Sam Curry
@samwcyo
Followers
88K
Following
8K
Media
172
Statuses
3K
Hacker, bug bounty hunter. Run a blog to better explain web application security.
Omaha, NE
Joined January 2017
We recently found a vulnerability affecting Hyundai and Genesis vehicles where we could remotely control the locks, engine, horn, headlights, and trunk of vehicles made after 2012. To explain how it worked and how we found it, we have @_specters_ as our mock car thief:
76
1K
5K
New writeup from @_specters_ and I: we're finally allowed to disclose a vulnerability reported to Kia which would've allowed an attacker to remotely control almost all vehicles made after 2013 using only the license plate. Full disclosure:.
92
1K
4K
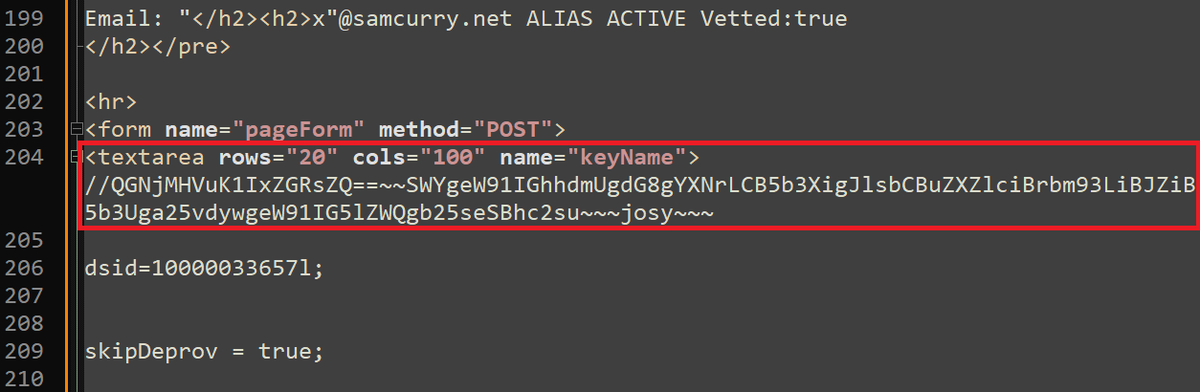
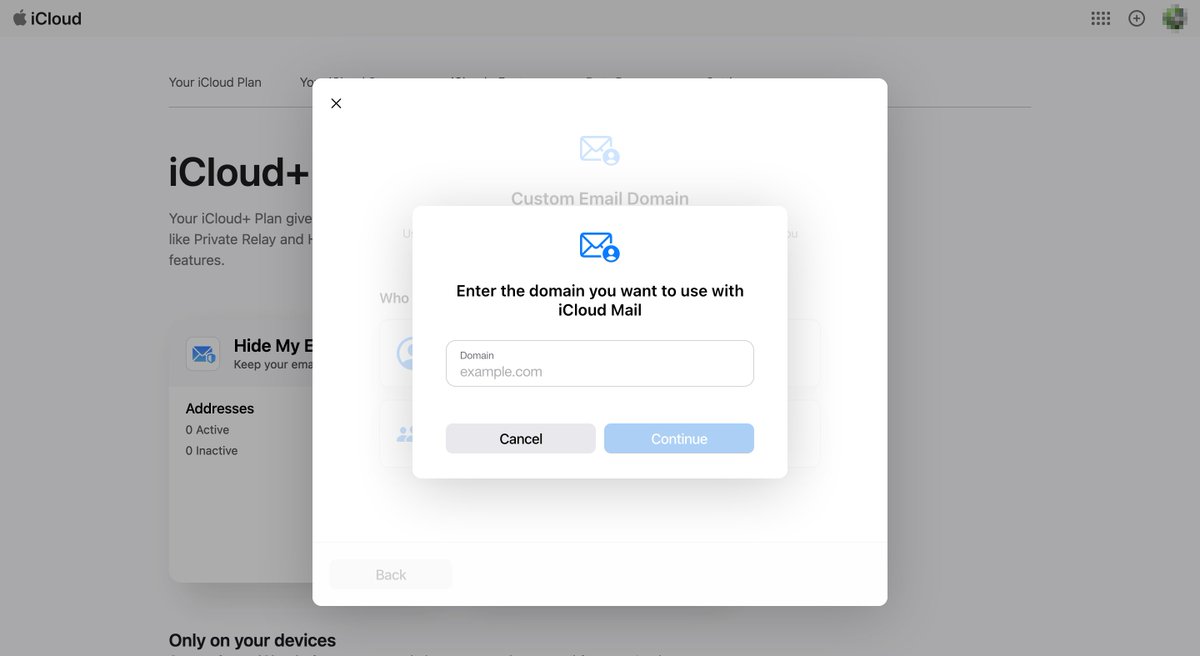
New writeup:. "We Hacked Apple for 3 Months: Here’s What We Found". Featuring. @bbuerhaus, @NahamSec, @erbbysam, and @_StaticFlow_ .
65
1K
3K
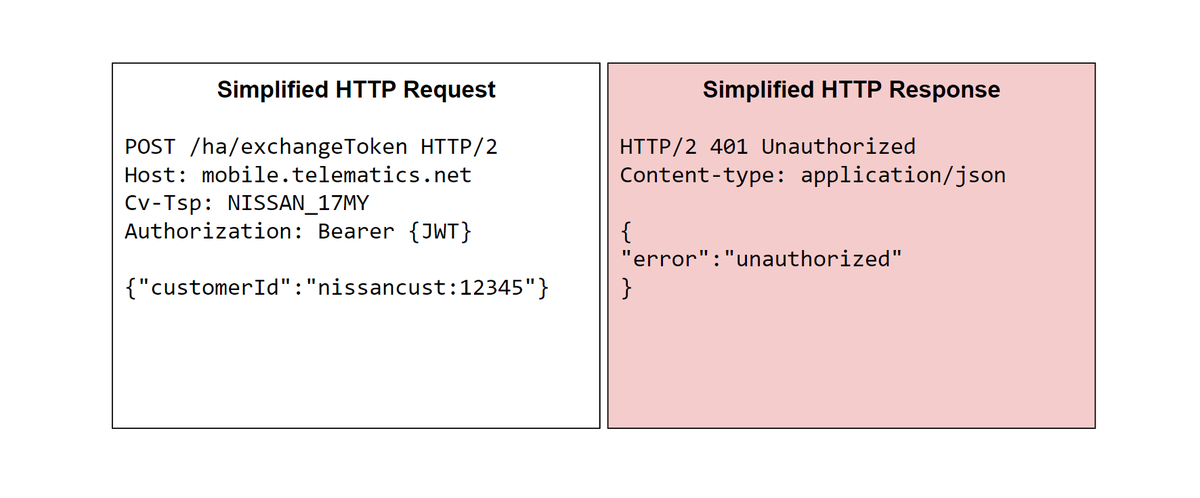
Super excited to release our car hacking research discussing vulnerabilities affecting hundreds of millions of vehicles, dozens of different car companies:. Contributors:.@_specters_ @bbuerhaus @xEHLE_ @iangcarroll, @sshell_ @infosec_au @NahamSec @rez0__.
64
754
2K
"Hacking Starbucks and Accessing Nearly 100 Million Customer Records" - write up on a recent directory traversal vulnerability found with @Rhynorater ☕️.
42
530
1K
New writeup, one of my favorite bugs 🤠 -. Filling in the Blanks: Exploiting Null Byte Buffer Overflow for a $40,000 Bounty. Featuring. @d0nutptr @0xacb @Regala_ @JLLiS @Yassineaboukir @plmaltais
26
484
1K
Thank you for reading, huge shout out to all of these amazing people for helping with this research:.@_specters_ @bbuerhaus @d0nutptr @xEHLE_ @iangcarroll @sshell_ @infosec_au!. We hope to publish more security findings over our few months spent researching this topic soon.
42
39
1K
New writeup:. "Hacking Millions of Modems (and Investigating Who Hacked My Modem)". Thanks for reading! Huge thanks to @blastbots, @bbuerhaus, @infosec_au, @d0nutptr, @iangcarroll, and everyone who reviewed the post beforehand.
48
395
1K
New blog post with @infosec_au:. We found a vulnerability in Subaru where an attacker, with just a license plate, could retrieve the full location history, unlock, and start vehicles remotely. The issue was reported and patched. Full post here:
47
299
965
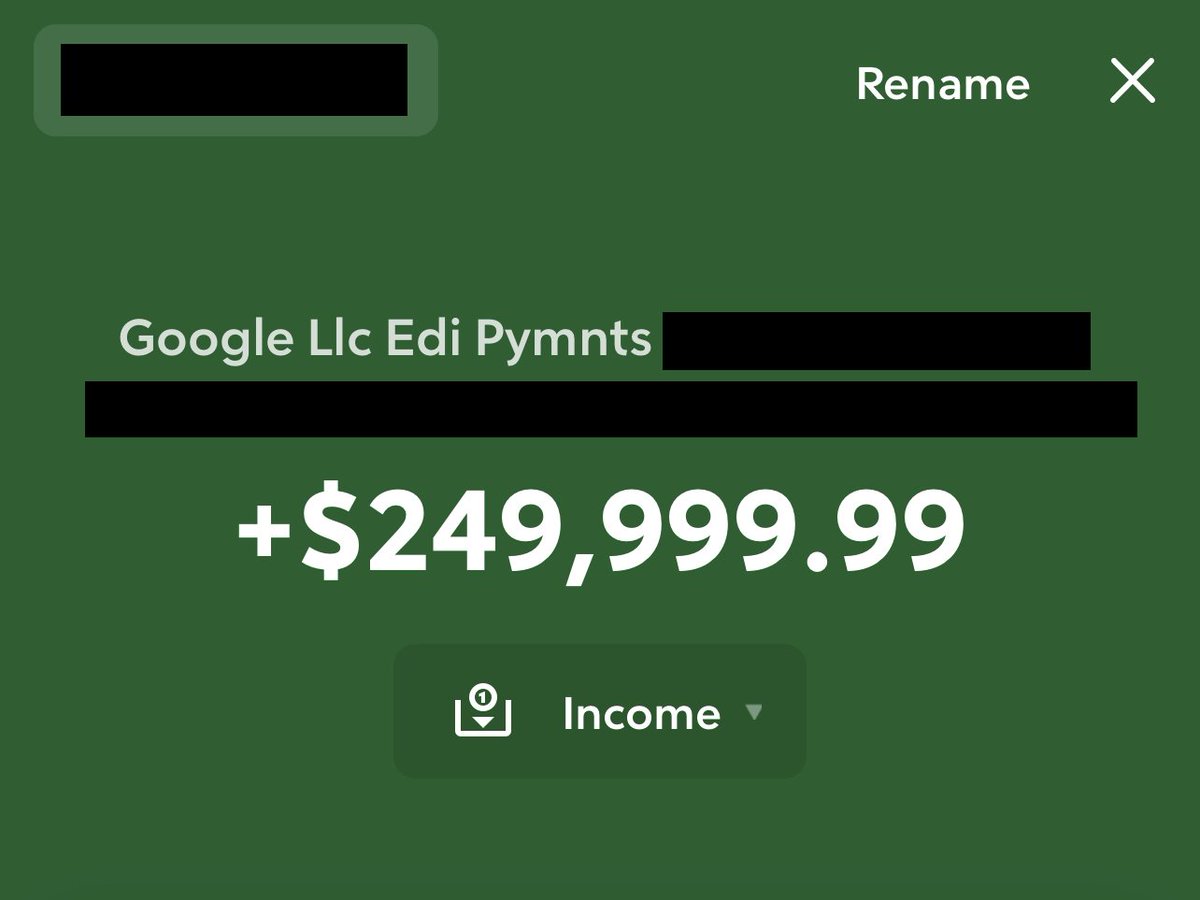
New writeup:. Between March, 2023 and May, 2023 we found multiple critical vulnerabilities in points[.]com the global provider for major airline and hotel rewards programs. Full post is available here:. Work from:.@infosec_au @iangcarroll.
24
258
664
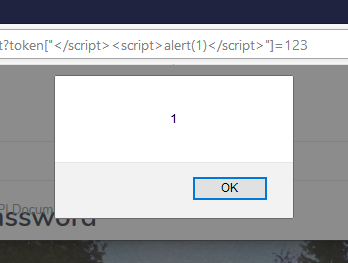
Had some recent success using untranslatable Unicode in place of a "?" when attacking URL parsers for SSRF/OAuth issues. What worked was. \udfff -> � -> ?. Therefore. {"redirectUri":" https://attacker\udfff@[victim]/"}. Equals. Location: https://attacker?@[victim]/
5
209
626
New blog post detailing some findings from auditing the Next.js ecosystem:. "Exploiting Web3's Hidden Attack Surface: Universal XSS on Netlify's Next.js Library". Huge thanks to @infosec_au and @bbuerhaus for helping explore this!.
12
185
534
New blog post on hacking EPP servers:. How we could've taken over the .ai, .bj, .bw, .ci, .gl, .ke, .kn, .lb, .ly, .mr, .ms, .mz, .ng, .pyc, .rw, .so, .ss, .td, and .zm TLDs. Work from @rhyselsmore, @bbuerhaus, @infosec_au, and myself.
16
174
562
Found some fun vulnerabilities on Instapage and HubSpot with @bbuerhaus, @sshell_, and @xEHLE_. Here's a thread with a couple mini writeups for them:. There are a few routes on the Hubspot CMS which are actually reverse proxies to Hubspot's CDN, you can see the "hs-fs" one below:
18
201
561
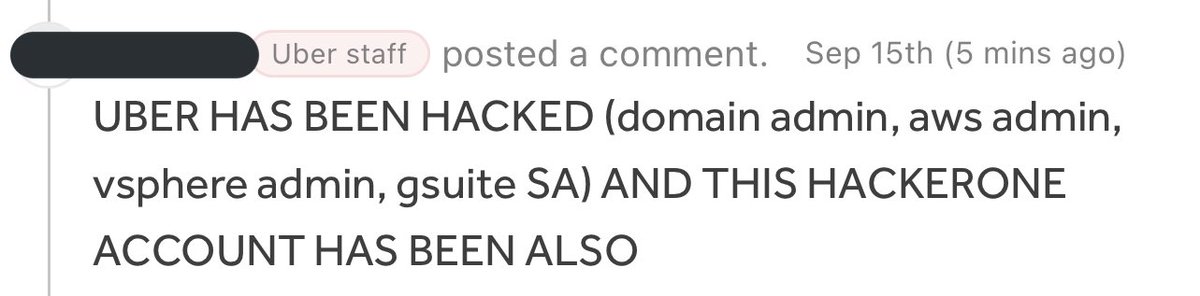
Here is the initial release of the PoC for CVE-2021-27651:. There were a few large organizations affected by this including the NSA, FBI, Unilever, Apple, American Express, and Wells Fargo. Probably somewhere around ~3,000 different customers.
Users of the Pega Infinity enterprise software platform are urged to update against a critical vulnerability (cc @samwcyo).
8
142
389
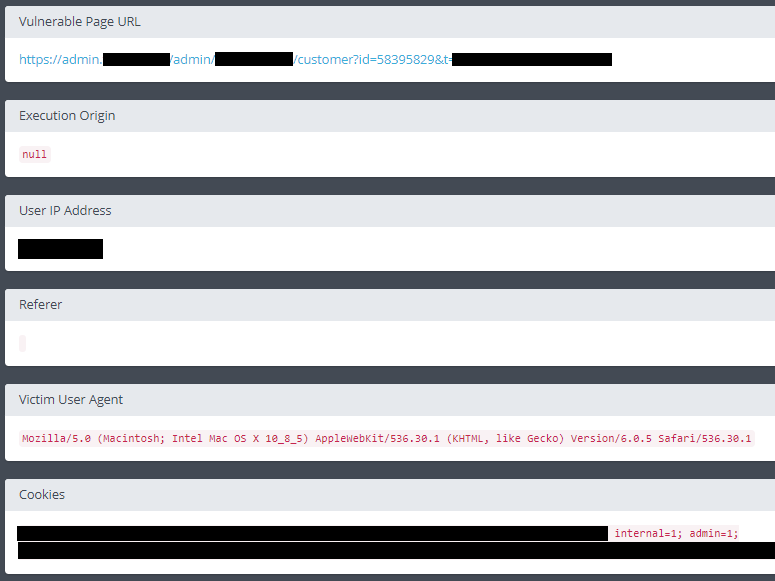
Ran into a neat authentication bypass via extension whitelist today with @bbuerhaus and @_specters_:. GET /admin%2ejsp%3b.png. Was able to turn a number of post-auth SQL injections into pre-auth vulns. Always fun messing with these. 😁.
3
94
387
Have just sent a blog post to a security team to review for publication and am super excited about it. The draft PDF is 53 pages long and is the result of 3 months of work alongside @bbuerhaus, @NahamSec, @erbbysam, and @_StaticFlow_. Hoping to publish it by the end of the week!.
15
31
362
Been working on some neat stuff which we can hopefully release soon:. - Found >50 critical bugs on a large target as a small team, wrote a long blog post for it (pending approval).- Collaborated with @infosec_au on an 0day (pending approval). Wish I could share them both now! 😄.
9
11
330
I was joking about adding a blind XSS payload to my Google Nest, but then it actually fired on their admin panel and I got rewarded through their VDP. 🥲. Huge thanks to the amazing @IAmMandatory for maintaining @XssHunter for free.
7
40
323
Cryptocurrency web apps are all mostly ran on the same 3 or 4 different hosting platforms. Over the last few months, we've been able to find vulnerabilities where we can write/modify content on nearly all of them. Excited to talk about this (and more) at @_kernelcon_ soon!.
8
29
285
Happy to have participated in the inaugural election security research forum at MITRE where we spent time auditing US voting systems. Thanks to @CISAgov, @Hacker0x01, @Bugcrowd, @jackhcable, and everyone who helped put the event together.
7
11
280
Picked up @0xteknogeek, @sshell_, and @ret2jazzy from the airport and they immediately found a Tesla vulnerability playing around with the screen in the back seat.
10
19
278
Will be giving a talk about hacking online games with only web security experience on Saturday, June 13th. This talk will discuss the parallels between web hacking and game hacking, then explore some neat vulnerabilities affecting MMOs and popular Steam games. More info below -.
We are ONE week away from #NahamCon2020: A virtual hacking conference with talks/workshops by @jeff_foley, @Jhaddix, @securinti, @snyff, @BitK_, @samwcyo and more! Check out the entire schedule on We are also hosting a CTF! Come play and win some cash!
11
44
269
If you're interested in learning more about DeFi hacks, @OriginProtocol has a well maintained repository of post-mortem writeups detailing a bunch of neat real world exploits here:
5
50
256
@spikeroche With the account takeover, you could access everything on the user’s SiriusXM account where you could enroll/unenroll from the service, but if I remember correctly the API calls for telematic services would work regardless of whether there was an active subscription.
3
10
251
If you enjoyed "Attacking Secondary Contexts in Web Applications" ( feel free to vote for it here!. There's an amazing amount of fantastic research here and if you haven't already I'd absolutely suggest dedicating a night just to read through all of these.
It's time to cast your vote for the Top 10 Web Hacking Techniques of 2020! Grab a brew, peruse our hefty nomination list, and select up to ten new techniques and ideas you think will have a lasting impact.
8
46
237
Nearly forgot: huge thanks to @netspooky for making the amazing ASCII art in the python script 💕.
7
4
218
Huge thanks to @davidbombal for covering the past car hacking research from @_specters_ @bbuerhaus @xEHLE_ @iangcarroll @sshell_ @infosec_au and I. David and his team put in a ton of effort to research this and asked some great questions. More than happy to share the fun stories.
Hackers remotely hack cars! Ferrari, Tesla, Porsche, BMW, Ford, Kia and so many more 😱. YouTube video: #car #cars #ferrari #tesla #porsche #bmw #ford #kia #mercedes #hyundai #hack #hacker #hacking #cybersecurity #infosec @samwcyo
6
33
228
Over the last few months, myself and a few friends have been building a small security consultancy called @PalisadeLLC. The company is specifically focused on securing web apps that leverage all things crypto (custodial wallets, payment processors, NFT marketplaces, etc.).
18
17
214
It's frustrating, we reported a SQL injection vulnerability to the Vulcan Forged bug bounty program 6 months ago that let you pull master private keys and plaintext passwords. This vulnerability had a similar level of impact, but was rewarded with $2,000. (1/5).
Four cases in ten days. $140M gone from @VulcanForged. "Compromised keys" are so hot right now. But it’s nothing to do with the markets, right?. rekt investigates.
5
36
202
Giving a talk at #NahamCon2022 about 15 different vulnerabilities we found while hacking crypto websites and some of our observations while working on crypto security. Huge thanks to @NahamSec and team for putting together this conference for another year!
3
22
200
Awesome work from @artsploit going over some of the really neat and novel approaches to hacking OAuth. Will be an awesome reference moving forward.
1
63
161