BlockSec Phalcon
@Phalcon_xyz
Followers
5K
Following
837
Statuses
828
A Platform to Monitor and Block Hacks | The only one boasting dozens of successful white-hat rescues. | Built by @BlockSecTeam 👉TG: https://t.co/RT0FyaxsIE
Joined July 2020
🚀 BlockSec Phalcon 2.0 Unleashed! Don't let your protocols be unprotected! We're thrilled to launch the 2.0 version of BlockSec Phalcon, the world's first crypto hack monitoring and blocking platform. BlockSec Phalcon 2.0 Delivers: 🛡️Extensive Coverage: Monitors the vast majority of threats protocols may encounter after launch, such as attacks, operational, interaction, and financial risks. Supports customized rules for complex scenarios. 🛡️Blocking Capability: With mempool detection and front-running technology, help protocols automatically block hacks before they are executed to prevent any loss. 🛡️One-Click Configuration: Auto-creates monitors for imported addresses, streamlining the setup process to just a single click. 🔥 Stay ahead of threats with powerful, automated security. Book a demo and start your free trial today: 👀 Discover more at 👉 #DeFiSecurity #ProtocolSecurity #BlockSec #Phalcon
13
7
45
.@YeiFinance 🤝 BlockSec Phalcon 24/7 attack monitoring ➕ millisecond automated blocking 🟰 Proactive defense 🟰 $140M+ assets secured 🛡️ Learn more in the blog👇: #DeFiSecurity #YeiFinance #Phalcon #Sei
0
3
7
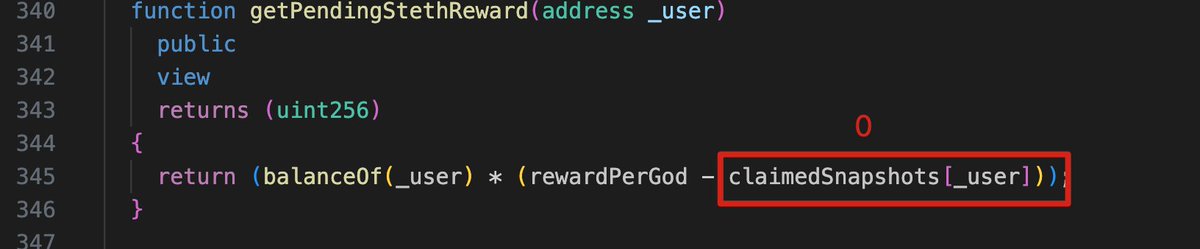
. An attack to @PeapodsFinance with around 3k loss. The attacker sets the slippageOverride to 999 to bypass the protection.
3
9
69
ALERT! Our system has detected several attack transactions targeting contracts on #BSC and #Arbitrum hours ago, resulting in losses of ~ $107K and $188K, respectively. Both incidents are price manipulation attacks: the first involves a price manipulation attack by forced investment, while the second exploits the lack of access control and slippage protection, enabling the attacker to forcibly burn victims' positions. Attack TX on #BSC: Attack TX on #Arbitrum: Subscribe to BlockSec Phalcon today to get alerted in realtime and take automatic actions to protect your assets.
0
4
4
ALERT! Our system detected a series of attacks targeting an unknown #XSD token on #ETH , #Base and #Optimism , resulting in ~$45k in losses. It is a price manipulation attack that leverages the flawed 'swapXSDforETH' function through two key steps to manipulate the #XSD token's price: 1) exploiting a reentrancy vulnerability, and 2) burning tokens held by the pool. Attack TX: Subscribe to BlockSec Phalcon today to get alerted in realtime and take automatic actions to protect your assets.
1
1
4
ALERT! Our system detected a series of attacks targeting the @odosprotocol protocol on #ETH #Base, resulting in ~$50k in losses. The root cause is arbitrary call vulnerability caused by unverified user input. We notice that the attacker exploited the precompile contract (0x4) to bypass the signature verification. Protocols utilizing this method should exercise caution to mitigate similar risks. Attack TX: Subscribe to BlockSec Phalcon today to get alerted in realtime and take automatic actions to protect your assets.
6
21
93
Subscribe to Phalcon to monitor and block hacks to protect users.
. @TheIdolsNFT was attacked in multiple transactions, with a loss of around 340k. The vulnerability is due to a flawed login when claiming rewards.
0
2
4
. BunniHub of @alienbasedex on base was attacked with multiple transactions. Though the loss in each transaction is small, it still shows the vulnerabilities existing in the smart contract. Subscribe to Phalcon to protect your protocol. Some attack tx:
0
3
8
🎉 Avalanche ✖️BlockSec Phalcon We're excited to announce comprehensive support on @avax with both BlockSec Phalcon and Phalcon Explorer. 🛡️ BlockSec Phalcon now brings its robust security features to protocols in the Avalanche ecosystem, offering continuous monitoring and automatic prevention of hacks, operational, interaction, and financial risks, 24/7. Learn more at 🥳 With Phalcon Explorer, easily track fund flows, balance changes, and invocation flow in a visualized way. Also, explore enhanced features like transaction simulation and debugging. Try it out at
4
32
98
Yet another case within 24 hours... To stay aware of the critical operations of a DeFi protocol, Phalcon is a must-have tool at hand to monitor the *Contract Upgrade*. Book a demo with the BlockSec Phalcon team to learn how Phalcon can help mitigate the operation risks.
On January 8, 2025, Moby experienced an incident involving the leakage of a private key, which affected some LP assets within certain protocols. However, we promptly addressed the situation based on our team’s swift efforts and support from partners. We want to emphasize that it was not a security issue related to the protocol’s smart contracts - hackers attempted to steal funds by simply upgrading existing smart contracts using stolen proxy private keys. We sincerely apologize for any concern this incident may have caused. Please rest assured that all users-traded option positions and deposited LP assets will be fully restored through our treasury. To ensure the stability of the protocol, we will undergo a system reorganization until Thursday, January 9, 2025, at 1:00 pm UTC. Moby team will continue to investigate the matter further and provide ongoing updates. Please rest assured that your assets remain safe. If you have any questions regarding this maintenances, please get in touch with us via our Official Telegram channel. 👉🏻
0
0
1
Being aware of the critical operation of a DeFi protocol is necessary. That's why you must have Phalcon in hand to monitor the *Contract Upgrade*. Book a demo with the BlockSec Phalcon team to learn how Phalcon can help mitigate the operation risks.
Important Announcement - Jan. 8, 2025 A hacker has taken over the admin address, upgraded the contracts, and transferred funds to their wallet. The team is not sure what happened and is currently investigating. The contract is no longer Orange. DO NOT interact with it (e.g., deposit or withdraw). It is recommended that all users revoke all contract approvals related to Orange Finance. Stryke vault - 0x22dd31a495CafB229131A16C54a8e5b2f43C1162 - 0xe1B68841E764Cc31be1Eb1e59d156a4ED1217c2C - 0x5f6D5a7e8eccA2A53C6322a96e9a48907A8284e0 - 0x708790D732c5886D56b0cBBEd7b60ABF47848FaA - 0xE32132282D181967960928b77236B3c472d5f396 - 0x01E371c500C49beA2fa985334f46A8Dc906253Ea - 0x3D2692Bb38686d0Fb9B1FAa2A3e2e5620EF112A9 - 0x49F60f02B45087ed99EcC4dE63D0337db0d0c6BF - 0x5bb109E834A4e4c5422526f0f3d42783031BA80d Stable vault (closed) - 0xd6ecEb3978bf2b76958b96E8A207246b98C7d639 - 0x65Fb7fa8731710b435999cB7d036D689097548e8 - 0x59671Aa8F4E5adCcb26f4c88F0d6047B0ae7620b - 0x0B48540e214bc196e1D0954834876691fE19068D
0
2
5
.@FEGtoken was attacked on #Ethereum, #BSC, and #Base last Sunday, resulting in losses exceeding $900K. As the core relayer contract (0x3a3709b8c67270a84fe96291b7e384044160c6b1) is not open-source, our investigation suggests that the root cause was likely a lack of validation on Wormhole bridge messages. Specifically, only the relayer can register withdrawal in the SmartBridge. However, when receiving a wormhole bridge message, the relayer doesn't check if the source address is allowed to trigger the withdrawal registration. We will use one of the attacks on #BSC as an example. The core attack involves the following three transactions: 1. the attacker initiated a bridge message with malicious payload on #Base: 2. the delivery made the relayer mistakenly allowed the attacker to withdraw massive FEG tokens on #BSC: 3. the attacker withdrew tokens and made profits on #BSC:
Update on Irregular Transactions and Investigation FEGrox is actively investigating the irregular transactions and has engaged PeckShield for additional support in uncovering the root cause. We completely understand your frustration—believe us, we feel it too. Over the last four years, we’ve poured our lives into building this project, making countless sacrifices along the way. This situation is deeply personal for all of us, and we are fully committed to finding answers and resolving it. Centralized exchanges have been notified to halt trading, and we will share updates in the chat as more information becomes available. Our preliminary investigation points to a vulnerability in the wormhole bridge, which had previously undergone an audit. You can review the audit report here: PeckShield Audit Report - FEG Bridge v1.0: We want to emphasize that the SmartDeFi contract code does not appear to be compromised. While the SmartDeFi protocol has been paused as a precautionary measure, the projects built on it remain safe at this time. We are continuing to examine the issue closely and deeply appreciate your patience and support as we work through this matter together.
2
3
22