Lukas Stefanko
@LukasStefanko
Followers
24K
Following
2K
Statuses
3K
Malware Researcher at @ESET Android security, malware analysis, app vulnerability research https://t.co/dnQvb9BCZj https://t.co/7RLveZTSoz
Slovak Republic
Joined December 2014
NetHunter Wi-Fi and Rubber Ducky mobile combo Android NetHunter kernel supports many popular external wifi chipsets including lot of cheap adapters. Rubber Ducky works without any problems on both devices so far. #TicWatchPro #OnePlus7
19
145
586
RT @ESETresearch: #BREAKING #ESETresearch NFC Android malware impersonates banking app in 🇵🇱 Poland. #NGate malware impersonates a banking…
0
29
0
@Matilda_Kiskina @binitamshah It is just another layer of hardening and I understand its inconvenient. So, it is not necessary to disable every time, because Apple pay request user authentication before every payment.
0
0
1
@Matilda_Kiskina @binitamshah Don't enter you card details into untrustworthy websites. Don't put your payment card in back side of smartphone when requested by app. If not using, disable NFC. Protect your card with RFID blocker. Use NFC with your smartphone to pay - the most secure solution.
1
0
1
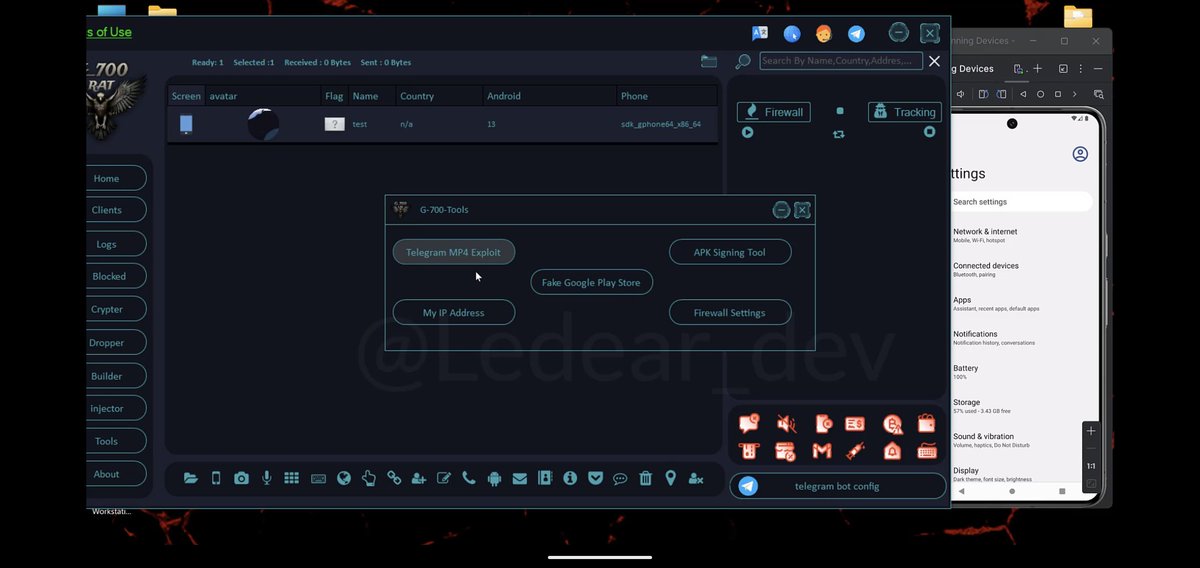
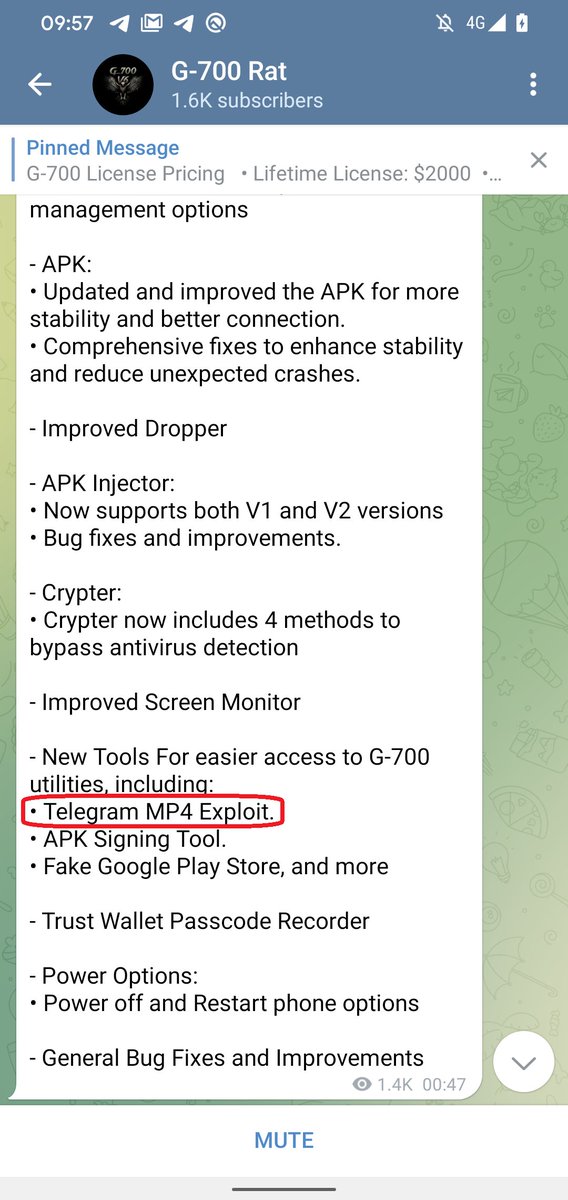
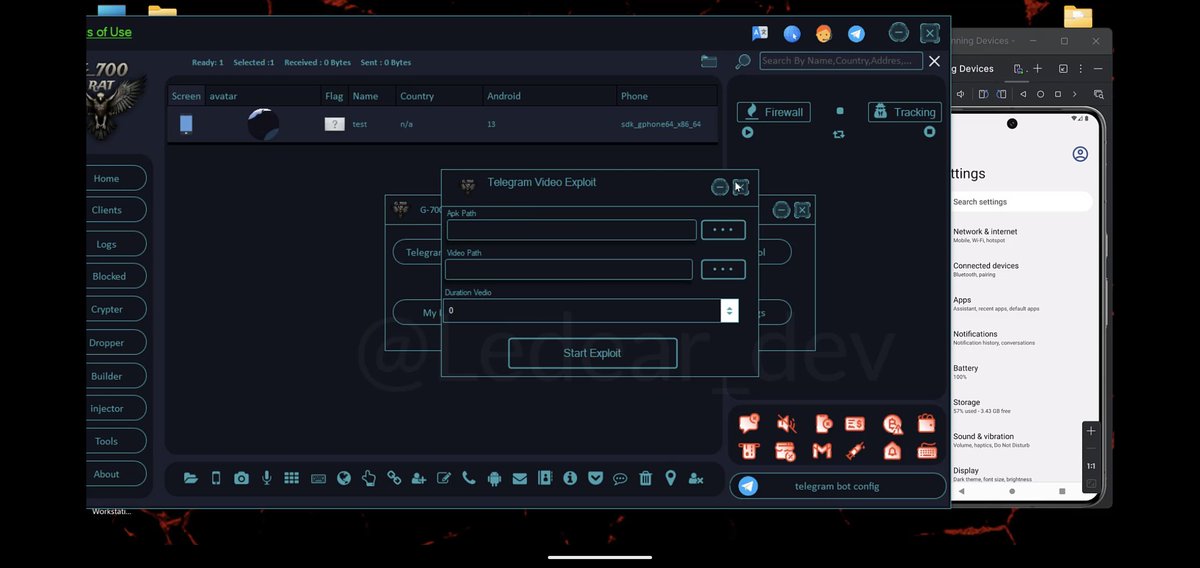
In the latest version of G-700 Android RAT was allegedly added exploitation of the #EvilVideo Telegram vulnerability (CVE-2024-7014) The exploit allows sending malicious APK files disguised as video EvilVideo: G-700 RAT:
2
15
42
RT @binitamshah: Cybercriminals Use NFC Relay to Turn Stolen Credit Cards into Cash without a PIN : credits @LukasS…
0
62
0
RT @ElementalX2: It was great meeting some really cool folks like @LukasStefanko , @Joseliyo_Jstnk @JaromirHorejsi and many others at @a…
0
2
0
Yesterday, I could share my and Jakub research about NFC relay malware #NGate at @avar_asia conference in #India 🇮🇳 In the picture is a screen from a demo where I show how to withdraw cash from an ATM without a physical payment card using smartphone, as was done by NGate TA #ESET
0
3
25
@malwrhunterteam It is #DoNot APT (APT-C-35) C&C: uploadwebpicts[.]store Related to
0
2
4
RT @androidmalware2: Unusual Android malware distribution vector - physical analog letter ✉️ Fake letters were sent to people at their hom…
0
78
0
RT @cherepanov74: BSides Bratislava is back! Save the Date: March 15th, 2025 #BSidesBA 📢 CFP is open until December, 31st 23:59 UTC. Mor…
0
7
0
RT @codeblue_jp: CODE BLUE 2024 Speakers Interview #4 Lukas Stefanko/ルーカス・ステファンコ Jakub Osmani/ヤクブ・オスマニ See for yourself👉
0
1
0
@malwrhunterteam Fake cryptocurrency - most-likely top secret investment method - app C&C: 45.87.153[.]107
0
0
2
RT @ESET: Check out the latest @ESETresearch podcast as @LukasStefanko delves into EvilVideo exploit targeting Telegram’s Android users. S…
0
4
0
Listen the latest #podcast hosted by @goretsky where we talk about #EvilVideo vulnerability (CVE-2024-7014) that affected #Telegram for Android app and allowed attackers to send malicious files posing as videos Info: Podcast:
0
2
11
RT @goretsky: Another @ESETresearch podcast recorded, this time with @LukasStefanko as my guest! It should be available at
0
1
0
@waekYui You are right, not rooted -> rooted -> emulate. I have to use NFC Card Emulator Pro, because NFCGate doesn't properly support NFC UID emulation on my tested OnePlus7, so this was the easy workaround. Your workplace requires only NFC UID to authorize? Not great, not terrible :)
0
0
0
@vl_sk Hi, ngate was distributed via phishing and social engineering. I haven't seen it on Google play or any other app store.
1
0
1