Ahsan Khan
@hunter0x7
Followers
33,045
Following
1,337
Media
115
Statuses
907
[Hacker + lover of bash] I Don't know how to hack but i know how to pwnd!
Joined January 2019
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
FEMA
• 456407 Tweets
Mutombo
• 207618 Tweets
Mets
• 159202 Tweets
Verizon
• 115449 Tweets
Braves
• 92955 Tweets
Kemp
• 81758 Tweets
Pete Rose
• 71106 Tweets
#grandefratello
• 44943 Tweets
Lindor
• 31846 Tweets
Hall of Fame
• 28486 Tweets
Titans
• 27131 Tweets
#الاجتياح_البري
• 27061 Tweets
Dolphins
• 23657 Tweets
Seahawks
• 17093 Tweets
あと3ヶ月
• 16919 Tweets
コーヒーの日
• 15221 Tweets
Happy New Month
• 14681 Tweets
WELCOME HOME BAMBAM
• 14223 Tweets
都民の日
• 12712 Tweets
Hit King
• 12653 Tweets
#SnowManライブグッズ
• 12032 Tweets
愛知1区
• 11240 Tweets
残り3ヶ月
• 11069 Tweets
河村たかし名古屋市長
• 10466 Tweets
Last Seen Profiles
Pinned Tweet
My spotlight with bugcrowd 🤗🤗
While he hits some pretty big bounties, you might be surprised how
@hunter0x7
got started in bug hunting.
Join us for this researcher spotlight and down to earth chat with Ahsan Khan!
#ItTakesACrowd
25
35
299
31
23
495
~Pwn
1. Create an account email
@burp_collab
*
2. Forgot password
3. Received requests from internal server + SMTP connection details
4. Got Internal headers + origin IP
5. = (403)
6. = (Headers + Origin IP = pwn)
Pwning isn't easy~
26
419
1K
~Pwn
Will be speaking at
@InfoSecComm
tomorrow so who’s waiting ♥️
Talk: Accessing Admin Panels
22
10
201
@remonsec
I see on ma left side there is no one to help and the right side which is full of failure and ma front a screen which is called future so buddy make yourself that much busy in the work so you dont have much time to think about to look on the left or right ♥️ good luck
5
28
190
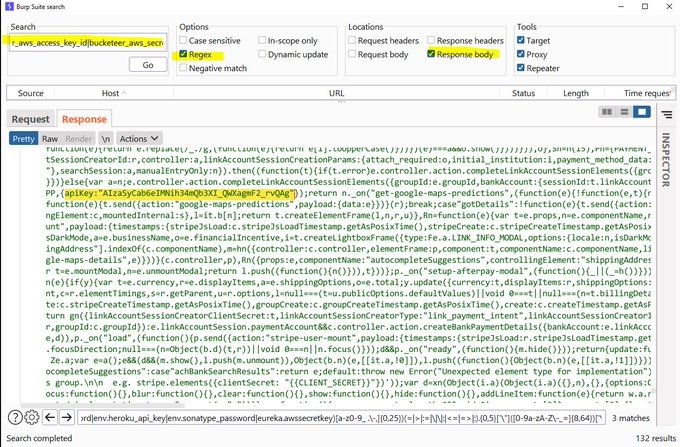
Update no 3: Reported 15 submissions (total).
Critical one:
Used Js Miner & for finding sen* info in JS files.
Found a JS file disclosing access token without any endpoint.
(1/3)
5
42
178