taha
@lordx64
Followers
7,059
Following
4,758
Media
36
Statuses
544
I blog about exploits & malware here : maintainer of Threat Intel Bot GPT all opinions are my own
Joined July 2009
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Elon
• 931256 Tweets
#गल_काटे_सो_कुफर_कसाई
• 170666 Tweets
Michigan
• 161554 Tweets
#UFC307
• 127040 Tweets
Vandy
• 120254 Tweets
Watch Sant RampalJi YouTube
• 119253 Tweets
Tennessee
• 112383 Tweets
Dodgers
• 107418 Tweets
Vanderbilt
• 84022 Tweets
Dark MAGA
• 81758 Tweets
トッキュウジャー
• 80796 Tweets
#BUS_KnockKnockKnock_Korat
• 74482 Tweets
Nico
• 73472 Tweets
Pereira
• 71472 Tweets
Bama
• 71222 Tweets
Ohtani
• 70989 Tweets
ドジャース
• 66207 Tweets
プリキュア
• 49368 Tweets
Khalil
• 47556 Tweets
Arkansas
• 37667 Tweets
DONBELLE ASAP RESURGENCE
• 36863 Tweets
Aldo
• 33358 Tweets
ポストシーズン
• 30748 Tweets
Bautista
• 26629 Tweets
Save Sanatan Dharma
• 26347 Tweets
Pennington
• 22963 Tweets
Ifigenia Martínez
• 18954 Tweets
Machado
• 18888 Tweets
京都大賞典
• 17903 Tweets
Poatan
• 14451 Tweets
大谷さん
• 14355 Tweets
山本由伸
• 11684 Tweets
Last Seen Profiles
The
#intelligence
community has been alerted this weekend about a recent data leak on GitHub involving a .cn contractor reputed to have cyber espionage capabilities. The full scope of this incident is still under investigation.
Typically, leaks like these are scrutinized for
2
40
172
Related to this hack:
1
2
103
@vxunderground
@wdormann
Sorry to ask but what is the password for Stuxnet 2.0? I need access plz
0
0
17
I then pivoted to look for other interesting stuff, it seems we have also CDR data in there, and
#ThreatIntelBot
was able to identify that format for me and provide me with a preview of this data. I will blurr some of the details here, but you got the idea.
0
3
16
@TrustWallet
hey
@TrustWallet
stick to the wallet business please, seriously though, who control your twitter account? please tell that person to just stop tweeting about this.
10
0
4
@wdormann
I checked your link, so the majority seems to be actual vulnerabilities: configuration issues, weak cryptography, implementation mistakes etc, that if an attacker analyze the device and figure it out, could exploit these vulns and install a backdoor.
xz backdoor, is pretty much
3
0
11
This is it guys, ssh auth bypass confirmed from the xz backdoor.
0
1
11
@simplylurking2
the thing is there are 20 000 backdoored npm packages discovered in 2023, so I am not sure if this is a good practice to assign a CVE to every backdoor supply chain attack because there are just many.
4
0
10
attribution is cool when done right
Interesting note on the
#xz
backdoor:
If you plot Jai Tan's commit history over time, the cluster of offending commits occurs at an unusual time compared to rest of their activity.
If the dev was pwned, it could be a sign that the threat actor contributed in their own timezone
44
461
4K
1
0
7
@juanandres_gs
Unicorn engine +ida , works very well, heres some code i wrote that you can adapt to pretty much emulate anything using ida pro on mac:
0
0
5
@sherrod_im
Ransomware distributed via Google/Bing search Ads, compromising enterprise networks. Although anticipated in 2020, the extent to which this has become a prevalent threat and a significant attack vector wasn't previously measurable.
1
0
5
Yes we need more stories on SS7
0
0
4
rumors circulating that there's an iOS vulnerability actively being exploited in the wild, but the source is
@TrustWallet
so I will be careful interpreting what they say without validation from
@Apple
security
1/2: ⚠️ Alert for iOS users: We have credible intel regarding a high-risk zero-day exploit targeting iMessage on the Dark Web.
This can infiltrate your iPhone without clicking any link. High-value targets are likely. Each use raises detection risk.
#CyberSecurity
673
3K
6K
1
0
4
@GelosSnake
Here
0
0
3
Damn this is awesome. Thanks le Grugq.
0
0
3
@msuiche
@lordnarfz0g
@Gi7w0rm
@vxunderground
@UK_Daniel_Card
@esa
@CISAJen
Thank you for your leadership
@msuiche
1
0
3
@L_Lgde
I disagree with the Victimology part and the tooling part you mentioning, due to the Minimal overlap (see below), and you don't mention the group distinction observed in the tradecraft:
"While we have discovered some minimal overlaps with other Chinese groups such as Violet
1
0
2
installing Darling on my daily box, it takes an eternity to compile. 30min in, and I am still at 17% of compilation.
1
0
2
@jfslowik
other shops: let's pick
@patrickwardle
research, write a blogpost about it, and not mention the source hoping no one will notice.🤡
0
0
2
good job
@richinseattle
If you use llamafile, llama.cpp, llama-cpp-python, Oobabooga, LMStudio or any other software that exposes llama.cpp grammar sampling, I found a few remotely exploitable bugs triggered through a single web request that got patched today. More to come from my work at
@Eclypsium
0
36
112
0
0
1
@UK_Daniel_Card
We should impose costs on this fox for burning OSINT threat intel feeds. +$1 on his linkedin monthly membership
0
0
1
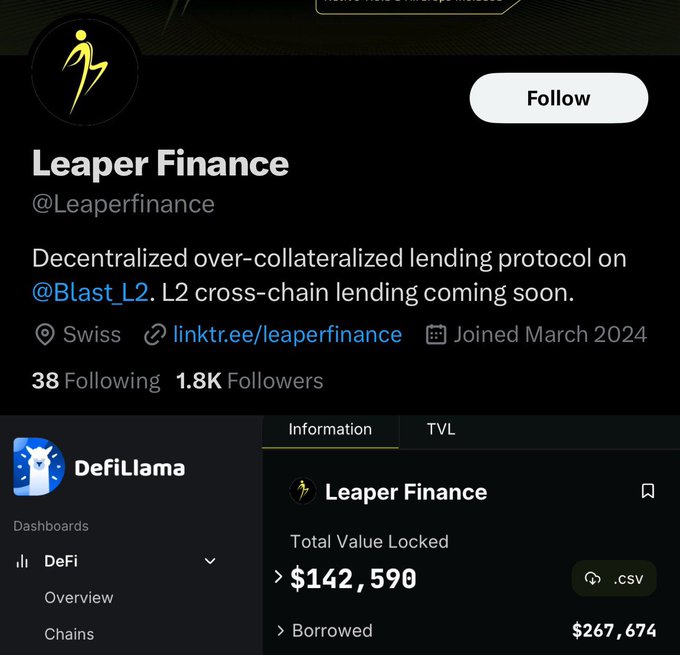
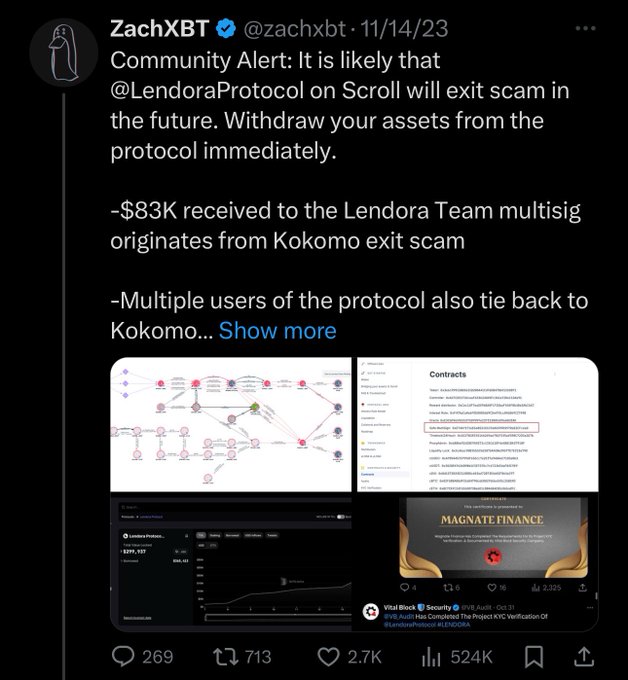
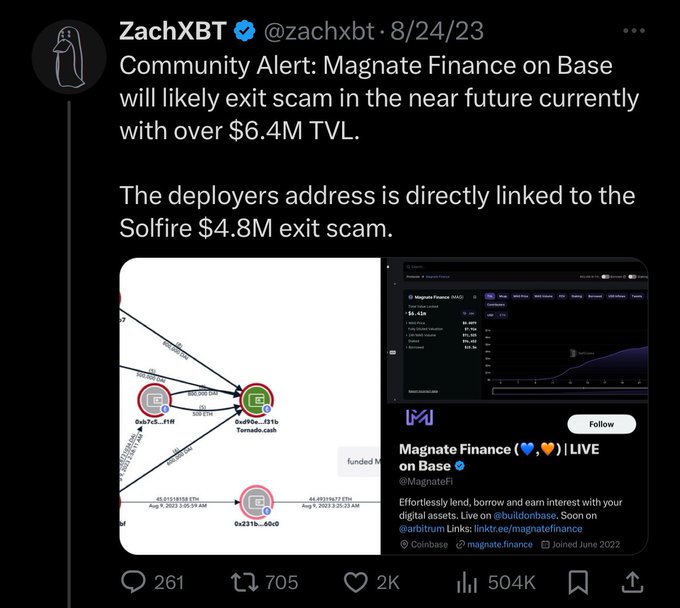
Hopefully these community powered investigations will help capture these scammers.
Community Alert: The group of scammers who stole 8 figs with Magnate, Kokomo, Lendora, Solfire, etc is back with a new project on Blast
@Leaperfinance
Last week they funded an address on Blast with ~$1M of laundered funds from the previous rugs and have begun adding liquidity
356
2K
6K
0
0
1
@HackingLZ
@simplylurking2
it's varying. some npm had 2 people using them. some have an easy 1K users. depends. but stil if you end up using these npm or their dependencies you get RCEd with a reverse shell.
0
0
1