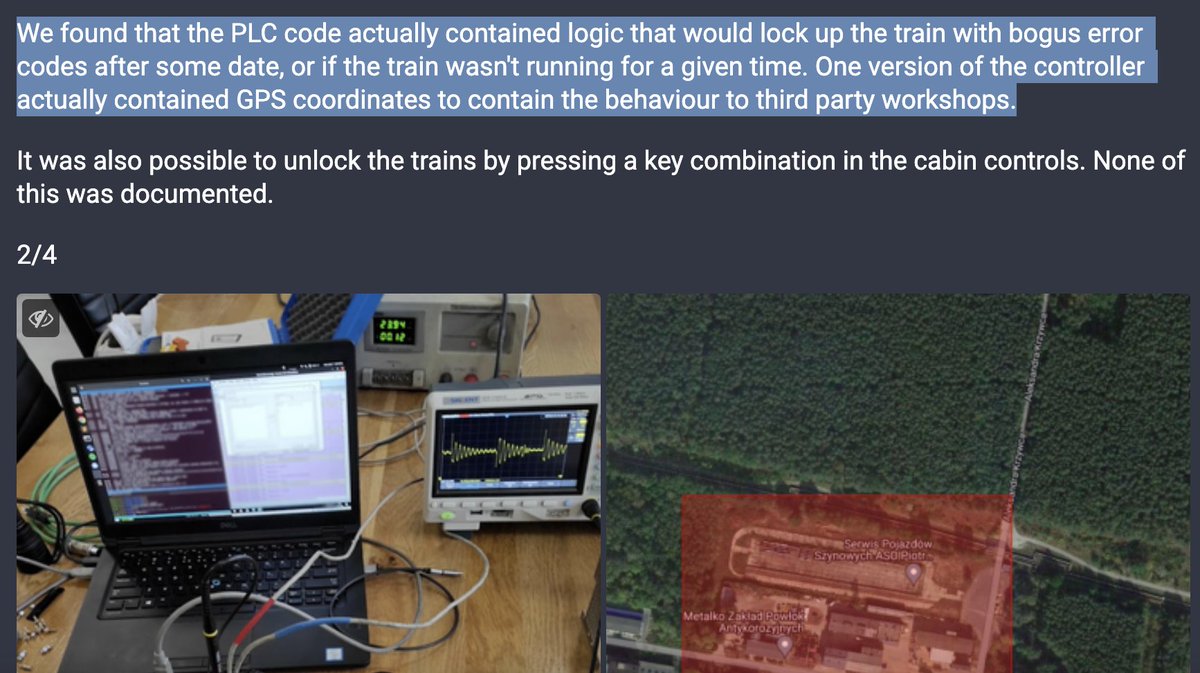
EW (?) operation against train system in Poland. Hijacked frequencies cause disruption (emergency RADIO-STOP signal emitted), and. Russian national anthem, and Putin's speech. Developing. Weird things start to happen. Requires physical proximity.
Komunikat ❗️ .W nocy z piątku na sobotę w województwie zachodniopomorskim odnotowano nieuprawnione nadawanie sygnału radio-stop. Niezwłocznie działania podjęły odpowiednie służby. Nie ma zagrożenia dla pasażerów kolei. Efektem zdarzenia są wyłącznie zmiany w kursowaniu pociągów👇
5
86
130
European Parliament intends to ship end-to-end encryption in #ePrivacy and prohibition of backdoors. Great!
4
105
113
Google/Chrome is deprecating and removing third-party cookies. So it has begun. End of the line for 3rd-party cookies is near. You will not be missed. #GDPR #DigitalServicesAct #privacy #dataprotection
User tracking on the web will be increasingly phased out. It will also be made more unwelcome, and illegal, than it is today. The political process to arrive there is in motion. Some technology companies feel this evolution and are preparing for this.
3
58
126
"Researchers developed a method to deliver a Facebook ad campaign to just one person out of 1.5 billion" "based only on the user’s interests", so on personal data (despite authors claiming otherwise!) . Ultra- targeting. #GDPR #ePrivacy #DigitalServicesAct
9
82
112
So here’s me giving my book Philosophy of Cybersecurity to the renowned cybersecurity thought leader (and haxor) @thegrugq. Thank you for a professional exchange of views!
4
6
119
My article with @gynvael in one of the most 31337 hacker/programming magazines out there! So you want to execute shellcode from Python? We got you covered! @pagedout_zine
1
29
124
First big case is in! Insurer lost a court battle: had to pay $1.4 billion to Merck, to cover the losses of the (allegedly) Russian NotPetya destructive wiper cyberattack, first released in Ukraine (2017). NotPetya was not "war".
Insurers increasingly formalising exclusion of cyberattack coverage. The Mondelez vs Zurich Insurance case where insurer refused coverege following #NotPetya infection citing "war-like activity" exclusion is known.
4
62
104
If you have a bad day, remember that Poland's top chief of Police apparently fired (by an 'accident') a grenade launcher RGW-90/Pallad-D. In his office. The result is structural damage to the building, the Main Police headquarters. Not even making this up. You CAN'T make this up.
Allegedly, a grenade launcher 'accidentally' fires in the center of Warsaw. In the main police department, by the way. It was a gift from Ukraine. I have no idea how that was possible.
11
30
112
My privacy analysis of Progressive Web Applications (web app manifest). Interesting user tracking and cookie respawning potential/risk; transparency. Progressive Web Apprehension. #PWA #PWApprehension
2
66
115
French DPA fines Electricite de France, France's largest electricity provider €600,000. Hashed passwords without a 128-bit random salt and use of MD5 is a violation of #GDPR security requirements.
2
56
102