pancak3
@pancak3lullz
Followers
12,824
Following
378
Media
1,359
Statuses
6,237
Explore trending content on Musk Viewer
Kendrick
• 312668 Tweets
Taylor
• 269338 Tweets
Super Bowl
• 265988 Tweets
Drake
• 181034 Tweets
JENNIE
• 143530 Tweets
#TommyHilfigerNYFWxPPGF
• 135587 Tweets
Giants
• 119073 Tweets
Steelers
• 110551 Tweets
Wayne
• 109626 Tweets
Bears
• 107010 Tweets
JISOO AT NYFW WITH TOMMY
• 88689 Tweets
NYFW24 WITH GEMINI FOURTH
• 88034 Tweets
#ZEVENT2024
• 84828 Tweets
Cowboys
• 83096 Tweets
Bengals
• 81657 Tweets
Browns
• 77959 Tweets
Panthers
• 68387 Tweets
Falcons
• 56552 Tweets
重陽の節句
• 50656 Tweets
Raiders
• 48045 Tweets
Chargers
• 41890 Tweets
Seahawks
• 39660 Tweets
Broncos
• 35109 Tweets
Daniel Jones
• 32642 Tweets
Baker
• 29577 Tweets
#GHDBT1
• 27124 Tweets
Caleb Williams
• 27112 Tweets
Seattle
• 27046 Tweets
#わたしの宝物
• 25776 Tweets
Cleveland
• 24594 Tweets
Deshaun Watson
• 23619 Tweets
Tom Brady
• 22196 Tweets
Forbes
• 18281 Tweets
Diggs
• 13220 Tweets
Zeke
• 11999 Tweets
Bo Nix
• 11030 Tweets
Will Levis
• 10962 Tweets
チャウヌ
• 10186 Tweets
Last Seen Profiles
We are proud to announce that we assisted the joint international LE
#OperationEndgame
, targeting notorious botnets
#IcedID
,
#Smokeloader
,
#SystemBC
&
#Pikabot
We provided key infrastructure to LEA and internal partners to disrupt these botnet operations
14
36
244
A couple more updates.
Cc:
@uuallan
1
59
151
Updates include $MSFT Office CVE-2021-38646 and
@billquick
’s web suite CVE-2021-42258.
Also, I feel enough time has passed since continuously trying to reach the company with no response to uncensor the EntroLink PPX-AnyLink 0day item.
Cc:
@uuallan
4
42
124
what the actual fuck?
"...the Company learned that a former executive officer of the Company deliberately de-activated and cancelled the renewal of the Company’s website..."
2
15
100
I expanded upon
@uuallan
's chart and included some non-initial access items.
0
35
96
Superstar75737 realizing his
#Smokeloader
botnet is gone
ALIAS: Superstar75737
#Smokeloader
NAME: ГРУБЕР Айрат Рустемович (Airat Rustemovich Gruber)
DOB: 21.05.1982
SNILS: 07803559786
TIN: 166005711627
PASSPORT: 9204429600
1
7
24
1
10
74
#ShadowSyndicate
appears to be much, much more than a RaaS affiliate...
Ref:
#LetsStopCybercrime
#CybercrimeFightersClub
2
18
71
#ApacheStruts
#CVE201811776
#snort
Some SNORT signatures I worked on today. Had some help from friends. Trying to detect people potentially attempting to exploit CVE-2018-11776. CC anyone that might care.
4
43
72
WHO IS LOOKING FOR A NEW JOB IN
#INFOSEC
?!?! Hit me up!
Please have previous SOC experience and be ready to roll. This is a Sr position.
8
48
53
"On December 12, 2023, HPE was notified that a suspected nation-state actor, believed to be the threat actor Midnight Blizzard, the state-sponsored actor also known as Cozy Bear, had gained unauthorized access to HPE’s cloud-based email environment."
Cybersecurity disclosure (1.05) found via SECurityTr8Ker for Hewlett Packard Enterprise Co (CIK: 0001645590)
Cc
@cocaman
4
3
29
0
19
56
“Login IDs and passwords of Tokyo Olympic ticket purchasers have been leaked on the internet”
To clear this up, looks like a bunch of people were generally infected with
#redline
and other stealers that supply “dark web markets” thus exposing their creds
The valid account information (ID/Password) of Tokyo 2020 volunteers and ticket buyers are also leaked, and it seems necessary to verify that this information includes personal information of domestic players and officials.
@Tokyo2020
@darktracer_int
#TokyoOlympics
0
15
37
2
41
53
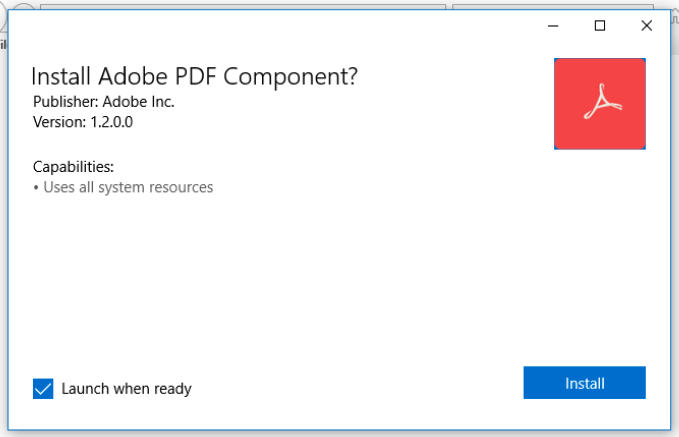
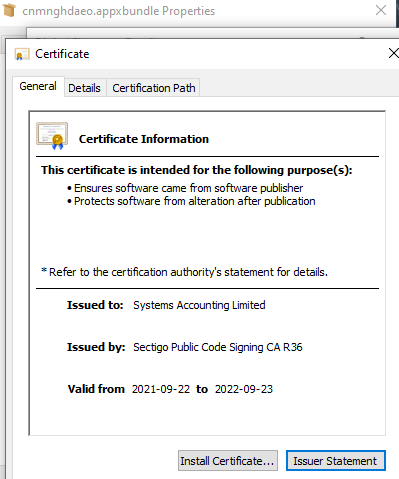
Bazarloader 🤝 Emotet
2021-11-04: Bazarloader starts using AppxBundle (ms-appinstaller) as an attack vector.
2021-11-26: Emotet starts using the AppxBundle (ms-appinstaller) as an attack vector.
More info:
Cc
@1ZRR4H
BREAKING:
#Emotet
malspam links can since yesterday link to an Universal App installer hosted on
@azure
imposing as an Adobe Update that drops E4 payload. This is the same initial attack vector as
#BazarLoader
used a few weeks ago, even using the same
@SectigoHQ
cert.
5
123
216
2
18
45
I made a Python version
6
3
43
Looks like “naned” was responsible for the creation of ‘TrickBoot’ - Trickbot’s UEFI module (permaDLL).
Ref.
Account (nicknames): naned
---
---
#trickbotleaks
#trickbot
#ransom
#ransomware
#malware
#conti
#trickleaks
@briankrebs
@VK_Intel
@MalwareTechBlog
@trickbotleaks
@pancak3lullz
@BleepinComputer
@ForbesTech
1
24
42
2
17
43
BlackCat/ALPHV crew made some adjustments to their ransomware. Previous methods for extracting the config aren’t working anymore. Introducing BlackCat/ALPHV 2.0??
SHA1: 8c70191b12f14eed594388c8fbe05efe6ebaa564
Cc
@vxunderground
@f0wlsec
Blackcat ransomware group (alternately refered to as ALPHV) has changed some of their binary characteristics. Previous methods of extracting binary configurations fails, some YARA rules no longer match
Example from
@hatching_io
:
tl;dr Maybe Blackcat 2.0?
1
15
57
0
11
41
Looks like a few additions need to be made to this entry. Thanks for the great read
@briankrebs
2
9
39
This is NightSky/Rook/AtomSilo/LockFile ransomware group
Cobalt Strike Server Found
C2: HTTPS @ 149[.]28[.]143[.]29:443
C2 Server: service[.]trendmrcio[.]com,/owa/63ll45DCfiTEg8lm7o3M
Country: Singapore
ASN: AS-CHOOPA
Host Header: www[.]google[.]com
#C2
#cobaltstrike
1
13
24
1
8
38
In our tracking of the
#LockBit
drama saga,
@Bl4ckSky28
and I have discovered EquiLend and Ernest Health are two prime examples of LockBit scrambling to appear like they are still a properly functioning RaaS.
1
10
38
Emotet EPOCH5 currently targeting Europe automotive industry.
maldoc hashes, download URLs, and C2 addresses here:
Cc
@DragosInc
@th3_protoCOL
@Cryptolaemus1
2
26
36
Be cautious in linking things here. "Scattered Spider" describes tactics, not a group. Also, being in Star Fraud chat doesn't necessarily mean they are part of the crew who used ALPHV.
3
3
34
#Egregor
claiming 25 companies are in their queue for analysis to determine ransom amounts 👀
0
15
33
Lmaooo...and just like that LockBit removes EquiLend and Ernest Health
In our tracking of the
#LockBit
drama saga,
@Bl4ckSky28
and I have discovered EquiLend and Ernest Health are two prime examples of LockBit scrambling to appear like they are still a properly functioning RaaS.
1
10
38
2
3
30
These are Hive payloads from early-mid September and a ‘how-to deploy’ text file.
1
5
27
Seems like TA551 may be collaborating with FIN12.
#TA551
>
#IcedID
>
#Nokoyawa
who is the only one with overlap between IcedID and Nokoyawa?
#FIN12
Proofpoint observed the HTML attachment campaign described in this report on October 31, 2022. Together with 10+ other HTML Smuggling campaigns leading to IcedID from September to November, we attribute to TA551.
Great work on detailing follow-on activity by
@TheDFIRReport
!
1
16
52
1
5
28