Mysk 🇨🇦🇩🇪
@mysk_co
Followers
16K
Following
4K
Media
1K
Statuses
5K
We're two #iOS developers and occasional #security researchers on two continents. #CyberSecurity 🎬 https://t.co/JGKIHaSEgs 📝https://t.co/69k7WAGSBT 🇨🇦🇩🇪
Canada - Germany
Joined November 2010
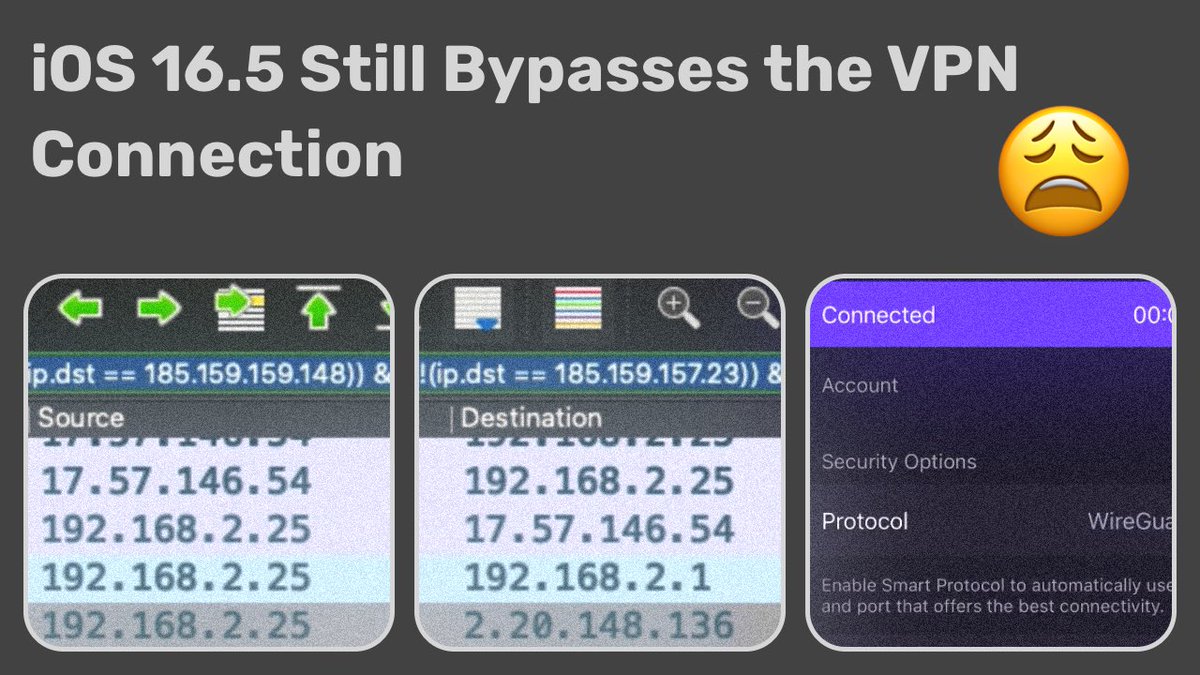
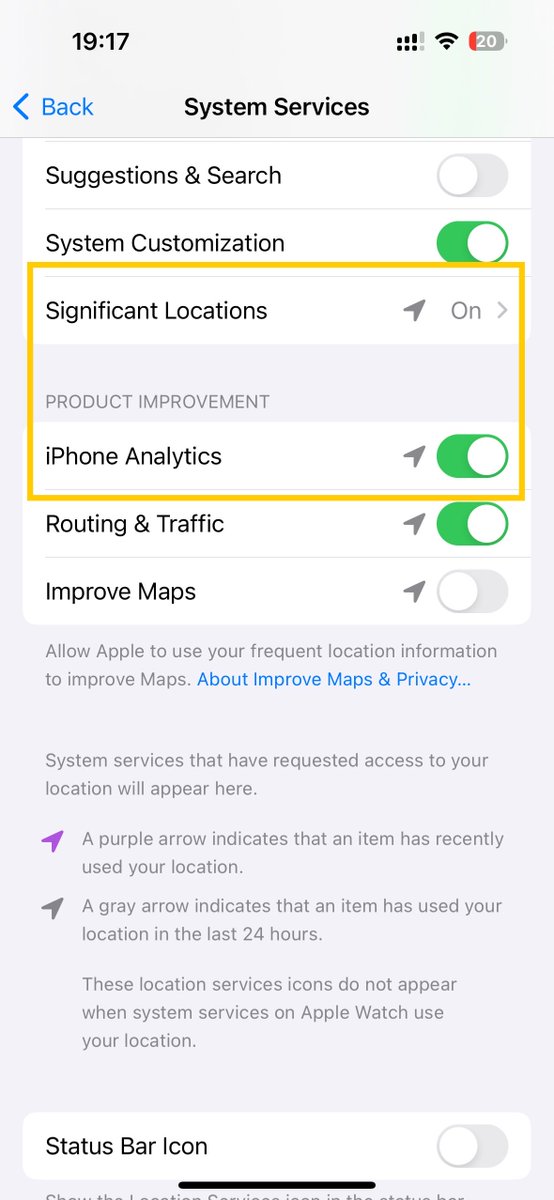
We confirm that iOS 16 does communicate with Apple services outside an active VPN tunnel. Worse, it leaks DNS requests. #Apple services that escape the VPN connection include Health, Maps, Wallet. We used @ProtonVPN and #Wireshark. Details in the video:. #CyberSecurity #Privacy
434
6K
20K
TL;DR: Don't install @signalapp for macOS, it is not secure. I carried out this small experiment:. - I wrote a simple Python script that copies the directory of Signal's local storage to another location (to mimic a malicious script or app).- I ran the script in the Terminal and
135
509
3K
I know what you're asking yourself and the answer is YES. #Android communicates with #Google services outside an active VPN connection, even with the options "Always-on" and "Block Connections without VPN.".I used a #Pixel phone running #Android13, its IP is 192.168.2.14 👇
32
222
886
Speaking of outdated, @MicrosoftEdge is the only browser on macOS that still requires administrative privileges to install. 🫠
19
50
876
🧵.1/5.The recent changes that Apple has made to App Store ads should raise many #privacy concerns. It seems that the #AppStore app on iOS 14.6 sends every tap you make in the app to Apple.👇This data is sent in one request: (data usage & personalized ads are off).#CyberSecurity
38
299
708
You can easily monitor the network traffic of any device using this simple method. You don't need a custom router for that. You just need a Mac and #Wireshark, and enjoy ✌️.
At Mysk we use this simple method to monitor the network activity of a device:.►Connect your Mac to the internet via LAN.►Share the internet from LAN to Wi-Fi.►Connect the device to this Wi-Fi.►Start #Wireshark on your Mac and pick brdige100.►Start capturing. #SecurityTips
14
73
629
WhatsApp messages are end-to-end encrypted, but user data is not only about messages. That also includes the metadata such as user location, which contacts the user is communicating with, the patterns of when the user is online, etc. This metadata according to your privacy policy
Many have said this already, but worth repeating: this is not correct. We take security seriously and that's why we end-to-end encrypt your messages. They don't get sent to us every night or exported to us. If you do want to backup your messages, you can use your cloud provider.
34
114
637
This video shows that @signalapp (7.15.0) on macOS stores photos and docs sent through the app locally without encryption. Worse, the files are stored in a location accessible by any app or script. However, text messages are stored locally in an encrypted DB. #privacy #security
35
110
501
@mer__edith Hi Meredith, let me address your points:. 1) The issue we highlighted does not require “full” access to the device. Signal desktop stores the chat database in an unprotected area of the file system that’s accessible by any user process. This would allow any program without any.
16
41
435
The community note is wrong and @elonmusk is right. Signal's desktop apps encrypt local chat history with a key stored in plain text and made accessible to any process. This leaves users vulnerable to exfiltration. The issue was reported in 2018, but it hasn't been addressed👇.
@realchrisrufo There are known vulnerabilities with Signal that are not being addressed. Seems odd ….
19
55
445
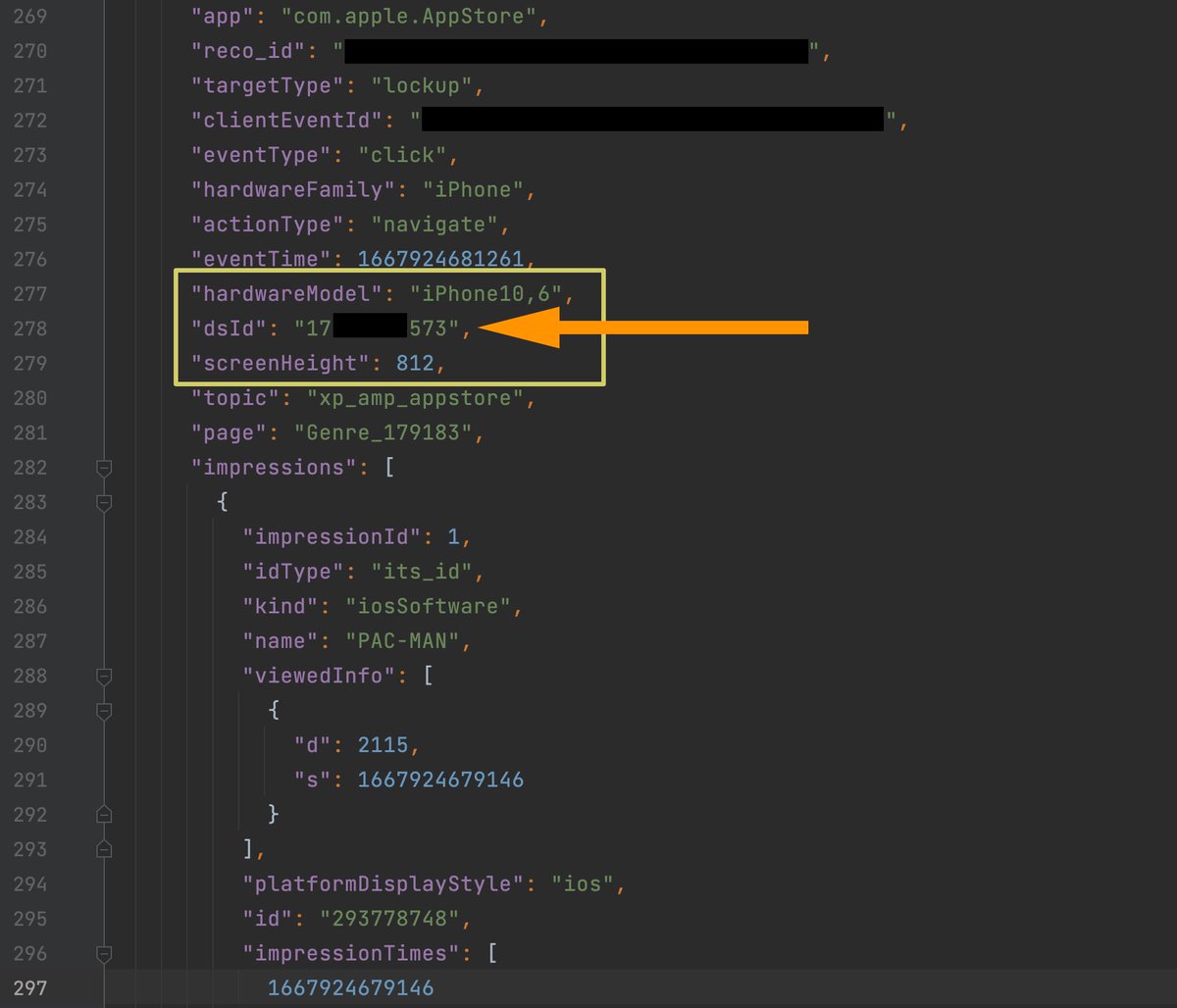
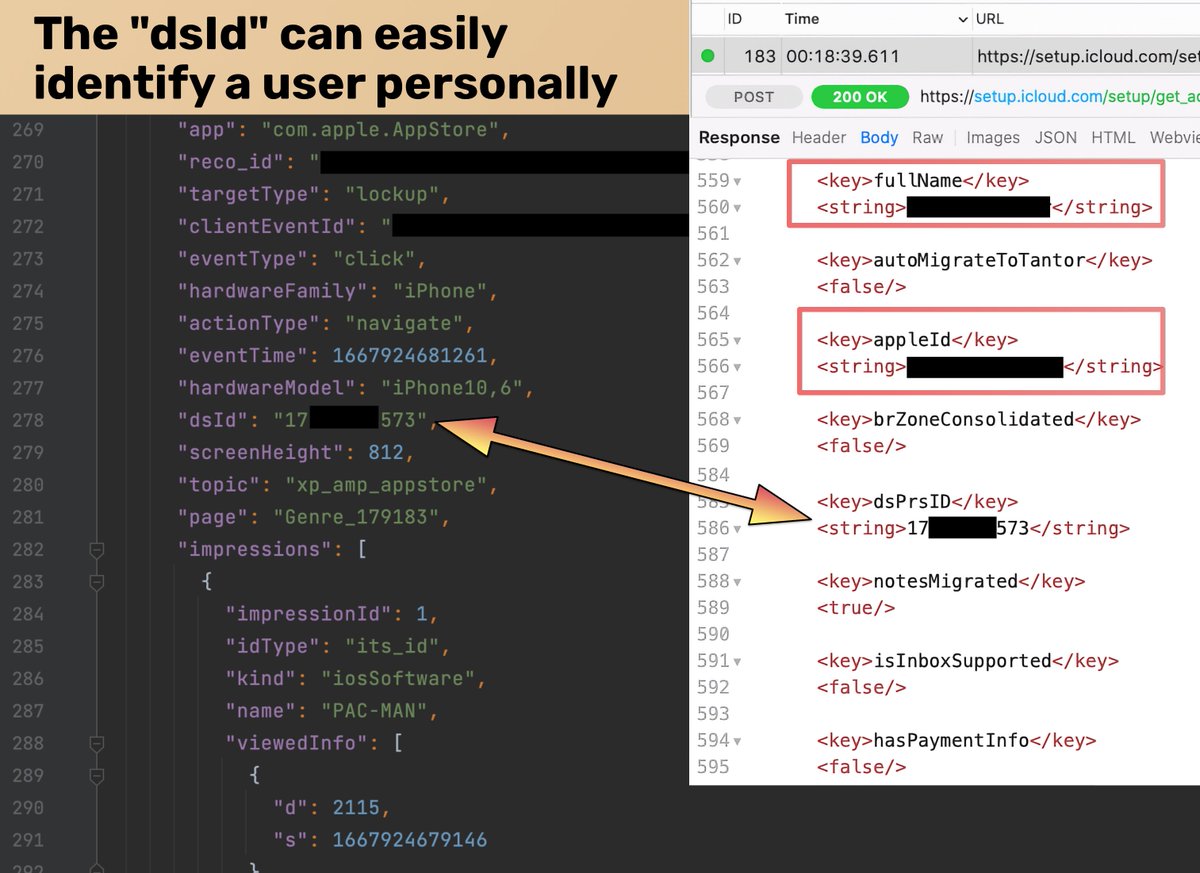
This is an example of what the App Store app shares with #Apple when you search for an app. Everything you type in the search field is recorded as an event and associated with your Apple ID before it is sent to Apple. When I search for "Google Authenticator," events are recorded
23
83
419
The community note is inaccurate. The claim "Find My is end-to-end encrypted" generally is misleading. Online devices report their location to Apple without end-to-end encryption even with Advanced Data Protection is on. This makes it possible to look up a device’s location
@9to5mac @benlovejoy This feature is super creepy surveillance tech and shouldn’t exist. Years ago, a kid stole a Mac laptop out of my car. Years later, I was checking out Find My and it showed a map with the house where the kid who stole my Mac lived. WTF Apple? How is that okay?!.
16
76
364
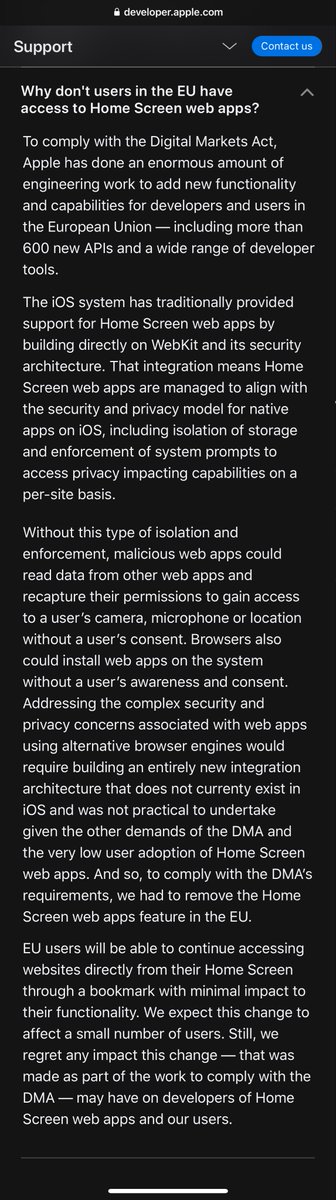
Apple decided to remove PWAs, then walked back the decision. Apple terminated Epic Games developer account, now they walked back the decision. What's going on with Apple?."Trust is built in drops and lost in buckets". How many buckets has Apple lost so far?.
Update - Apple has told us and committed to the European Commission that they will reinstate our developer account. We are moving forward as planned to launch the Epic Games Store and bring Fortnite back to iOS in Europe. More below⬇️.
20
52
384
On Android, several Google services bypass an active VPN connection. As a result, a VPN connection won't hide your IP address from Google. And since YouTube is a first-party app on Android, it will get your real IP address and roughly determine your location despite using a VPN.
13
126
376
On macOS, iMessage stores the chat history locally in plain text, but the data is sandboxed and no other process can access it without permission. @Whatsapp also stores the local history in plain text but stores the data in a location accessible by any process/app/script started.
11
45
339
🧵 .1/6. Apple's Data & Privacy statement starts with the calming phrase "Apple believes privacy is a fundamental human right" then goes on to describe how the platform aggressively collects your data. You must accept the statement or stop using your iPhone. #CyberSecurity
13
116
324
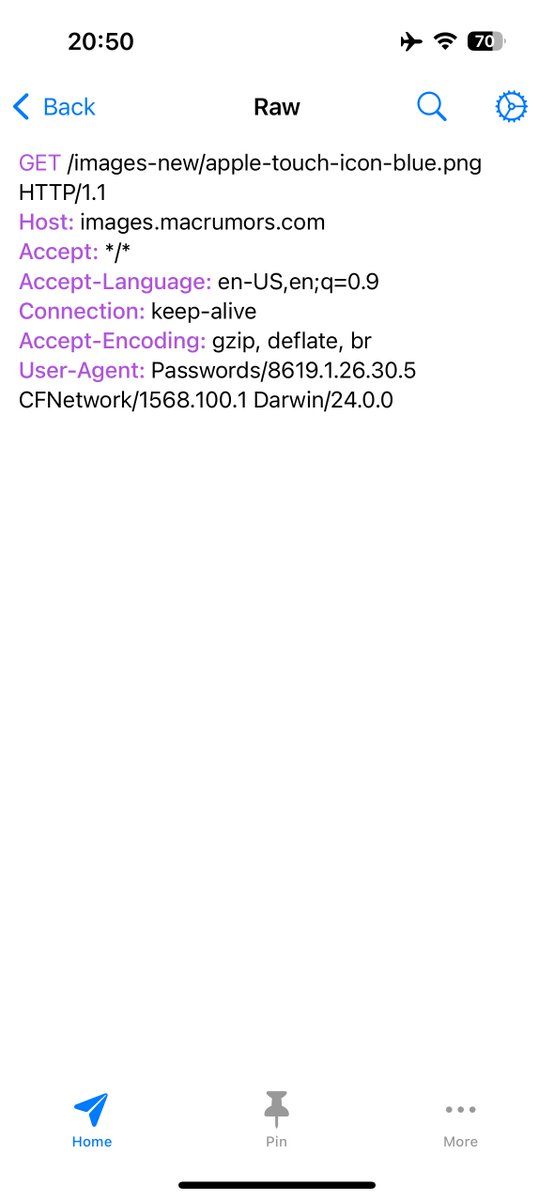
Just realized that the Passwords app communicates with 147 websites. It turns out the app calls every website of your added accounts to download its icon. The request has this user-agent:.User-Agent: Passwords/8619.1.26.30.5 CFNetwork/1568.100.1 Darwin/24.0.0. #iOS18
19
26
302
Apple blocked Spotify's update for including a button that emailed a link for purchasing audiobooks. Amazon is doing exactly the same. If you tap on the "I Want This Book" button in the #iOS app, you get a link to purchase the book outside the app. Apple Review Team approved it.
13
41
269
🚨@signalapp on its website presents both mobile and desktop versions to be equally secure. As we showed, the desktop versions are vulnerable to data exfiltration and session hijacking. This is consistent with early reports from 2018 and results from developers who successfully.
TL;DR: Don't install @signalapp for macOS, it is not secure. I carried out this small experiment:. - I wrote a simple Python script that copies the directory of Signal's local storage to another location (to mimic a malicious script or app).- I ran the script in the Terminal and
12
39
271
To the unknown future dissident, activist, or freedom seeker whose life will be saved as a result of the enhanced security added to Signal Desktop: You're welcome.
Signal is finally tightening its desktop client's security by changing how it stores plain text encryption keys for the data store after downplaying the issue since 2018.
14
28
262
Dear #Android users,.Chrome shares your motion sensor with all the websites you visit by default. This video shows how you can disable it. Please do it now. You can learn more about this here:. #CyberSecurity #Privacy
18
197
243
At Mysk we use this simple method to monitor the network activity of a device:.►Connect your Mac to the internet via LAN.►Share the internet from LAN to Wi-Fi.►Connect the device to this Wi-Fi.►Start #Wireshark on your Mac and pick brdige100.►Start capturing. #SecurityTips
9
45
245
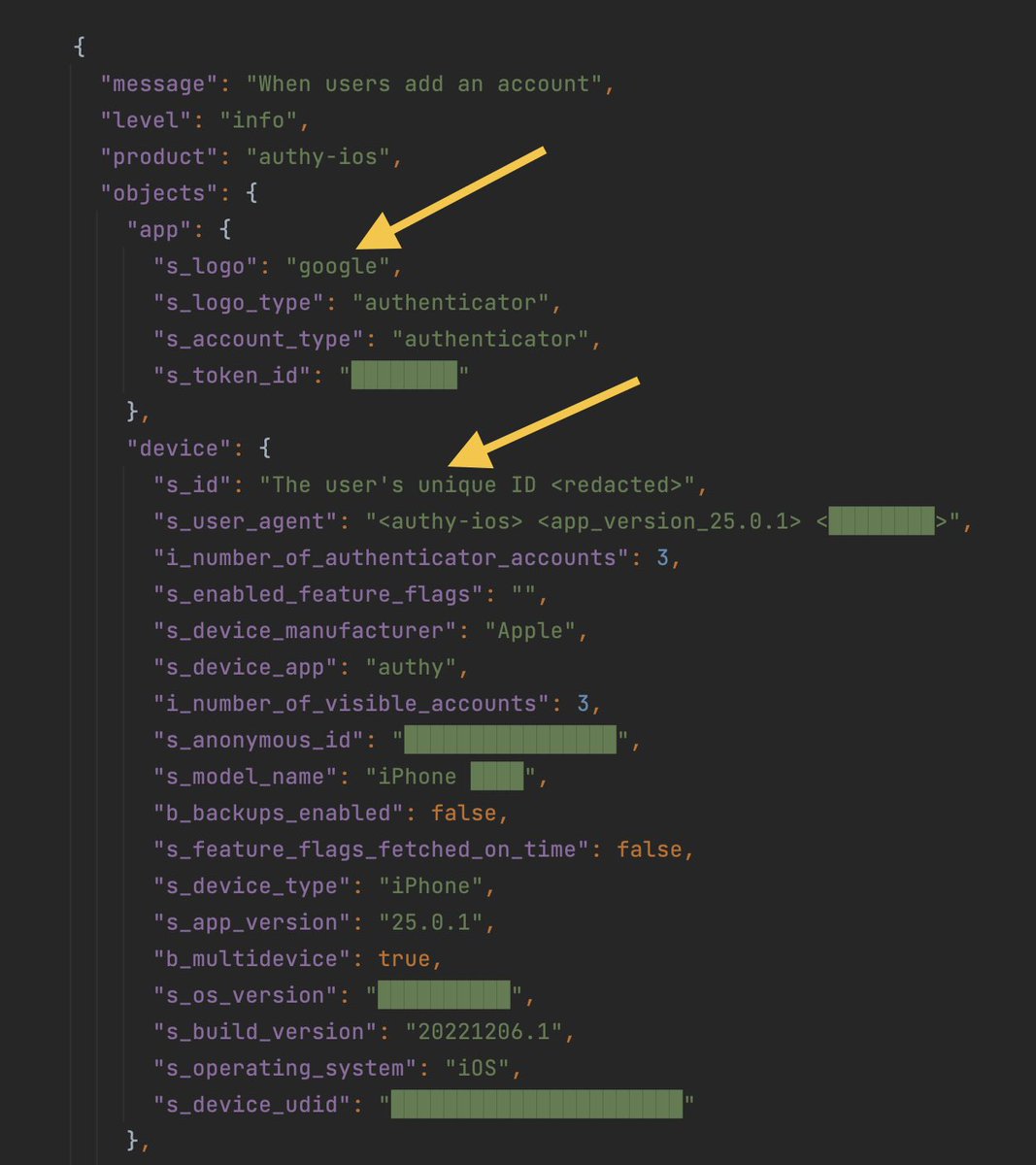
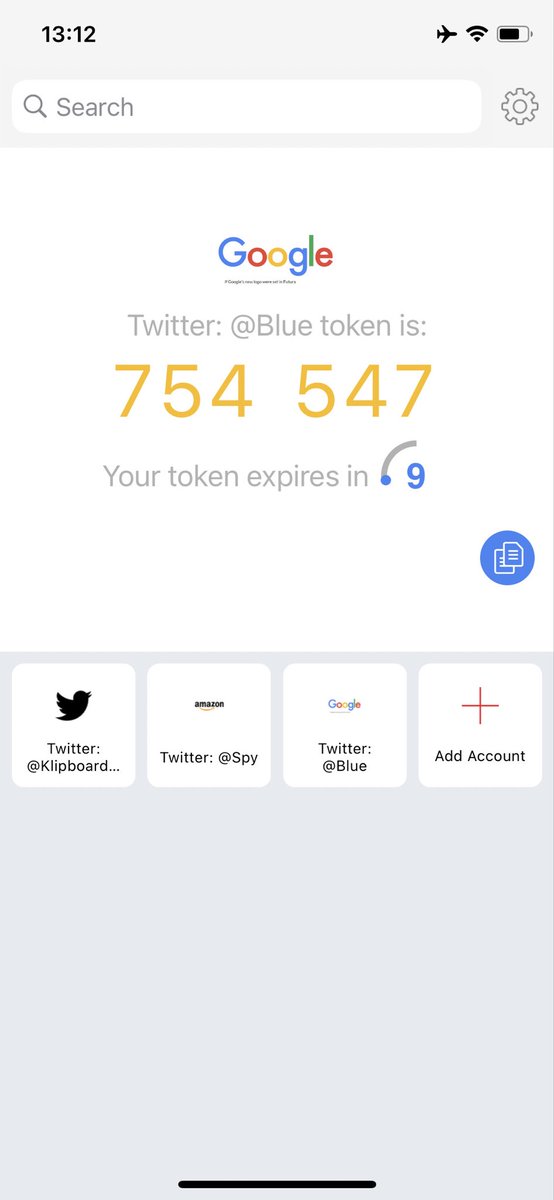
As @PrivacyMatters speculated, Authy sends too much analytics for an authenticator app. It associates analytics with the user's ID, which is tied to phone number and email. The analytics include the issuer name of each scanned QR code. Try to use a different #2FA app. #Privacy
24
56
244
Philips Hue will soon force users to create a Hue account and sign in to continue to use the app and control the smart lights. The best security model to protect smart devices is to keep them disconnected from the internet, or at least keep this option available. #Privacy
23
41
219
A lot of accounts promote crypto scams on X and they hardly get suspended. And now this:. @ProtonWallet
18
22
204
@VeraJourova The draft mandates providers to perform human oversight of content sent over a private and end-to-end encrypted channel so that they detect false positives. How would employees view such content without breaking encryption and invading one's privacy?
2
12
200
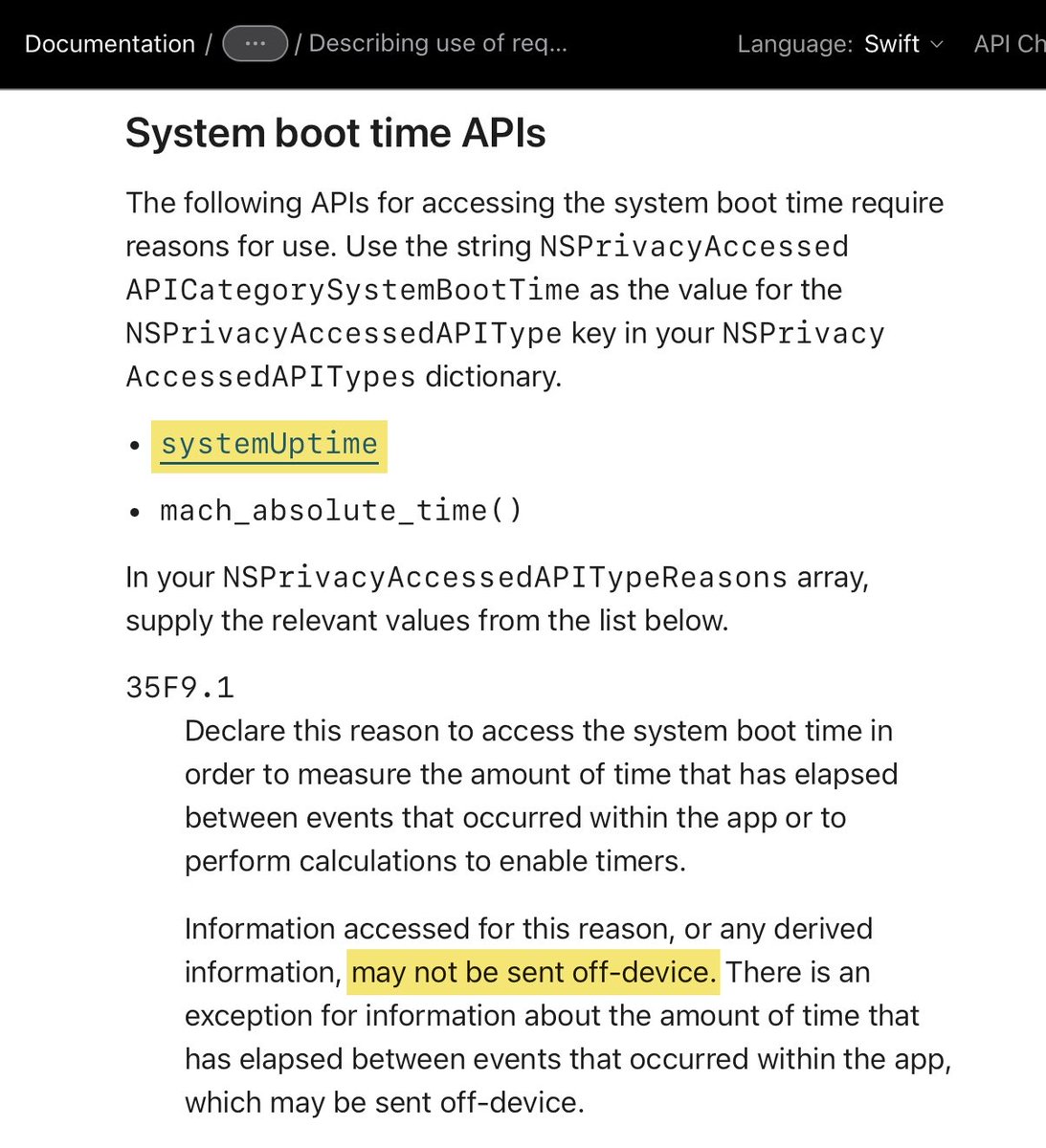
It's May 1. Instagram for iOS just got updated. It still sends the device's system uptime to remote servers. Starting today developers are no longer allowed to access this API without providing a reason. And in no way can the app send the value off-device. #Privacy
5
28
195
Sorry Signal and WhatsApp, you're not getting full access to my contacts. Stop begging. Be grateful you have access to a dummy contact. Both apps now check for the new #iOS18 authorization status "limited" and complain if the user authorizes access to some contacts only.
11
15
204
🎬 The App Store will continue to be the only place to install apps on the iPhone, even in the EU. Users should be aware that the App Store collects exhaustive usage data and sends it to #Apple. This can't be turned off. We made this video to show how tapping an app link gets.
4
48
187
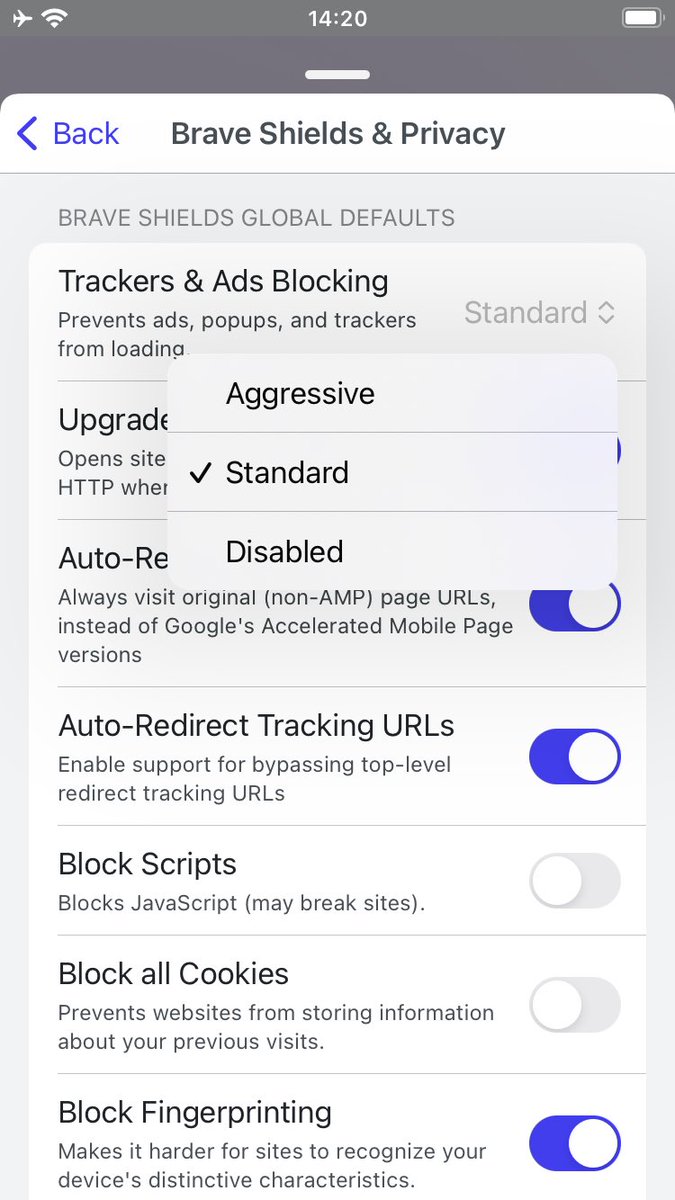
Nice! @brave for iOS just got updated to support the new "marketplace-kit" scheme. Brave only calls the scheme when trackers blocking is disabled. As we reported earlier, Apple implemented the new scheme in a way that allows tracking across websites based on the unique client_id.
5
29
187
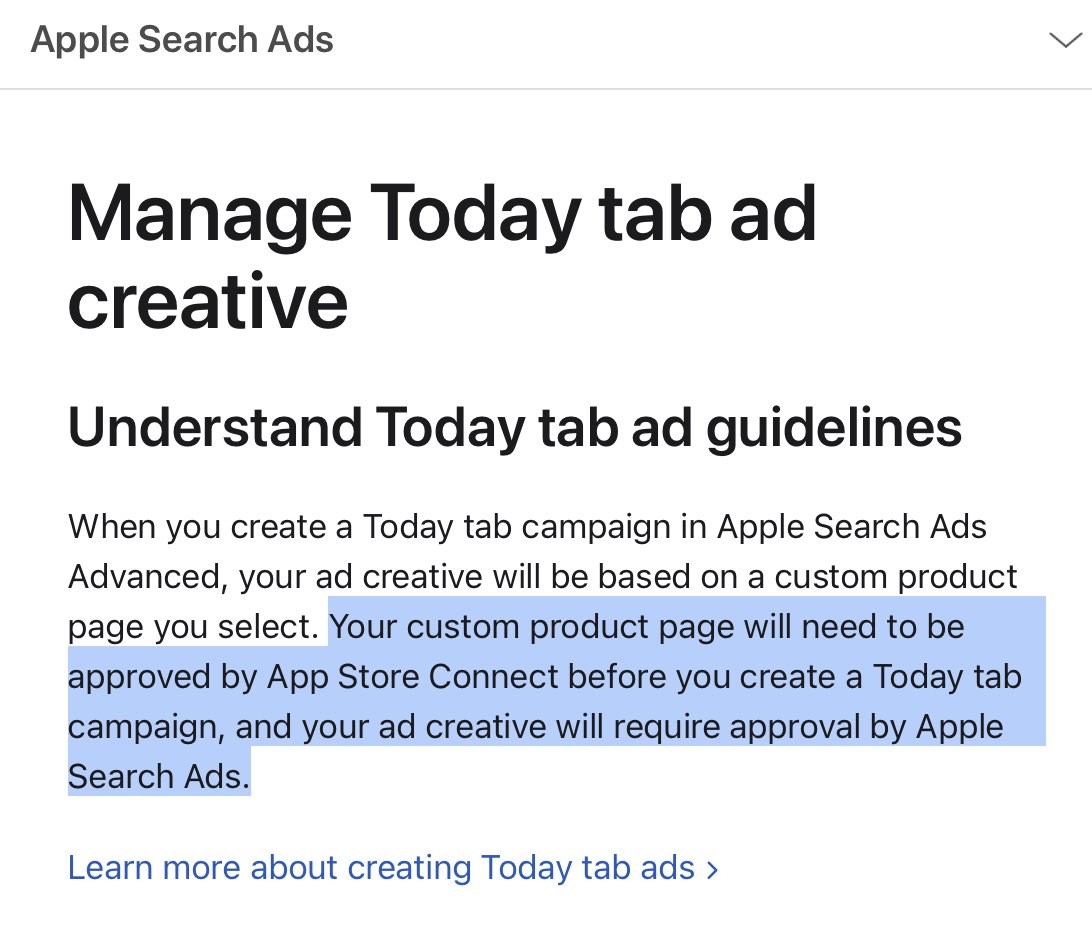
BREAKING: The App Store has taken down the scam #2FA app that steals secrets. We warned about this app four months ago. This wouldn't have happened without your support to spread the word. Thank you! 🙏🙏✌️
🎬 So this scam #2FA app is using custom product pages of Apple Search Ads to trick users. It has different campaigns per search keywords. When searching for "Microsoft Authenticator", it shows screenshots highlighting "Microsoft". and when searching for "Google Authenticator",
12
30
182
More context:.
This video shows that @signalapp (7.15.0) on macOS stores photos and docs sent through the app locally without encryption. Worse, the files are stored in a location accessible by any app or script. However, text messages are stored locally in an encrypted DB. #privacy #security
6
10
185
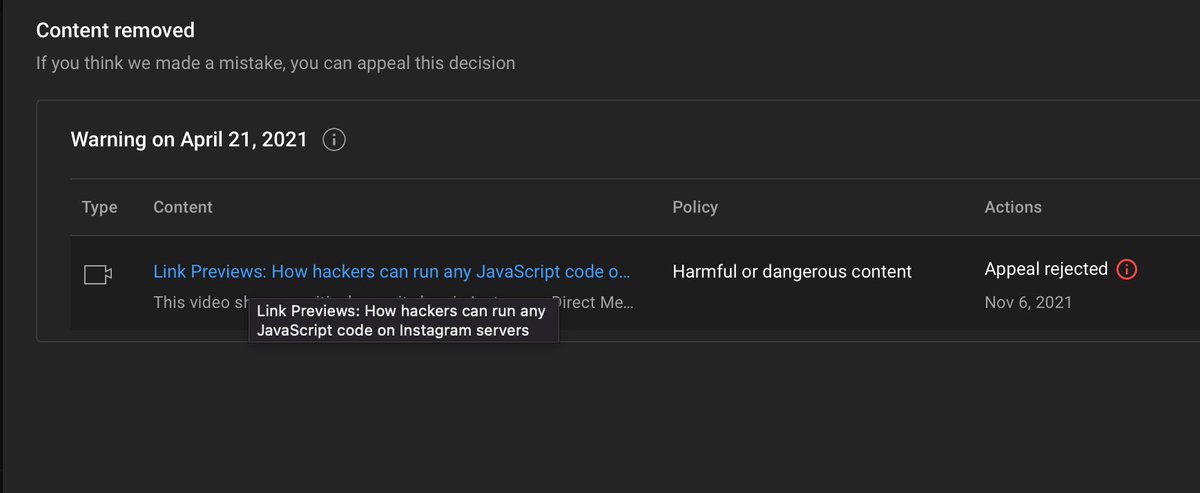
🧵.1/7.During our research on link previews, we discovered that Instagram servers execute #JS code in links sent in DM. We contacted Facebook security team. They said it was expected behavior, no issue. We published the work. @TeamYouTube took down the video and sent us a warning
10
65
184
This old thread by @signalapp's president addresses a report by johnjhacking about the same desktop app vulnerability we highlighted. The response downplays the risks on the basis that the level of access required to hijack a session is "only available if the device is already.
The report by johnjhacking is confused. What they propose requires a level of access that's only available if the device is already completely compromised: “First and foremost, you need access to the device.” TLDR someone compromising your device is not a problem with Signal. 1/.
14
26
185
Google Authenticator still syncs two-factor authentication secrets without E2EE. If you enable cloud syncing, this means:.1️⃣ Google can read the secrets and generate one-time passwords for your accounts.2️⃣ Google knows the services you use.3️⃣ #Google knows your usernames.#Privacy.
Google has just updated its 2FA Authenticator app and added a much-needed feature: the ability to sync secrets across devices. TL;DR: Don't turn it on. The new update allows users to sign in with their Google Account and sync 2FA secrets across their iOS and Android devices.
10
65
178
Thank you @Apple! We were rewarded a bounty of $5,000 for reporting this bug. 🙏. CVE-2023-42846.
🚨 NEW: Private Wi-Fi addresses had been useless ever since they were introduced in iOS 14. When an iPhone joins a network, it sends multicast requests to discover AirPlay devices in the network. In these requests, iOS sends the device's real Wi-Fi MAC address. 🎬 Watch the
16
14
177
We prepared this video to illustrate why access to the accelerometer should get a permission in iOS. Unrestricted access to accelerometer data can breach user privacy. We used Facebook as an example in the video. #Cybersecurity #Privacy #iOS .
11
89
168
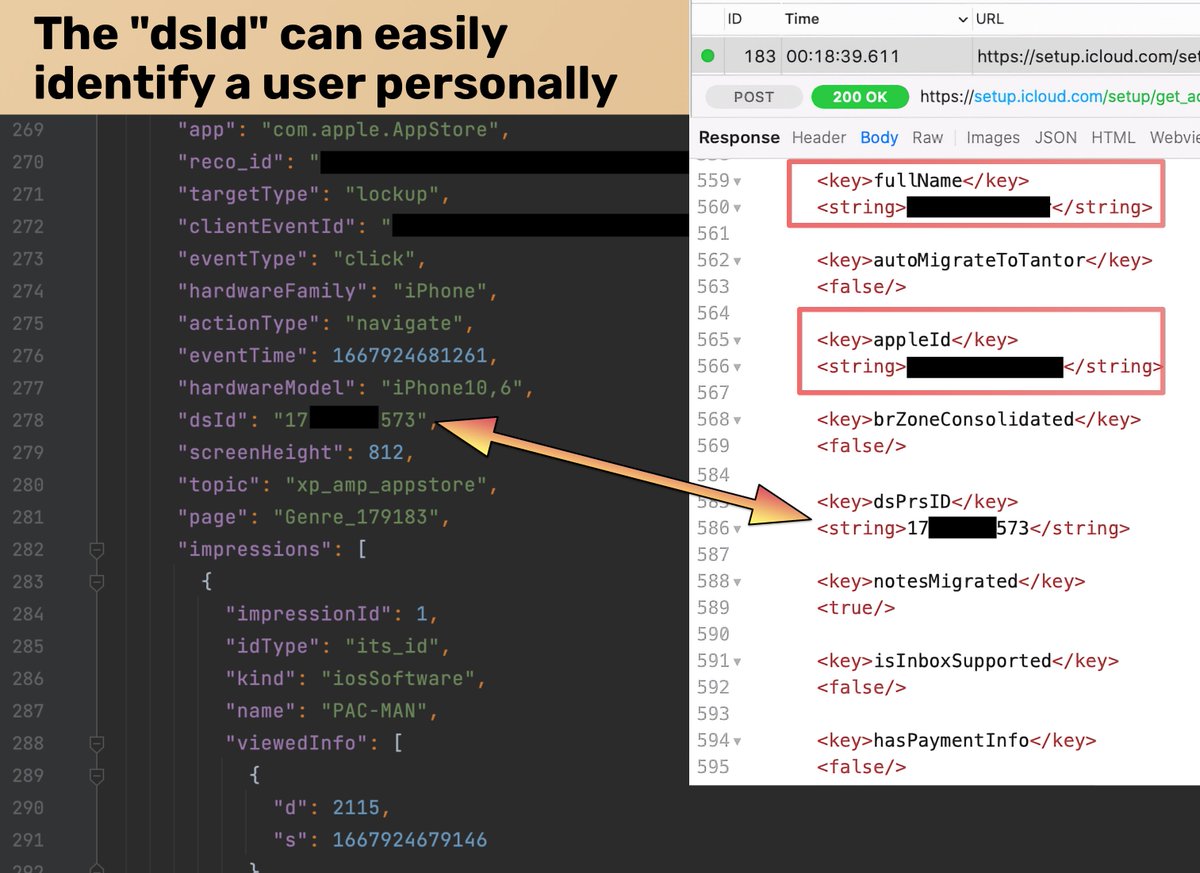
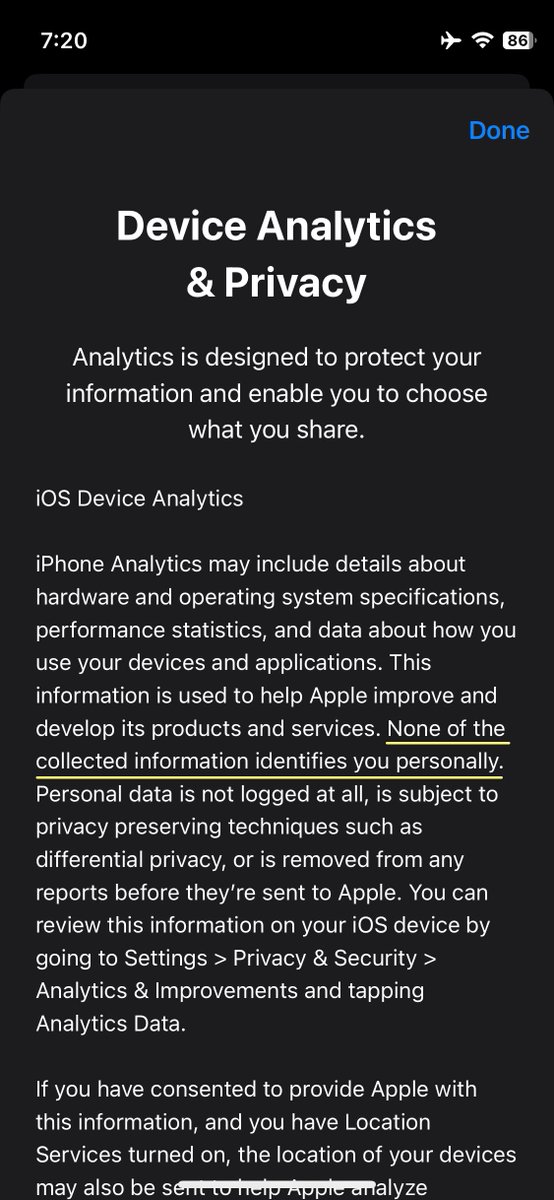
2/6.Apple states in their Device Analytics & Privacy statement that the collected data does not identify you personally. This is inaccurate. We also showed earlier that the #AppStore keeps sending detailed analytics to Apple even when sharing analytics is switched off.
5
40
165
So does @WhatsApp and @Apple iMessage, and likely many other apps. Open a terminal on a Mac and check:. strings ~/Library/Group\ Containers/group.net.whatsapp.WhatsApp.shared/ChatStorage.sqlite. strings ~/Library/Messages/chat.db.
7
27
168
Many comments suggest that if you don't want Apple to collect this private data about you, don't buy an iPhone. Well, many users already bought iPhones based on Apple's privacy promises. What should they do?.Moreover, Apple has its own definition of the term "tracking" 👇
🎬 The App Store will continue to be the only place to install apps on the iPhone, even in the EU. Users should be aware that the App Store collects exhaustive usage data and sends it to #Apple. This can't be turned off. We made this video to show how tapping an app link gets.
11
35
161
YES!! iOS 18 will let users decide which contacts an app can access. This is sad news for data harvesting apps such as LinkedIn. #iOS18 #WWDC #Privacy.
#iOS17 should stop apps from harvesting contact details when they have access to contacts and calendars. This video shows the data that LinkedIn syncs when it has access to contacts and calendars. 🤯.#WWDC23 #privacy #cybersecurity #cybersecuritytips.
6
18
155
When you view the tweet below by @signalapp on an iPhone, you'll see a card showing the Signal app with a button to install the app. If you tap on the button, a sheet is presented within the Twitter app showing more details about Signal. Even though the sheet is presented inside
Announcement! Signal is refreshing our board as we grow. We’re delighted to welcome @krmaher, @ambaonadventure, and @jaysullivan as Signal’s new Directors. Learn more here:
13
37
152
Signal now addresses vulnerabilities that have been known since 2018. Two CVEs were filed in this regard in 2023: CVE-2023-24068 & CVE-2023-24069.This proves the community note on @elonmusk' post wrong. Now do the right thing and vote against it. Thank you 🙏✌️.More links below:.
@realchrisrufo There are known vulnerabilities with Signal that are not being addressed. Seems odd ….
7
28
153
Update: The Lockdown Mode leaks more traffic outside the VPN tunnel than the "normal" mode. It also sends push notification traffic outside the VPN tunnel. This is weird for an extreme protection mode. Here is a screenshot of the traffic (VPN and Kill Switch enabled) #iOS
6
32
145
🚨🎬.Here is what happens when you insert an unlocked SIM card into a locked iPhone:. - The #iPhone accepts the SIM card and connects to the internet 😳.- Apple immediately adds the phone number of the SIM card to the Apple ID of the iPhone owner 😲.- Apple accepts the new phone
12
33
149
@hugelgupf @Apple Order an iPhone or iPad. Sign in to your iCloud account, accept the new terms, reset the device, and then send the device back to Apple. You can always return items purchased from Apple within 2 weeks. It's not good for the environment, but it should work.
11
4
142
✌️.
Signal encryption key vulnerability being fixed on Mac (and less fully on Windows) by @benlovejoy.
9
10
138
A few remarks about the #CrowdStrike outage:. ➡️ A broken update rolled out to customers without sufficient testing. The bug is clearly so easily reproducible. ➡️ The update was released on Friday. Not a great sign. ➡️ A staged rollout would’ve avoided most of the damage.
5
16
143
Back in the day, the rules to obtain the blue checks were absolutely arbitrary. Those who had "friends" at Twitter got it easily. Also Twitter employees allegedly sold the blue checks. Verified accounts used to have a clear advantage over unverified accounts. There was no clear.
Back in the day, #BlueChecks used to mean trustworthy sources of information✔️🐦. Now with X, our preliminary view is that:. ❌They deceive users. ❌They infrige #DSA. X has now the right of defence —but if our view is confirmed we will impose fines & require significant changes.
8
15
145