Charlie Miller
@0xcharlie
Followers
73,924
Following
72
Media
1,199
Statuses
19,503
Explore trending content on Musk Viewer
President
• 1795990 Tweets
Supreme Court
• 1254283 Tweets
SCOTUS
• 631379 Tweets
Ronaldo
• 616804 Tweets
Portugal
• 443515 Tweets
Canada
• 415686 Tweets
Constitution
• 266987 Tweets
Diogo Costa
• 250292 Tweets
Klay
• 186384 Tweets
سلمان
• 109747 Tweets
Oblak
• 90300 Tweets
Corinthians
• 86752 Tweets
رونالدو
• 79437 Tweets
فرنسا
• 65900 Tweets
Sesko
• 49743 Tweets
#البرتغال_سلوفينيا
• 46396 Tweets
#poupettekenza
• 45775 Tweets
#PORSVN
• 42905 Tweets
كريستيانو
• 32787 Tweets
オスカル
• 28702 Tweets
#PORSLO
• 26113 Tweets
アンドレ
• 22693 Tweets
フェルゼン
• 22182 Tweets
Penaldo
• 21263 Tweets
Wesley
• 19509 Tweets
Bruno Fernandes
• 18757 Tweets
كوستا
• 18697 Tweets
Veiga
• 15781 Tweets
Jhon Jhon
• 15609 Tweets
ポルトガル
• 14919 Tweets
ロナウド
• 12836 Tweets
الدون
• 11133 Tweets
Last Seen Profiles
This seems like an impossible task to me. The director of the NSA makes 197k a year (with no equity). Glassdoor says the AVERAGE appsec engineer at facebook makes 195k. How can you recruit elite talent in that market?
72
166
1K
As a former NSA guy, watching the community reverse engineer this exploit makes me think of all the people who developed it sitting and crying somewhere as it’s secrets are spilled.
27
127
1K
This is lame. In Pwn2Own, if you hack a fully patched system, you win. I don't care if the vendor knew about the vuln. If they knew about it, they should have patched it. This is a win, plain and simple.
It's a partial win. Despite the great demonstration (with ASCII art), the bug used by
@alisaesage
had been reported prior to the contest. It's still great work, & we're thrilled she broke ground as the 1st woman to participate as an independent researcher in
#Pwn2Own
history.
89
22
166
14
175
983
@GovParsonMO
Hi governor, I’m a Missouri resident and a computer security expert. You’re totally wrong here, there was no unauthorized access and reporting security issues is encouraged in our field (so they can get fixed!). The alternative are flaws never getting fixed. cc:
@stltoday
4
51
783
When you watch this do you wonder about hackers taking control of the car? Myself and other team members have been working for almost four years to make that really hard to do. So far so good 😊
Watch the most advanced robot in the world driving—without hesitation or confusion—through a bunch of anxiety-inducing scenarios.
@Cruise
’s technology is rapidly rocketing beyond human driving capability. So exciting.
36
178
963
8
84
513
After 1.5 years, today I'm moving on from
@Uber
. I've enjoyed the challenge of making their autonomous cars as secure as possible.
39
68
393
So
@keen_lab
just dropped a really awesome paper about hacking BMW cars. Get it here: . What follows in my analysis (1/21):
3
201
333
Super interesting paper (as usual) by
@keen_lab
. It talks about how Tesla autopilot works and how what happens if attacker can get code execution on it.
3
88
204
i love how people are shocked that
@apple
doesn’t like security researchers (see
@CorelliumHQ
drama), meanwhile i’ve been banned from doing research for them for 8 years.
11
60
195
Its easy to criticize security decisions if you don't understand the tradeoffs involved. Let me explain why Twitter made various security decisions, right or wrong. Remember I was Twitter appsec tech lead a while back so I have some insight.
7
77
194
Another interesting paper by
@keen_lab
about car hacking, this time a Mercedes. I read the car hacking papers (this one is 86 pages) so you don't have to! Thoughts in this thread (1/8)
2
62
185
You may recall me and
@nudehaberdasher
hacked a 2014 Jeep Cherokee. We chose that car because it had no gateway module between the telematics module and the modules with physical controls. I just looked at the 2020 model, there is still no gateway module.
13
36
160
Second edition of my book on fuzzing (with
@JaredDeMott
,
@attekett
, and
@aritakanen
) pre-sale available now 30% off, see flyer for details.
10
50
160
@chrisrohlf
that’s the thing, it’s not really lots of eyes but it just takes one pair and there’s lots of lonely guys in their basement (like me)
3
0
155
I love that this job req calls me out by name but i don’t meet their requirements...
@0xcharlie
Automotive Security Researcher
Do you know who Kevin Mahaffey and Marc Rogers are? How about Charlie Miller and Chris Valasek? Do you want to be in their line of work, but for national security purposes?
1
0
1
10
26
149
Privacy concerned users switching to worse privacy protecting apps because Signal does something privacy preserving better than other apps but not perfectly. Welcome to infosec!
6
32
147
When I was appsec tech lead at twitter, this would have been a major headache to fix. Now i just get to enjoy it! Cool work.
4
14
145
This is really about apple making money, but he is correct.
Sideloading Apps Would ‘Break’ the Security and Privacy of iPhone, Says Tim Cook by
@SamiFathi_
53
91
980
10
15
142
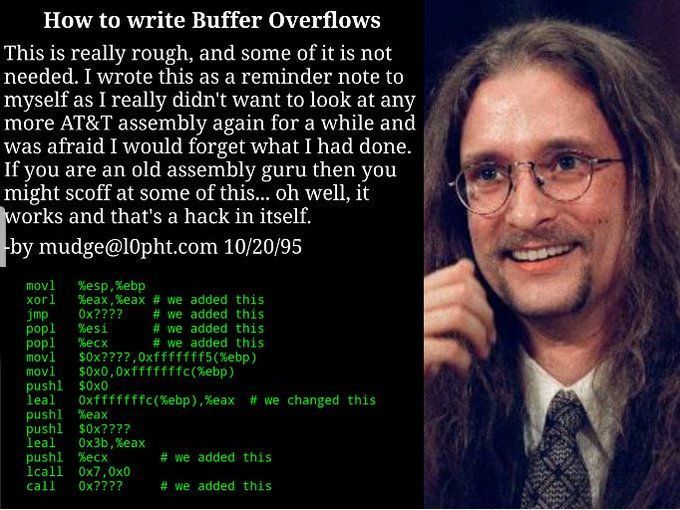
I read these papers almost 20 years ago when I was getting started. If you haven’t read them, you should!
1995: Mudge published "How to Write Buffer Overflows", one of the first papers about buffer overflow exploitation. Then
@dotMudge
sent a copy to
@aleph_one
, who wrote "Smashing the Stack For Fun and Profit" in 1996. Seminal paper to seminal paper. Mudge's:
4
301
839
4
25
140
I'm reading the Apple iOS security doc:
http://t.co/UA85iiKe
and its amazing because Apple never talks about security in detail like this.
12
139
135
I planned a short romantic getaway with my wife
@genderteach
at Half Moon Bay while I was at
#CISOFORUM
. She had to cancel at the last second but I soldiered on as best I could without her.
3
14
135
If the existence of 0-days changes your threat model, you’re doing threat modeling wrong.
4
33
131
I say this about once a year but my biggest accomplishment of being
@Twitter
appsec tech lead was migrating them off imagemagick.
So, here is another gift for you about Imagemagick RCE 0-day that afftceted to GhostScript-9.50 😀
#RCE
#imagemagick
#ghostscript
14
328
826
1
13
131
Even though everyone, and especially
@ryanaraine
, hates when I say it,
@BlackHatUSA
should only contain highly technical talks. Less-technical talks are what RSA is for. (Also, there shouldn't be a "business hall" or pay-to-speak slots). Yes I lose this argument every year.
15
6
126
Will miss you
@dakami
. You were a cool dude. Personally, I learned a lot about public speaking from you and aspired to give talks like you.
1
4
129
watching
@natashenka
preach attack surface reduction. About 90% of my day job is trying to reduce attack surface...
1
31
129