The Shadowserver Foundation
@Shadowserver
Followers
19,164
Following
0
Media
421
Statuses
1,905
Our mission is to make the Internet more secure by bringing to light vulnerabilities, malicious activity and emerging threats. Join our Alliance!
Global
Joined March 2009
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Brazil
• 1211585 Tweets
Elon Musk
• 727945 Tweets
Meu Twitter
• 491510 Tweets
#BUS1stFANCON_KnockKnockKnock
• 199617 Tweets
Adeus Twitter
• 187935 Tweets
Wisconsin
• 116879 Tweets
Caitlin Clark
• 77858 Tweets
Bluesky
• 50055 Tweets
ブラジル
• 47187 Tweets
#GFRunTheWorldConcertD1
• 45255 Tweets
#プレイバックガチャ
• 39196 Tweets
Angel Reese
• 38472 Tweets
#INZM_30Mviews
• 24335 Tweets
michigan state
• 23117 Tweets
Djokovic
• 22689 Tweets
野菜の日
• 20124 Tweets
Popyrin
• 13432 Tweets
Stanford
• 13246 Tweets
台風一過
• 11532 Tweets
Last Seen Profiles
We are reporting out Microsoft Exchange servers still likely vulnerable to CVE-2022-41082
#ProxyNotShell
. Nearly 70K IPs found without MS patches applied (based on version info). Previously recommended mitigation techniques can be bypassed by attackers
6
115
268
@Shadowserver
urgently needs your financial support to move data center before May 26th, to be able to continue providing public benefit services. Please help
#saveshadowserver
and help secure the Internet!
#shadowserver
#infosec
#CyberSecurity
#appeal
3
216
127
UPDATE: Improved Cisco IOS XE Web UI CVE-2023-20198 implant detection, after threat actor modified their compromised device config (hat tip to
@foxit
)
30,487 unique IPs on 2023-10-23
Latest data in tonight's compromised website report. Dashboard stats updated after end of day.
5
62
106
It’s here! Our new Dashboard lets you explore some of our Internet-scale data sets: scanning for exposed services, large honeypot sensor networks for detecting attacks, botnet sinkholing & more. A special thank you to UK FCDO
@LondonCyber
for funding!
3
47
101
At least 539 Unitronics PLC instances (port 20256/tcp) still publicly exposed worldwide (2023-12-02 scan). Unitronics PLC instances have been targeted recently as part of attacks against Water & Wastewater systems. (see
@CISACyber
@WaterISAC
alert: )
2
43
86
Now scanning for exposed Microsoft Message Queuing (MSMQ) services on IPv4/IPv6. Over 403K found on 2023-04-12. Filter traffic to port 1801/TCP & apply MS patch! IP data shared for your network/constituency in Accessible MSMQ report going out tomorrow -
🚨 We discovered 3 vulnerabilities in Microsoft Message Queuing (MSMQ) service, including
#QueueJumper
(CVE-2023-21554), a Critical vulnerability that could allow unauthorized attackers to remotely execute code.
More details in our blog 👉
#PatchNow
4
111
283
2
27
82
Cyclops Blink: modular
#malware
framework targeting network devices announced as potential replacement for VPNFilter
New Special Report run today contains 1573 victim IPs in 495 ASNs & 70 countries, plus 25 C2s:
Urgent remediation needed!
#ThreatIntel
1
46
76
Attention: Now sharing Palo Alto GlobalProtect instances that we tag as CVE-2024-3400 vulnerable (without the "possible-" prefix). Scanning based on confirming existence of files left behind by exploits.
6634 vulnerable IPs found on 2024-04-20:
5
41
66
Cisco IOS XE CVE-2023-20198 compromised instance update: we see around 37K with implants with 19K unique hex values (which may suggest that around 19K is the actual amount of compromised devices). Data for 2023-10-19.
330 IPv6 instances as well.
0
45
65
Heads up! As part of Operation Endgame we are sharing Smokeloader malware infections in our daily sinkhole reports.
Current Dashboard world map view:
Details on Operation Endgame coordinated by
@EC3Europol
:
1
38
65
We started seeing exploitation attempts of CVE-2022-30525 May 13th. If you have any of the affected Zyxel firewalls in your network/constituency, patch now.
Zyxel advisory:
1
31
66
In collaboration with
@Volexity
we have added daily scans & reports of compromised Ivanti Connect Secure VPN instances. Data shared in our Compromised Website report, tagged "ivanti-connect-secure".
609 IPs found on 2023-01-16:
.
@Volexity
provides an update on its Ivanti Connect Secure VPN report concerning chained exploitation of CVE-2024-21887/CVE-2023-46805. Based on new data, 1700+ devices have been compromised following widespread exploitation. Details:
#dfir
#threatintel
3
107
176
1
45
63
Scanning for vulnerable Ivanti Connect Secure (CVE-2023-46805 & CVE-2024-21887) instances has been added to our daily scan list. 6809 found vulnerable for 2024-01-15 scans using methodology from
@watchtowrcyber
- )
More details:
2
37
64
We are sharing out Socks5Systemz proxy botnet infected IPs in our free daily SInkhole HTTP Event reports .
Over 36K IPs seen infected 2023-11-12.
Thank you
@Bitsight
for the collaboration!
Socks5Systemz Infection tracker:
1
28
63
We are sharing Palo Alto GlobalProtect instances that we believe are possibly vulnerable (there may be mitigations in place) to CVE-2024-3400:
Data in Vulnerable HTTP report
22, 542 possibly vulnerable IPs found on 2024-04-18:
1
32
60
Nearly 600K SMB services (port 445/TCP) exposed on the Internet. Down from 1.5M seen in May 2017 when we started scanning and reporting (when
#Wannacry
appeared). Improvements especially in Asia, but still too many out there! Top: US, Russia. See latest:
1
36
59
We observed CVE-2024-21893 exploitation using '/dana-na/auth/saml-logout.cgi' on Feb 2nd hours before
@Rapid7
posting & unsurprisingly lots to '/dana-ws/saml20.ws' after publication. This includes reverse shell attempts & other checks. To date, over 170 attacking IPs involved
We have published our AttackerKB
@rapid7
analysis for CVE-2024-21893, an SSRF vulnerability in the SAML component of Ivanti Connect Secure, that has recently been exploited in the wild, allowing attackers bypass the mitigation for an earlier exploit chain.
4
62
154
1
26
60
Overall still at least 1350 compromised Citrix NetScaler devices seen in our scans (most have webshells installed as a result of previous CVE-2023-3519 exploitation campaigns)
Remediation progress:
Latest country breakdown:
Sharing new data on Citrix NetScaler devices compromised via a CVE-2023-3519 campaign that involves malicious code injection to steal credentials (see the writeup by
@IBM
X-Force for details). We see 285 NetScaler IPs compromised:
2
14
25
0
33
57
With many un-patched MS
#Exchange
Servers still being rapidly compromised, we have partnered with
@kryptoslogic
to provide another Special Report covering 6720 exposed webshells that could be used to deploy ransomware, etc. Please remediate urgently!
1
37
57
Heads-up! We have published details of Citrix CVE-2023-3519 incidents thanks to collaboration with our trusted partners. Please ensure you follow the detection & hunting steps provided for signs of possible compromise & webshell presence.
#cybersecurity
1
36
54
#Log4j
CVE-2021-44228 scanning & exploit activity is being shared in the daily Honeypot HTTP Scanner Events report since the start: . Since 2021-12-12 the vulnerability_id field for these should also contain the CVE-2021-44228 tag.
2
33
55
Sharp increase in queries for "/oauth/idp/.well-known/openid-configuration" endpoint associated with Citrix NetScaler CVE-2023-4966 (leaking of session tokens) observed by our honeypot sensors. This is after recent
@assetnote
publication.
1
23
56
We are happy to announce the first major extension to our newly launched Dashboard – the addition of Internet-wide IoT device fingerprinting and server-side attack statistics, collected through the
@VARIoT_project
.
Dashboard:
2
30
55
Over a month after Citrix advisory publication NetScaler CVE-2023-4966 exploitation attempts continue to be one of the most common attacks seen by our honeypot sensor network.
If you are running NetScaler & did not patch initially assume compromise.
Sharp increase in queries for "/oauth/idp/.well-known/openid-configuration" endpoint associated with Citrix NetScaler CVE-2023-4966 (leaking of session tokens) observed by our honeypot sensors. This is after recent
@assetnote
publication.
1
23
56
1
21
52
If you are searching for exposed Ivanti Connect Secure appliances in your network/constituency, you can get a daily breakdown of these (amongst other devices) in our device identification report:
(vendor is set to "Pulse Secure")
Over 17.1K exposed
.
@Volexity
detected an incident where it discovered a threat actor chained 2
#0days
in Ivanti Connect Secure, CVE-2023-46805/CVE-2024-21887, to achieve RCE, modifying components of the software to backdoor the device.
#dfir
#threatintel
#memoryforensics
5
165
298
1
28
51
~3800 vulnerable ConnectWise ScreenConnect instances (authentication bypass using an alternate path or channel (CVSS 10) & path traversal (CVSS 8.4))
IP data in:
~93% instances of ScreenConnect seen on 2024-02-20 still vulnerable:
2
21
52
We have also started scanning & sharing F5 BIG-IP instances that remain vulnerable to CVE-2023-46747. 382 vulnerable instances found on 2023-11-29. This vulnerability is actively exploited & on
@CISACyber
KEV list. Assume compromise if you receive a report from us!
1
24
50
Although we are not scanning IPv4 /0 for CVE-2021-44228 &
#Log4Shell
, new one-off Vulnerable
#log4j
Servers Special Report just sent to 132 nCSIRTs and 6000+ network owners globally.
Data courtesy of
@AlphaStrikeLabs
Info & analysis:
Please patch now!
0
34
50
International Law Enforcement coordinated action against Emotet. Great effort: Shadowserver tips its hat to everyone involved & hard work over the years
Sinkholed events included in our free daily reports for CERTs and network owners from today:
1
14
50
Donor
#Kudos
:
@craignewmark
philanthropist and all round awesome person, generously offered to cover entire $400k data center move within first 24 hours, funds received before contract deadline. Critical initial impact investment, perfect start for
#appeal
to
#saveshadowserver
!
3
14
49
Second one-off Special Report on exposed Exchange Servers, based on scanning collaboration with
@DIVDnl
. Kudos for sharing! 64088 of 111988 IPs potentially still vulnerable 20210309 - please patch & remediate quickly. Blog: Report:
2
35
48
Heads up! We are sharing out a second Special Report on Compromised SSH hosts detected through leakage of malicious public SSH keys placed on them by attackers:
This time 10020 compromised hosts found. Top countries US (3K), China (2.9K), Singapore (423)
1
24
47
We have just sent out a one-off report on Fortinet device IPs very likely vulnerable to CVE-2022-40684. 17415 seen worldwide (scan by
@leak_ix
). See:
Most in US (3.4K) and India (1.7K). These should be patched and not have their admin interface exposed.
2
25
46
With detailed vulnerability/exploit analysis now published, we have started to observe Fortinet CVE-2024-21762 exploitation attempts executing callbacks as of March 17th UTC. These are currently coming from one IP hitting FortiGate devices.
Investigate for compromise & update!
1
22
43
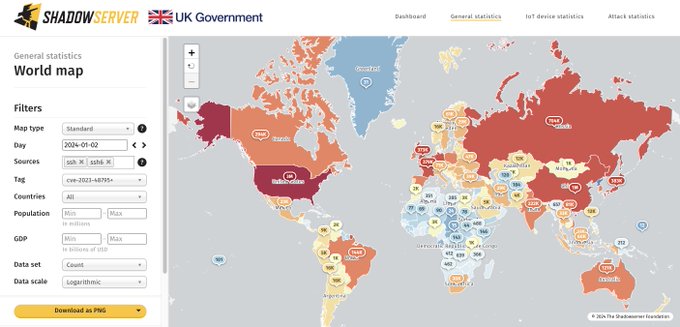
Data on vulnerable Ivanti Connect Secure devices now available on our Dashboard, for example
World map:
Tree map:
Tracker:
Scanning for vulnerable Ivanti Connect Secure (CVE-2023-46805 & CVE-2024-21887) instances has been added to our daily scan list. 6809 found vulnerable for 2024-01-15 scans using methodology from
@watchtowrcyber
- )
More details:
2
37
64
0
22
41
As part of Operation Endgame we shared a second one-off Special Report on IcedID/Latrodectus bot infections:
Dashboard map view:
Details on Operation Endgame coordinated by
@EC3Europol
:
2
17
42
As of end of last week, we are sharing IPs of PlugX infected machines in our daily sinkhole reports thanks to collaboration with
@sekoia_io
Background at
Dashboard stats for 2024-05-06 (~9K hosts daily):
1
29
39