SpiderLabs
@SpiderLabs
Followers
27K
Following
183
Statuses
6K
The elite security team at @Trustwave. Response & Investigations. Analysis & Testing. Research & Development. Follow for info on the latest #infosec threats.
Everywhere
Joined January 2009
RT @Trustwave: Ransomware gangs aren’t just evolving, they’re ...recycling...? ♻️💰 @SpiderLabs' latest research reveals how #LockBit, #Qil…
0
2
0
#FacebookMessenger chatbota: friend or foe? 🎭 Our team has uncovered a #phishing scam where attackers mimic #Meta’s live support, tricking victims into giving up credentials through targeted, bogus security alerts that bypass typical #phishing detection. 🎣 Don't fall victim to these fake (yet convincing) tactics. Here's what you need to know:
0
2
2
💻🚨 #MalwareAlert: Attackers are distributing a PDF disguised as a “complaint.” The link directs users to a suspicious site featuring a fake CAPTCHA in a #pastejacking attack, tricking Windows users into pasting malicious commands. Final payload? #LummaStealer. #IoCs: karagulismerkezi[.]com booking[.]important-confiirm[.]com C2: futurisfticconcepts[.]top Lumma cb4338cf14eb6aca9f3deabd3af20ad3 a9c963f508783e2d5fdf8c96b6e98970a25dca2a #Malware #MailMarshal #CyberSecurity
0
3
8
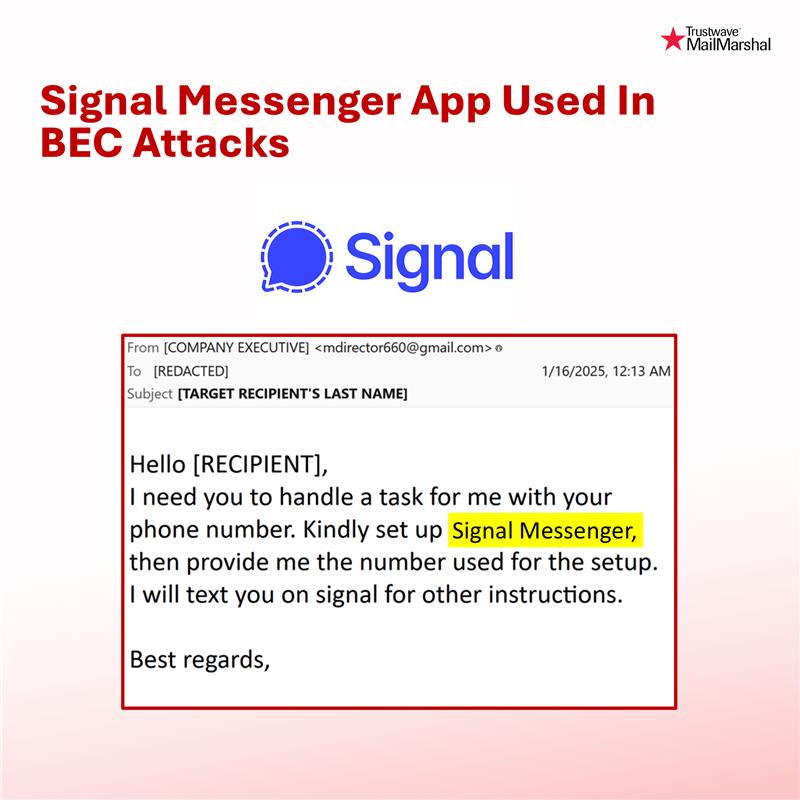
📩🚨 #BECAlert: Fraudsters are now utilizing Signal Messenger app in dual-channel BEC scams, in addition to direct SMS/call and WhatsApp. The email, sent by the impersonated company executive instructs the recipient to sign up on the app. Fraudsters will then take the conversation mobile where there is less security and detection. #MailMarshal #Signal #BEC #WhatsApp
0
1
3
🚨 Alert: A malicious spam campaign targeting private sectors in UAE has been discovered, deploying the DarkVision RAT. The RAT injects into Msbuild.exe process and connects to C2 at acuweld[.] Stay vigilant! IoCs: C2: acuweld[.](85[.]31.47.116) at port 3440 http://87[.]120.113.91/Jycbxzgdptf.mp3 MD5: 6120fd70c3f1b9e4bfd6c16087e8c0ce SHA256: 0b7130c39a0a84cd2ebbc95fea5bee6639bdcb5f003e94b745f9d98ef19007a3 #CyberSecurity #PhishingAlert
0
0
2
APT34 (OilRig) isn't just another #cyberthreat, it's a persistent force refining its tactics in the shadows. 👥💻 Allow us to recap findings from our recent research on #OilRig's operations: 🔹 Evolving tactics: Leveraging DNS tunneling, stolen credentials, and new malware strains. 🔹 Global reach: From government targets to critical industries, no sector is off-limits. 🔹 Adaptive tradecraft: Continuous refinement to bypass modern defenses. Understanding their playbook is key to staying ahead. Check out our dissection of #APT34:
0
0
4
Phishing Alert 🎣⚠️ A #phishing campaign uses a self-contained HTML form mimicking a login page to steal credentials (username/password), IP address, geolocation, and other details, exfiltrating the data to a Telegram bot. IOCs: * Bot Token: 7635668190:AAGCE0kOWSc6lH1EEmSez9bVrartnfDkQ5E * Chat ID: 7145425544 * API Endpoint: token>/sendMessage
0
0
6
@Oracle may be the 'king of databases,' but ODAT (Oracle Database Attack Tool) proves even royalty has vulnerabilities. Here's why #ODAT stands out: 🔓 Exploits misconfigurations and weak auth gaps 💾 Uses TNS poisoning, brute force, and SQL injection ⚔️ Highlights the risks of poorly secured #Oracle environments Explore how ODAT challenges security, what it means for your defenders, and why #SpiderLabs is keeping it on our radar:
0
0
1
#Ransomware in 2024 was smarter, faster, and deadlier than years prior, with gangs like #BlackCat and #LockBit evolving their precision targeting, double extortion, and cross-platform attacks. 😈💻 🕷️ #SpiderLabs unpacks the top players and cutting-edge tactics of 2024 to help you anticipate what's to come in the threat landscape of 2025:
0
1
2
Xbash: the Swiss Army knife of #malware. ☠️ Part #ransomware, part #cryptojacker, part #database destroyer. Xbash exploits weak passwords, wipes #data, mines #crypto, and targets Linux and Windows. Our researchers did a deep dive to share Xbash tactics and a full simulation of its wrath:
0
0
3
🚨 Zero-day vulnerability, CVE-2024-55591, has been uncovered in #Fortinet FortiOS and FortiProxy, threatening critical infrastructure and global enterprises. While Trustwave is not vulnerable, we are monitoring the issue to share technical details, IOCs, and urgent mitigation steps:
0
0
2
📢 #Magecart continues to dominate the e-commerce threat landscape. #SpiderLabs has dissected their evolving skimming techniques, key targets, and the persistent risks they pose to online retailers in a deep dive to expose how this notorious group is adapting to stay ahead of defenses:
0
1
2
🪝🚨 #PhishingAlert: #Phishing messages impersonating Human Resource (HR) representatives are on the rise again this holiday season! Here are the quick details: 🪝 Lures include holiday bonuses, leave applications, year-end reviews, and compliance agreements 🪝 Utilize phishing links, malicious attachments, and QR Codes (#quishing) 🪝 Target companies of all sizes and across all regions
0
2
2
🚨 Prompt Injection: LLM's Critical Attack Surface Unvalidated external data sources are the new zero-day vulnerability in AI systems. As LLMs consume inputs from multiple contexts, each interaction becomes a potential attack vector—rendering traditional security perimeters obsolete. Least privilege isn't just an architecture principle; it's survival protocol for the AI era. #AI #LLM #ZeroDay #Cybersecurity #CyberBreach #CyberAttack
0
1
1
🚨 New delivery technique spotted! Threat actors abusing Atera RMM now use fake payment emails to lure victims. Leveraging HTML smuggling, they drop the same MSI installer for Atera directly on the target device. #MailMarshal #CyberSecurity #ThreatIntel
#Cybercriminals are actively abusing the legitimate Atera RMM tool in a spam campaign targeting Spanish-speaking users. Fraudulent emails, spoofing the Ministry of Mobility and Transportation of Mexico City, falsely claim a traffic speeding violation and offer a 50% discount for early payment. Attached is a ZIP file containing an MSI installer. When clicked, it deploys the Atera Agent, granting threat actors remote access to the victim's system. #IoCs: Infraccion=Multa.msi ca95e99d14a8ddfdf12406dd3d884888 c3f805710d62fd6f1f1258a4c6c64ca0a5f69b3c650f3714a02cc691b7ffba30 Atera Integrator Login: ibarra3168@gmail[.]com Atera Account ID: 001Q300000ODucuIAD
0
1
2
🚨 Beware of fake SSA notifications! These lead to fraudulent portals that auto-download of #ConnectWise #ScreenConnect, which attackers abuse to take control of your device. Stay vigilant!🛡️ IoCs: hxxps://statement-certification[.]com/view?token hxxps://statement-certification[.]com/View/re hxxps://bitbucket[.]org/megan12/thankyou/downloads/ CnC: lucaria[.]site:49152 191[.]96[.]207[.]97:49152 Hashes: 9d636e359422652a86bd5ace9e39988318e7b9cf fe6e7c43205076528ecf6a4f24b07fcf07a64c5e f50f5be15273db9b229b3d80b3c20c13669c77b7 #CyberSecurity #Malware #IOC #StaySafeOnline #OnlineSafety #MailMarshal
0
2
0
🚨🪝 #PhishingAlert: #Microsoft O365 users are targeted by #phishing campaigns exploiting ‘userinfo’ URL component to evade detections. Within the 'userinfo' component, the attackers inserted over 1,000 characters of whitespace after the domain string, tricking URL parsers and evading security filters. When the URL is processed by the browser, the 'userinfo' component is ignored, and the phishing domain is loaded instead. IOCs: hxxps[://]farmboyclothing[.]com/ hxxps[://]login[.]microsft[.]hillgarden[.]com[.]tr/ #Cybersecurity #OnlineSafety #MailMarshal #IOC #Phish
0
6
9
🚨 Beware of #phishing mails targeting #Facebook users! Cybercriminals are impersonating the Facebook Ads Manager page with a fake support chatbox. They ask for screenshots, passwords, and even your #2FA setup key & QR. Stay alert! IoCs: hxxps://platform-drive-4163[.]my[.]salesforce-sites[.]com/mera hxxps://account[.]metasystemaccount[.]com/ hxxps://account[.]metasystemaccount[.]com/messages[.]php hxxps://account[.]metasystemaccount[.]com/admin_info[.]php POST: hxxps://account[.]metasystemaccount[.]com/check_user_page[.]php POST: hxxps://account[.]metasystemaccount[.]com/telegram_api[.]php #CyberSecurity #OnlineSafety #MailMarshal #IOC
1
5
6
#Cybercriminals are actively abusing the legitimate Atera RMM tool in a spam campaign targeting Spanish-speaking users. Fraudulent emails, spoofing the Ministry of Mobility and Transportation of Mexico City, falsely claim a traffic speeding violation and offer a 50% discount for early payment. Attached is a ZIP file containing an MSI installer. When clicked, it deploys the Atera Agent, granting threat actors remote access to the victim's system. #IoCs: Infraccion=Multa.msi ca95e99d14a8ddfdf12406dd3d884888 c3f805710d62fd6f1f1258a4c6c64ca0a5f69b3c650f3714a02cc691b7ffba30 Atera Integrator Login: ibarra3168@gmail[.]com Atera Account ID: 001Q300000ODucuIAD
0
3
4