AmberWolf
@AmberWolfSec
Followers
331
Following
0
Statuses
19
Offensive Cyber, Risk Management & Governance, Vulnerability Research and Technical Due Diligence
UK
Joined February 2024
RT @buffaloverflow: Heres the slides from our HackFest Hollywood talk.. We shared details on a new Palo Alto 0day and provide some tips on…
0
1
0
The slides for @buffaloverflow and @johnnyspandex's "Very Pwnable Networks: Exploiting the Top Corporate VPN Clients for Remote Root and SYSTEM Shells" are now available on our GitHub: #hackfest
0
47
107
RT @jon__reiter: Richard and David from @AmberWolfSec speaking about Very Pwnable Networks: Exploiting the Top Corporate VPN Clients for R…
0
2
0
🚨New Vulnerability: Authenticated RCE in Ivanti Connect Secure (CVE-2024-37404). Discovered by @buffaloverflow , this exploit grants root access via RCE. Read about the discovery, exploit method, and vendor mitigations here:
0
14
35
RT @buffaloverflow: Authentication bypass in Safeguard for Privileged Passwords, discovered by @johnnyspandex and myself Advisory from @Am…
0
9
0
Delighted that Richard Warren and David Cash will be presenting "Very Pwnable Networks: Exploiting the Top Corporate VPN Clients for Remote Root and SYSTEM Shells" at #SANSHackFest in October!
📣 The #SANSHackFest Agenda is LIVE & packed w/ highly technical talks from @dwizzzleMSFT @yarden_shafir @buffaloverflow & David Cash @33y0re & more! Join us in Hollywood for exclusive access to ALL talks, workshops, & challenges. ➡️ Agenda: #PenTest
0
1
6
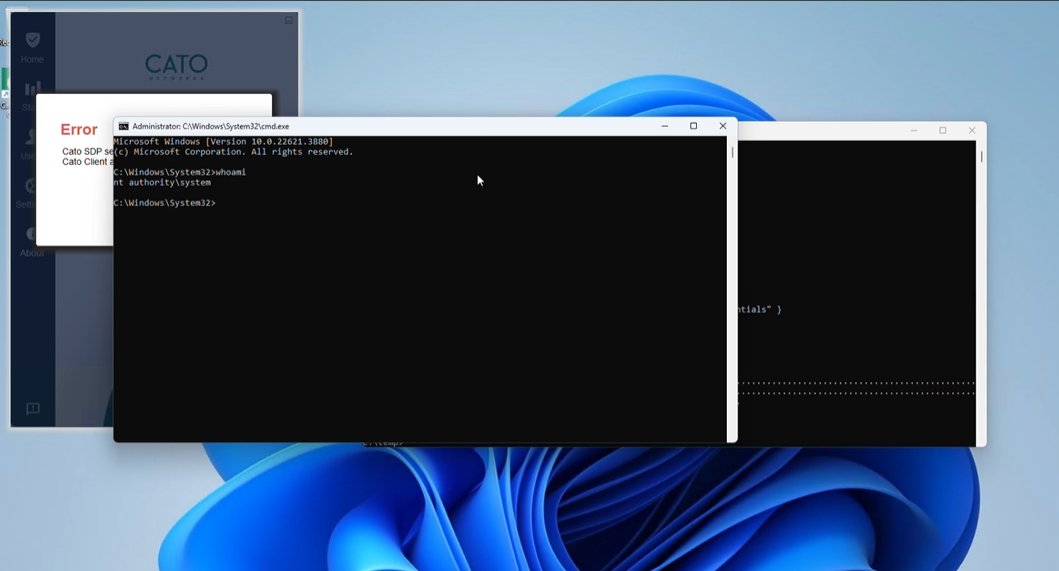
AmberWolf researchers Richard Warren and David Cash found high-risk vulnerabilities in Cato Client, including remote code execution and SYSTEM privilege escalation. Learn more in our blog series: #vulnerability
0
15
37