wei
@XiaoWei___
Followers
2K
Following
88
Statuses
21
virtualization and webbrowser security researcher
People's Republic of China
Joined July 2018
RT @mj0011sec: 0Click Windows Tcpip RCE found by Kunlun Lab. We offer intel services for proactive defense to critical vulnerabilities. Con…
0
3
0
Glad to progress with my friends.I got #2 this time.Thanks msrc and my friends.
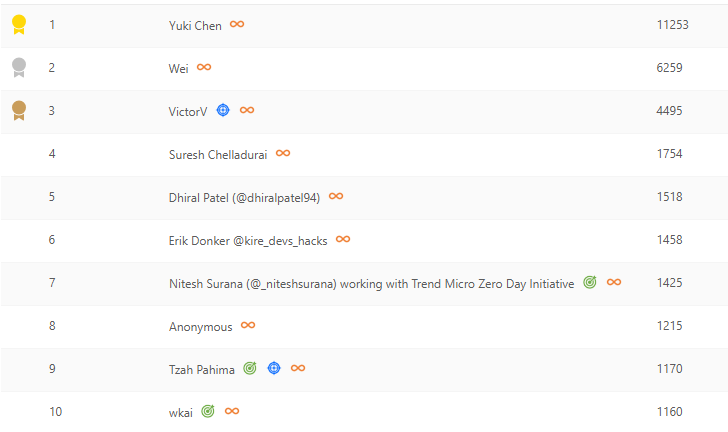
The Microsoft Researcher Recognition Program offers public thanks and recognition to security researchers who help protect our customers by discovering and sharing security vulnerabilities under Coordinated Vulnerability Disclosure. Today, we are excited to recognize this year’s 100 Most Valuable Researchers (MVRs), based on the total number of points earned for each valid report. Please join us in celebrating this year’s MVRs, including our top 10: 1. 🥇 Yuki Chen @guhe120 2. 🥈Wei @XiaoWei___ 3. 🥉VictorV @vv474172261 4. Suresh Chelladurai 5. Dhiral Patel @dhiralpatel94 6. Erik Donker @kire_devs_hacks 7. Nutesh Surana @_niteshsurana working with Trend Micro Zero Day Initiative @thezdi 8. Anonymous 9. Tzah Pahima @TzahPahima 10. wkai See the full list of this year’s 100 MVRs, in addition to our Azure, Office, Windows, and Dynamics 365 leaderboards: #bugbounty #infosec
3
0
22
@Synacktiv @soaphornseuo @BrunoPujos @OnlyTheDuck @ekoparty I have this bug for several years. It is a good bug.I have a very stable exploit for it.
0
1
8
@_nafod haha,I have made a ckeck.If host have a bluetooth and it's turned on,then virtual bluetooth will be a default device.
0
0
3
@thezdi @abdhariri @fluoroacetate @abdhariri @fluoroacetate It seems that the bug can not be triggered with default configuration in vmware workstation. There are a usb hub devive and a hid device with default config. In my debugging,they don't support bulk endpoints. Did i do anything wrong?
0
0
3