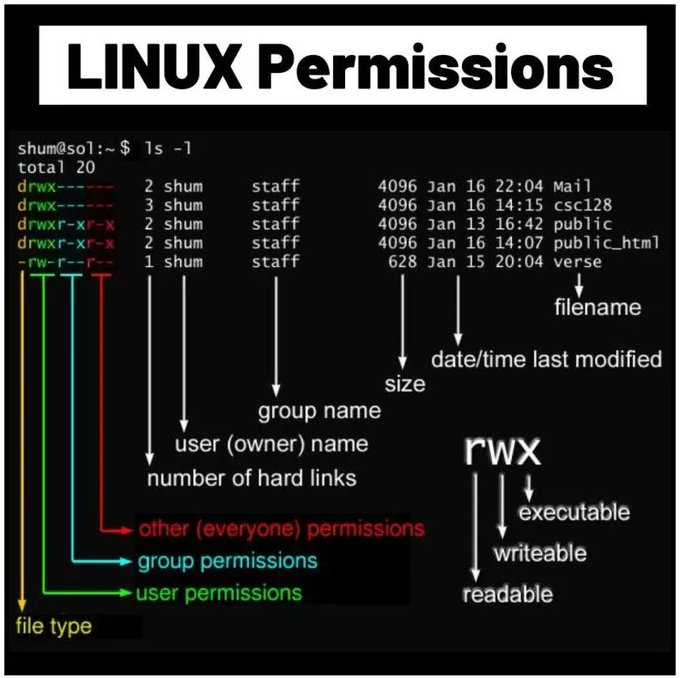
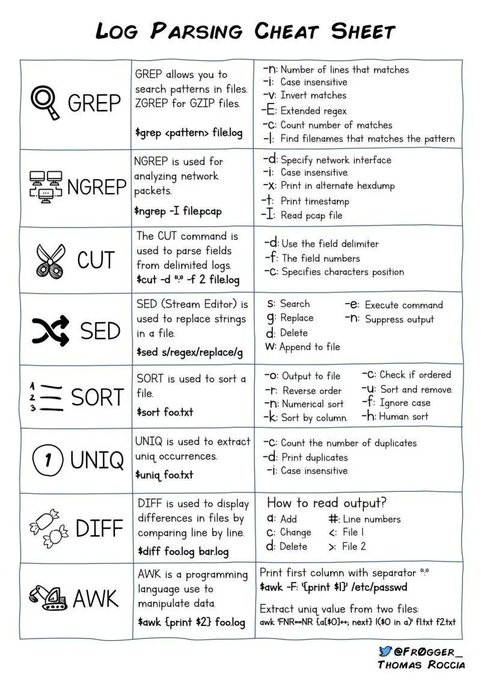
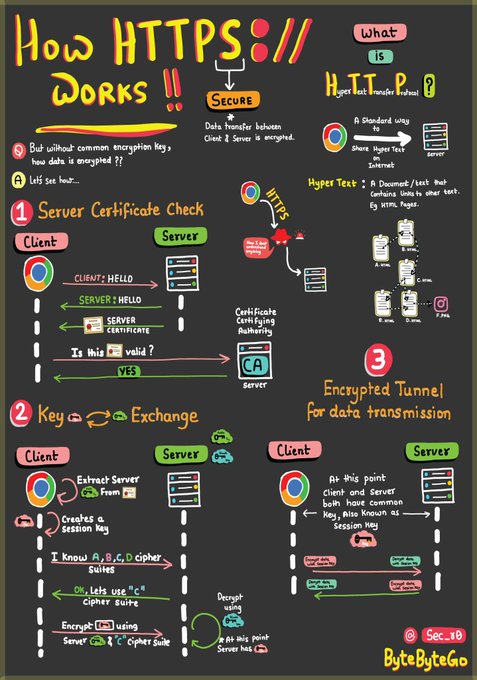
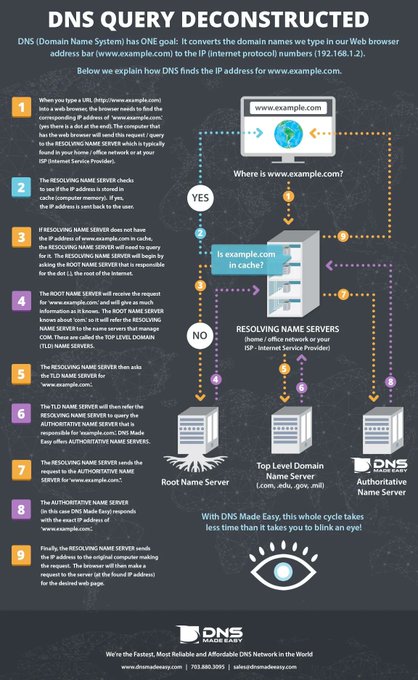
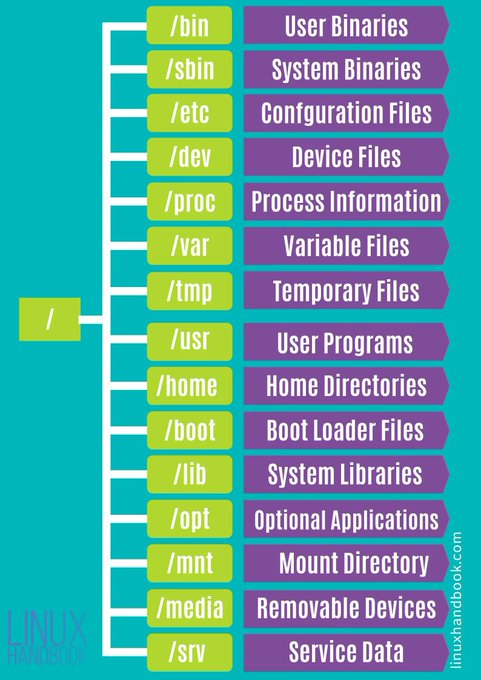
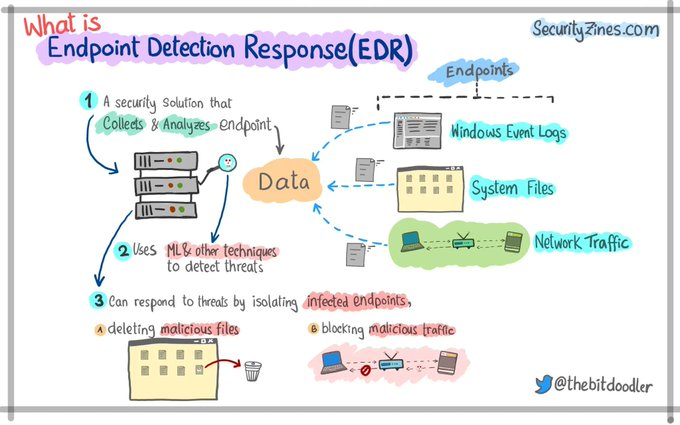
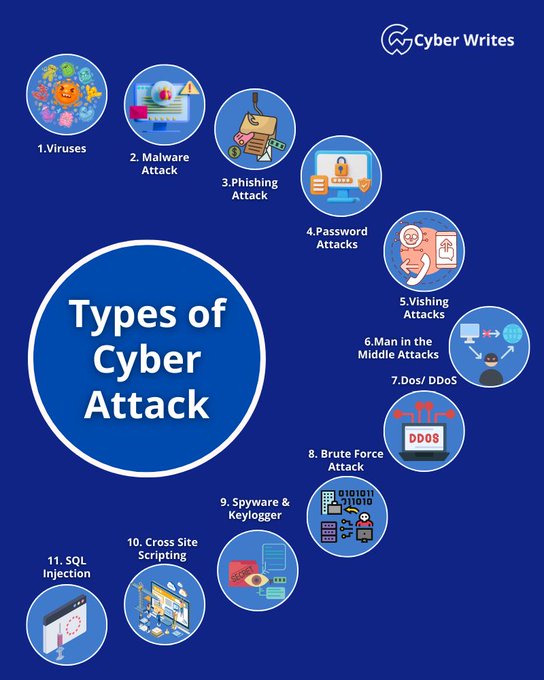
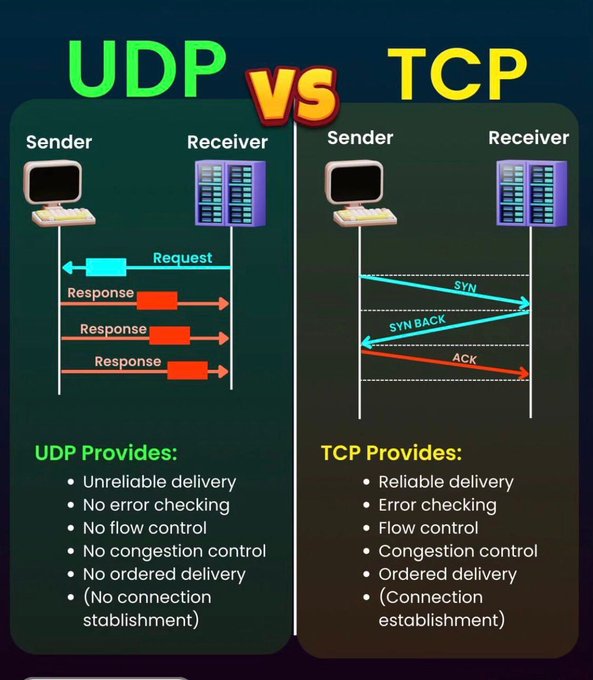
LetsDefend
@LetsDefendIO
Followers
102,902
Following
0
Media
1,560
Statuses
2,108
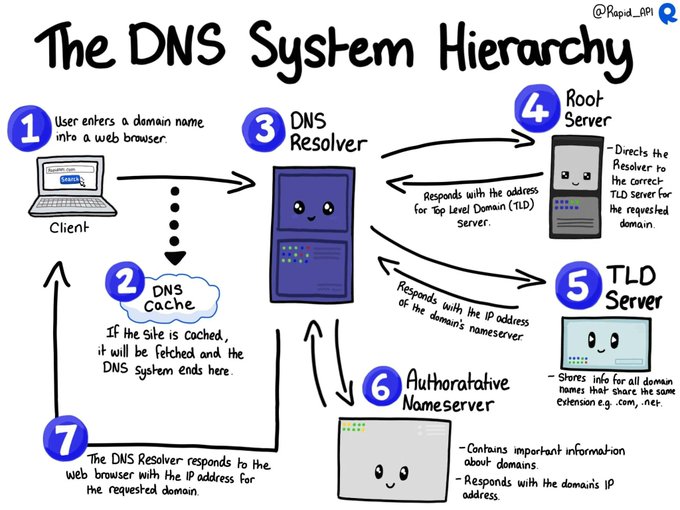
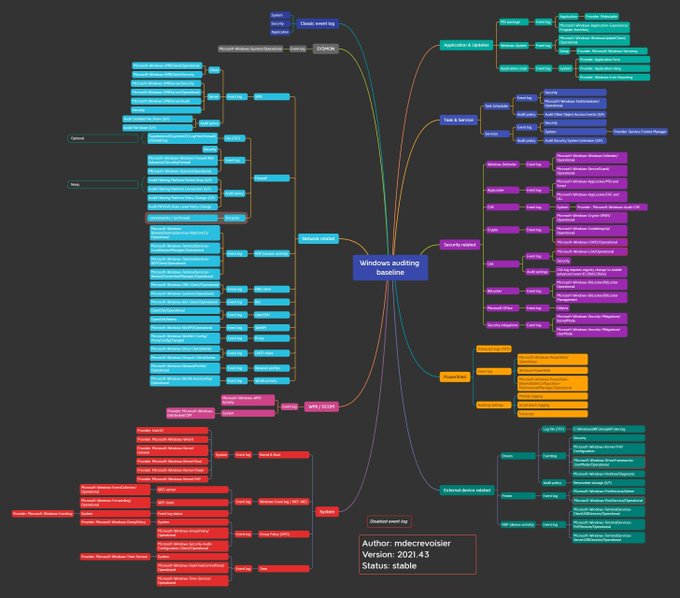
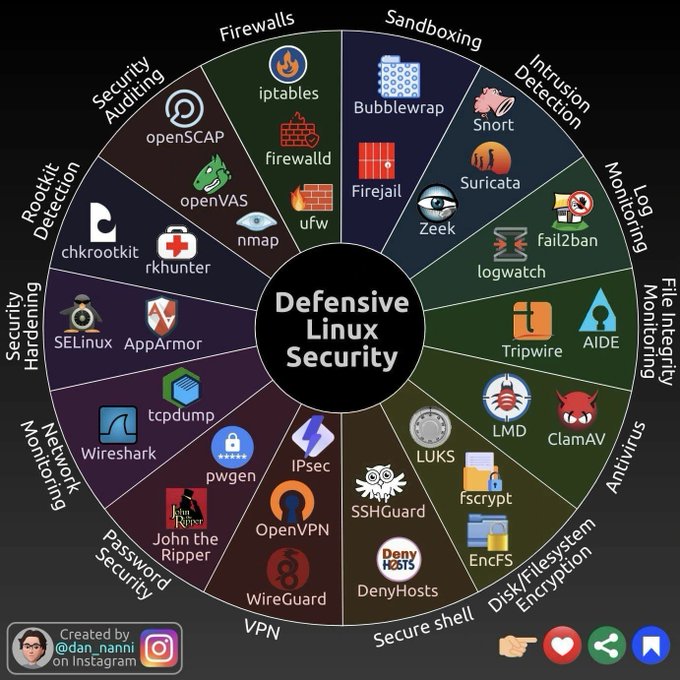
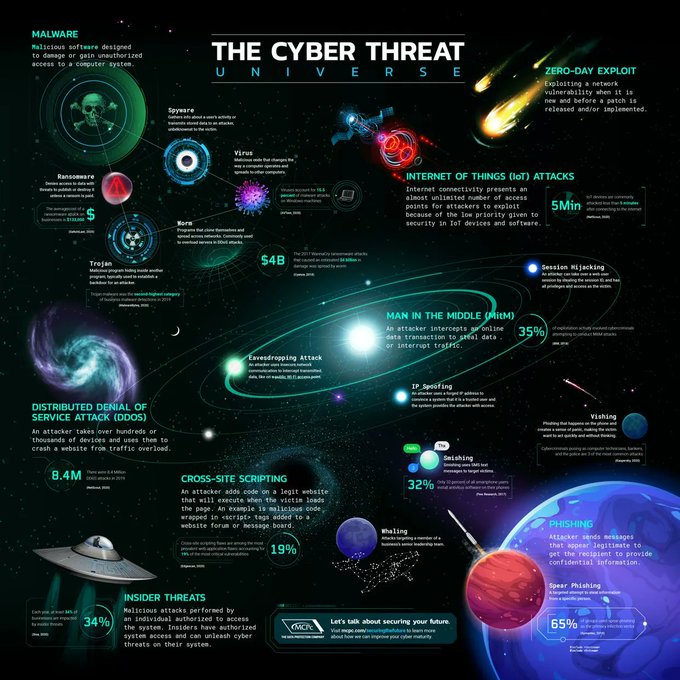
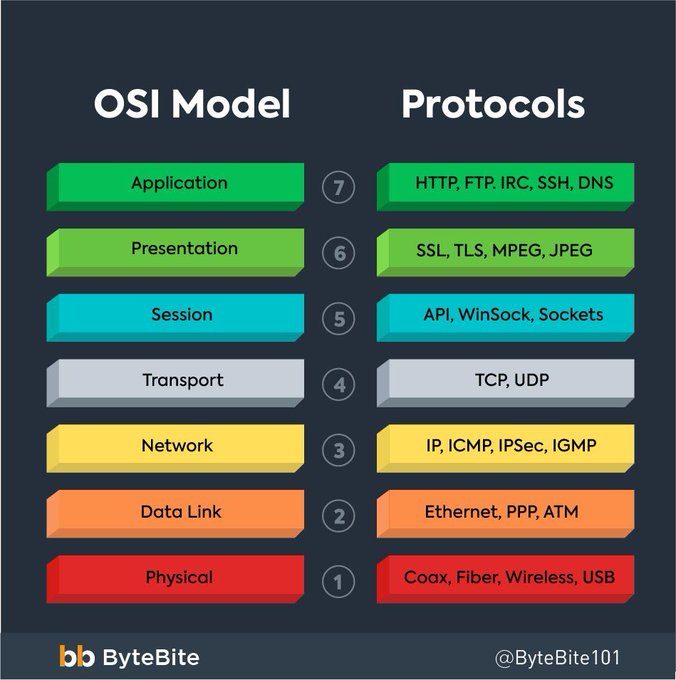
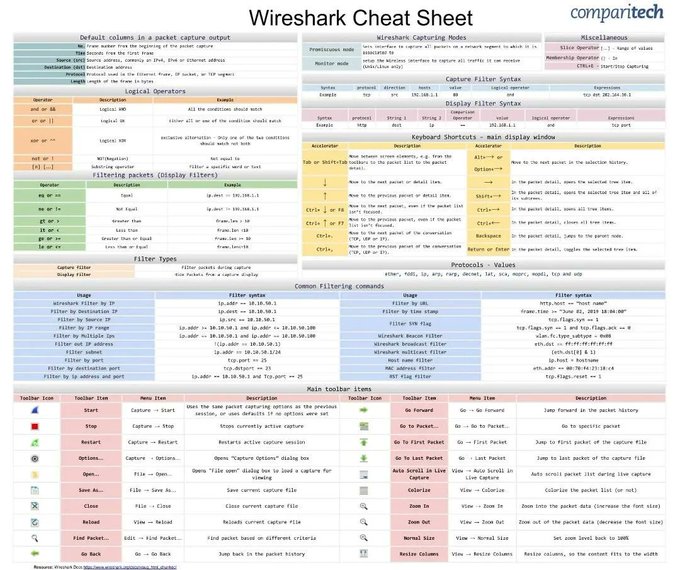
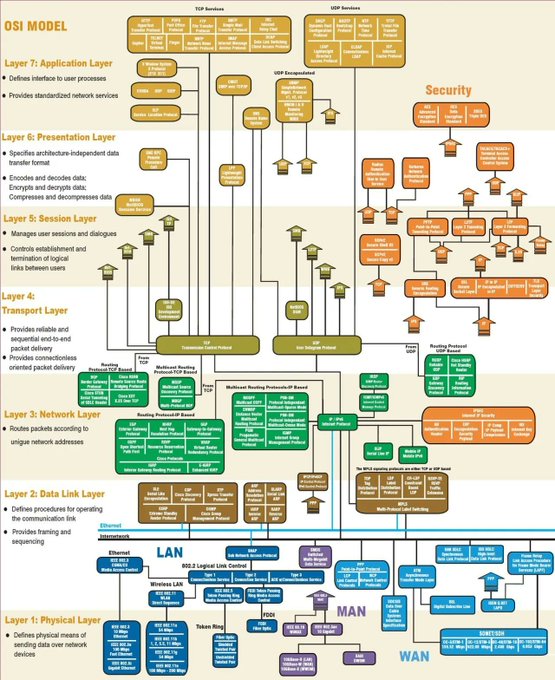
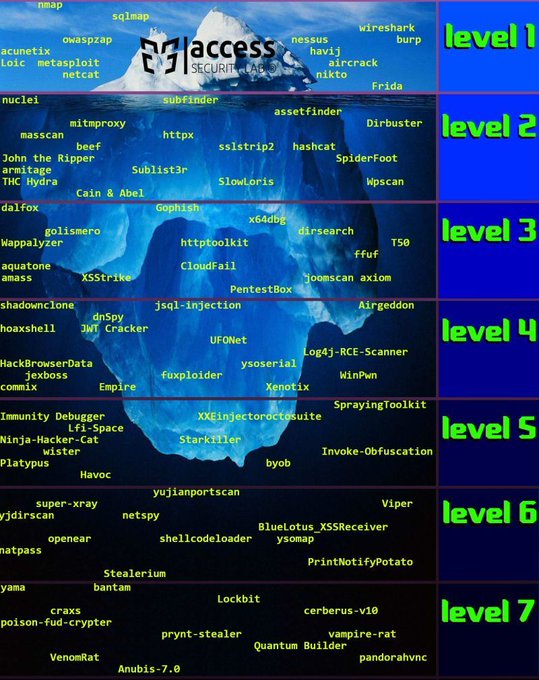
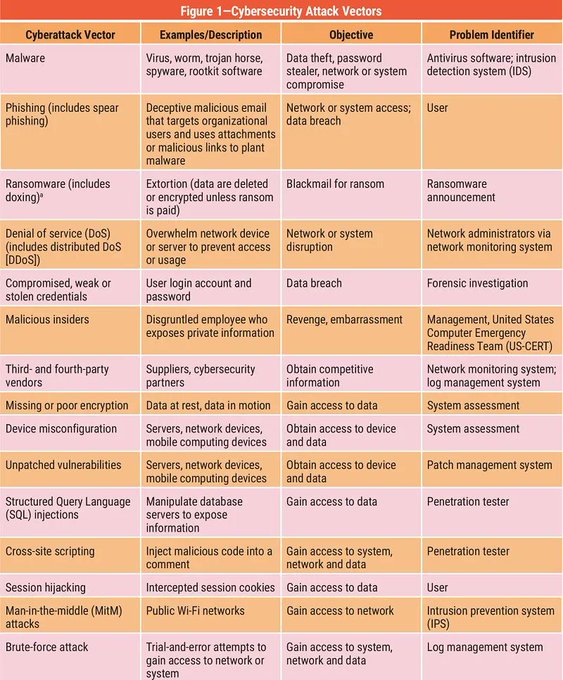
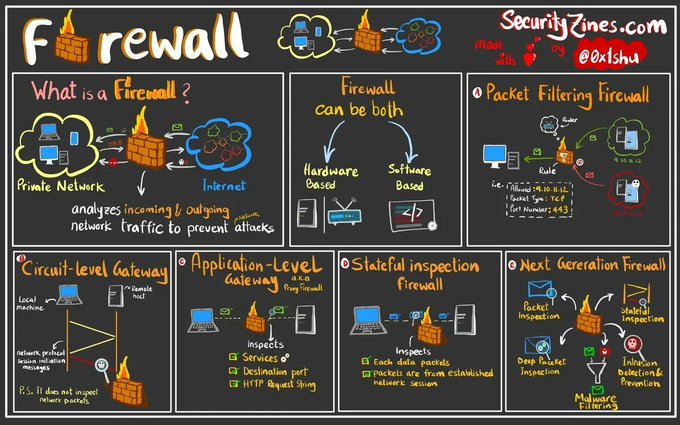
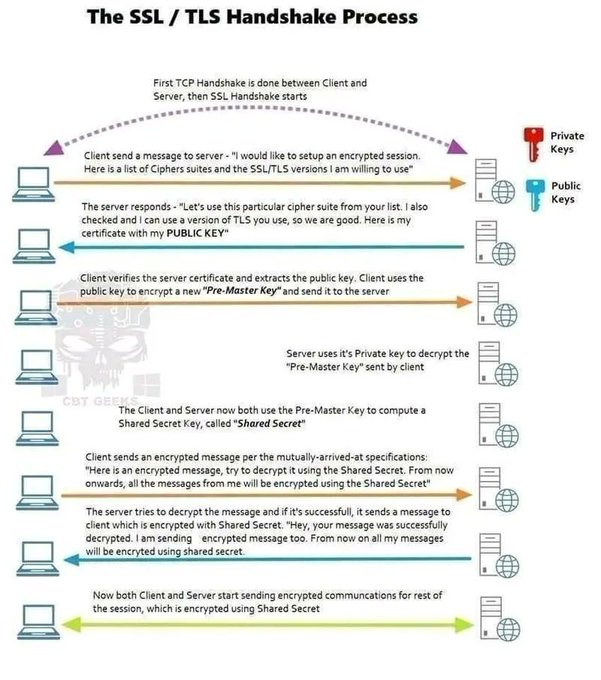
LetsDefend is a hands-on Blue Team training platform that enables people to gain practical experience by investigating real cyber attacks inside a simulated SOC
Cloud
Joined July 2020
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
$DOGS
• 448291 Tweets
श्री कृष्ण
• 411399 Tweets
TEMU
• 356891 Tweets
Oasis
• 340064 Tweets
台風の影響
• 187779 Tweets
最大5,000円報酬
• 177294 Tweets
#JAEHYUN_SMOKE_OUTNOW
• 105698 Tweets
領空侵犯
• 96498 Tweets
Sven
• 68544 Tweets
中国軍機
• 52096 Tweets
#BufftalkxENGFA
• 50525 Tweets
Good Monday
• 45536 Tweets
日本領空
• 44915 Tweets
シロネン
• 39434 Tweets
NuNew X The Toys
• 33026 Tweets
STEP INTO CINEMA PARADISE
• 30167 Tweets
Sultan Alparslan
• 29524 Tweets
LINGORM THESTANDARD POP
• 24078 Tweets
線状降水帯
• 19320 Tweets
Lazさん
• 18965 Tweets
緊急発進
• 15228 Tweets
#恋のおしまい
• 12363 Tweets
WHERE DO WE GO
• 11565 Tweets
#InternationalDogDay
• 11339 Tweets
Last Seen Profiles