Scott Piper
@0xdabbad00
Followers
19K
Following
38K
Media
476
Statuses
10K
https://t.co/EXe2MI3bAU Cloud security historian. Developed https://t.co/ZXFwkuyseC, CloudMapper, and Parliament. Organizer for @fwdcloudsec. Researcher at @wiz_io ✦
Salt Lake City, UT
Joined August 2012
In 2016, @dagrz gave one of the greatest cloud security talks ever, filled with new techniques that have been rediscovered repeatedly in the years since. I've remastered it from video obtained from an audience member and the slide deck.
13
73
310
😱😱😱 This is worse than ChaosDB for AWS. @orcasec gained access to all AWS resources in all AWS accounts! They accessed the AWS internal CloudFormation service. Separately, they did something similar for Glue.
25
473
1K
AWSSupportServiceRolePolicy just got s3:GetObject. 😱 That role is supposed to only have metadata visibility. @AWSSecurityInfo you need to roll that back.
15
149
653
There has never been an encryption related announcement from AWS that I didn't stare at thinking "You weren't doing that already?!?" 😳.
AWS Secrets Manager now automatically enables SSL connections when rotating database secrets. AWS Secrets Manager now transparently supports SSL connections when rotating database secrets for Amazon RDS MySQL, MariaDB, SQL Server, PostgreSQL, and Mo.
14
73
465
Big news! I'm shutting down my consulting business and just had my first day with @aurora_inno where I'll be leading AWS security. We're hiring!. I suspect I'll be busy for a while, so I wanted to write down some project ideas I wasn't able to get to:
63
31
429
S3 is designed to lose only 1 object per year for every 100B objects (which is really good!), but it means it now loses 2000 objects per year.
Welcome to #AWS Pi Day 2022 - . Amazon S3 now holds more than 200 trillion (2 x 10^14) objects (almost 29,000 objects for each resident of planet Earth) and averages over 100 million requests per second!.
9
45
263
Yikes! 😱 Project Zero found an issue that allows an attacker to impersonate any AWS IAM role (and similar GCP attack) to obtain secrets from Hashicorp Vault. The concept generically applies to likely lots of other software that tries to prove an AWS identity to something else.
2
102
245
Open-source Windows x86,x64 debugger http://t.co/gKefR9GO5W with IDA-like jump target side bar. http://t.co/dGlw76KbrW.
13
223
229
Cool AWS attack research by @Ryan_Jarv! If you have the ability to change route tables in a VPC and control an EC2 there, you can give custom userdata to all EC2s to get code exec on them. Presented at @BSidesDetroit. Slides and video:
1
56
215
Cool new AWS security tools coming out of @NCCGroupInfosec recently:.- - These have some similarities to CloudMapper command's, but do some things differently.
1
85
188
Don't hire consultants that break NDAs and publicly shame their clients in order to win Internet points.
This Associated Press story includes references and quotes from a guy who did an audit (not strictly security) for Colonial in 2017 that found “atrocious” information management practices and “a patchwork of poorly connected and secured systems.”
7
19
151
Cloud vulns of the past 4 weeks 🧵:.Azure:.- ChaosDB: - Azurescape - OMIGOD: - Log Analytics role privesc:
This took almost a year to get through the disclosure approval process, but here's the @NetSPI blog that covers the privilege escalation issue (now fixed) that we found with the Azure Log Analytics Contributor role -
4
63
153
This is amazing and terrifying. Azure Sentinel looks to be more capable of monitoring AWS environments than AWS's own GuardDuty. 😮 Specifically, the ability to detect IAM role credential exfil
#AzureSentinel❤️#AWS. See ⬇️as @ashwinpatil sets the stage to executes a cloud kill chain - from abusing IAM previliges in AWS to exfilling data, mimicking the Capital One Breach -- followed by detection logic. cc: @0xdabbad00.
2
54
149
Access Denied errors are going to say why type of policy is denying them! (SCP vs resource vs IAM vs boundary vs VPC end-point, etc.) This is going to be a huge help for debugging these.
The AWS Security, Identity & Compliance Blog #AWSSecurity.By: Guaravee Gandhi*.
12
31
145
It's out! Open-source tool for visualizing #awscloud environments developed at @duosec: Demo: #cloudsecurity.
4
76
147
Slides from my talk at #IRespondCon. Main points: For IR on AWS if you don't have logs already in ELK/Splunk:.- Use CloudTrail Event History for 90 days of guaranteed to exist CloudTrail logs that an attacker can't touch. - Learn jq and Athena.
2
55
131
Thank you @cloudflare for your R2 announcement 2 months ago to force AWS to reduce their egress charges.
#AWS Free Tier Data Transfer Expansion – 100 GB From Regions and 1 TB From Amazon CloudFront Per Month -
3
23
128
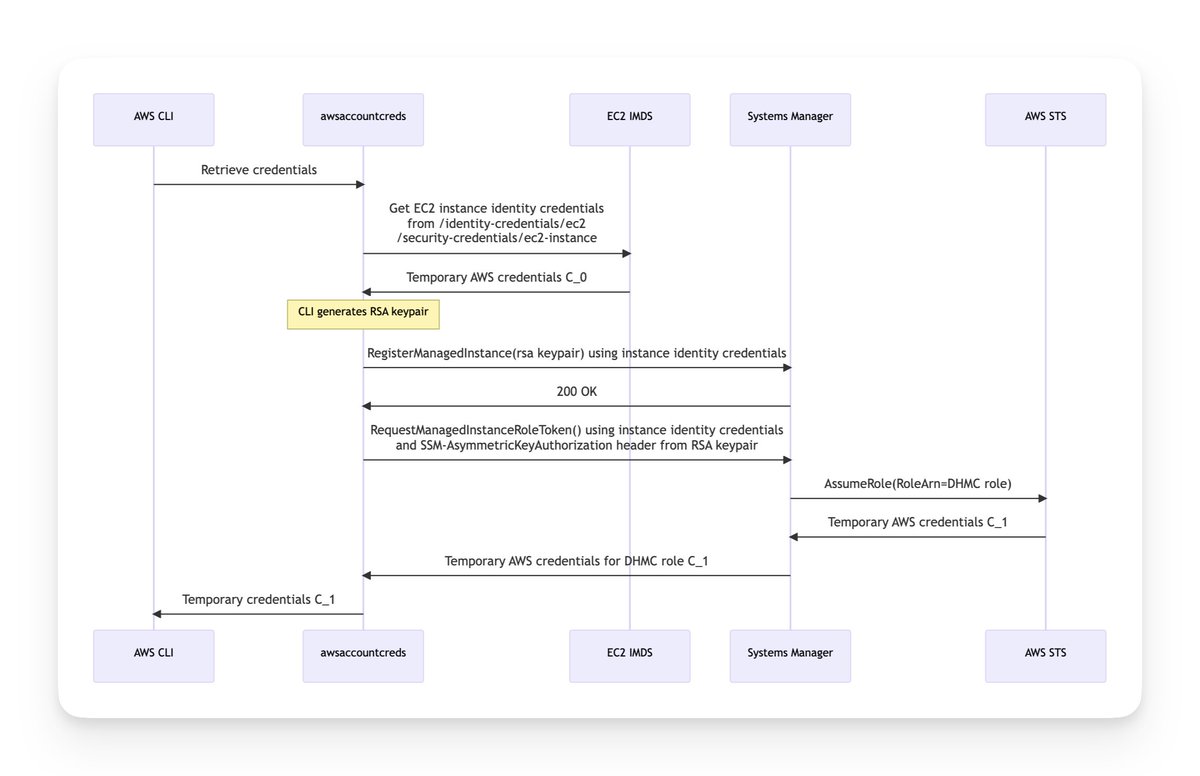
I am in constant awe of Aidan's ability to quickly jump onto a new feature, figure out how it works, develop a new tool that uses that, write a blog post, and in this case communicate findings to AWS security and create a diagram! This was 75 hours from announcement to all this!.
I published a blog post (and PoC CLI) describing how the new Systems Manager Default Host Management Configuration (what a mouthful) provides a new way to pass an IAM role to all EC2 instances in your account+region - even those without instance profiles.
6
10
129
AWS just released a security bulletin about their addition of s3:GetObject to the support role: Below is what I wrote in 2020, where I reference various previous blunders. A few short months later they had the ReadOnlyAccess disaster. 🧵.
It is insane that AWS doesn't appear to have any controls over who at AWS can update Managed Policies. In the past month they've clearly made two innocent blunders here, but what if someone removed key privileges from a commonly used policy? What about insider threats?.
2
32
128
Come work on the AWS security team at Square with me and other great folks! No cloudsec or security experience needed. Remote.
We're hiring early career software engineers who are looking to break into cloud security. No previous security experience required - we'll teach you!. Apply here:.
4
36
120
I am very curious to learn more about the new Roles Anywhere service that hit the SDK today. "Roles Anywhere provides a secure way for your workloads such as servers, containers, and applications running outside of AWS to obtain Temporary AWS credentials.".
AWS SDK for Go has a new release "Release v1.44.48", published at 2022-07-05 18:24:57 (UTC). #pcb_aws.
5
21
120
Multi-account AND multi-region 🤯🤯🤯 Every team at AWS, go talk to the Systems Manager team on how they did multi-region aggregation (looking at you GuardDuty, Access Analyzer, and CloudWatch Events).
AWS Systems Manager Explorer now provides a multi-account, multi-region summary of AWS Compute Optimizer recommendations. Starting today, AWS Systems Manager Explorer provides a summary of AWS Compute Optimizer recommendations to help you improve c.
0
20
116
AWS Lambda API names will no longer include the version in their CloudTrail records on Oct 20. Check your detection rules. Ex. CreateFunction20150331 will now be just CreateFunction. There is no public notice, only an email to select customers. #aws_breaking_change.
3
37
114
😱 If an AWS IAM user is phished, the cookies allow access to be maintained despite changing the password, logging out, or changing MFA. Only defense is DenyAll the user for 12 hours until the cookies expire. Great find @SpenGietz !.
We just released some new research on the power of phished persistent cookies in AWS. Read it on our website here!
6
66
117
The average lifetime of a Lambda run-time between AWS support for it to EOL is 2 years and 23 days (for those that have been given EOL dates so far). The idea of only needing to worry about your code with serverless has some exceptions. #aws_breaking_changes
6
43
112
The proactive community engagement by @notdurson of AWS security is a huge asset to the trust us cloudsec folks have in AWS. Thank you.
3
13
109
Second log4j2 bulletin from AWS (published 7:30 PM PDT on Saturday): More AWS services are impacted. Subtle acknowledgements that S3 and other services are now patched or are being patched. 😬.The recommended WAF rules do not look comprehensive.
AWS security bulletin on the log4j issue: Doesn't say much other than you should use their WAF product. which can be bypassed.
0
39
113
The nice thing about AWS AZ's is a guarantee that they are physically spread out ("many kilometers"). GCP zones on the other hand are located within the same building, so a physical incident impacting one zone (a flood in this case), impacts all within the region.
Update: High Multiple Products incident: Multiple Google Cloud services in the europe-west9 region are impacted. Summary: Multiple Google Cloud services in the europe-west9 region are impacted 1/11.
7
18
108
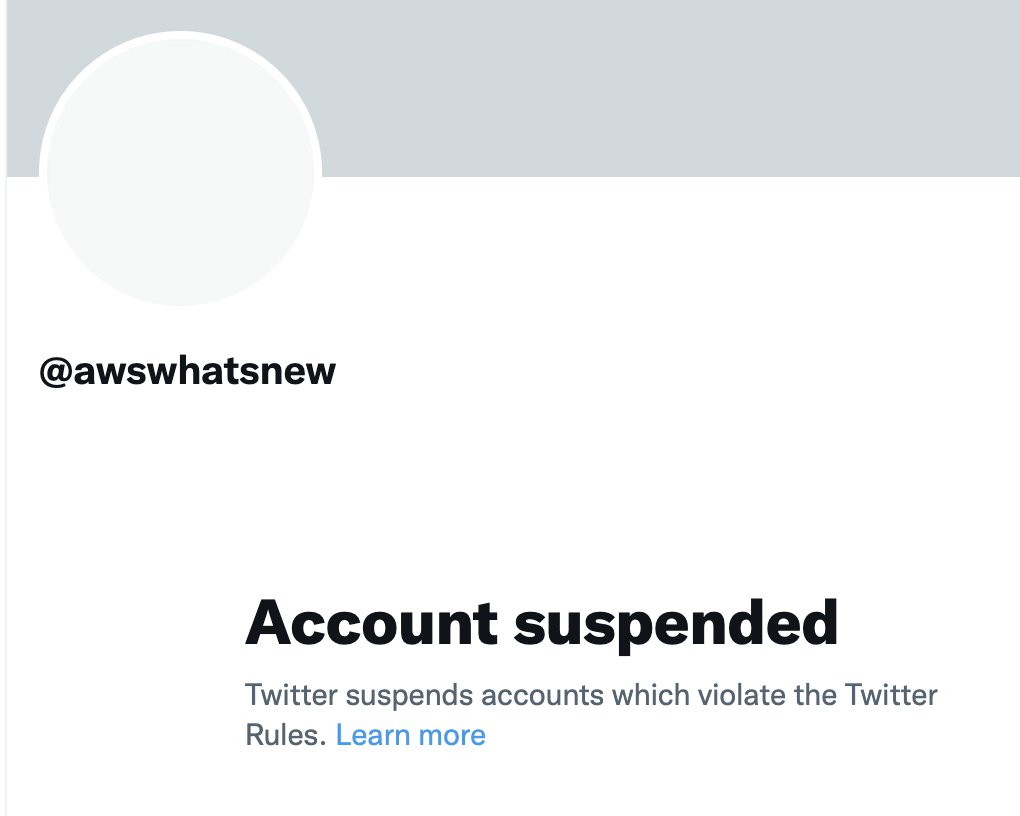
Hey @TwitterSupport, please re-enable this account: @awswhatsnew It just tweets the links from Amazon's RSS feed.
5
10
105
AWS re:Invent 2021 Youtube playlists are up. Here is Security and Compliance and Identity. h/t @zoph.
1
33
110
Steps AWS can take to help customers avoid breaches like Cap One's (based on some assumptions of what happened) #awswishlist:.- HTTP Host Header check the metadata service to prevent SSRF. Easy game changing win. - Improve granularity of Access Advisor to action level. 1/2.
15
35
107