Atredis Partners
@Atredis
Followers
3K
Following
275
Statuses
591
Atredis is a team of world-renowned security researchers and consultants. We do risk-centric, research-driven security testing and consulting.
All over North America
Joined August 2013
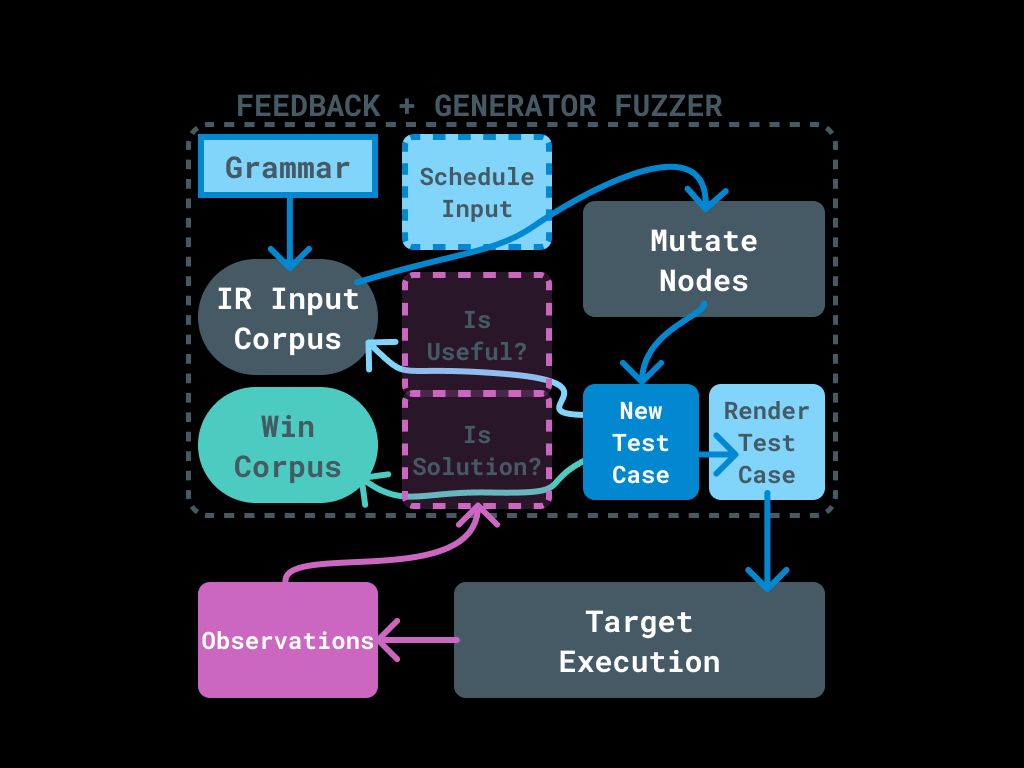
ICYMI: Jordan (@jordan9001) put together an awesome tutorial on getting started with LibAFL on our blog! Also, be sure to check out his symbolic execution training at RingZer0 (virtual) the week of February 10:
0
4
6
Jordan (@jordan9001) put together an awesome tutorial on getting started with LibAFL on our blog! Also, be sure to check out his symbolic execution training at RingZer0 in Austin (and virtually) the week of February 10:
0
6
15
Here's @jordan9001 with some deep thoughts on symbolic execution, check out the great symbex training he's put together as well!
0
14
22
If you've ever wanted to shell out on a Jumbotron, Brandon Perry (@BrandonPrry) has you covered! He got hold of a mountain of gear and spent some time poking around.
0
7
13
Brandon Perry (@BrandonPrry) recently found dozens of crashes in @Apple's GarageBand and Logic Pro X. Two of these were CVE-worthy (CVE-2022-22657 and CVE-2022-22664). Here's a quick write-up:
1
21
46
And we're happy to have you, fam!
I am happy to say that I'll be starting at @Atredis next week. :)
0
2
8
During personal research, Brandon Perry (@brandonprry) found a chain of issues in SysAid ITIL that ended in remote code execution. Resulting CVEs include: CVE-2021-43971, CVE-2021-43972, CVE-2021-43973, CVE-2021-43974. Read the full post for the details:
0
11
23
We don't often get to talk about our gigs, so we're excited @uchi_mata from @SalesforceEng wrote about working with @_tomsteele and @0xJDow on multi-tenancy and the @kubernetesio Control Plane! Blog: || Our report and config data:
0
21
22