Charlie Bromberg « Shutdown »
@_nwodtuhs
Followers
13,307
Following
652
Media
613
Statuses
3,242
Trying to hack the way we hack things 🏴☠️
Exegol
Joined July 2018
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
SB19 ROCKS ARANETA
• 268866 Tweets
Eminem
• 183696 Tweets
Alex
• 179088 Tweets
NuNew x Poncheewan
• 157279 Tweets
#音楽の日
• 139937 Tweets
Githurai
• 118055 Tweets
#MyLoveMixUpTHep6
• 117400 Tweets
#Mステ
• 110717 Tweets
LAST FOREVER
• 97440 Tweets
#金スマ
• 55353 Tweets
IG Koome
• 48360 Tweets
NiziU
• 48343 Tweets
キングダム
• 44781 Tweets
1 YR OF ELVISH'S BB SAGA
• 36768 Tweets
Cenk
• 33741 Tweets
Medvedev
• 21280 Tweets
土ポーズ
• 10945 Tweets
ジェシー
• 10752 Tweets
Last Seen Profiles
Here are the slides for my talk « Delegating Kerberos to bypass Kerberos delegation limitation » 😈 at
@1ns0mn1h4ck
#INS22
16
238
602
Christmas gift 🎄🎁 from
@m3g9tr0n
and I ✨
You probably already know The Hacker Recipes (), let me introduce The Hacker Tools ().
This project aims at providing documentation on some tools, starting with
@gentilkiwi
's Mimikatz 🥝
9
144
344
Oh yeah 🤘 DACL read/write/backup/restore tooling in Impacket Python. Example screenshot with DCSync, but WriteMembers, ResetPassword and FullControl also possible
🔧 PR:
🧑🍳 The Hacker Recipes:
Co-authored by
@BlWasp_
Something awesome coming your way, brought to you by
@BlWasp_
and I 🥰
We still have some tedious things to deal with, but it's almost ready for a v1 drop
5
12
62
6
134
323
Oh by the way, here are some cypher queries for
#Bloodhound
to find all kinds of Kerberos delegations
2
62
268
Releasing a few things based on S4U2self+u2u, enjoy
- SPN-less RBCD (based on
@tiraniddo
research 🔥)
- Sapphire tickets (based on the 💎Diamond ticket approach by
@SemperisTech
and research by
@gentilkiwi
). Credits also to
@agsolino
@MartinGalloAr
@TalBeerySec
@chernymi
8
99
268
[🔥 thread]
@podalirius_
and I present to you PyWhisker, a powerful, python native, tool that can be used for persistent and stealthy backdooring of user and computer Active Directory objects 😈
2
96
254
Coming soon (on Impacket maybe 🤔?)... brought to you by
@podalirius_
🦋 and I
🐍 Python equivalent to Rubeus's describe command allowing to
- parse tickets
- calculate AES and RC4 kerberos keys
- decrypt the encrypted part of the ticket
- parse the PAC
- ...
(work in progress)
9
53
203
Hang tight Active Directory hackers 😈 In ~24h
@podalirius_
and I will be releasing a Python equivalent to
@elad_shamir
's Whisker allowing for full exploitation of the "Shadow Credentials" attack, combined with
@_dirkjan
's PKINITtools, on UNIX-like systems
2
44
195
SCCM/MECM abuse page update on The Hacker Recipes 🧑🍳 thanks to
@BlWasp_
and
@d34dl0ck_
We love dem diagrams don't we 😊
4
52
190
Btw, by default on 2016 and 2019 domain controllers, attackers can coerce authentications without needing prior knowledge of an AD account's credentials
4
67
183
Cut little box for the
@flipper_zero
🥰, fits with the silicon case and has room for the cable and some other small accessories. Credits to "Draik" and "Ric Thru" on for the case, I only designed the inside wedges.
3
24
167
UnPAC-the-Hash
When validating Kerberos pre-auth using PKINIT, the KDC includes the LM and NT hash of the user in the PAC that the TGT and Service Ticket contain, allowing the attackers to pass-the-hash, create Silver Tickets or use S4U2Self.
➡️
@gentilkiwi
@_nwodtuhs
@MGrafnetter
@elad_shamir
@_dirkjan
PAC-the-hash would be what Kerberos does, and UnPAC-the-hash what we do using tools such as Mimikatz, Rubeus, etc.
#HowDoYouCloseThePollBeforeTheEnd
1
0
5
1
53
158
Having fun right now with the dream team 🤗 thanks
@flipper_zero
for rocking our afterwork 💪
@Wlayzz
@volker_carstein
@pathtaga
@FlowwB
@askilow
so glad to work with you all
5
3
136
Here is an update on the DACL abuse graph. As it turns out, the ReadGMSAPassword case is a bit particular. gMSA accounts are managed by other principals and even a GenericAll on those principals wouldn't allows for direct read of the gMSA's password.
1
46
140
ntlmrelayx now introduces the --no-multirelay flag, why that? Well because in certain scenarios, the multirelay features makes the relay fail.
Scenarios below (🌿🌿🌿) (sheet in progress)
Source:
Hi there! Big update on
#impacket
. Just merged a large PR refactoring ntlmrelayx[.]py!
Includes:
➡️Multi-relay capabilities in HTTP
➡️Multiple HTTP listeners (
@saerxcit
)
➡️ADCS ESC1 and ESC6 attacks (hugo-syn)
➡️Shadow Credentials attack (
@_nwodtuhs
)
1
84
255
3
34
132
Ever wondered how to find IP subnets in an Active Directory environment?
@podalirius_
and I are writing a small CME module for this
(CLI screenshot below made with
@podalirius_
’s LDAPMonitor )
6
29
125
🏆 new achievement unlocked
This awesome BloodHound coin now joins the CME coin! Thank you
@SpecterOps
and
@_wald0
for sending it over ❤️ I’m thrilled you like my contribution to this killer project
10
2
125
3rd place 🥉at
@RedTeamVillage_
CTF with « Team France 🇫🇷 » with colleagues of
@ecole2600
@phreaks2600
@capgeminifrance
@ComcyberFR
@Ubisoft
@GitGuardian
3
7
116
Impacket Pull Request brought to you by
@hacks_zach
@0xdeaddood
@n00py1
and I (yet to be reviewed/merged atm)
Credits also to
@filip_dragovic
and
@mpgn_x64
Ability to do a "reg save" remotely from Python 🐍
If you compromise a member of the Backup Operators group there is a direct path the become Domain Admin without a RDP/WinRM access to the DC !
Dump and export the SAM remotely on a remote share ! 🔥🎉
Thanks to
@filip_dragovic
for the initial POC !
5
291
740
2
34
115
[thread] Hi hackers!
@podalirius_
and I present to you this new tool 🌟🎀 𝖘𝖒𝖆𝖗𝖙𝖇𝖗𝖚𝖙𝖊 🎀🌟
This tool allows for bruteforcing NTLM and Kerberos in Active Directory domains (there are A LOT of features, detailed in the thread below).
➡️
5
36
112
So apparently Microsoft ninja-patched two things lately in KB5014692 (06/14/2022)
1. ShadowCoerce (auth coercion abusing MS-FSRVP)
2. Self-RBCD trick to bypass limitations of Kerberos Constrained Delegation without Protocol Transition
Identified this with
@Geiseric4
and
@mkolsek
1
33
110
Wrapping things up and pushing a pull request on Impacket, followed by guidance on the matter
- Kerberoast trough AS-REQ w/o pre-auth
- Service ticket request through AS-REQ
Again, great work by
@exploitph
Glad to finally get my AS-REQ research out there.
@Microsoft
decided requesting ST's from the AS was by design so here's a couple of ways to Kerberoast without any creds and bypass detections based on 4769's
13
168
440
2
28
104
✨After 8 months of hard work with
@Dramelac_
, now's the time ⏰ Exegol, a community-driven and fully-featured hacking environment, updates to v4.0
An opportunity to show you why you should probably drop your current pentesting env and get started with Exegol (10min read)
6
36
99
For those who missed this, among other huge and awesome features, BloodHound will integrate 3 new edges: AddSelf, WriteSPN, AddKeyCredentialLink
Here’s my take on how you can abuse those from Linux systems
Tomorrow: join us as we show what's new, and what some of our plans for the rest of the year are with FOSS
#BloodHound
:
Recording available afterwards.
1
18
94
1
21
97
RODC attacks, Kerberos key list, RODC golden ticket now on The Hacker Recipes 🧑🍳 thanks to
@BlWasp_
@askilow
@d34dl0ck_
•
•
•
0
27
96
Merci
@1ns0mn1h4ck
🇨🇭!
My talk this morning was « A ticket worth waiting 65 years for »
Slide deck at
For the attendees, hope you liked it, and for the readers, I hope you extract valuable knowledge from it ✌️
5
35
94
That tool is criminally under-starred on GitHub, check it out and try it on your next engagement 🕷️
@BlackLanternLLC
5
27
91
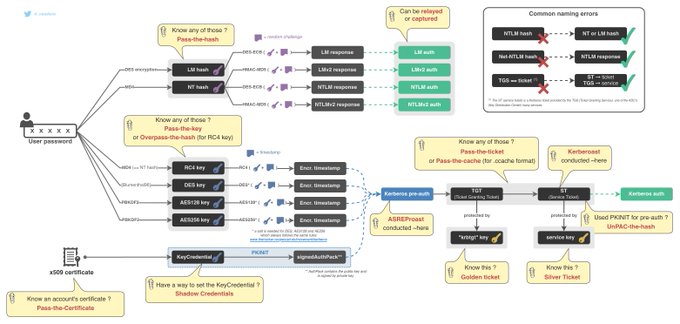
Updated The Hacker Recipes and the "Pass-the-things" mindmap for ASREQroast (=/= ASREProast)
@_nwodtuhs
@drawio
1. Right, AS-REP roasting is mentioned, but AS-REQ cracking is not.
I understand that there are 2 ways of obtaining AS-REPs (encrypted TGTs) for cracking: The more common one is AS-REP Roasting that misuses the DONT_REQ_PREAUTH flag. The second option is performing MITM+tcpdump.
1
1
5
2
20
92
After 3+ years of hard work, 1k+ commits, 10+ contributors, 5k+ users, I am now in London, ready to present Exegol at
@BlackHatEvents
Arsenal on Thursday. I’m honoured 🙏
@Dramelac_
joined the adventure a year ago as lead dev and is accompanying me on this great milestone 🤘🤘
5
11
88
Comme promis, voilà le write-up pour le challenge Richelieu organisé par la
@DGSECOM
have fun ! 🕵️♂️
1
40
83
User A has GenericWrite over User B?
Let’s combine a Shadow Credentials attack with an UnPAC-the-Hash and obtain the NT hash from User B 💪
1️⃣
2️⃣
A lot has happened this year, so you may have missed what is, to me, one of the most exciting attack primitives in a long time -- turning GenericWrite into (effectively) targeted DCSync.
Blog by
@elad_shamir
:
Based on original research by
@MGrafnetter
3
75
173
1
21
79
For the Active Directory curious among us, in case you missed it,
@AlmondOffSec
/
@lowercase_drm
have been releasing a few things lately around SSL/TLS in Active Directory.
A dedicated "SSL/TLS" will be added shortly to The Hacker Recipes.
1
24
82
Kuddos to
@Jenaye_fr
for starting the Evasion part on The Hacker Recipes 🧑🍳
Still a work in progress, there's a lot of ground to cover (obfuscation, process injection, creating loaders/droppers/stagers etc.), but at least we're kicking off things 😁
2
22
80
✨ The Hacker Recipes presents the "delegation to krbtgt" persistence technique
gg to
@volker_carstein
for preparing the recipe!
Shoutout to the usual suspects for the awesome research in
@elad_shamir
@harmj0y
@cnotin
@agsolino
@_dirkjan
and many others
1
19
79
J'ai été invité à reprendre le team lead de l'équipe
#SogetiAcesOfSpades
@sogeti_fr
🥳 et je remercie
@podalirius_
qui a accepter de me seconder sur ce rôle 💪
De belles choses sont à venir et nous sommes impatients de participer aux prochains CTFs !
8
1
72
Printer Bug got a new friend now 🔥 Enabled by default on all Windows machines, hard to disable. This leads to an incoming SMB auth that can be captured or relayed.
➡️ Patch against CVE-2019-1040 and CVE-2019-1166
➡️ Enable LDAP signing and LDAPS Channel Binding
0
27
74
Today I talked about Kerberos delegations at
@_leHACK_
, and what a blast it was! Thanks
@asso_hzv
for hosting me 🙏
Also huge shoutout to
@hackthebox_eu
who sponsored my talk and allowed me to give away 10 VIP vouchers and a Silver Annual pass for HTB Academy 💚
4
5
71
@hackthebox_eu
is sponsoring a feature that will be released very soon ✨multi-architecture support ✨
Thanks to them, Exegol will be supported on ARM64 devices very soon (i.e. raspi, mac M1/2, …)
HTB is a great actor in our community, and now supports Exegol 🥹
Thank you 💚
0
14
71
@rootdump
Shameless plug, but you may find it useful. Includes almost all AD abuse techniques, Linux & Windows commands, mindmaps, theoretical & practical explanations, etc.
4
11
67
Exegol 4.0.5 released today 😎
- You can now enable shell logging to record all commands and outputs during your engagement.
- Changes to the filesystem for hardening and better UX purposes
- Some bug fix & docker SDK upgrade
Gg to
@Dramelac_
@Mathisca_
for coding all that 💪
2
16
69
Two weeks ago, I started a personal challenge on
@hackthebox_eu
that ended yesterday. Here are the results.
📅 2 weeks
👤 19 active users
#⃣ 18 active roots
🤯 2 insane machines
🏴 6 challenges
🏰 1
@Akerva_FR
fortress
🕵️ rank "elite hacker"
I may go to sleep now😴
7
1
65
🧵 Want to abuse Kerberos Constrained Delegation without Protocol Transition using the RBCD technique with Python ? I submitted a PR on Impacket’s getST to allow for arbitrary tickets to be used as « additional-ticket » in S4U2Proxy requests
Credits
@elad_shamir
for the research
1
15
66
GPOddity, now in Exegol (nightly images), will be in the next release images ✌️
⏩ GPOddity
⏩ Exegol
Coming soon in
During a recent Active Directory intrusion test,
@croco_byte
was led to devise a new versatile attack vector targeting Group Policy Objects, allowing their exploitation through NTLM relaying.
6
110
251
0
17
67
On a side note, the target RPC interface can be reached through multiple named pipes
- \pipe\efsr (enabled by default on win 2016 DCs)
- \pipe\lsass
- \pipe\lsarpc (NULL auth accepted)
- \pipe\samr (NULL auth accepted)
1
17
63
🧠 Thanks to a collective brainstorming with
@elad_shamir
and
@HackAndDo
, PyWhisker now features export and import actions to save and restore KeyCreds when conducting Shadow Credentials attacks. (One could also use these features to play with PKINIT👀)
🤝 made with
@podalirius_
1
12
61
Something awesome coming your way, brought to you by
@BlWasp_
and I 🥰
We still have some tedious things to deal with, but it's almost ready for a v1 drop
5
12
62
👨🍳 The Hacker Recipe of the day 🍨 Credential Harvesting from the Windows service LSASS.exe for lateral movement in Active Directory domains
🎙️Featuring
@HackAndDo
's lsassy,
@gentilkiwi
's mimikatz and
@SkelSec
's pypykatz
1
33
60
So thrilled to announce
@Dramelac_
and I will be presenting the Exegol project at
@BlackHatEvents
#BHEU
Arsenal in London 🥳
6
6
58