HE1M
@0xHE1M
Followers
1,246
Following
87
Media
7
Statuses
50
Explore trending content on Musk Viewer
Kendrick
• 294191 Tweets
Super Bowl
• 253672 Tweets
Defense
• 232734 Tweets
Ronaldo
• 184954 Tweets
Drake
• 167583 Tweets
Patriots
• 137258 Tweets
Giants
• 114541 Tweets
Steelers
• 105468 Tweets
Bears
• 104848 Tweets
Wayne
• 102484 Tweets
Bengals
• 78959 Tweets
Cowboys
• 76589 Tweets
Dolphins
• 66848 Tweets
Panthers
• 65937 Tweets
Browns
• 62319 Tweets
Falcons
• 55273 Tweets
Titans
• 51436 Tweets
JISOO AT NYFW WITH TOMMY
• 49476 Tweets
Colts
• 43358 Tweets
Texans
• 39916 Tweets
Raiders
• 34095 Tweets
Seahawks
• 31408 Tweets
Daniel Jones
• 30369 Tweets
Broncos
• 29925 Tweets
Chargers
• 28036 Tweets
#Sinner
• 25817 Tweets
Caleb Williams
• 25593 Tweets
Josh Allen
• 24380 Tweets
Baker
• 20979 Tweets
#深澤辰哉
• 19973 Tweets
Cleveland
• 19906 Tweets
#わたしの宝物
• 19617 Tweets
Bryce Young
• 19332 Tweets
#GHDBT1
• 18912 Tweets
Tom Brady
• 18733 Tweets
Forbes
• 17502 Tweets
TJ Watt
• 16464 Tweets
Deshaun Watson
• 12923 Tweets
Kirk Cousins
• 11313 Tweets
Zeke
• 11277 Tweets
Aubrey
• 10915 Tweets
Will Levis
• 10439 Tweets
Last Seen Profiles
Glad to be part of
@optimismFND
contest in
@sherlockdefi
✨🔴 Optimism 🔴✨contest post-mortem soon 👀
TL;DR
- Top-notch team Sherlock paid to compete found a High Solo (
@zachobront
@trust__90
)
- "Not well-known" security expert found a High Solo
Sherlock is the only auditor in the world who incentives both types of participants 💪
1
4
33
13
4
123
Thanks
@zachobront
and
@andyfeili
I talk to
@zachobront
about his audit process, how he collaborates with other top auditors to find unique bugs and his recent success on
@immunefi
and
@sherlockdefi
.
13
26
127
1
5
65
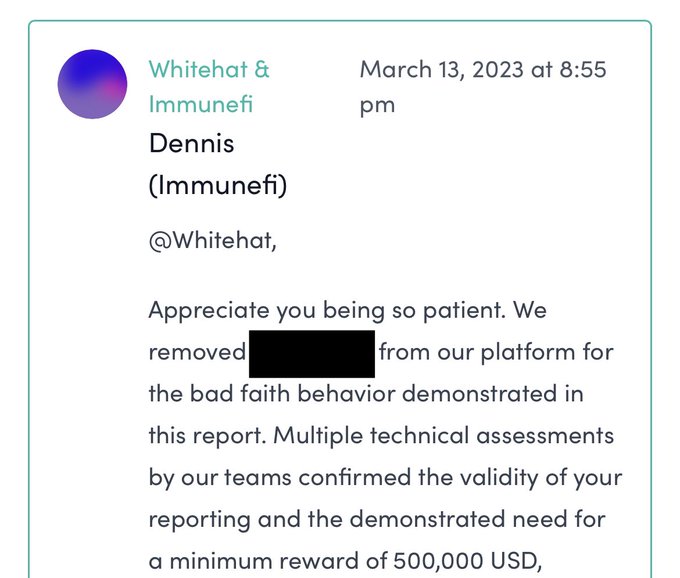
Attack scenario:
- The whitehat reports the finding.
- The project is unresponsive.
-
@immunefi
removes it from the platform.
The project is the winner, and the whitehat is the loser!!!
5
1
42
@0xTendency
@HollaWaldfee100
@xiaoming9090
@WatchPug_
Try to explain the codebase for a person who doesn’t know anything about programming, then you will find out something in the middle of discussion that you were not looking at before. It helps to see the codebase from different points of view.
1
3
29
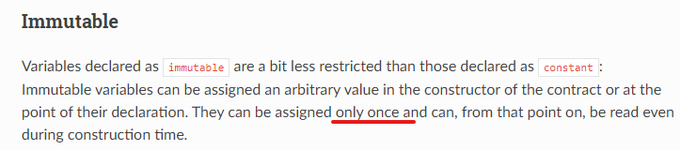
In continuation of Immutables story:
They can be initialized more than once or left uninitialized if using the modifier in constructor.
In other words, by using modifiers we can run the function (to which the modifier is applied) more than once or even skip it.
@solidity_lang
3
3
30
Glad to be part of
@zksync
contest in
@code4rena
(1/2) Awards have been announced for the $165,500 USDC
@zksync
V2 contest!
Top 5:
🥇 Soosh - $70,985.01 USDC
🥈 HE1M - $34,676.27 USDC
🥉 codehacker - $24,571.73 USDC
🏅 0x1f8b - $2,320.96 USDC
🏅 chaduke - $2,102.32 USDC
4
1
40
3
2
27
@hacking_this
@trust__90
You are discouraging a trusted whitehat from saving our ecosystem. The laws you mention as well as other laws are what took our freedom.
2
0
21
Greate finding!
We recently disclosed a high risk double-spend vulnerability in
@AcrossProtocol
's bridge relayer infrastructure. No user funds were at risk! The issue was fixed and awarded with a $90,000 🪲 bounty. Read all the juicy details here:
4
20
71
0
0
6
Again “uninitialized variable”!!!
My bug bounty write-up on a critical vulnerability I discovered on Arbitrum Nitro which allowed an attacker to steal all incoming ETH deposits to the L1->L2 bridge
@icodeblockchain
@samiamka2
@Mudit__Gupta
@0xRecruiter
@BowTiedCrocodil
@BowTiedDevil
63
224
1K
0
0
4
@akincibor1
@immunefi
@wormholecrypto
It happened to me on the aspenLabs project. I reported two bugs, but they were unresponsive. Finally it was delisted from
@immunefi
platform.
0
0
3
@Platypusdefi
First hack, then negotiate!
This is the new approach that white hats are following, because the projects do not behave honestly in bug bounty programs.
0
0
2
@farazsth98
This happens a lot in
@immunefi
. The protocols try to downgrade your report, and Immunefi can not do anything.
Even worse, if the protocol is not responsive at all and you insist on it, Immunefi only finally removes them from platform silently.
1
0
2
@realgmhacker
@immunefi
If a protocol has a bug bounty but no TVL, it is waste of time for white hats if they find critical bug. 😁
1
0
2
@0xAstronatey
Sad to hear that! Projects sometimes do their best to downgrade our findings, that is when a black hat borns😁
1
0
1
@pcaversaccio
A post mortem regarding this feature or bug is explained in details by
@saurik
in optimism
@optimismFND
.
0
0
1