Binni Shah
@binitamshah
Followers
137,400
Following
186
Media
4,930
Statuses
33,845
Linux Evangelist, Malwares , Security Enthusiast, Investor, Contrarian , Neurology , Philanthropist , Reformist ,Sigma female. Born to break rules and banality
India | NY
Joined March 2009
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Kendrick
• 312668 Tweets
Taylor
• 269338 Tweets
Super Bowl
• 265988 Tweets
Drake
• 181034 Tweets
JENNIE
• 143530 Tweets
#TommyHilfigerNYFWxPPGF
• 135587 Tweets
Giants
• 119073 Tweets
Steelers
• 110551 Tweets
Wayne
• 109626 Tweets
Bears
• 107010 Tweets
JISOO AT NYFW WITH TOMMY
• 88689 Tweets
NYFW24 WITH GEMINI FOURTH
• 88034 Tweets
#ZEVENT2024
• 84828 Tweets
Cowboys
• 83096 Tweets
Bengals
• 81657 Tweets
Browns
• 77959 Tweets
Panthers
• 68387 Tweets
Falcons
• 56552 Tweets
重陽の節句
• 50656 Tweets
Raiders
• 48045 Tweets
Chargers
• 41890 Tweets
Seahawks
• 39660 Tweets
Broncos
• 35109 Tweets
Daniel Jones
• 32642 Tweets
Baker
• 29577 Tweets
#GHDBT1
• 27124 Tweets
Caleb Williams
• 27112 Tweets
Seattle
• 27046 Tweets
#わたしの宝物
• 25776 Tweets
Cleveland
• 24594 Tweets
Deshaun Watson
• 23619 Tweets
Tom Brady
• 22196 Tweets
Forbes
• 18281 Tweets
Diggs
• 13220 Tweets
Zeke
• 11999 Tweets
Bo Nix
• 11030 Tweets
Will Levis
• 10962 Tweets
チャウヌ
• 10186 Tweets
Last Seen Profiles
How to build a TCP proxy (Part 1) : Intro :
Fake DNS Server (Part 2) :
Proxy Server (Part 3) :
Fake Certificate Authority (Part 4) : cc
@RobJHeaton
12
762
2K
Imhex : A Hex Editor for Reverse Engineers, Programmers and people that value their eye sight when working at 3 AM : credits
@WerWolv
20
492
2K
ImHex : A Hex Editor for Reverse Engineers, Programmers and people who value their retinas when working at 3 AM : credits
@WerWolv
28
354
2K
Tsurugi Linux : A heavily customized Linux distro designed for DFIR investigations, malware analysis and Open Sourced intelligence activities : cc
@Sug4r7
||
@blackmoon105
|| tsurugi_linux
8
528
1K
Reverse-Engineering : A FREE comprehensive reverse engineering tutorial covering x86, x64, 32-bit ARM & 64-bit ARM architectures : credits
@mytechnotalent
7
320
1K
Offensive Software Exploitation (OSE) Course : credits
@binaryz0ne
Ref : HTID (Hacking Techniques and Intrusion Detection) :
27
347
1K
The Illustrated TLS Connection - Every byte of a TLS connection explained and reproduced : cc
@xargsnotbombs
8
408
946
GHunt : Introducing an OSINT tool to investigate Google Accounts to find their real name, physical location, devices , their devices etc : credits
@mxchreborn
8
268
892
Beginner-Network-Pentesting : Notes for Beginner Network Pentesting Course : cc
@thecybermentor
Full 15-hour video :
5
309
862
Passhunt - a simple tool for searching of default credentials for network devices, web applications and more. Search through 523 vendors and their 2084 default passwords : cc
@ManiarViral
4
373
849
qrcp : Transfer files over wifi from your computer to your mobile device by scanning a QR code without leaving the terminal : cc
@daw985
8
305
834
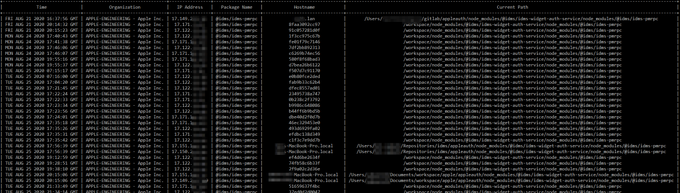
How I Hacked Into Apple, Microsoft and Dozens of Other Companies - The Story of a Novel Supply Chain Attack : credits
@alxbrsn
9
226
817
hexyl : A command-line simple hex viewer for terminal (It uses a colored output to distinguish different categories of bytes (NULL bytes, printable ASCII characters, ASCII whitespace characters, other ASCII characters and non-ASCII) ) : cc
@sharkdp86
11
316
826
ImHex : A Hex Editor for Reverse Engineers, Programmers and people who value their retinas when working at 3 AM : credits
@WerWolv
10
172
813
WiFi Hacking Cheatsheets & Mindmap + Headless Pwnbox/RogueAP Project based on Raspberry Pi : credits
@Xst3nZ
6
255
787