Akshay Srivastav
@akshaysrivastv
Followers
3,134
Following
560
Media
28
Statuses
903
Independent Security Researcher | Smart Contract Auditor | SR @SpearbitDAO | Top warden & lookout @code4rena
Joined January 2016
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
بايرن
• 525039 Tweets
بولونيا
• 507270 Tweets
Wizkid
• 336588 Tweets
Davido
• 308142 Tweets
Bayern
• 61369 Tweets
Shakira
• 52872 Tweets
Centro Carter
• 48507 Tweets
Shana Tova
• 46102 Tweets
KARIME EN HOY
• 37526 Tweets
Gago
• 37063 Tweets
Rosh Hashanah
• 36081 Tweets
GALA EN HOY
• 35464 Tweets
Lille
• 34986 Tweets
Aston Villa
• 25336 Tweets
Bologna
• 20296 Tweets
Girona
• 17798 Tweets
Channie
• 15436 Tweets
Anfield
• 14181 Tweets
Bank of America
• 14091 Tweets
Feyenoord
• 12520 Tweets
Camavinga
• 12190 Tweets
Play BabyDoge PAWS
• 10496 Tweets
Last Seen Profiles
A short exercise that I suggested to some new auditors to level up their audit game
- Pick up a past
@code4rena
contest (small one)
- Spend a weekend to find all bugs in it
After you are done, open up the results of that contest and analyze two things:
14
69
252
I reported 1 High and 1 Medium severity bugs in Chainlink CCIP codebase during their
@code4rena
contest
The results were announced today and I was able grab the 2nd spot
This was the top contest of this year on C4. A highly reputed protocol & $300K rewards
24
7
209
Today Bonq protocol suffered a $120 millions oracle manipulation attack.
But how was the attacker able to manipulate prices on
@BonqDAO
and how was
@WeAreTellor
leveraged to perform the attack. Details here 👇👇👇
28
47
173
I was on a break for a while but now I am back at audits
A couple of personal updates:
- I've joined
@SpearbitDAO
as an ASR
- I'm also now a lookout at
@code4rena
where I'll be helping in contest judging
I'll be jumping straight into audits once I'm back from
@ETHIndiaco
23
2
104
Everyone is competing in Solidity based audit contests
But $280,000 are up for grabs right now for non-solidity smart contract audits
$100K Cairo contest on
@code4rena
$80K Rust contest on
@HatsFinance
$50K Rust contest on
@cantinaxyz
$50K Rust contest on
@secure3io
LG anon.
6
5
94
Extremely happy and thankful to be back at leaderboard ranking of
@code4rena
- Top 10 in 2023
- Top 4 in last 90 days
Sharing the stage with all these legendary auditors feels really amazing. They all are geniuses of this competitive audits industry 🔥🔥
13
7
81
Audit report for the
@OndoFinance
contest on
@code4rena
is public now
This one is my best contest yet ($10K+ rewards).
Total bugs found: 1H + 5M
Some of the bugs found in the code are unique and some are generic ones (which can help you in your next contest)
10
7
84
The guys at
@code4rena
know how to keep the auditors motivated.
I opened their site to check the new UI revamp and saw my name on their main page, among the elite C4 auditors🤩
I still have a lot to learn from those OGs. The UI refresh looks great, a huge thnks fr the mention🫡
8
2
82
One of my CT friend notified me that I'm in the Top 4 wardens of last 60 days
@code4rena
leaderboard.
Web3 security is a highly rewarding field and the hard work really pays off🙏
6
1
73
Another achievement unlocked✅
All thanks to
@code4rena
for providing open opportunities to everyone to come forward make positive impact in the web3 security space🙌
Awards have been announced for the $60,500 USDC
@OndoFinance
competition!
Top 5:
🥇
@akshaysrivastv
- $11,205.52 USDC
🥈
@hansfriese
- $7,517.41 USDC
🥉
@bin2chen
- $5,956.16 USDC
🏅 adriro - $3,616.11 USDC
🏅 zaskoh - $2,821.71 USDC (1/2)
4
2
45
11
1
67
Starting my morning with this good news. It feels good to find bugs and get paid in doing so.
✅ Goal to secure a place in the top 5 of a
@code4rena
contest achieved (I got
#4
). Now onto the next one💪💪
9
1
70
During this audit I really got into my “audit flow” and ended up reporting 15 HMs (7 High & 8 Medium severity) bugs.
I’m happy with the result and will share some interesting findings once report is published.
Awards have been announced for the $81,500 USDC
@tangibleDAO
audit 🤝
Top 5:
🥇
@akshaysrivastv
- $4,064.72 USDC
🥈 Haipls - $3,226.37 USDC
🥉
@iamdirky
- $3,061.13 USDC
🏅 SpicyMeatball - $2,743.91 USDC
🏅 nemveer - $2,634.73 USDC (1/2)
1
2
31
9
1
68
It took just 3 weeks for the top 3 guys to earn $800K
But it also took exceptional talent and years of hard work to find critical bugs that hundreds of other competitors missed
Kudos to all the winners
Fortunately I also found two medium severity bugs in this contest 🙏
Awards have been announced for the $1.1m USDC
@zksync
Era audit 🎉 🎉
Top 5:
🥇 xuwinnie - $502,041.99 USDC
🥈 ChainLight - $157,696.85 USDC
🥉 Audittens - $140,480.81 USDC
🏅 minhtrng - $38,573.19 USDC
🏅 erebus - $25,342.88 USDC
Read more at:
26
45
398
2
0
66
In this session I talked about
- my audit strategies
- my audit process
- and my way of finding bugs
Feel free to check it out👇
Discover the different approaches to smart contract auditing and the tools and techniques that top auditors use with
@akshaysrivastv
. Insights on auditing, mindset, and tools. Learn how to avoid missing bugs and look into unexpected places. 👀👀👀
7
9
58
7
9
57
In my world Alice and Bob are the two most innocent users who somehow always end up losing money💸💸
#Security
#ProofOfConcepts
9
2
51
LiFi devs are 100% aware about the next steps to stop the today’s attack
Why??
Bcoz they faced the EXACT SAME attack back in March 2022
It’s hard to believe how you can introduce the exact same bug in your protocol twice
@lifiprotocol
8
4
49
On
@code4rena
the bugs you find give you earnings, and the bugs you miss give you learnings.
Both are good for auditors.
3
2
46
Solid codebase with just 4 medium severity issues.
If this would have been a private audit then even these top auditors would have just found one or two issues.
The value that competitive audits provide is far greater than the traditional ones.
Awards have been announced for the $90,500 USDC
@AragonProject
competition!
Top 5:
🥇
@carlitox477
- $17,746.25 USDC
🥇
@adrianromero
- $17,746.25 USDC
🥈 V_B (
@vladbochok1
, barichek) - $8,058.25 USDC
🥉 0x52 - $7,985.81 USDC
🏅
@akshaysrivastv
- $6,215.37 USDC (1/2)
6
3
52
2
0
45
Another way to keep the IMMUTABLEs uninitialized is to initialize them in a failing "try { }" block
In this example the "try" call always fails leaving the immutable var to be uninitialized (set as 0)
4
1
45
My first AMA, show some ❤️ guys.
Do you have any questions/thoughts about web3 security or smart contract audits?
Drop them here👇👇👇
Warden spotlight:
@akshaysrivastv
🔎
In the last 90 days, they’ve earned $18k+ from 18 findings. They’ve also provided insightful analyses of web3 security in the past, so if you’ve got any questions for them, now’s your chance!
Drop them in the replies below ⬇️
20
12
77
4
1
37
Nearly 3 weeks have passed since I suggested this exercise to improve anyone’s auditing skills
I’ve received many thankful DMs explaining how impactful this exercise is for new auditors
Some of them are even making this a regular biweekly task
Securing web3 together 🤝🤝
A short exercise that I suggested to some new auditors to level up their audit game
- Pick up a past
@code4rena
contest (small one)
- Spend a weekend to find all bugs in it
After you are done, open up the results of that contest and analyze two things:
14
69
252
0
1
36
I received plenty of questions in this tweet and I tried to answer them all.
Ranging from getting started with auditing, my audit approach, common bugs, to tips for getting rewarded in C4 contests.
Thanks again
@code4rena
for the spotlight 🙏
Heads up, I’m still answering…
Warden spotlight:
@akshaysrivastv
🔎
In the last 90 days, they’ve earned $18k+ from 18 findings. They’ve also provided insightful analyses of web3 security in the past, so if you’ve got any questions for them, now’s your chance!
Drop them in the replies below ⬇️
20
12
77
3
2
35
Creating TWAP oracles for fully on-chain prices is a difficult problem to solve.
Just be aware that any TWAP over:
- pools with low liquidity, or
- shorter time duration
is not very difficult to manipulate.
A similar thing happened in this exploit
#ImmunefiSecurityAlert
1/ On July 11, an exploit on
@Rodeo_Finance
resulted in a loss of ~472 ETH, valued at roughly ~$890,000.
This was caused by what’s known as an oracle manipulation attack.
Let’s break this hack down in a human-readable format
👇
2
24
100
1
4
35
If you are an auditor who compete in public audit contests or plan to compete in future then do check out this alpha packed session by
@GalloDaSballo
.
I got the opportunity to be part of this session. All thanks to
@code4rena
🙌
How to find your submissions after a competition, thoughts on automated tools, how to best format a QA report, and more: it’s all in our latest Office Hours session with
@GalloDaSballo
+ guest Warden
@akshaysrivastv
🫡
Watch it now for all the alpha 🤝
2
13
37
3
2
34
This is 100% true
Crypto twitter only shows you the story 50 successful auditors who are earning 6-7 figures
Just be aware that there are thousands who didn’t make it
Hate to break it to the new auditors out there, but the truth is that independent auditing is only financially rewarding for the top 10-20% whether through audit contests or private audits. You can check the
@code4rena
and
@sherlockdefi
leaderboards and try getting private audits
41
14
160
4
0
33
A developer mindset thinks about how to make the code do what it intends to do.
An auditor mindset thinks about how to stop the code from doing what it intends to do.
#SmartContractHacking
0
5
28
There is no typo here, nearly 200 auditors reported the same 11 bugs in the codebase and most of them ended up earning less than $500.
Days in competitive audit space are not always bright and sunny✌️
The report is in for
@rabbithole_gg
's January audit competition with C4 🔎
In securing this protocol, C4 Wardens uncovered:
High risk: 110 total, 2 unique
Medium risk: 143 total, 9 unique
Gas reports: 50
QA reports: 89
Read more:
0
1
22
4
0
27
@MattGladson
@BonqDAO
@WeAreTellor
The mechanics of maintaining an oracle are too tricky. Only chainlink has somehow pulled it off.
In this case the mistake was on Bonq’s end, Tellor is supposed to provide instant and older prices.
2
1
24
The idea that the act of creating open-source code can be legally punishable is an extremely scary thought
#RandomThought
#NotRelatedToAnyRecentCryptoIncident
1
2
23
Thanks to
@blockthreat
for including one of my bug analysis in this week's newsletter🙏
If you don't already know Blockthreat is now a "must read newsletter" if you are in web3 security.
Do check out the Blockthreat newsletter here:
2
3
23
C4 just launched their Pro League🏆🏆
Top tier auditors collaborating to secure your protocol. You cannot ask for anything better.
I am happy to be a part of it. Let's go chads🚀🚀
Introducing Code4rena Pro League 🏆
⭐ All-star auditors
🔒 Custom security services
🥇 The best security talent including
@cmichelio
,
@samczsun
,
@hellocccz
,
@IAm0x52
,
@xuwinniexu
,
@zachobront
, and more!
Read more:
14
127
242
1
2
23
The timeline on is really a great feature. You can see all live and upcoming contests on a flat calendar.
Till now I was using Google calendar to view and manage contests but not anymore.
Great work ser
@GalloDaSballo
🫡🫡
1
0
23
Official LiFi statement about the $10M attack
“The incident was caused by an individual human error in overseeing the deployment process”
Web3 industry needs to figure out secure deployment and upgrade standards for decentralised protocols
1
1
23
This most basic change is way too error prone
In Solidity the design pattern of ‘require’ and ‘if-revert’ statements are completely opposite
Make sure you transition from one to another safely 🤞
1
0
21
Do check out my recent discussion with
@ImmuneBytes
@Aabhassood
In this chat we discussed about all security related things of our web3 space 👇👇
ImmuneBytes presents 📺 'Web3 Ninja'.
Meet the two veterans
@Aabhassood
(Founder & CEO
@ImmuneBytes
) and
@Akshaysrivastv
(Smart Contract Auditor, Top warden
@code4rena
) discussing the evolving nature of security challenges in the
#Web3
space.
Full episode:
1
5
16
0
2
18
Appreciation from the best ❤️
@CyfrinAudits
@trailofbits
@OpenZeppelin
@ConsenSysAudits
@SpearbitDAO
@trust__90
@dedaub
@sigp_io
@MixBytes
@WatchPug_
@HalbornSecurity
@code4rena
@sherlockdefi
@CertoraInc
But also... Don't discount solo auditors!
-
@pashovkrum
-
@IAm0x52
-
@zachobront
-
@romanboehr
- cccz
-
@akshaysrivastv
-
@0xKaden
And there are a LOT more I'm missing, but these are some great smart contract auditors I've seen in this space.
3
1
50
0
0
17
@0xc86
@code4rena
1. Yes i do keep track to all public state changing functions and money exit function. They are always the key piece😉
2. I read about the bugs I missed. Also I’m very fond of reading about recent hacks. Most of my hack analysis comes naturally. So that keeps my skills sharp.
2
1
16
I was lucky enough to report one of the three med-severity bug in this contest.
Feels good to help
@PoolTogether_
in securing their smart contracts.
More details in the public report👇
The findings are in for
@PoolTogether_
's December 2022 audit competition with C4 🔎
In securing the PoolTogether smart contracts, C4 Wardens uncovered:
• 10 total, 3 unique medium-sev vulnerabilities
• 8 QA findings
• 4 gas optimizations
Read more:
1
1
27
3
0
17
Hey
@_iphelix
I think you leaked too much alpha here on Blockchain Threat Intelligence.
Really a great talk🫡🫡
1
5
16
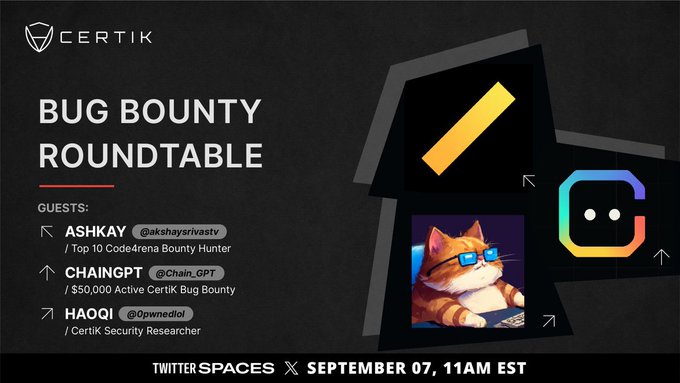
Want to explore web3 bug bounties?
Catch me live with
@CertiK
tomorrow👇👇
Join us tomorrow, Thursday the 7th at 11am ET, for a panel on bug bounties in Web3.
Featuring top 10 bounty hunter
@akshaysrivastv
,
@Chain_GPT
, and CertiK's own ethical hacker/security researcher
@0pwnedlol
28
25
384
0
1
16
Slots booked 🔒
See you there
@eulerfinance
Welcome... to the new largest competition in history with
@eulerfinance
!
💰 $1,250,000 USDC
🗓️ May 20th - June 17th
📍
@cantinaxyz
Invite only. Don't have one? Details below:
97
155
295
1
0
15
Why is that the smart contracts of a permissionless protocol containing millions in user funds are not hosted publicly on Github?
@BonqDAO
Their website doesn't even mention Github anywhere.
Found but the source code isn't there.
2
0
15
@boredGenius
I am having a hard time explaining people how I find bugs in DeFi protocols and make a living out of it 🥲
1
0
14
@PlutusCrypto
@gjaldon
@BonqDAO
@WeAreTellor
Yes I think chainlink was also integrated. There was some aggregation or ratio of both price feeds. But since the price by Tellor was so high, chainlink price was nullified.
8
0
12
4 year old unknown bug just got exploited 🚨
0
1
11
@0xleastwood
The interesting thing is those selling courses learned sc security from open resources
0
0
12
@peak_bolt
@code4rena
After a few contests self assessment becomes the key piece. At that time you already have some data points, like things you lack at, things you are good at, codebases that you enjoy, etc.
You just need to work on those and optimize.
The second point I shared in the tweet is
2
0
10
@0kage_eth
@immunefi
Maybe a ban from ImmuneFi should be publicly announced, just like how a new bounty is announced
0
0
11