Anthony Weems
@amlweems
Followers
2,897
Following
253
Media
8
Statuses
171
Cloud Vulnerability Research • The opinions stated here are my own, not those of my company.
Joined April 2008
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Arsenal
• 564211 Tweets
#DoubleTrouble_D1
• 237647 Tweets
ارسنال
• 205458 Tweets
haechan
• 163317 Tweets
Rice
• 118445 Tweets
Brighton
• 89454 Tweets
#ドッキリGP
• 89346 Tweets
Ticketmaster
• 87854 Tweets
Saka
• 69225 Tweets
#خلصوا_صفقات_الهلال2
• 46609 Tweets
ライブツアー
• 41112 Tweets
Qoo10
• 36005 Tweets
ポムの樹
• 32611 Tweets
#ARSBHA
• 28026 Tweets
Joao Pedro
• 22849 Tweets
マッサマン
• 16595 Tweets
ジンくん
• 15026 Tweets
Kai Havertz
• 14605 Tweets
アーセナル
• 13284 Tweets
大曲の花火
• 12122 Tweets
Veltman
• 10476 Tweets
Last Seen Profiles
Just finished Portswigger's new Burp Suite Certification. I've always been a huge fan of the
@WebSecAcademy
and this is an excellent capstone on the labs. Thanks
@PortSwigger
for all the educational content!
#burpsuitecertified
3
3
57
@WebSecAcademy
Thanks for this round of labs! The last two are definitely the most challenging. For anyone stuck, I *highly* recommend this blog post from
@_atorralba
: . Although the conditions are different, it's an excellent walkthrough of the process.
2
1
20
I'm really excited for this video! I got a chance to collab with
@LiveOverflow
and share the process for discovering the localhost bypass for CVE-2021-45046 with code review and differential fuzzing. :)
2
2
19
My team
@praetorianlabs
just published our work in reverse engineering the Proxylogon patches for CVE-2021-26857, CVE-2021-26855, and CVE-2021-27065. I learned a lot more about Exchange than I thought I'd ever need, but had a blast.
1
5
17
@albinowax
@webtonull
A few years ago I accidentally found a vuln like this while using Turbo Intruder for password guessing. Was getting inconsistent results (e.g. valid session for a user with an invalid password). Thought I'd found a bug in Turbo Intruder, but it was a race condition in my target.
0
2
15
@julianor
@vx__notduck1e
@CodeAsm_
I've tested and signature replay works as expected, allowing modification of the command (except the first 5 chars). But I agree it is unrealistic until we actually capture a real signature (which may never happen).
0
0
6
Awesome new work from
@albinowax
on cache poisoning. Cache Key Injection especially feels like it should have some interesting variants.
2
0
5
This is one of the most exciting projects I got to work on last year. 🙂
Helping
@WPEngine
#Secure
Its Next Generation Architecture and
#Kubernetes
Implementation.
#Security
#InfoSec
#AppSec
#containerization
via
@PraetorianLabs
0
0
3
0
1
5
Thanks for the seamless contribution process! Cheers to
@BouncyHat
and
@dallasl1200
😄
Thanks to
@amlweems
, Michael Weber, and Dallas Kaman for performing an analysis on CVE-2021-26855, the Microsoft Exchange SSRF vuln!
0
9
26
0
0
5
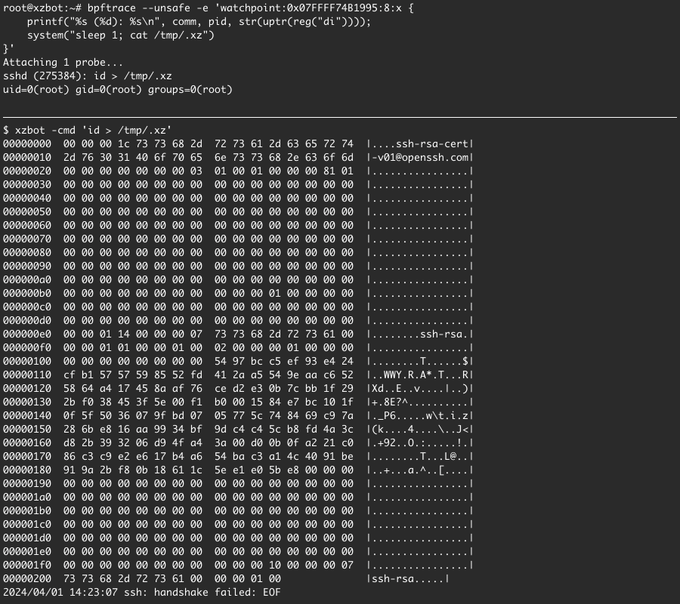
@therealshodan
Did you capture SSH certificates as well? The payload is embedded in the CA signing key in the cert and will always start with 16 bytes that match a specific pattern.
(see for the payload format)
1
0
3
@therealshodan
fyi: if you search for keys, the magic command byte can be obfuscated, I've updated the code with an example.
0
0
2
Also, some great new labs on
@WebSecAcademy
to go along with the research. Thank you for continuing to create free educational content like this.
1
0
2
Shout out to
@b1ack0wl
for his awesome project! :D
0
0
1
@OstensiblyKathy
Did you know you're supposed to "season" your cutting board during its first week in your home? Fun fact.
0
0
1
@ctfhacker
there was a vuln that the CGC operators didn't know about, discovered by one of the teams
1
1
1
.
@ctfhacker
also, one bot found an unknown vuln and the other bot patched it after observing the attempted pov
#d2qd
0
0
1
Excellent write-up, nice job! :D
My writeup for
@superkojiman
's Brainpan3 featuring Binjitsu and Pwndbg:
http://t.co/2KzKYmt58Q
0
18
19
0
0
1
All of our password hashing recommendations rolled in to ONE blog post.
@kelbyludwig
's content is
#2dcc
.
1
0
1
By far my favorite book/movie combo of the year.
#TheMartian
#RobinsonCrusoeOnMars
http://t.co/6pQ6uG403C
0
0
0
.
@ctfhacker
d2qd to the max!
0
0
1