BlockSec
@BlockSecTeam
Followers
24,897
Following
278
Media
545
Statuses
1,841
Smart Contract & EVM Chain Audit | Boost Web3 through Next-Gen Security & Usability Innovations @Phalcon_xyz @MetaSleuth @MetaDockTeam 👉TG:
Joined December 2020
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
FEMA
• 1195043 Tweets
Tina Peters
• 252599 Tweets
Liz Cheney
• 175745 Tweets
裏金議員
• 163487 Tweets
#LISAxMoonlitFloor
• 144337 Tweets
SCJN
• 107609 Tweets
Ten Hag
• 101065 Tweets
The Boss
• 98700 Tweets
#GHGala5
• 97885 Tweets
MOONLIT FLOOR OUT NOW
• 92703 Tweets
Bruce
• 83265 Tweets
Happy Anniversary
• 52629 Tweets
Rashford
• 46543 Tweets
Maguire
• 42965 Tweets
Brewers
• 40718 Tweets
原則公認
• 34902 Tweets
EL DESTELLO IS OUT
• 34531 Tweets
Violeta
• 32703 Tweets
天使の日
• 29169 Tweets
Falcons
• 24096 Tweets
もちづきさん
• 21594 Tweets
Halle
• 20814 Tweets
Garth Brooks
• 15408 Tweets
ゴールデン進出
• 14873 Tweets
Athena
• 14206 Tweets
Bucs
• 13389 Tweets
#911onABC
• 12920 Tweets
Bijan
• 11402 Tweets
Mike Evans
• 10651 Tweets
Last Seen Profiles
We blocked an attack on
@ParaSpace_NFT
and rescued 2900 eth. Please contact us asap. Dmed 45 minutes ago but get no response.
147
125
866
We help
@Platypusdefi
recover 2.4M USDC from the attacker contract successfully!
BlockSec will always be here to secure the whole ecosystem.
39
76
616
.
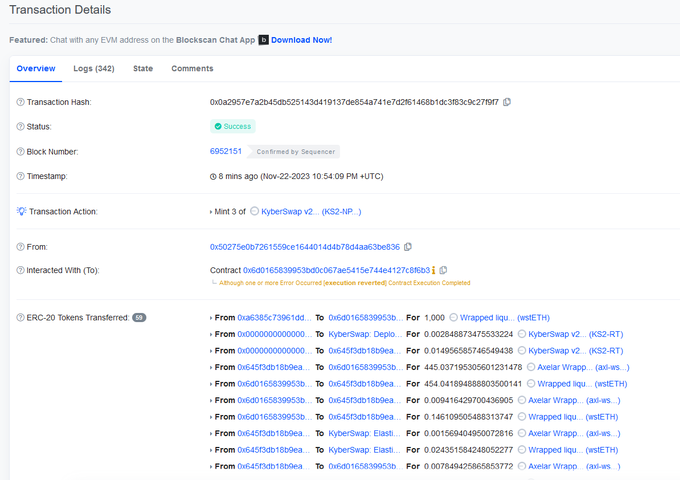
@KyberSwap
was exploited due to tick manipulation and double liquidity counting.
In summary, the attackers borrowed a flash loan and drained the pools with low liquidity. By executing swaps and altering positions, they manipulated the current prices and ticks of the victimized
12
105
432
1/
@samczsun
explained that the attacker exploited the vulnerability in mev-boost-relay to drain MEV bots. After digging into the attack, we have two more findings. First, the attacker used a honeypot tx to lure MEV bots. Second, the honeypot tx has a self-protected mechanism.
Dusk for sandwich bots? A few top mev bots were targetted in block
@peckshield
@BlockSecTeam
@bertcmiller
@samczsun
@bbbb
68
159
580
15
104
343
1/ Exploits on chain are growing at an alarming rate. Here's how
#BlockSec
responds when an attack occurs and the secret weapons we deploy to analyze incidents quickly and accurately.
12
147
197
1/ Alert | BlockSec detected that exploiters are replaying the message (calldata) of the PoS chain on
@EthereumPow
. The root cause of the exploitation is that the bridge doesn't correctly verify the actual chainid (which is maintained by itself) of the cross-chain message.
26
93
290
Please note that this reentrancy issue is associated with the use of 'use_eth', which could potentially place the WETH-related pools in jeopardy!
@CurveFinance
, please DM us if you need any help.
36
60
224
Looks like an MEV bot has been attacked() due to the lack of a check for the sender.
@Mudit__Gupta
9
32
212
Hey,
@0xsifu
We have successfully blocked an attack transaction and rescued 100 Ether. Please get in touch with us.
26
10
200
Please revoke approval to 0x1231deb6f5749ef6ce6943a275a1d3e7486f4eae (: LiFi Diamond) asap!
@lifiprotocol
46
110
190
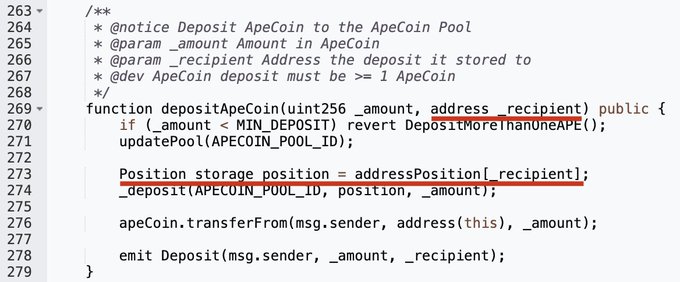
1/ There is a flawed logic in borrow() of the ParaProxy contract (0x638a) of
@ParaSpace_NFT
. The attacker can borrow more tokens as his scaledBalance will be enlarged by depositing into the position of the proxy (0xC5c9), i.e., specifying the _recipient of depositApeCoin().
We blocked an attack on
@ParaSpace_NFT
and rescued 2900 eth. Please contact us asap. Dmed 45 minutes ago but get no response.
147
125
866
6
40
167
.
@AaveAave
the latest upgrade of ReserveInterestRateStrategy in Aave V2 (Polygon) has caused a temporary halt of the protocol, impacting assets worth ~$110M!
The root cause is the new ReserveInterestRateStrategy is only compatible with Ethereum, not compatible with Polygon.
found a governance issue in Aave V2 impacting the Polygon Aave V2 Pool, causing USDT/BTC/ETH/MATIC assets worth up to 120 million to become inaccessible.
@AaveAave
4
10
63
22
44
174
Indeed, smart contracts compiled using Vyper versions 0.2.15, 0.2.16, and 0.3.0 are vulnerable, which can lead to the failure of the reentrancy guard.
7
65
167
Unibot
@TeamUnibot
was reported to be hacked.
As the code is not open-sourced, we suspect that there is a lack of input validation of the function 0xb2bd16ab in the 0x126c contract, which allows an arbitrary call. Therefore, an attacker could invoke 'transferFrom' to transfer
4
53
158
1/ We are thrilled to release Rustle (), the first automatic auditor for
@NEARProtocol
community.
@PagodaPlatform
@proximityfi
5
80
137
We knew that
@SushiSwap
RouteProcessor2 was attacked. We evaluated possible damages in the past few hours and made this public only after we think it's safe : users' assets are always our first priority.
Btw: we rescued part of them and will release the details later.
10
20
134
We observed that the
#Euler
attacker 0xb66cd966670d962C227B3EABA30a872DbFb995db is returning money to Euler finance now.
3000 Ether was returning so far.
13
24
132
Excited to be the ecosystem security partner for
@Ancient8_gg
! 🎉
We are currently partnering with Ancient8 for auditing, with more security-focused collabs in the pipeline.
Ancient8 aims to empower the next 100 million Metaverse citizens, and BlockSec is here to secure their
72
65
86
1/ We have analyzed the recent
@Platypusdefi
attack and found that the attacker made a mistake in the first attack transaction, which prevented the attacker from withdrawing the profits. Here is the full story.
Thanks,
@spreekaway
for pointing out this direction.
3
26
129
🎉Phalcon now supports
#Avalanche
C-Chain
@avalancheavax
!
* Latest transactions since block height 20876888 are available. Old transactions are importing and should be available later
* Now we support
#ETH
#BSC
#Cronos
#Avalanche
Try this transaction:
5
34
116
1/ the attack to the
@ElephantStatus
is a traditional price manipulation attack. We will use the following transaction() to illustrate the process.
@defiprime
@bbbb
@Mudit__Gupta
@bantg
9
36
118
1/
@SturdyFinance
was attacked and the loss is ~442 ETH. The root cause is due to the typical Balancer's read-only reentrancy, while the price of B-stETH-STABLE was manipulated!
4
26
113
Hey
@LefterisJP
, your blame is unfair. There are some facts you did not know.
- We located this WETH pool (0x8301) issue at 17:10 UTC on July 30. Unfortunately, we cannot DM
@CurveFinance
on Twitter because their DM is not allowed. So we shared this finding with a trusted
You either need to be an idiot or outright malicious to tweet out potential vulnerabilities
@BlockSecTeam
while there is an ongoing incident
Adding screenshots and asking the potential victim to DM you? IN A PUBLIC TWEET?
I wont even quote your tweet/s but what the actual fuck?
27
41
370
34
15
108
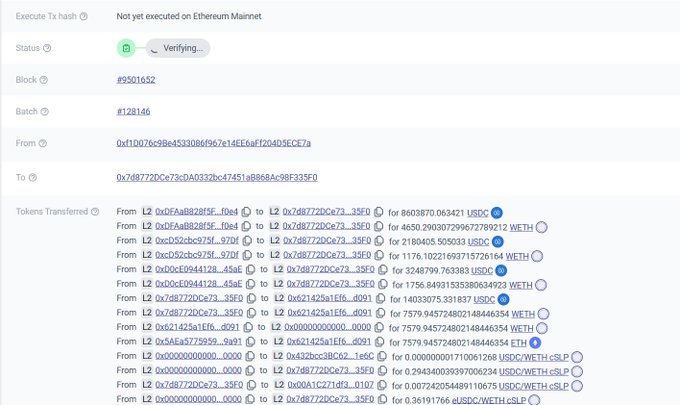
We are assisting
@Era_Lend
to this issue, and the root cause has been identified. The total loss is ~$3.4M.
Specifically, this is a read-only re-entrancy attack.
Another attack tx is:
Attacker address:
0xf1D076c9Be4533086f967e14EE6aFf204D5ECE7a
2
17
62
13
42
102
1/
@iearnfinance
was hacked with two consecutive attack transactions. The root cause is due to an (on-purpose?) misconfiguration which makes the rebalance of the pools rely on an incorrect underlying token. This misconfiguration has been there for more than three years.
4
25
106
Thrilled to announce our proposal has been supported by a grant from Uniswap Foundation
@UniswapFND
! Our static analyzer will support the secure operations of Uniswap v4. 🦄
The new "Hooks" feature in
#Uniswap
v4 significantly enhances the extensibility and flexibility of
7
25
100
1/ We confirmed that both
@paraswap
deployer address (0x490ce4616672e93b1c8f5e43aa80312fd73dee8c) and
@curve
deployer address(0x07a3458ad662fbcdd4fca0b1b37be6a5b1bcd7ac) are vulnerable to the profanity vulnerability. The private keys can be recovered.
1/ Hi
@paraswap
,I heard that you want to see this? your deployer address private key may have been compromised (possibly due to Profanity vulnerability) and funds have been stolen on multiple chains.
20
53
238
8
27
104
1/
@eulerfinance
is attacked. The root cause is due to the lack of liquidity check in the function donateToReserves()
See the detailed attack steps below.
8
33
97
1/
@Pawnfi
was attacked in a furry of transactions (e.g., ) The root cause for the attack is that the protocol failed to verify whether the NFT had actually been transferred when users used a specified NFT as collateral for borrowing.
7
20
97
1/ RouteProcessor2
@SushiSwap
has a vulnerability that can drain accounts that approved to this contract. Our system immediately detected the attack attempt to
@0xsifu
and rescued some funds. Unfortunately, some other funds cannot be rescued.
9
22
95
.
@LeetSwap
on $Base was attacked, and the loss was over 340 ETH. The attacker abused the public _transferFeesSupportingTaxTokens function to manipulate the pool:
1. Swapping $WETH for another token A.
2. Invoking the _transferFeesSupportingTaxTokens function to transfer token A,
3
24
96
The
@Hope_money_
on Ethereum was subjected to an exploit due to a precision loss issue. There have been several such attacks recently. We advise developers to review these incidents and promptly conduct self-checks. Here are the details:
4
30
91
@user272736
@PolyNetwork2
From the on chain data analysis, we cannot verify this claim from the PolyNetworks:
2
20
93
1/ How is a honeypot contract trapped by an MEV bot
The defi_game() is a honeypot contract. If the player can guess the answer to the question, he/she will get the Ether inside the contract.
@Mudit__Gupta
4
25
87
1/
@ZunamiProtocol
was hacked, and the loss is over $2M. It is a price manipulation attack that dues to the flawed calculation of the LP price, i.e., within the totalHoldings function of strategies like MIMCurveStakeDao where sdt and sdtPrice were artificially inflated.
2
18
88
1/2) Our monitoring system alerted that SashimiSwap
@SashimiSwap
was attacked (both Ethereum and BSC). and we confirmed that it is due to the bad logic of the swap function, which ALWAYS use the first pair to calculate the balances.
@bantg
@defiprime
5
23
93
Well, besides public mint, public burn, public oracle, we now have public safeTransferFrom ......
@Mudit__Gupta
10
11
87
1/5) Yesterday, we reported the attack towards the Visor project (
@VisorFinance
). We deleted the twitter later due to the raised concern that the disclosed information could be abused to attack others. Then we confirmed that other pools are safe (also confirmed by
@samczsun
).
12
23
80
The exploiters use
@ankr
's deployer address to replace the $aBNBc contract's implementation. Afterward, use the new added backdoor function (0x3b3a5522) to mint $aBNBc token.
The following chart shows the exploiters' fund flow generated by MetaDock with one-click.
3
28
84
1/
@Level__Finance
was reported to be hacked due to the lack of checks of repeated items for the array argument of the vulnerable function. Note that the hacker first tried to make a preparation but failed several times 7 days ago, and finally made it before launching the attacks.
4
24
78
Our monitoring system detected that multiple pools related to
@RariCapital
@feiprotocol
were attacked, and lost more than 80M US dollars. The root cause is due to a typical reentrancy vulnerability.
@defiprime
20
37
76
1/
@dForcenet
attacked in both
@arbitrum
and
@optimismFND
. The root cause is the well-known read-only reentrancy in the curve pool.
5
17
76
The strategic partnership between BlockSec Phalcon and
@puffer_finance
is set to elevate the entire
#Restaking
field to new heights of security standards. 🙌
👏 We're excited to announce a new level of partnership with
@puffer_finance
. We are integrating our Phalcon platform into Puffer’s protocol to enhance their security measures.
5
11
60
6
11
65
The
@ExactlyProtocol
has been paused. It's time to review the attack.
The root cause is
#insufficient_check
. The attacker was able to bypass the permit check in the leverage function of the DebtManager contract by directly passing a fake market address without validation, and
#PhalconAttackAlert
@ExactlyProtocol
got hacked with~$7.3M loss by now.
Join Phalcon Block Waitlist, get precise alert before attack tx was executed, take automatic actions to fight hackers back. 🦾
0
11
13
7
27
79
It’s a ridiculous logic. The Vyper officially announced the affected versions on UTC 16:44 July 30, and Curve confirmed at 16:45. After that, three attacks happened between 19:08 and 22:00. Do you think these exploits might have been white hacked if they hadn't tweeted and
Gotta wonder if some of yesterday's exploits might have been white hacked in time if multiple "auditors" like
@SupremacyHQ
and
@BlockSecTeam
hadn't tweeted which Vyper versions were affected when a team was working hard to keep it under wraps. Shameful behaviour.
15
172
709
6
16
76
💡 Curious about how
#PufferProtocol
keeps its funds secure? Check out BlockSec's deep dive into its access control architecture!
Understand the roles, smart contracts, and strategies for managing over $900M assets. Knowledge is power!
@puffer_finance
7
13
61
This 'attacker' (a $14m profit) is funded from
@binance
, whitehat? Please check it
@cz_binance
2
13
67
Hey,
@ParaSpace_NFT
dmed you guys 45 minutes ago but got no response. Please contact us asap.
2
6
71
Glad to help
@ParaSpace_NFT
recover the fund and appreciate the transparency in the whole process. Long term collaboration is on the way to help secure the project and the whole ecosystem.
Thank you again to
@BlockSecTeam
and their exceptional assistance in ensuring the security of the ParaSpace platform. We received the 2,909 $ETH that the
@BlockSecTeam
recovered and awarded them a 5% bounty.
Key updates you need to know RE our security patch/overhaul 🪡
4
14
100
1
8
68
1/ BitKeep’s
@BitKeepOS
(unverified) contract (0x75eb on BSC) was hacked. Looks like its function allows the attacker to execute an arbitrary call, i.e., both addr & function signature can be specified in the calldata --- then tokens approved to the contract were transferred out.
2
16
67
🚨
@starsarenacom
has been exploited. Since it is not open source, we suspect that some key configurations have been manipulated due to a re-entrancy issue.
They forked
@friendtech
's code, but the issue is in the new/edited parts.
#PhalconAttackAlert
@starsarenacom
got hacked with~$2.9M loss.
Join Phalcon Block Waitlist, get precise alert before attack tx was executed, and take automatic actions to fight hackers back. 🦾
0
2
7
5
29
66
1/ Our system monitored that
@0vixProtocol
on Ploygon was hacked, and the loss is around $2M. The root cause is due to the flawed price calculation of a deflation token.
4
26
69
.
@raft_fi
protocol on Ethereum was attacked due to a precision loss issue. The loss amounted to ~1577 Ether. However, the attacker mistakenly burnt 1570 of them, ultimately resulting in a net profit of -4 Ether after accounting for costs such as gas fees.
The attacker initially
3
22
55
🎉 Exciting news! BlockSec has partnered with
@Conflux_Network
to provide top-notch security services and insightful tools for the Conflux ecosystem. 💪 Together, we are committed to creating a more secure and robust on-chain network. 🚀
#blockchainsecurity
#Conflux
#BlockSec
2
17
59
Woo, you can simulate a transaction directly on
@etherscan
now, powered by
@MetaDockTeam
.
1/5 MetaDock's hidden gem? Transaction Simulation powered by
@Phalcon_xyz
🚀.
You can pre-execute or simulate any transaction using MetaDock.
E.g., before minting an NFT, quickly gauge the right gas limit and costs with MetaDock's Simulation feature.
But how? ⬇️
2
4
21
2
15
68
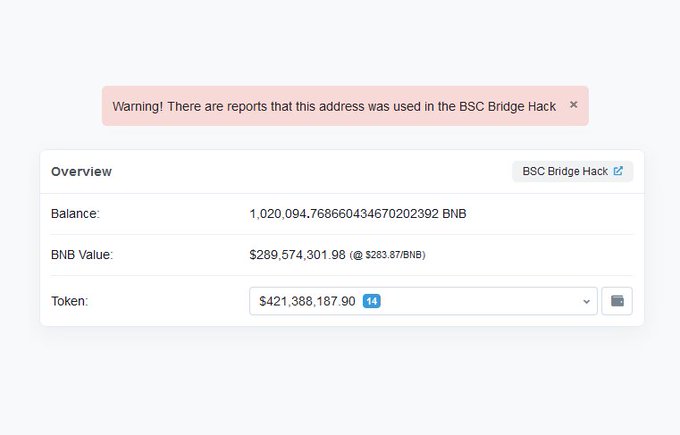
1/ The Binance cross-chain bridge has been attacked. The root cause is due to the vulnerability in the message verification, as reported by
@samczsun
().
In fact, bridges have been valuable targets for attackers. The figure shows the representative ones.
5
18
63
We are assisting
@Era_Lend
to this issue, and the root cause has been identified. The total loss is ~$3.4M.
Specifically, this is a read-only re-entrancy attack.
Another attack tx is:
Attacker address:
0xf1D076c9Be4533086f967e14EE6aFf204D5ECE7a
2
17
62
This is a killer feature for (security) researchers, you can now view private variables on Etherscan.
Thanks to
@MetaDockTeam
. Install the MetaDock extension and enjoy the feature now.
5
12
63
Yesterday, our system detected an attack on the
@hypr_network
's OP Stack Bridge. We promptly reached out to their team to share our findings. As always, we are glad to help:)
Now that the team has taken actions and disclosed it publicly, we'd like to provide some insight into
3
17
52
.
@MidasCapitalXYZ
has been exploited with losses ~$600K. The Midas is a fork of Compound and this attack is similar to
@HundredFinance
and
@SiloFinance
(the vulnerability disclosed today). Here's an attack transaction:
3
17
57
oops,
@safemoon
has been attacked due to a public burn issue (in 2023!!) with a loss of around 8M.
The original attack tx (0xbcf5e30c164837b5d7c42fd7e33e47a0072dc014e7f0a67aa7710af49d0ce53b) was front-run by an MEV bot.
4
12
58
Happy to be the security parter of Stratos
@Stratos_Network
.
BlockSec has audited a couple of representative projects in the
#Cosmos
ecosystem
@cosmos
. Work with Stratos is one step further to commit to the Cosmos ecosystem.
🎉 We’re thrilled to announce that Stratos will work with
@BlockSecTeam
for security auditing.
🔒 Their innovative research, vast project experience, and reliable security services will help pave the way for the successful launch of the
#Stratos
Decentralized Storage Mainnet.
3
27
97
0
13
59
2 weeks ago,
@Balancer
and its fork
@beethoven_x
sufferd attacks, with total losses ~$2.1M. The subtlety of the bug and its exploitation have remain under-analyzed. In this report we deliver a comprehensive community-engaging analysis.
3
21
62
1/
@skywardfinance
was attacked by in transaction . The loss is more than 1M $NEAR Tokens.
@NEARProtocol
3
18
56
1/ Our investigation shows that Bo Shen's (
@boshen1011
) wallet attacker abused an MEV bot to transfer funds between his/her addresses (0x24b93...bc2e and 0x66F6...Ae14). We suspect it is to make the fund tracing harder.
Here is how the trick works:
4
8
52
Due to the affected protocol being paused, here is a preliminary analysis of this
@Platypusdefi
incident:
1. It's a Flashloan attack, with a total loss of ~$2M. The Hacker manipulated 'cash' and 'liability' which affected the swap price.
2. The first attack tx is:
#PhalconAttackAlert
@Platypusdefi
on Avalanche got hacked with~$575K loss.
Join Phalcon Block Waitlist, get precise alert before attack tx was executed, and take automatic actions to fight hackers back. 🦾
0
3
4
2
16
56
.
@Wise_Lending
has been attacked (notable white-hat c0ffeebabe.eth managed to front-run successfully), and the Pool has been drained. In this incident, the attacker exploited two issues to successfully carry out the attack:
1. Manipulating the value of each shares through
3
10
56
.
@bitpaidio
on BSC has just been exploited. The root cause of the issue was that Lock_Token() did not properly update the lock times. The exploiter made a lock() 6 months ago, which led to an over-calculation of rewards during the withdraw().
The loss from this attack amounts to
2
12
55