Ivan Kwiatkowski
@JusticeRage
Followers
10,322
Following
75
Media
282
Statuses
2,884
Lead cyber threat researcher @HarfangLab . Maintainer of Manalyze, Gepetto, and writer. Trolling on a purely personal capacity.
France
Joined April 2014
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
SEVENTEEN
• 1535141 Tweets
Hanni
• 169941 Tweets
無料クーポン
• 161105 Tweets
Jets
• 121704 Tweets
連休明け
• 93538 Tweets
Carat
• 87635 Tweets
DG X ORM KORNNAPHAT
• 77901 Tweets
अब्दुल कलाम
• 60452 Tweets
पूर्व राष्ट्रपति
• 42349 Tweets
भारत रत्न
• 32619 Tweets
FELIP TAKES ON BBPHSTAGE
• 24619 Tweets
JC BBPH MAINSTAGE
• 23908 Tweets
The Next Prince Q9
• 23618 Tweets
ミンギュ
• 17872 Tweets
金木犀の香り
• 15582 Tweets
バーニス
• 14943 Tweets
मुस्लिम एरिया
• 13980 Tweets
うさぎだらけくじ
• 12881 Tweets
ITZY WORLD IS STILL DIFFERENT
• 11960 Tweets
ジョシュア
• 11896 Tweets
スングァン
• 11446 Tweets
エスクプス
• 11017 Tweets
ドギョム
• 10178 Tweets
Last Seen Profiles
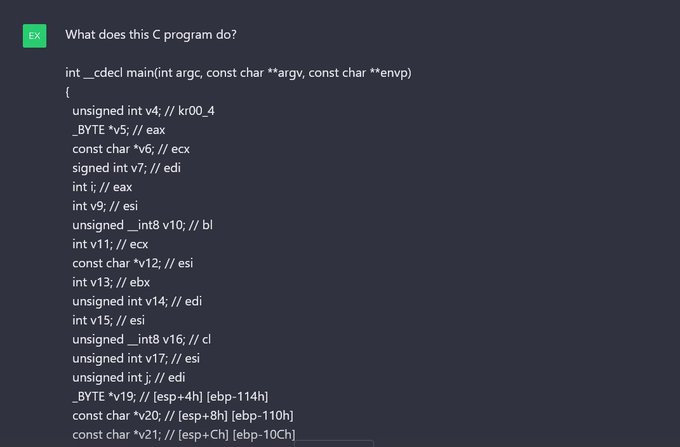
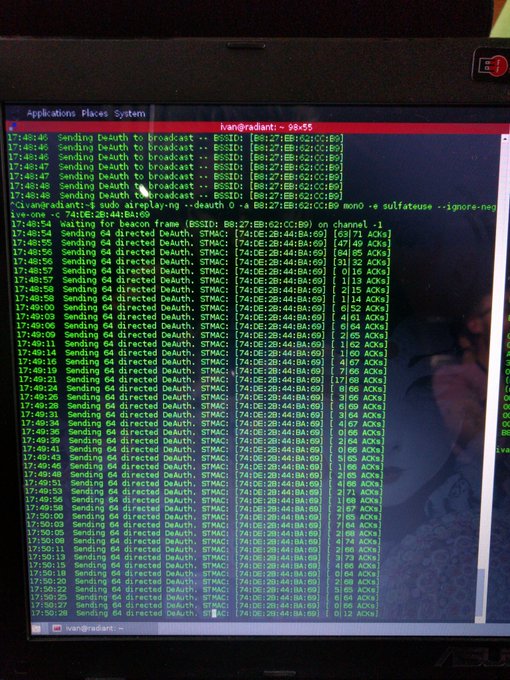
I wrote an IDA plugin that queries
#ChatGPT
and explains decompiled functions. It's still very bleeding edge, but you can find the code here and try it out:
(Yes, the video was performed on a very basic case for simplicity's sake.)
22
376
1K
Do you know what all lawyers are doing right now? Reading
#CrowdStrike
EULAs.
Let's have a look, shall we? Such documents are super easy to find online, I put one there for reference:
Let's see what happens when something hits the fan. (It's good.) 🧵
37
201
1K
@RemyBuisine
J'ai mis en place hier soir au cas où cela se produirait, à afficher avec un téléphone portable !
18
167
426
Our online reverse-engineering / malware analysis course (intermediate level) is finally launching!
@legezo
and I have been working on it almost exclusively for 6 months now. 50+h of video, 100h of virtual lab time, 10 real-life APT malware cases.
8
110
330
New blog post about an UEFI firmware bootkit!
Research was led by our dearly missed
@_marklech_
1
125
258
Personal news: I have resigned from my position in
@Kaspersky
's GReAT team. I'm very grateful for my time there and everything the team accomplished.
I don't have any reason to believe anything I wrote about the company was untrue at the time I wrote it.
I will now take a
26
12
226
Our research on the new(?) mercenary APT DeathStalker is finally out!
Please take a look if you're interested in Evilnum or Janicab!
(cc
@securechicken
)
2
104
172
I have the pleasure to announce I'm joining
@HarfangLab
as Lead Cyber Threat Researcher starting tomorrow!
I'll be working on APTs from everywhere, reversing malware, writing FOSS tools and blog posts!
20
5
164
We're very happy that this research is released:
In it,
@felixaime
,
@securechicken
and I discuss the connection between the VHD ransomware and the Lazarus group.
This work was made possible with huge help from Kaspersky's GERT (IR) team.
1
82
152
@ActuPolitiqueN
Dites-donc les gars, traiter la gauche de nazis en utilisant Pétain+Hitler comme exemple pour défendre l'extrême droite, faut vraiment n'avoir aucune conscience historique.
Faut ouvrir des livres des fois, hein
27
5
151
Our team just released a report on
#CharmingKitten
/
#APT35
.
We discovered a new malware family called Cyclops, written in Go. It launches a local web server which exposes a REST API used to control the malware. The port is forwarded to the C2 via SSH.
1
59
150
Hahaha, gotcha
#ChatGPT
!
They've been patching loads of jailbreaks as they are found, but the possibilities are endless.
6
29
144
A few days ago, I contributed an IDA Pro script which extracts type information from Go binaries to
@juanandres_gs
' AlphaGolang repository.
We just released an article that gives background on how this works:
Code:
0
59
137
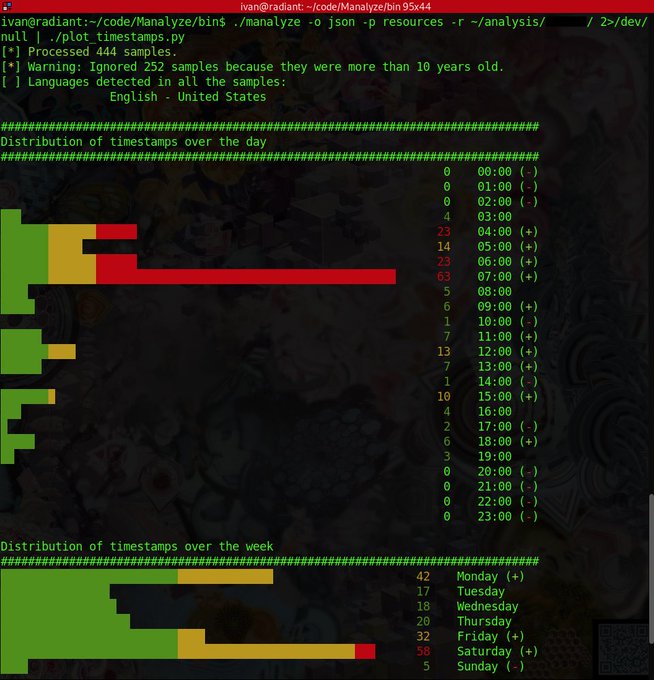
I've added a script to Manalyze which plots the compilation timestamps of a PE collection:
Credit goes to
@x0rz
for the pretty charts.
2
38
133
I wrote my first blog post with
@harfanglab
: a primer on reverse engineering .NET AOT applications.
This will be interesting to people who never created FLAIR signatures in IDA.
1
65
125
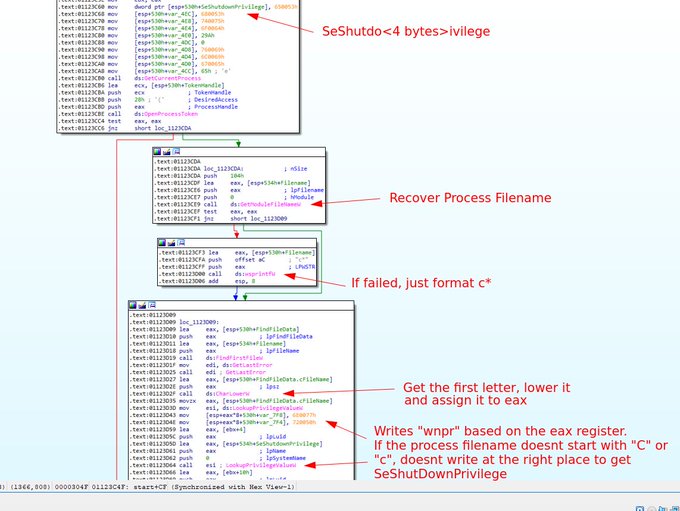
I feel like there's a need to clarify what is going on here, it's an interesting anti-sandbox trick.
The SeShutdownPrivilege string is constructed on the stack dynamically, in particular the program uses the first letter of its filename as an index in the string.
If you analyze HermeticWiper ( 61b25d11392172e587d8da3045812a66c3385451) and you are a beginner to malware RE, be careful to your sample name. Sometimes, it breaks or modifies the behavior of the malware.
#HermeticWiper
#malware
2
35
136
1
39
123
Ping to all hash crackers:
@trustedsec
has just released a great set of scripts at .
- Wordlist deduplication
- Analysis of already cracked hashes
- Launches all the run-of-the-mill attacks from a single command
And a lot of other goodies.
0
50
117
Hidden gem in
@DonnchaC
's
#37C3
talk on Predator spyware: state actors could generate
@letsencrypt
certificates for any website by using their MitM capabilities at ISP level to complete verification challenges (both HTTP and DNS I expect).
CT may be the only way to detect this.
2
39
115
New research from our team (h/t
@securechicken
):
Compromised routers leveraged as malicious infrastructure to target government organizations in Europe and Caucasus (possible APT28 activity)
2
57
112
Spotted: a French website impersonates
@KeePass
at , bundles it with adware () and worst of all (apologies to non-French speaking readers):
12
136
110
If you're using
@Zimbra
, mass-exploitation of CVE-2024-45519 has begun. Patch yesterday.
Malicious emails are coming from 79.124.49[.]86 and attempting to curl a file from that IP.
5
53
109
The
#ISoon
leak confirms beyond the shadow of a doubt USG's attribution of APT41 activities to Chengdu 404!
ISoon is quite amused by it too!
0
26
105
I hear a lot of people are looking for Pegasus samples. Dear
@ANSSI_FR
, please buy the product, get all 0days patched, leak the tools and infra. Burn them to the ground and I swear I will never ever complain again about how my tax money is spent.
3
14
95
Our reverse-engineering course has been out for a few months now, and the feedback is amazing :)
If you haven't checked it out, there's IDA scripting, mock C2 development, hardcore deobfuscation and even Go. Feel free to DM me with any question!
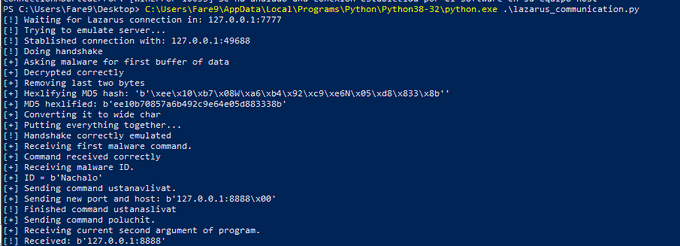
So after finishing another video from
@kaspersky
malware training, I've implemented the commands from Lazarus sample in the C2 emulator, it was pretty interesting learning about this topic, thanks to
@JusticeRage
for the extra exercise.
2
8
48
3
23
94
To be fair, anti-cheat usually only has a single process to protect, which its developers fully own.
EDR and endpoint solutions have to defend whole systems that they have zero control over, which is a much more difficult task.
We welcome constructive feedback from game hackers!
2
10
95
Our team has been investigating
#LockerGoga
and we can assess with medium confidence that it is linked to GrimSpider.
We believe a Cobalt Strike / meterpreter combination is used during the post-exploitation phase. C2s use the default SSL certificate on port 443 ;)
5
57
92
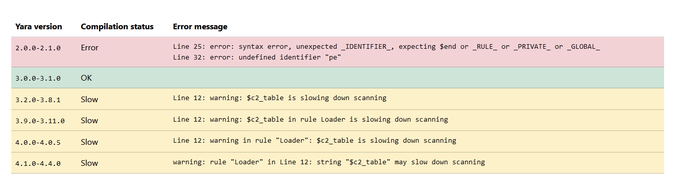
#100DaysofYARA
I created a web service that allows you to verify on which yara versions your rule compiles.
In the past, shipping rules to customers, I wondered if there were limitations but couldn't find out easily. Now I can.
2
35
90
List of Ivanti / PulseSecure C2s we discovered (h/t
@securechicken
):
146.0.228[.]66:1080/assets/js/xml.php
146.0.228[.]66:1080/css/chat.jsp
146.0.228[.]66:8111/css/chat.jsp
152.32.128[.]64
154.223.17[.]218
159.65.130[.]146:80
159.65.130[.]146:80/index
35.201.216[.]249:80/index
1
16
82
I added a script which automatically shelljacks (log term) into users who SSH into a box to my repo! cc
@emptymonkey
2
35
78
I just stumbled on to this very interesting Linux post-exploitation talk by
@_ta0
:
It's full of hidden gems, I'll be watching it again so I can take notes.
0
44
80
Dear
@HexRaysSA
, considering that you won't allow me to renew my licence, I'd appreciate it if you either:
a) Granted me an OSS dev license, considering the value I bring to your customers for free
b) Refrained from using my work for PR purposes
Cheers
#Gepetto
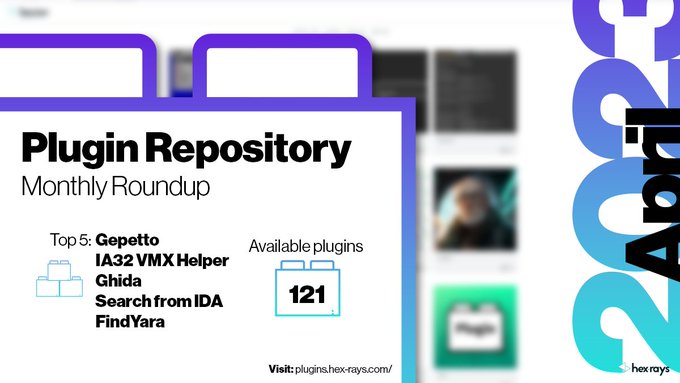
keeps the first position for the second month in a row! Good job
@JusticeRage
👏
Got a plugin that could be on the top of the chart? Publish it, and let’s see 🌐
#IDAPlugin
#PluginRoundup
#IDAPro
#IDAPython
1
3
18
5
11
75
Our team has been tracking
#DoppelG
änger activities for over a month, and we've just published our research! In total, we share ~250 URLs to disinformation content and ~800 handles of X accounts part of the dissemination network.
1
34
74
Very unhappy and disappointed by this move from
@HexRaysSA
. During trainings, how can I justify the investment for newcomers if now they can't use the software after a year?
7
13
73
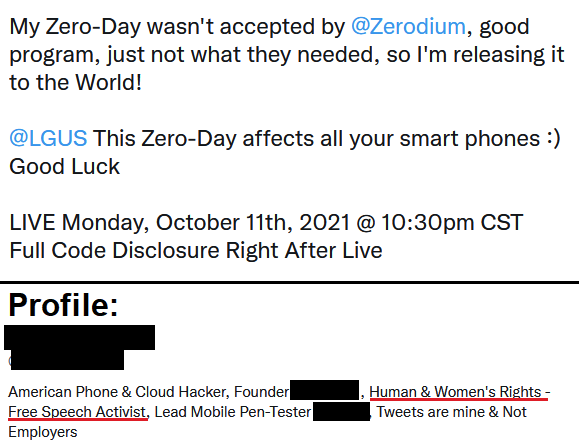
@x0rz
*Looks at bio*
"Human & Women's Rights - Free Speech Activist" selling 0days to Zerodium
Yup, that seems about right.
3
8
73
New research: our team at
@harfanglab
just published an investigation into possible Arid Viper (but definitely Hamas-related) activity against 🇮🇱 targets, based on a tip from
@NicoleFishi19
.
We analyzed the malware (including 2 wipers) & IW aspect:
2
31
74
@BushidoToken
According to CORRECTIV, she's actually Russian, and linked to Evil Empire / DoppelGänger activities.
100% chance this is a front for 🇷🇺 intelligence if the brokering aspect is even legit.
1
10
67
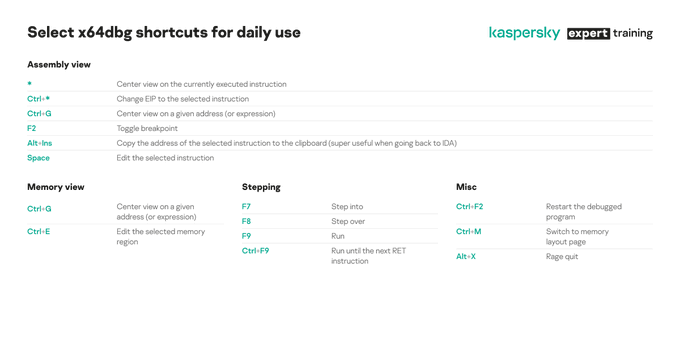
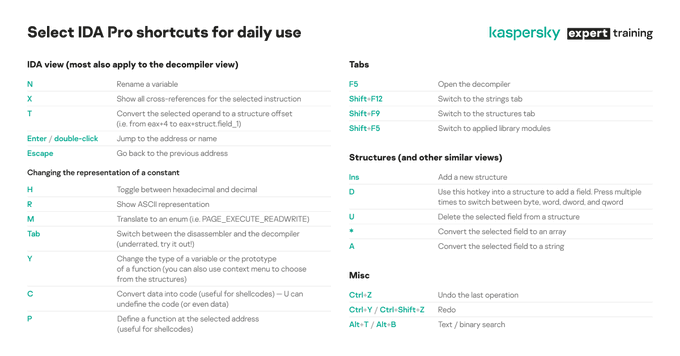
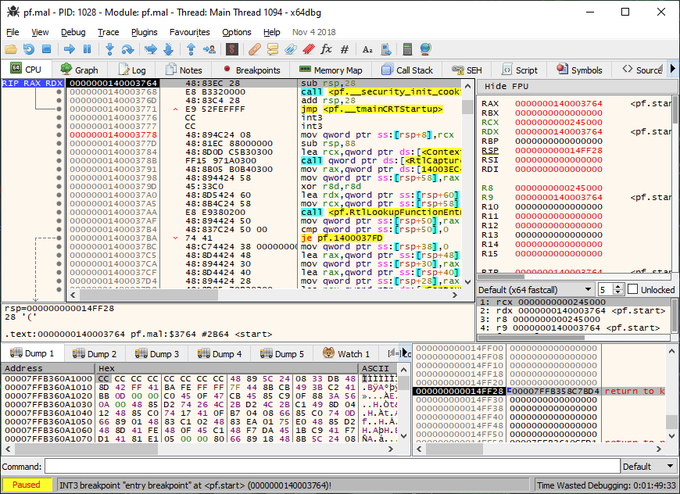
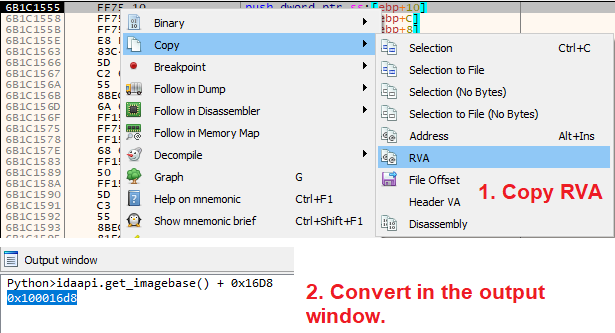
When debugging DLLs, I often need to go back and forth between
@x64dbg
and IDA. So far, here is the quickest way I have found to convert addresses. Is there a better one?
7
24
66