Shlomie Liberow
@Shlibness
Followers
3K
Following
851
Statuses
1K
Head of Hacker R&D @Hacker0x01. Lover of 4AM shell battles. All things hacking!
London
Joined June 2009
Visit --> SSO Visit gt; login Reviews Javascript --> if (data == 'SUCCESS') { location.href = "/admin/<snipped>?uname="+username+""; } Visit: lt;snipped>?uname=admin Admin Access... #bugbountytips
2
85
259
RT @0xLupin: We just released a new article on how we made 50,000$ in #BugBounty by doing a really cool Software Supply Chain Attack🔥 🔗Lin…
0
100
0
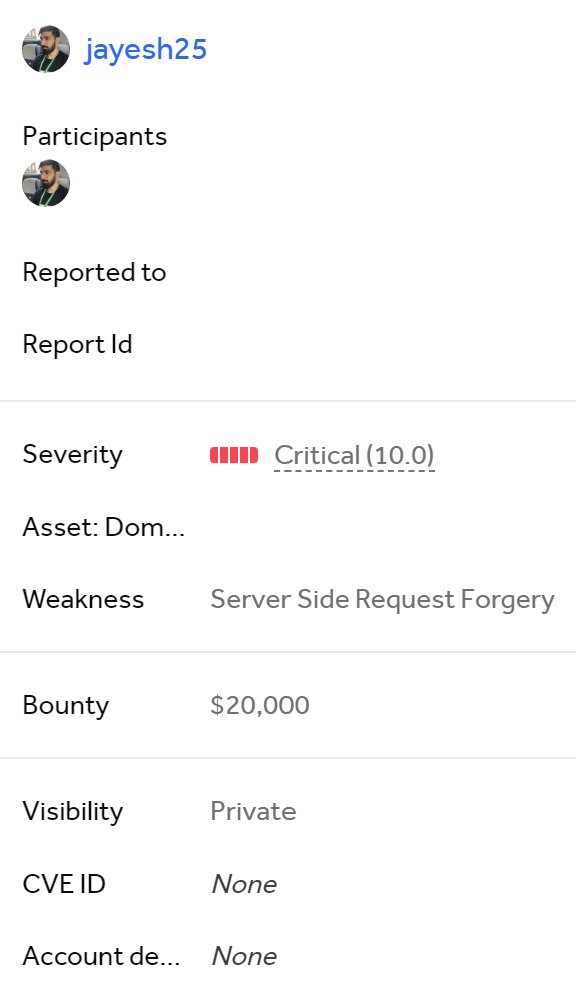
Always a joy collaborating with @Jayesh25_ and digging in deep
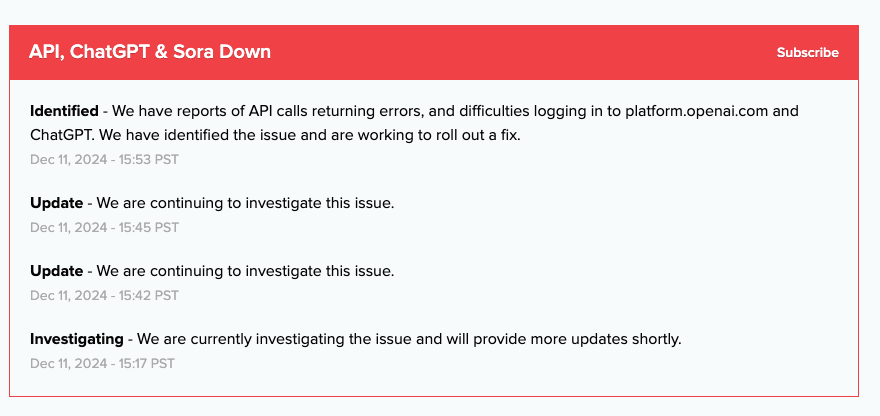
🚨 Yay, we were rewarded with $20,000 on our @Hacker0x01 submission for a SSRF bug discovered in collaboration with @Shlibness! 💰🎉 🥳 We uncovered a Critical SSRF vulnerability, turning it into unauthorized access to internal admin endpoints, leading to PII leaks and administrative access! Here’s how we escalated a simple SSRF to a $20,000 bounty. 💰🛡️ 🔍 Step-by-Step Breakdown: 1️⃣During our testing, we found an endpoint accepting an "url" parameter. 2️⃣To confirm it was vulnerable to SSRF, we passed a Burp Collaborator URL and received an HTTP pingback, indicating a potential SSRF issue. ✅ 3️⃣We then attempted to escalate this Issue by accessing localhost and AWS metadata. 4️⃣It turned out the endpoint was part of an AWS Lambda function. By hitting http://localhost:9001/2018-06-01/runtime/invocation/next, we retrieved Lambda function details. 💡 5️⃣At this point, there were no sensitive credentials or Information leaked. But since the SSRF allowed partial read, we wondered: "What if we could access internal services whitelisted for this Lambda?" 🤔 6️⃣Next, we identified two categories of targets across all subdomains: Externally resolving but not directly accessible via HTTP Internally resolving and obviously not accessible via the Internet🌐 7️⃣We used Shub's @infosec_au Surf tool ( for discovering potential Internal targets and found 5000+ viable subdomains that were inaccessible from the internet. 🎯 8️⃣Chaining the SSRF further, we searched for Swagger endpoints on all these targets Identified by the surf tool, we ended up looking for endpoints like: http:///swagger-ui/swagger.json
http:///api/v1/api-docs
http:///api/v2/api-docs etc We discovered that the Lambda function had whitelisted access to internal hosts exposing Swagger API documentation. 🚀 9️⃣The Swagger docs revealed administrative endpoints. Chaining the SSRF again, we accessed these Internal API endpoints, leading to PII leaks and unauthorized access to other internal administrative functionalities. 🔓 ⚠️ Impact: This vulnerability allowed attackers to access internal administrative endpoints, leaking PII and exposing other critical business risks. 🚨 💡Lesson Learned: Don’t stop at confirming SSRF! Always think outside the box and explore ways to escalate for maximum impact. Creativity wins the game! 🧠✨ #BugBounty #HackerOne #BugCrowd #YesWehack #Intigriti #bugbountytips #security Y
4
1
210
@hakluke I've not had it work autonomously all the way not least because it's not truly necessary to use AI for parts of the flow that are fairly structured but I did have luck with AI finding a specific endpoint I needed based on historical context I fed in that led to a recent critical.
0
0
0
@shaoruu @cursor_ai It has a tendency to randomly delete comments left in code even when I specify not to do this via 'rules for AI'
0
0
0
RT @RachelMoiselle: Here is one of the pogromists. He explicitly says he is going on a Jew hunt and curses the Jews. Jews. Not ‘Maccabi…
0
599
0
A must watch by @Blaklis_ covering some funky bug bounty exploits with all the juicy details.
0
43
179