Stefán Jökull Sigurðarson
@stebets
Followers
2K
Following
10K
Media
1K
Statuses
15K
Microsoft MVP, Code Wrangler/Chief Iceberg Rider and Employee 1.0 @haveibeenpwned, @dotnetfdn member, @[email protected]. He/him
Reykjavík, Iceland
Joined February 2009
It’s official now. I’ll be joining @troyhunt and @Charlotte_Hunt_ later this summer, working full time for @haveibeenpwned!Really excited about this awesome opportunity and I’m very much looking forward to it! 🥳.
Massive day for @Charlotte_Hunt_ and I today as we welcome our first ever *proper* @haveibeenpwned employee: @stebets
10
6
115
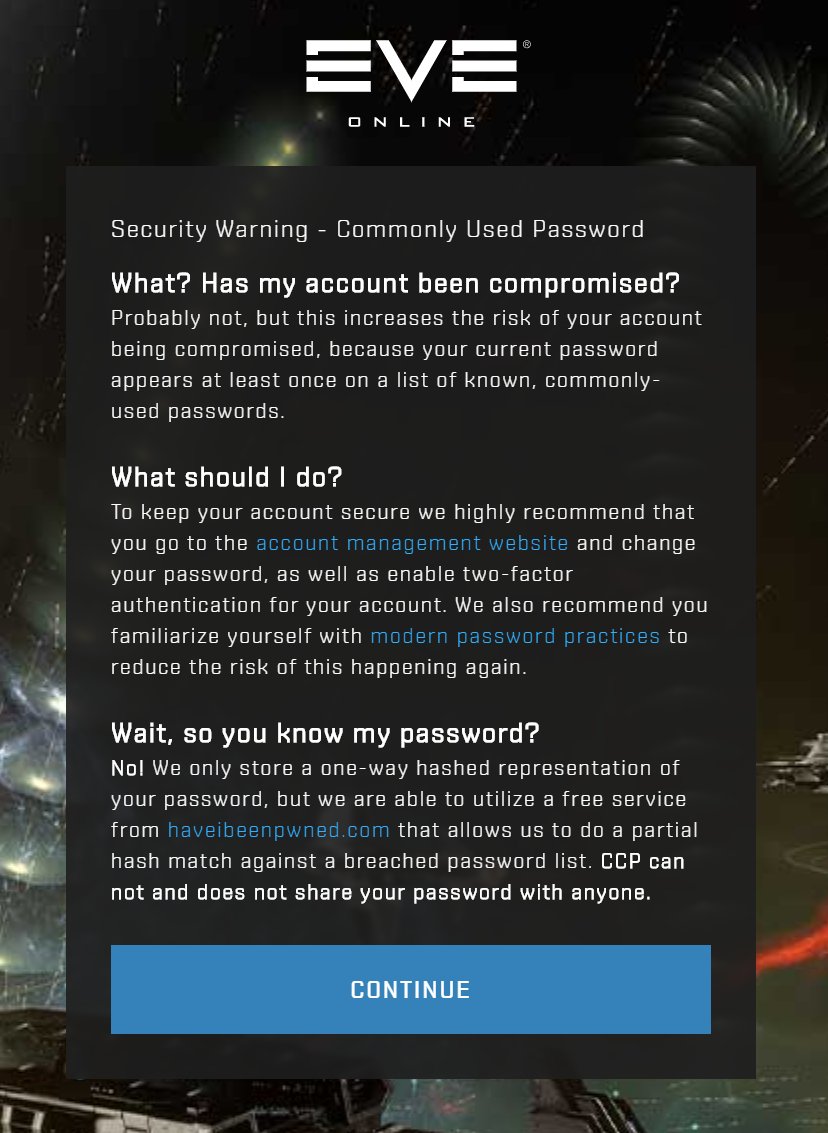
Password reuse is one of the biggest threats to our online security. We integrated @haveibeenpwned into our registration and login funnels for @EveOnline, specifically to help users be more aware of this problem.
15
113
668
Here's what updating an Core app from .NET Core 3.1 -> .NET 5.0 looks like :D No code changes, just a new framework target. #dotnet #performance
16
75
403
@richo3000 @iamharaldur @Delta News flash, Halli is not a Delta employee and does not have to adhere to their policies.
3
0
339
@Nick_Craver That’s easy to fix. Just remove 2FA. It’s bloatware anyhow and makes it harder for people to log in. Disable that rate limiter on logins while you are at it. We want people to log in faster. Also IP checks and credential stuffing checks. This is all slowing Twitter down!.
5
10
324
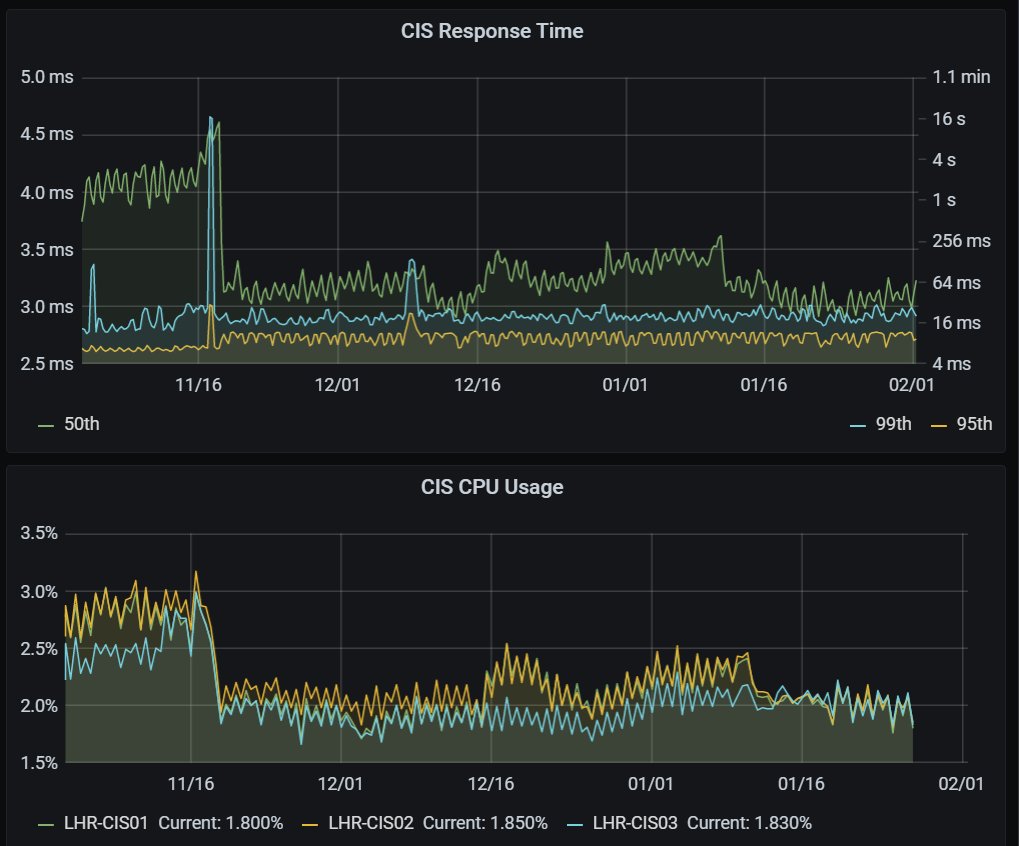
Just upgraded a major service from .NET Framework 4.8 to .NET 5.0 this week and after ironing out a few bugs we're seeing MASSIVE improvements in response times and reduced CPU usage. I'll post more data later today hopefully :) #dotnet #performance.
11
22
266
@Nick_Craver Away with CSRF checks so we can automate the login process. And stop hashing the passwords, it’s wasting CPU cycles.
8
8
242
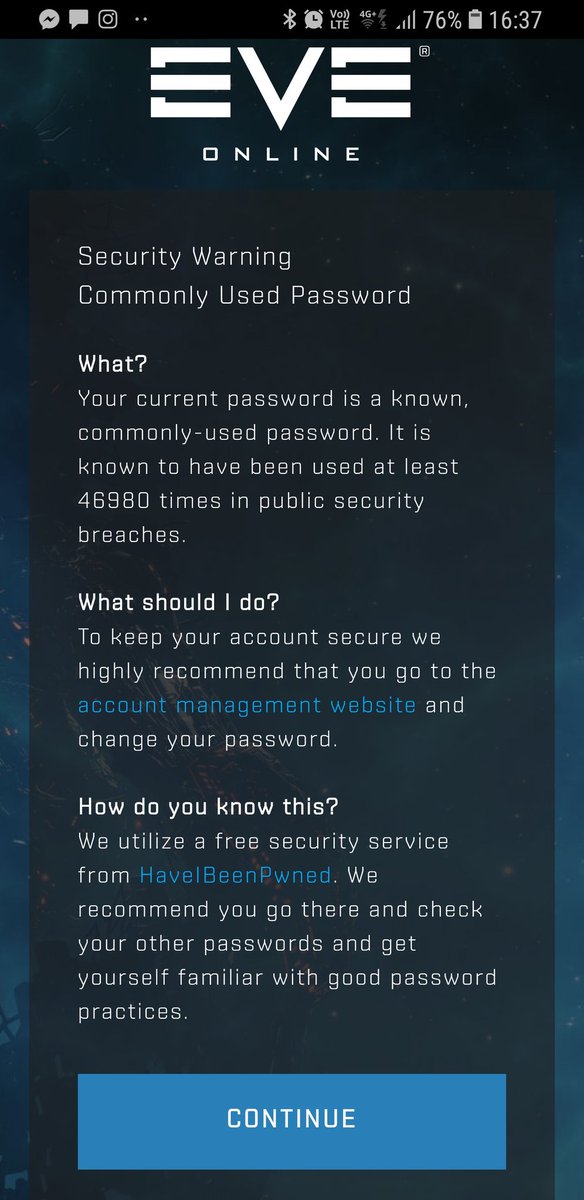
WIP: Helping our @EveOnline players to be aware if their passwords are on a list of known compromised passwords. Thanks @haveibeenpwned ! CC: @troyhunt #tweetfleet #security #workinprogress
8
46
185
Just blogged: Real world example of reducing allocations using Span<T> and Memory<T> #dotnet #performance #rabbitmq.
3
55
181
@SwiftOnSecurity Saw USS Gerald Ford up close st NDC Oslo in may. It’s huge! We also got chased off for coming too close 😅
3
1
157
List of people I follow for high-perf topics in .NET (Framework and Core):.@ben_a_adams .@davidfowl .@marcgravell .@Nick_Craver .@damageboy .@xoofx .@stevejgordon .@maoni0 .@SitnikAdam .@konradkokosa .@jaredpar .@matthewwarren .@benmwatson.
9
34
150
Wow, look at the the difference in CPU usage between .NET Framework 4.8 and .NET 5.0! Awesome performance improvements from the @dotnet team. Well done! #dotnet #performance
5
25
146
So. I promised more data :) Let's start with looking at response time which has improved in several ways. We deployed the new version at 10:30 last monday. The median response time has dropped almost 60% (from 5.5 - 7ms previously to about 2.5ms after). #dotnet #performance
Just upgraded a major service from .NET Framework 4.8 to .NET 5.0 this week and after ironing out a few bugs we're seeing MASSIVE improvements in response times and reduced CPU usage. I'll post more data later today hopefully :) #dotnet #performance.
1
23
128
Updated an app from .NET 5.0 to .NET 6.0 (A). Almost no code changes. Not much perf difference, as the app is already heavily optimized. Then turned on Profile Guided Optimization (B). Boom, instant 5% improvement in median response times and CPU usage drop. #dotnet
7
16
121
Ok, Microsoft Edge vafrinn var að bæta við íslenskum talgervli (text-to-speech) og hann virkar fáránlega vel! CC: @mi_malt @liljaalfreds
3
6
89
I always knew the internet was shit when it came to ads and tracking, but I didn't quite expect this. Stats from my Pi-Hole proxying my DNS at home for less than 12 hours. overnight!. Thanks to @Scott_Helme for writing an excellent guide on it:
3
24
76
@Nick_Craver Look! A famous experienced software person that makes mistakes!!! Everyone does it. We fail, we learn, that's how things work and get improved :) #impostersyndrome.
1
9
73
@larsklint I wish websites would stop validating email addresses. There's always an overwhelming chance they are doing it wrong.
3
8
67
@krstbjrg Hæ @logreglan. Vona að þetta sé eitthvað sem verði skoðað með tæknimönnum @discord og einhverjir dregnir til ábyrgðar!.
0
0
62
@Jon_Gnarr @geirfinns Til hamingju! Þú hefur unnið internetið! Hvert á ég að senda verðlaunin?.
1
0
57
Woohoo, the .NET Core 2.1 NuGet packages have started flowing. Here's System.Memory!!! Hi Span<T>!! CC: @ben_a_adams @benmwatson #perfmatters.
2
21
57
As of now, the @EveOnline SSO is enforcing a CSP (Content Security Policy)! This has taken a few weeks to prepare and get right but it's finally live! Big shoutout to @Scott_Helme, @troyhunt and @reporturi for their inspiration and assistance. #tweetfleet
1
11
52
More @EveOnline account security improvements are now live with some nice things from our friends at @1Password. Additional credit goes to @haveibeenpwned, @troyhunt and @Scott_Helme for good advice and feedback. Thanks everyone! #tweetfleet .
0
10
48
@solskinssolveig Á þeim nótum. myndi frítt námskeið til þess að finna og eyða svona hlutum, ásamt því að kenna öryggi og hvernig á að halda sínum gögnum og tölvunotkun prívat vera eitthvað sem væri áhugi fyrir? Finnst það vera eitthvað sem ég gæti lagt af mörkum með mína þekkingu.
1
2
46
@adhdjesse Me in focus mode….“Oh, it’s almost noon. I should get some lunch, I’ll just finish this one thing first”. *what feels like 10 mins passes”. “Oh god I’m late to pick up the kid from kindergarten (4:00pm), I forgot to let the dogs out and I’m hungry! Where are the car keys?!”.
1
1
47
@troyhunt @haveibeenpwned Yup me too. Who runs that site anyway?! I noticed it recently lost it's EV certificate. Not sure I trust it anymore. .
3
0
45
This post from three years ago amazes me still to this day! The difference from Framework 4.8 to .NET 8 today would be even more massive!.
Wow, look at the the difference in CPU usage between .NET Framework 4.8 and .NET 5.0! Awesome performance improvements from the @dotnet team. Well done! #dotnet #performance
2
4
46
So, my talk on account security in @EveOnline from #NDCSydney just showed up online :) Here it is:
2
14
41
When @haveibeenpwned does a full cache purge like when they upgraded their PwnedPasswords to v6 the other day, how quickly does the @Cloudflare edge node cache populate? Turns out it's quick (around 5 hours) for our @EveOnline implementation at least :) CC: @troyhunt @IcyApril
1
4
44
Will write a blog post about the learnings on it. It will include a bunch of references to Span<T>, Memory<T>, slicing and BinaryPrimitives…. funtimes :D #dotnet #performance.
5
3
45
Did you know that implementing a check against @haveibeenpwned (thanks @troyhunt) for your account registration and login pages helps people create more secure passwords? After implementing it and a few iterations over a couple of years we have seen some very solid improvements.
1
11
40
This is funny but a serious issue though. Don't skip biometric authentication just because someone can hack around it with lab equipment or unrealistic scenarios. It's much easier to spy on you typing your PIN or pattern than it is faking your face or fingerprint/iris.
If your threat actor is someone physically present who can grab your phone whilst you’re asleep then slip glasses onto your face without waking you whilst hovering the phone over your head, read this: “Apple's iPhone FaceID Hacked In Less Than 120 Seconds”
4
12
42
I can hardly believe it but one of my talks made it for the #NDCOslo agenda, It was actually one picked out of over 1500 talk submissions!!.I'm deeply honored and can't wait to step on that stage and also to watch and learn from all the other fantastic speakers and friends there.
5
1
43
Using .NET and need to cache things? Try FusionCache, made by @jodydonetti. I've written my own layered cache in the past, but FusionCache just makes it easy and extensible as well. We're using the latest version in @haveibeenpwned and it's been awesome!.
FusionCache v2 is finally out 🎉. I still can't believe it: months of work & experiments, tons of features, perf tuning & more. The big themes are:.🏷️ Tagging.🧼 Clear().Ⓜ️ Microsoft HybridCache support. The gargantuan release note has the jiucy details!.
1
2
41
Hvernig ætli þetta hafi farið með fragile karlrembuna í þessum @OlofTara? Það sorglega við þetta þó er að í karlaboltanum hefðu 15 gæslukallar verið búnir að tækla hann. En Meistaradeild kvenna í fótbolta verðskuldar greinilega ekki annað en að leikmenn sjái um þetta sjálfir.
3
1
36
As always, even when @haveibeenpwned does a complete @Cloudflare cache purge, it recovers remarkably quickly. Always impressed by this! Good job @troyhunt and @IcyApril :)
2
2
34
Poll and brainstorming time. If we detect that a user has a pwned password (according to @haveibeenpwned) and is therefore an easier target in the event of a breach, should we:.
35
17
34
Well would you look at that @davidfowl! My PR to add OpenTelemetry to the .NET RabbitMQ library has been merged. Next up: some improvements to OTel baggage propagation (hi @MartinDotNet) and some docs + examples! I'll also look at getting this integrated into Aspire (unless.
2
4
34
And merged! Feels good to be able to contribute openly to @haveibeenpwned Pwned Passwords since this free service from @troyhunt has had a measurable impact on account security in @EveOnline. Looking forward to providing more contributions :).
0
4
30
Can't say our @EveOnline players aren't dedicated to finding their characters in all sorts of weather. or is he perhaps scouring for victims.
5
5
32
An absolutely HUGE fight taking place in @EveOnline right now! Over 6500 players at the start, around 5.900 right now but it's still going strong. Check it out! #tweetfleet
1
3
31
@salkadelasol Næst færðu að heyra eina af klassísku línuna fyrir konur í skemmtanabransanum: "Þú þarft bara að vera duglegri að koma þér á framfæri!".
0
0
29
@Bjarkiswagmoney @eddafalak Húmor þarf að vera eitthvað sem er fyndið. Þetta er bara ekki fyndið.
1
0
31
@Scott_Helme @j_opdenakker @troyhunt Here are the promised 2FA stats. Here are the ratio of users that have enabled 2FA:. % of all users since launch (including dormant): 0.35%.% of active users since 2FA was available: 1.45%.% of active users since @haveibeenpwned integration: 4.39%.
5
7
29
@BubbiMorthens Fólkið segir að tónlistin geri börnin að dópistum, tölvuleikir geri þau að morðingjum og sjónvarpið að fávitum. Kannski ætti fólk að hætta að láta þessa hluti ala upp börnin sín og eyða frekar tíma með þeim og ræða við þau sem jafningja, frekar en að agnúast útí afþreyinguna.
0
0
30
@the_brc The padlock symbol has nothing to do with safety or trust. just the confidentiality of data between the client and the server (website). Associating the padlock symbol with trust is just plain bad advice!. CC: @Scott_Helme.
0
0
28
Honoured to be a part of this project! Thanks for the opportunity @troyhunt.
I’m enormously pleased today to finally deliver on 2 long-standing promises: open sourced HIBP code and an ingestion pipeline for newly seen passwords provided by law enforcement agencies, beginning with the FBI:
0
2
26
@MiddleOfMayhem @joerogan @nypost Nothing in that article on Graves, Grusch, Fravor or Underwood or the data they have provided. Please try again.
1
0
23
And this is why @troyhunt has an entire presentation just on IoT devices and bad security.
A new security flaw (CVE-2020-6007) in Philips Smart Light Bulbs 💡 could let remote attackers gain access to your entire WiFi network (over-the-air without cracking password) & launch further attacks against other devices connected to the same. Details:
1
8
26
And we're live on TQ! Just English for now (translated versions coming in the next few days) but we're now actively notifying pilots when logging in either through the launcher of websites. Fly safe capsuleers! CC: @EveOnline @troyhunt #tweetfleet
WIP: Helping our @EveOnline players to be aware if their passwords are on a list of known compromised passwords. Thanks @haveibeenpwned ! CC: @troyhunt #tweetfleet #security #workinprogress
1
11
25
Once again, a small token of gratitude from us at @ccpgames for the advice and help in improving our account security as well as providing @haveibeenpwned and @reporturi. You and @Scott_Helme deserve it :).
Had a lovely care package arrive from Reykjavik courtesy of @stebets and the @EveOnline folks today. They’ve been making great use of Pwned Passwords and sent me over some pretty epic EVE swag and a sizable beer glass - which I have subsequently filled! 🍺
0
5
26
Incredibly excited and happy to announce that my talk "EVE Online: Defending our players from hackers and the evolution of account security" has been accepted for #ndclondon!.
2
1
24
Achievement unlocked! My blog has now been added to the HSTS browser preload list :) Thanks @troyhunt and @Scott_Helme for letting us know about this :)
2
2
27
@Nick_Craver Not sure what changes got deployed to the Azure Functions Runtime on May 16th but I like them! This is the last 90 days for a function that hasn't been updated since March 23rd.
1
2
25
Starting a small, programmer oriented, blog series on our security work for @eveonline. First part is up right now!.
0
6
25
@troyhunt @haveibeenpwned @Cloudflare @EveOnline @IcyApril So @troyhunt, congratulations and a really happy @haveibeenpwned birthday from us here at @EveOnline. Keep up the awesome work, we all appreciate it :)
2
3
22
So by doing stuff faster, we also start using DB connection synchronously faster. We uncovered this by using the awesome Ben.BlockingDetector NuGet package from @ben_a_adams. You can find that here:
1
2
24
Woohoo, #ndclondon feedback is in for my talk 💚 = 38.💛 = 1.❤️ = 0. Thank you all for providing feedback. Now going to enjoy the rest of the conference, it has been absolutely awesome so far! Good job @NDC_Conferences!.
1
0
23
@atli_vidar Pro tip, þakkaðu henni fyrir að hafa unnið allt hard-workið og segðu henni hvað þetta var auðvelt eftir að hún var búin að preppa hana svona vel. P.s. Ég veit alveg að við pabbarnir erum með superior svæfingarskills, en þetta er best fyrir alla.
0
0
23
@GossiTheDog I'm pretty sure it was a dodgy looking guy wearing a Guy Fawkes mask and a black hoodie. Those hackers are THE WORST! Most likely had stickers on his laptop as well, maybe even a "Who the f*** is @Scott_Helme" sticker.
2
0
22
Blogged! Performance optimizations and benchmarking in C# using #benchmarkdotnet CC: @matthewwarren.
3
11
24
Come see my talk on @haveibeenpwned and how to serve billions of request and terabytes of data without going broke @ @NDC_Conferences - Room 8 - 13:40 today! It's going to be fun :).
1
1
23
Thinking of doing a complete brain dump on Twitter of a workday tomorrow as I work on EVE SSO tickets and improvements. How does that sound #tweetfleet? Beware, it'd be full of technical jargon and programming concepts and probably the occasional rage-tweet. .
3
1
24
Here's a poll for you EVE players and #tweetfleet. If we discover that your EVE account password has been used in a data breach elsewhere, how should we treat that account+password?.
1
5
21