5unkn0wn
@5unKn0wn
Followers
1K
Following
3K
Statuses
442
Taeyang Lee, a security researcher at @theori_io.
Seoul, Republic of Korea
Joined February 2017
@mrexodia @BackEngineerLab All obfuscated functions are composed of huge loop-based MBA instructions. However, through identifying meaningful register (or memory) access near the first access point, we can reveal each MBA's input/output patterns. This allows us to analyze the original algorithm efficiently
0
0
10
gg
Theori, 2024 사이버공격방어대회(CCE) 종합우승 🏆 CCE 일반부에 참여한 티오리 4개 팀이 1, 2, 3, 4등 모두 차지했습니다! 🥇 종합우승 'The Duckling': @junorouse, @5unKn0wn, @_bincat, 성해빈 🥈 일반부 우승 'The Gosling': 강우원, @RBTree_, @yechan_bae, 김현태 🥉 일반부 준우승 'GYG': @s0ngsari530, @bbbig12 🎖 일반부 장려 '군필': @imssm99 티오리 인턴들도 청소년 부문에서 우수한 성적을 거뒀습니다. 🥈 청소년부 준우승 '냥코': 권율, 맹서현 🥉 청소년부 장려 '솜사탕은씻어먹어요': 도원준 이번 우승으로 티오리는 지난 2019년-2022년 종합우승, 2023년 일반우승에 이어 6번째 우승을 달성합니다! 사이버공격방어대회(CCE)는 국가정보원 주최, 국가보안기술연구소가 주관하는 국내 해킹방어대회입니다. 티오리는 국내외 CTF에서 우승하며 세계 최고의 사이버 보안 역량을 끊임없이 입증하고 있습니다. 참여하신 모든 분들 고생하셨습니다. #Theori #티오리 #CCE #CTF #Winner #Hacking #Hacker #Cybersecurity
0
1
14
Fav chall: Helium implements ephemeral key exchange through slightly modified libhydrogen. The most painful but fun part was analyzing whole inlined sse3 functions and identifying modified algorithms. After exchanging the key, we can read the flag via arbitrary file read vuln😋
🏆 Theori Wins DEF CON 32 CTF and DARPA AI Cyber Challenge (AIxCC) Semifinals! 🏆 We are thrilled to announce that Theori has once again emerged victorious at DEF CON 32 CTF—the world-renowned "Hacker Olympics"! With this win, Theori secures its 8th overall victory and an unprecedented three consecutive titles—the most in DEF CON history! DEF CON CTF is the largest and most prestigious hacking defense competition in the world, attracting the brightest cybersecurity talents globally. Theori's CTF team, The Duck, teamed up with Maple Bacon from @UBC and PPP from @CarnegieMellon to form the record-breaking team Maple Mallard Magistrates (MMM). But wait, there's more! Riding the wave of our DEF CON victory, Theori has also advanced to the finals of the AIxCC competition, an AI Cyber Challenge hosted by Defense Advanced Research Projects Agency (@DARPA ). Out of countless competitors, only 7 teams made it to the finals, and we're proud to be among them, securing a $2 million prize. This double achievement is more than just a record—it's a testament to Theori's unrivaled expertise in cybersecurity and our unwavering drive to push the boundaries of innovation. A huge shoutout to all the amazing teams who made it to the finals for both DEF CON and AIxCC—you all brought fierce competition! And a big thank you to the organizers who make this event outstanding every year. What's next? As we celebrate this historic win, we're already gearing up for the next big challenge. Stay tuned for more groundbreaking innovations from Theori! #DEFCON32 #DEFCONCTF32 #Theori #Cybersecurity #TheDuck #MMM #AIxCC #DARPA #HackerOlympics
0
0
29
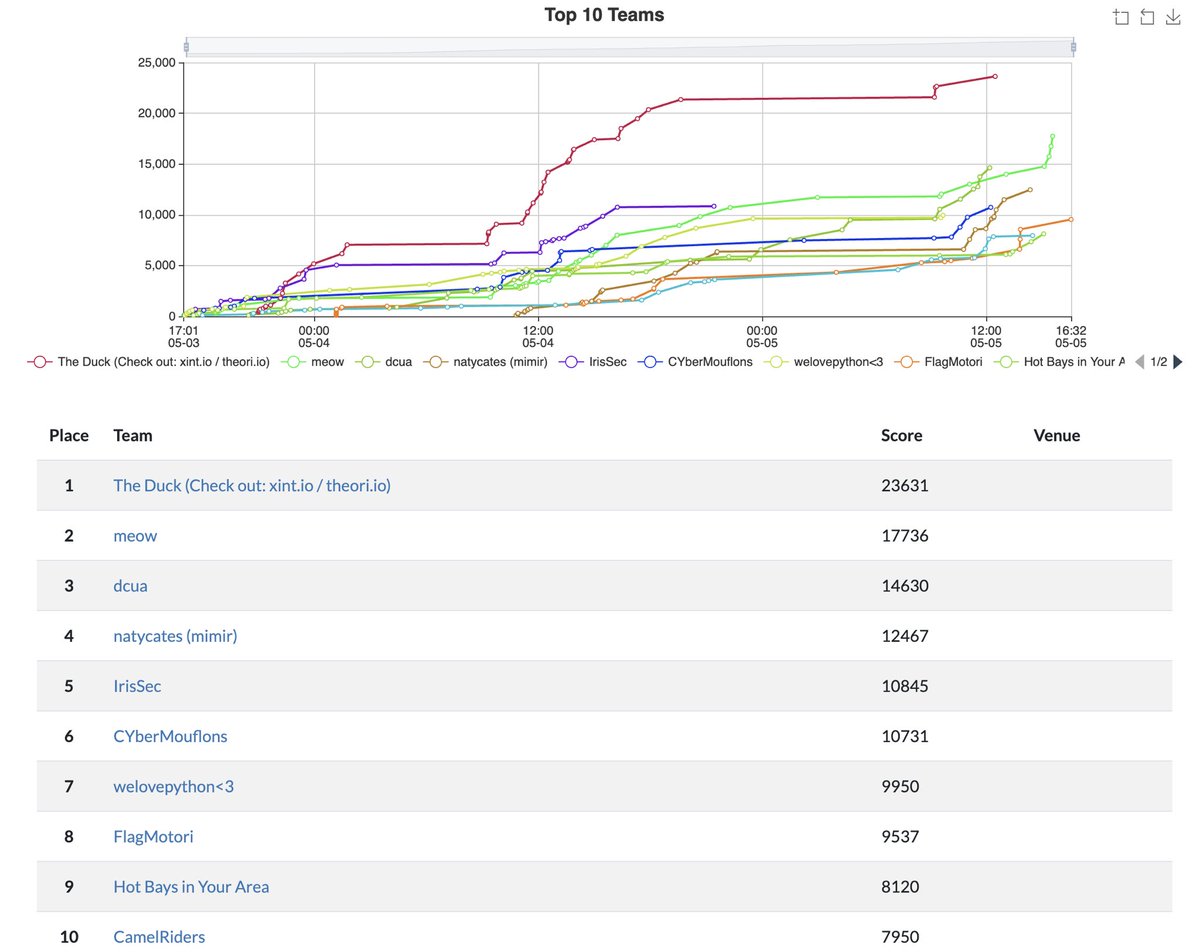
Ran priority scheduling for playing multiple ctf 🤭
Two birds with one stone? Nah more like two CTFs with one duck! 🏆🦆 Theori sweeps both the @BSidesSF CTF and @defcon qualifiers at the top of the leaderboard! Congrats to our teams #TheDuck and #MMM for first place! Curious what these genius hackers are further capable of? Check out our newest security solution at @RSAConference Booth 634! #Theori #티오리 #DEFCON #BsidesSF #BsidesSF2024
1
1
25
RT @binarly_io: 🚨Breaking news from the lab: Finding the Hidden Threats Posed by Dead and Vulnerable Code Primitives Our REsearch team hig…
0
18
0
RT @theori_io: Do you use a virtual machine to browse dangerous links safely? If you use the Chrome browser inside that virtual machine, is…
0
267
0
@junorouse @YQ996CO28254695 @fenbushi @titanbuilderxyz @ultrasoundmoney @sui414 @flashbotsmev @TenderlyApp eat, sleep, pwn, repeat 😋
0
0
1
RT @Blackhatmea: ألف مبروك لفريق The Duck الفائز بالمركز الثاني في مسابقة #التقط_العلم ضمن فعالية #بلاك_هات23، وجائزة 200,000 ريال 👏🏻👏🏻 @N…
0
6
0