Yuki Chen
@guhe120
Followers
10K
Following
212
Statuses
369
古河, Indepent security researcher, Bug bounty, ACG Otaku, Pwn2Own 15/16/17, PwnFest16,TianfuCup 18/19/20, 5 times MSRC MVR yearly Top 1. Got two pwnie awards.
Joined September 2013
I've made my 5th yearly Top1 on MSRC leader board, glad that I'm still able to push myself forward as an independent security researcher and achieved #1 in both Windows and Azure research area with a record high score. Congrats to all researchers on the leader board this year.
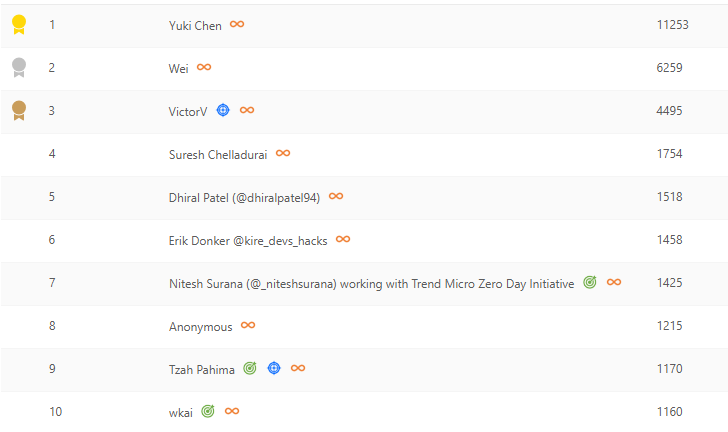
The Microsoft Researcher Recognition Program offers public thanks and recognition to security researchers who help protect our customers by discovering and sharing security vulnerabilities under Coordinated Vulnerability Disclosure. Today, we are excited to recognize this year’s 100 Most Valuable Researchers (MVRs), based on the total number of points earned for each valid report. Please join us in celebrating this year’s MVRs, including our top 10: 1. 🥇 Yuki Chen @guhe120 2. 🥈Wei @XiaoWei___ 3. 🥉VictorV @vv474172261 4. Suresh Chelladurai 5. Dhiral Patel @dhiralpatel94 6. Erik Donker @kire_devs_hacks 7. Nutesh Surana @_niteshsurana working with Trend Micro Zero Day Initiative @thezdi 8. Anonymous 9. Tzah Pahima @TzahPahima 10. wkai See the full list of this year’s 100 MVRs, in addition to our Azure, Office, Windows, and Dynamics 365 leaderboards: #bugbounty #infosec
13
11
185
Congrats!
Congratulations to everyone on the list. Thanks for the support from MSRC. It's really hard to be top1 once, @guhe120 is kami of MSRC!🫡
2
0
12
There were multiple LDAP related vulneraiblites fixed in Dec, and ironicly, CVE-2024-49112 - with the highest CVSS score - is actually less exploitable than some others IMO😂 I may cover this topic in some security conference this year
Here is the ironic side of vuln response based on CVSS score - especially when it comes to binary vulns. Everyone cares about CVE-2024-49112 because MS assigns CVSS 9.8 to this vulneraiblity, but never forget the score is highly affected by the skills of the analysis team behind
2
11
84
@hackingspace To avoid confusion, the PoC by SafeBreach is not CVE-2024-49112 but another information leak bug fixed in the same month
0
3
12
Nice analysis but it seems this PoC is an information leak bug (CVE-2024-49113 ?) I reported that is incorrectly tagged as DoS. So instead of calling it LDAPNightmare I'd prefer LdapBleeding. And @msftsecresponse could you please help to correct the bulletin🤣?
Starting 2025 strong! We’ve developed a PoC exploit for CVE-2024-49112. Read the blog and check out the GitHub repo: Just the beginning of the great things SafeBreach will deliver this year; stay informed at #CTEM #whatisPropagate
2
25
139
Write an Exp to pop shell and get your tickets to @REverseConf @offbyoneconf, BTW I like the password to the zip file 😆
Think you’ve got what it takes to pop shells and snag your ticket to... @REverseConf and @offbyoneconf ? 😏
4
1
29
Hello @msftsecresponse, is there any legitimate process inside MSRC to escalate an issue if I beleive it's not assessed properly and fairly by current engineering team?
7
4
58
Just returned from the SAS2024 and really enjoyed the event. Everything well organized, good tecnical topics, beautiful sights. Everyone had lots of fun no matter you attend the conference as a listener or speaker. Highly recommended. #TheSAS2024
1
0
39
Will discuss some examples/experiences/tips for looking for pre-auth RCE bugs in Windows compontents and reporting them to WIP bug bounty program. See you at #TheSAS2024
A favorite APT tool and an expensive bug bounty item: pre-auth RCE in Windows components. How do you find and report them? Join the #TheSAS2024 talk by Yuki Chen (@guhe120), the MSRC Most Valuable Security Researcher and winner of Pwnie and Tianfu Cup, to tap into their practical experience of WIP participation. ⏩ Agenda and tickets:
2
17
133
Congrats!🥳🥳
A lucky year🥳 Really thanks to MSRC and bounty team for their helping. I really appreciate my mentor @XiaoWei___ and @guhe120 , they inspired me a lot. I'm also grateful to my company @KunlunLab and colleagues. And congratulation for all researchers on the list🥳🥳🥳
0
0
13
Achieved #1 this quarter, thanks!
Shoutout to the top 10 researchers in the leaderboard on X: 🥇Yuki @guhe120 🥈Lewis & Ver & Zhiniang (@edwardzpeng, @Ver0759, @LewisLee53) 🥉Wei @XiaoWei___ Nitesh @_niteshsurana Sathish @SathishOFC
@scwuaptx Felix Dhiral @dhiralpatel94
2
0
51
RT @DarkNavyOrg: Our new blog post, "Exploiting Steam: Usual and Unusual Ways in the CEF Framework" Usual way: V8 + sandbox exploit for CE…
0
37
0