Jake | JCyberSec_
@JCyberSec_
Followers
9K
Following
25K
Media
3K
Statuses
9K
Expert in Credential Phishing and Phishing Kit Research. Working in Cyber Security - Threat Intelligence #Phishing
UK
Joined August 2017
I got phished. Not a training phish a REAL #phishing site⚠️. I am a security expert but I still fell for it🫡. ⛔️You shouldn't blame users everyone can get tricked. Here is what happened. 🧵⤵️.
73
257
1K
Threat Actors using the global CrowdStrike outage to spin up new domains 🌐. 👁️Keep an eye out for malware posing to 'fix' the issue.🔒Malicious phishing pages posing as a fixing site. #Phishing
19
310
491
:: Phishing Hunting Thread ::. This is a thread about how to hunt and find #Phishing sites. Retweets would be great to help spread the knowledge and please add your own techniques, ideas and suggestions. Let's go hunting!
8
220
372
🔥Threat actor sending Hermes #phishing via SMS is arrested!🚓. 🔍Note the actor was using a Hotel room to hide their geo-location . These actors are clever to hide their tracks, keep this in mind when dealing with them.
7
73
212
So you want to learn about phishing kits 🧑🎓. 🧵 In this thread I will highlight threat hunting skills and IoCs within phishing kits to look for ⤵️. Retweets are appreciated ♻️. 🔍Follow me for more #phishing intelligence @Jcybersec_
4
102
214
Announcing KIT Intel 📣. 🎉A Phishing Kit Intelligence Platform. “Understand the threat actors' playbook and capabilities”. #KITIntel. 🧵 THREAD ⤵️
7
59
189
How to create a good #phishing site:. ✅ - Use a legitimate host.✅ - Use the latest theme of the target.✅ - Ensure it has a TLS.✅ - Host the exfil address on a legitimate service. 🌐/pianohub-170fd.dt.r.appspot.com/.POST to 🌐 /sonarquberb.azurewebsites.net/1/handler.php
5
53
183
I have just found a phishing kit with an API key in. The API key has only 1000 free searches. It would be awful if someone did 1000 searches with that key in a loop. #phishing
4
31
145
⚠️So you have heard about the Twilio breach?. SMS #phishing messages were sent to Twilio staff resulting in multiple employees accounts being compromised 📱. 🥷Threat actors then accessed 163 customers resulting in further compromise. Here is a timeline of events. Thread🧵⤵️
3
58
130
Never seen a fake @haveibeenpwned #phishing website before 🤯. 🌐hxxps://have-i-been-pwned.com/uhive970477wyksm/account.💢@Namecheap . #KITIntel🔍 I would assume the passwords as being exfiltrated but currently the POST gets a 400 status code . 🔠For awareness @troyhunt
5
43
102
I have been able to capture #Flubots deployment code⚠️. 🔍This code is used on websites when a victim attempts to download the malicious APK. Here is what I found ⤵️. 1/n
5
37
102
New CTI chart 🔥. Cyber threat hunting maturity ranking system. 🖥️Where does your organisation sit on this?. #CTI #ThreatHunting #ThreatIntel
Saw these in my feed and wanted to share. Interesting #CTI escalation pyramid and a #DRIF pyramid chain. Gotta love colourful images, especially if they help process and procedure understanding.
1
35
96
:: Phishing Admin Panel Hunting Thread ::. In this thread we will find ways to hunt and attribute phishing admin panels. This is a continuation from my #phishing hunting thread released earlier this year. (. Please retweet to knowledge share among others.
:: Phishing Hunting Thread ::. This is a thread about how to hunt and find #Phishing sites. Retweets would be great to help spread the knowledge and please add your own techniques, ideas and suggestions. Let's go hunting!
2
45
76
With all the noise about Browser In The Browser (BITB) #phishing templates🖥️. 🔍I made a YARA rule to detect a deployed template based upon the code provided by @mrd0x 💀. Made by :: @JCyberSec_🥷.Download here ::
2
30
74
🎉 We have just passed 50,000 unique phishing kits in our repository. 🔍All these kits are parsed, processed, and searchable. It is really interesting to see how many kits are duplicated across domains and campaigns. This shows that #phishing is getting disrupted well enough💀.
6
14
72
Just written a new script to enhance data in @urlscanio. I now upload new found malware panels with tags for the type for ease of use. I hope people find this valuable and if you're hunting panels you can utilise these submissions. Next step is to automate the script running!
4
9
63
#Emotet Summer holidays over - Emotet is back online. 📊. What Do We Know So Far?. Since Friday morning, the servers of cybercrime gang MUMMY SPIDER (aka. TA542) are active again. 🔊. Thread - Retweet to help share knowledge! ♻️
2
46
60
Never fire or punish anyone for falling for a #phishing site. Education - Sure. Punishment - No. The user didn't fail; your internal security controls failed. If an employee falls for a phish then you have failed to block, detect, and secure your user-base.
1
16
56
To tell what botnet an #Emotet sample is from, extract the payload and then analyze the RSA Key. Visualizing relationships between RSA keys and C&C servers can be seen in the image. 1/3
1
22
60
@LeveragedHonky It wasn't a cold message I was selling an item. I didn't see that the link was to an external site I clicked it quickly assuming it was the finalise the transaction page. The red flags are obvious. This was a low level unsophisticated phish. But distracted and on autopilot. .
3
0
55
⚠️ New Slack channel :: Magecart Intel Sharing ⚠️. If you're engaged in hunting or protecting against #Magecart then come join. Split into with different TLP areas to enable effective intel sharing and allowing for collaborative working amount peers. 📬 DM me for an invite now.
5
18
57
🔥We have just discovered an E-Commerce entrepreneur who is selling #phishing kits and bullet proof hosting on the side. 🌐hxxps://sellix.io/o365spammer . 🧵THREAD ⤵️
4
18
48
🔥So where are we with SolarWinds Orion and what have we learnt since the original disclosure. 🔎. 📄A thread to pull public information together. 1/n. 💥#SolarWinds #SolarWindsOrion
1
28
50
Friday read 📖. How To Unpack Malware - . A fantastic and deep analysis of packers written by @Marco_Ramilli 👍. 🔎Covering: UNPACME (@unpacme), DiE, process and DLL injection, Process Hollowing, APC, Process Doppelgänging, and debuggers. #Malware #CTI.
1
22
49
📢Using intel which my team generated Officers from Londons Police @DCPCU_tweets executed four search warrants across England relating to #phishing SMS campaigns linked to Hi Mum/Dad #Familyscams 🔍🚓. 👀Gotta love when a plan comes together🚨.
2
5
44
I have discovered a GitHub user pushing crypto #phishing 🔥. 🕴️The user has phishing pages for:.CoinBase.TrustWallet.MetaMask.SafeMoon.MetaWallet. ✉️All stolen data is sent via (@formsubmitio). 🧵IoCs below ⤵️
2
14
42
I can already see how this is going to be abused by threat actors. Going to make tracking these threats 100x harder. Who is pastebin working for? Security or threat actors?.
We’re excited to announce 2 great new features for #Pastebin, we think you’ll enjoy using them! In the interest of #security, the first is: Burn After Read, and the second is: Password Protected Pastes. Head on over to to check them out 🕵️
4
10
44
Let's do a detailed #FF because Friday and knowledge sharing is good!. Format - Username :: Reason to follow them. Note: These are in no alphabetical order. Feel free to append your own list!. #THREAD #FollowFriday
1
10
42
Easy #Phishing win for a Monday morning:.- /dns04.com.- /dns05.com. 900 hits on @urlscanio of which 289 are phishing. Targets include: WhatsApp, Apple, Bank of America, Amazon. Regex: "domain:dns[0-9]{2}.com". #cyber @nullcookies @packet_Wire @dave_daves @Spam404 @n0p1shing
0
13
39
InterPol👮♂️ announced the arrest of 3 individuals linked to #16Shop; the prolific Phishing-as-a-Service service📁. 📅16Shop has been around for years, with public attribution available since 2018!👀. It is great arrests are being made but is this too little too late?🤔. 🧵⤵️
1
10
40
I found a strange website today. 🖥️It led me to discover a huge #phishing infrastructure setup . Everything was hiding behind this seemingly innocent website. Read on to understand what happened ⤵️
4
9
36
This is big. ⚠️. Multiple crypto accounts all hijacked almost simultaneously. Using COVID theme. 🌐Scan of the site: 💰Bitcoin wallet: Cloudflare detects the site as malicious. #cryptoforhealth #Crypto 💲
5
22
36
I never thought I would see the day when @Namecheap were getting more likes than my tweet . Good work folks! 👍
2
0
37
Whilst looking into another thing I stumbled across another #MageCart campaign. URL🌐 hxxps://jquerycdnlib.at/5c21f3dbf01e0.js - 217.8.117.42.Filename: 5c21f3dbf01e0.js. The code grabs card details and then sends back to itself to store on the domain. @iblametom @malwrhunterteam
1
16
36
For the latest SOTI report (Phishing for Finance), .@SteveD3 and I looked at Kr3pto and Ex-Robotos phishing kits. We were able to work together with our unique datasets to discover exclusive insights into SMS Credential phishing. Check it out:
0
17
35
A little Christmas gift to all you #phishing threat hunters out there . 🎄. 📂A thread of phishing kits. 1/n⤵️
1
12
33
And here are some great #Phishing feed resources to use to hunt ::.- @PhishStats - - @open_phish - - @PhishTank_Bot - - @urlscanio -
1
10
34
I am seeing an increase in the use of upside down letters used in phishing attacks ⚠️. #KITIntel🔍 All these URLs are linked to Creds bros #phishingkits. 🟢This TTP is used to bypass static URL scanning and is not new
1
14
32
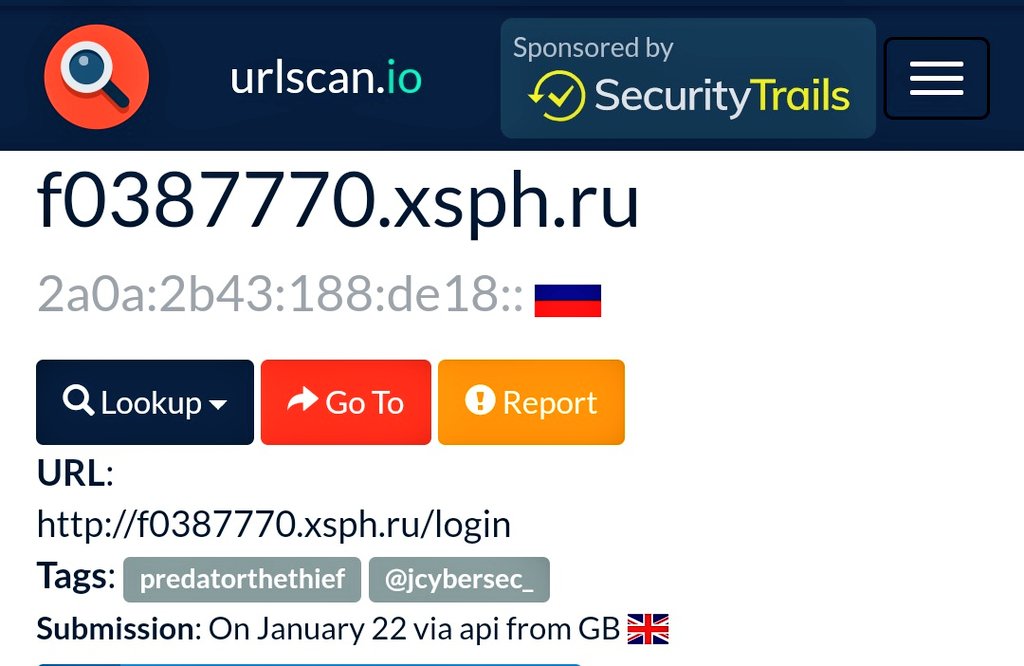
Check out this cesspool of filth⚠️. 44 new #PredatorTheThief💳 URLs have appeared within the last two weeks. @urlscanio has 268 domains archived. IPs rotate but all sit on AS35278 belonging to @sprinthost. #Malware @JAMESWT_MHT.@James_inthe_box.@malwrhunterteam @MaelSecurity
3
13
34
As stated at the start of this thread here are some great #Phishing accounts to follow ::.- @JCyberSec_ .- @IpNigh .- @PhishingAi .- @packet_Wire .- @ActorExpose .- @PhishStats .- @FeedPhish .- @JayTHL .- @Cyberfishio .- @dave_daves .- @ozuma5119 .- @smica83
2
10
32
Highly suspicious newly registered domain on Cloudflare ⚠️. 🌐 - /LETENCRYPTS.ORG.📅 - Dec 30, 2020 . Paging: @letsencrypt.
0
6
32
⚠️I am seeing a new trend of WhatsApp based SMS #phishing📱. 🔍These lead a user to directly transfer money pretending to be a persons son/daughter. Phishing can use any vector to contact you. Stay alert!
7
20
34
So @Namecheap (@lothar97 @NamecheapCEO) released a report titled "Our fight against fraud and abuse" 📄. Here are the key takeaways and something ALL web hosting companies should read and understand ⤵️
2
13
33
Modified Facebook #phishing page🎣. 🌐/protectionsoffice404.000webhostapp.com. 📃Pages:./m.help.htm./m.upgrade.pay.htm./confirmed.htm. ⚠️Rare kit always hosted on 000 based on historic deployments. Hosted by @000webhost_com - Take this down.
4
21
29
Saturday #MalwarePanelUpdate 📊. Lots of new panels from a range of #malware including: #AZORult, #kpot, #Lokibot, #BlackNET, #Tesla, and #OskiStealer. 🖥️Full IoC list: They have all been pushed to @urlscanio with my tag if you want to view them. 🌐
1
15
30
#MageCart script located in the wild on several eCommerce sites.⚠️. 🌐Script is loaded from hxxps://adventurewar.com/payment/mage_secure/payment.js - 103.134.152.1.TLS @letsencrypt
2
10
29
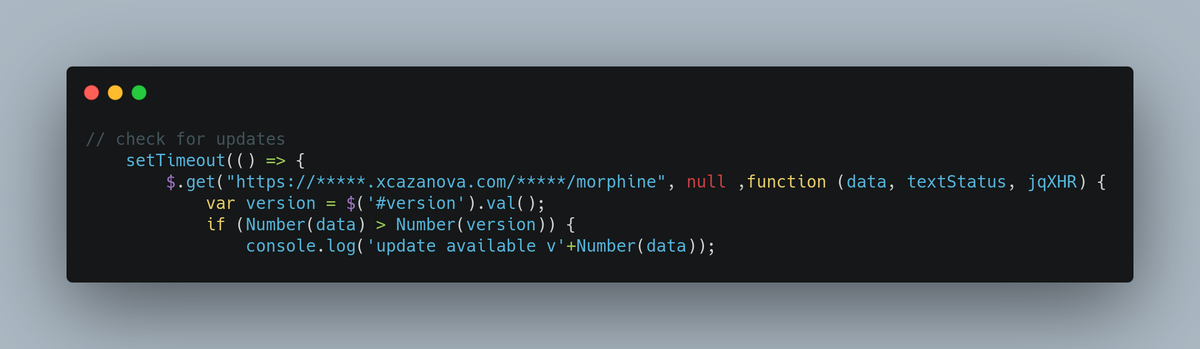
#Phishing Actor Cazanova continues to try and distance himself from his phishing kits. Asserting his website is down; HOWEVER, the version tracker portal is still online hosted on his site. His site is NOT down or offline. #CyberSecurity #Phishing .@BleepinComputer @urlscanio
7
9
27
This is still a very relevant image for all CTI analysts to understand and link to current reporting. Direct link between #Emotet, #TrickBot, and #IcedID. Also links between #WizardSpider as creators / closely linked to #GrimSpider #Ryuk. Image Source:
1
5
29
I have created an open team on @KeybaseIO for Phishing hunting. 🎣. ⚠️If you want to join search for "Phishing" and request to join. I am hoping we can share IoCs and other #Phishing and #PhishingKit intel.🌐. Please RT♻️ to share this to more people.
2
23
30
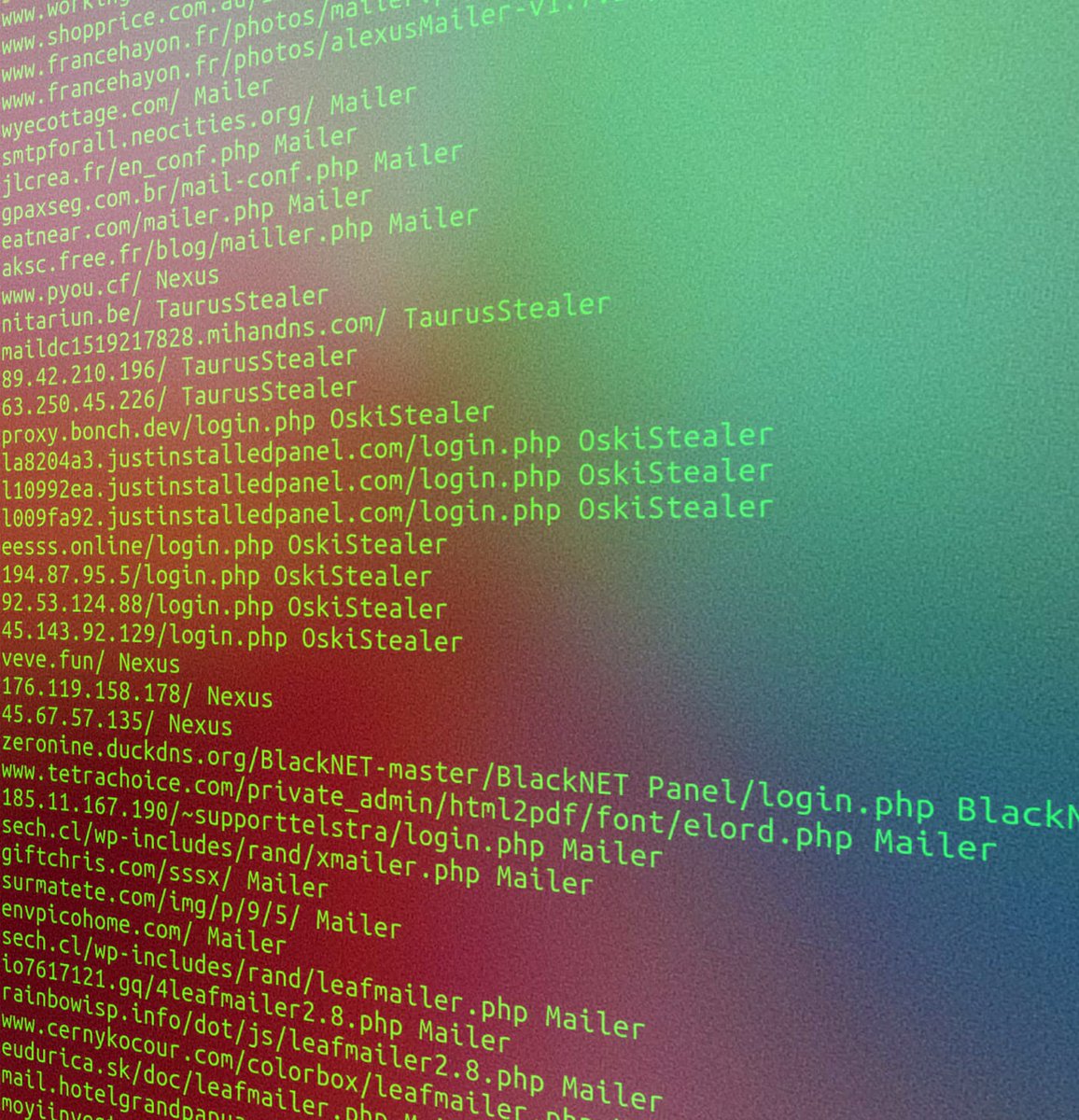
It's been a while, but here is today's #Malware panel updates which include: 📊. 23 new #Mailers 📧.8 new #OskiStealer 🪝.4 new #Nexus 💵 and #TaurusStealer 💲. Brand new C2 panels on @urlscanio uploaded with my tag ⚠️. IOC List: #MalwarePanelUpdate
1
7
26
I have just seen a new #phishing kit targeting the UK's NHS 🇬🇧🧑⚕️. 🌐hxxps://nhsdigitalpassports.uk/Alert.php. ⚠️Intel: The "Alert.php" filename has also been seen in Post Office phishing websites showing these kits are highly likely to be linked. @UK_Daniel_Card @LisaForteUK
🚨We are seeing a worrying trend of new #COVID vaccination #Phishing campaigns targeting the UK 📊. 💰The Phishing site requests personal details and payment details after stating a payment of £4.99 is required for a 'Covid pass'
2
26
28
If you are going to host #phishing on @gitlab then you would do wise to not use a photo of yourself as your profile picture. What else can we find out about this individual. ?. 1/n
#phishing Alert @BankofAmerica @BofA_Help. hxxps://daviking95.gitlab.io/boa/account.html. @malwrhunterteam @PhishStats @urlscanio.@Bank_Security @gandibar
2
8
26